57 Set Up User and Group Security
This chapter contains these topics:
From Master Directory (G), choose Hidden Selection 27
From Advanced & Technical Operations (G9), choose Security & System Admin
From Security & System Administration (G94), choose Security Officer
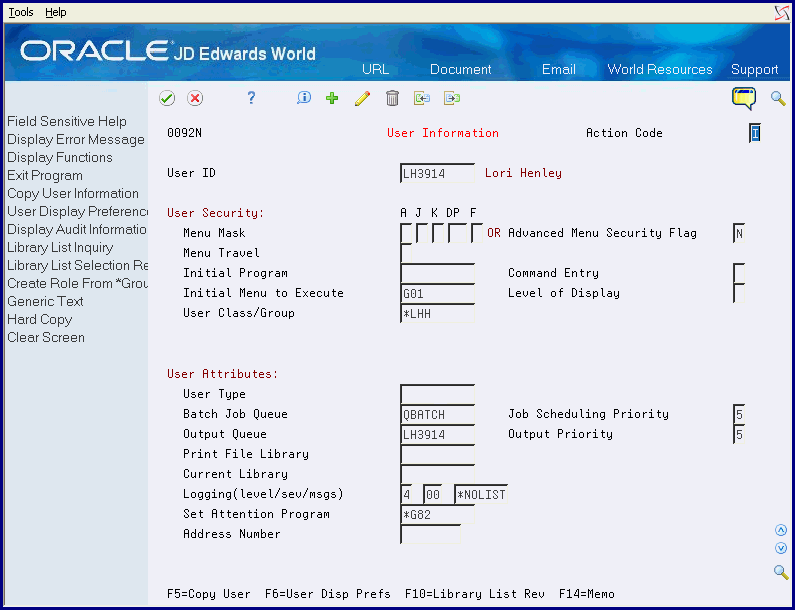
From Security Officer (G9401), choose User Information
57.1 Setting Up User Security
Set up user security to restrict users from certain features. For example, an AP clerk might access an initial custom menu, but cannot use command entry, menu traveling, or fast path. User security offers the following:
-
Advanced menu Security OR User keys used in conjunction with menu locks for menu masking
-
Initial menu to execute
-
Menu traveling
-
Command entry
-
User class/group
See Also:
-
Chapter 19, "Work with User Profiles" for more information about user profiles.
57.2 Securing Command Entry
Securing command entry on the User Information screen changes your display on JD Edwards World screens. The Command line changes to the Selection line.
Note:
This does not secure Command Entry on IBM screens.To secure Command Entry on IBM screens
-
Use Advanced Menu security or Menu masking to hide Hidden Selection 36 - Command Entry.
-
Set the Allow Command Entry field to 'N' on the User Information screen.
-
Set the Limit capabilities to *YES in the IBM user profile.
Note:
When the Limit Capabilities field is set to *YES on the IBM User Profile it overrides a Y setting in the Allow Command Entry field in the User Information program (P0092) on the Security Office menu (G9401). This restricts the use of commands on the Command Line, Group Jobs, and Software Versions Repository (SVR) (F2 in SVR). It is recommended that you review all IBM user profiles that access JD Edwards World software. Set the Limit Capabilities field to *NO or *PARTIAL to allow the user to run commands from these options. If some user's profiles have the Limit Capabilities field set to *YES, then you can set up the system to allow them to execute certain commands by entering CHGCMD on the Command Line. For example, to allow users to execute the CHGOBJ command, enter CHGCMD CHGOBJ on the Command Line and then set the Allow Limit Users (ALWLMTUSR) field to *YES.57.3 Setting Up Group Security
Group security is the ability to group users so that each individual takes on the characteristics of the group. Create groups based on similar job requirements. The name of the group must begin with an asterisk (*). For example: If the group is *AP assign each Accounts Payable clerk the group *AP.
When you set up groups, certain security features are available that you can place on the group as a whole. You secure each member through the group.
*PUBLIC is considered a group profile. *PUBLIC is not delivered with the system. Add *PUBLIC to activate it. Once added, all users automatically are included.
Roles may also be set up, in order to allow users access to security defined for multiple groups. Roles may comprise users and/or groups.
See Also:
-
Chapter 20, "Work with Roles" for more information about roles.
-
Part XIII, "JD Edwards World Security" for more information about how to set up user and group security.
-
On User Information, add a group user profile with the following:
-
User class/group field must be blank
-
Name of group must begin with *
The system does not require a corresponding IBM profile.
-
-
Add the group profile name to the User Class/Group field for each user ID in the group.