60 Work with Business Unit Security
This chapter contains these topics:
60.1 About Business Unit Security
From Master Directory (G), choose Hidden Selection 27
From Advanced & Technical Operations (G9), choose Security & System Admin
From Security & System Administration (G94), choose Security Officer
From Security Officer (G9401), choose Business Unit
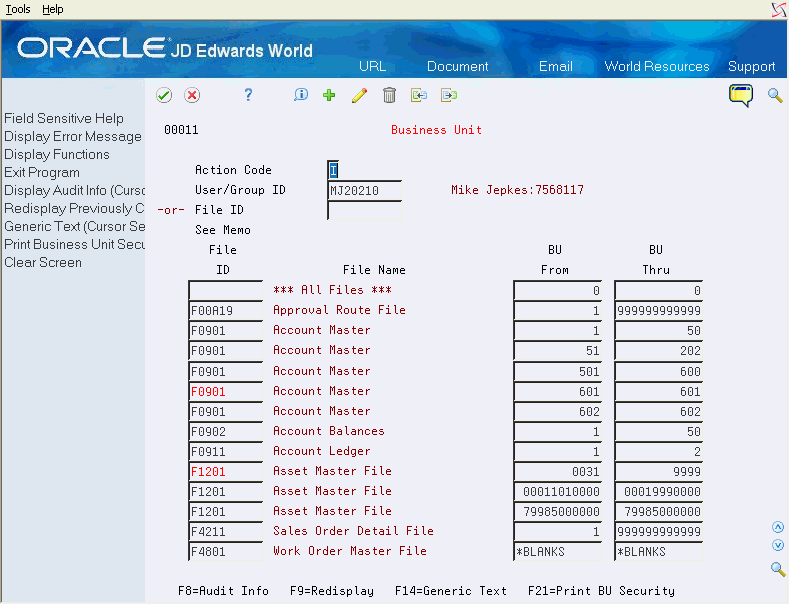
Business Unit Security Revisions (P00011) allows you to set up or change business unit security for an individual user ID, a group profile ID, or *PUBLIC. Business unit security information is stored in the Business Unit Security file (F0001).
Business unit security allows you to secure a portion of the records in a file based on the business unit. Typically, business units are used to define locations, divisions, and other natural boundaries of management authority. Using business unit security, you may restrict users or groups of users from entering into areas outside of their responsibility.
Business unit security accommodates role-based security. In addition to user and group level security, users may be assigned to a security role. When users sign on with a security role, all the groups tied to that security role will be considered when determining authorization to business units.
Important:
The Business Unit Security program by default denies access if you have not set up records To allow access to business unit security, you must set up records for individual users, groups, or *PUBLIC with the appropriate authorization.Note that if you do not set up Business Unit security to allow access, then Dream Writers that include a Business Unit coded field will automatically add the Business Unit field to the data selection with no criteria (i.e. MCU < " ") upon execution, and the programs will thus joblog with a message that no records are selected.
60.1.1 Setting up Business Unit Security
To set up business unit security
-
On Business Unit, enter a user ID, group ID or file ID.
-
Specify the range of business units using the Business Unit From and Thru fields.
In the top half of the screen, you may enter either User/Group ID or File ID. Upon pressing enter, the subfile will display all files associated with a particular user/group ID, or all users and groups associated with a particular file ID.
To add new lines to an existing user or group ID or file ID, inquire first. You can then place an 'A' in the Action Code field and enter new information on either the first available blank space or over an existing ID. If you enter a 'C' in the Action Code field and enter information in the first available blank space, the record is added. If there is a 'C' in the Action Code field and you type over an existing record, that record's information is changed (including the key).
Use the 'D' action code cautiously. If you enter 'D' in the Action Code field after you have inquired on a user or file ID, all records in the subfile are deleted. To delete just one record in the subfile, place a 'C' in the Action Code field, scroll down and clear the User ID, Business Unit From and Business Unit To fields in the line that has to be deleted, and press Enter.
The following function keys are available on the screen - note that your cursor must be on a subfile record in order to use these options:
-
F14 - Memo: Use this option to enter free-form text with any notes, comments or explanations about the security record. If a memo exists for a record, the subfile values in the User/Group ID or Video Screen column are highlighted and the text 'See Memo' displays above the column.
-
F8 - Audit Information: Use this option to retrieve audit information for a security record.
Press F9 to display an inquiry again after an update.
60.2 Considerations for Business Unit Security
This section discusses important consideration for implementing business unit security.
60.2.1 Files Secured Using Business Unit Security
Business unit security is based on a business unit Data Dictionary item such as MCU. Business unit data items are identified by COSTCTRSEC in the Data Item Class field in the Data Dictionary file. The security is based on the first business unit data item found in the file. If no business unit data item resides in the file, business unit security is be in effect for that file.
60.2.2 Alphanumeric and Numeric Characters for Business Unit Setup
This sections discusses considerations for setting up business units.
60.2.2.1 Alphanumeric Business Unit Definition
An Alphanumeric business unit is a business unit name that contains at least one non-numeric character in the business unit name. The following table lists examples of alphanumeric business unit setup:
| Business Unit | Description | Explanation |
|---|---|---|
| DEN | Denver | Every character is a letter |
| M30 | Memphis Mfg. Plant | 'M' is not a digit |
| 02D | Denver Corporate Hq | 'D' is not a digit |
| 1983A | A Income Statement | 'A' is not a digit |
| 200-102 | Milling Machine | '-' is not a digit |
| 200.103 | Milling Machine | '.' is not a digit |
Each business unit name in this table is considered alphanumeric because it contains at least one non-numeric character (not including blank characters).
60.2.2.2 Numeric Business Unit Definition
A numeric business unit is a business unit name that contains only digit characters 0-9 in the business unit name. The following table lists examples of numeric business unit setup:
| Business Unit | Description | Explanation |
|---|---|---|
| 1 | A Financial Company | Every character is a digit from 0-9 |
| 7 | A Model Payroll Company | Every character is a digit from 0-9 |
| 07 | A Different Payroll | Every character is a digit from 0-9 |
| 11 | Corporate Office Systems | Every character is a digit from 0-9 |
| 4343 | Vector Manufacturing Co | Every character is a digit from 0-9 |
| 0004344 | Venus Universal Supply | Every character is a digit from 0-9 |
| 778882002 | Valley View Subdivision | Every character is a digit from 0-9 |
Each business unit name in this table is considered numeric because it contains only numeric characters (not including blank characters). Note that '7' and ' 07' are different numeric business units because it is a character-based data type and not a true number.
60.2.2.3 Planning Business Unit Setup
Most interactive programs (as well as FASTR reporting) differentiate between numeric and alphanumeric business units within the business unit security ranges; SQL-based applications such as World Writer and DREAM Writer-based programs do not. To achieve consistent results with business unit security, it is very important to plan the business units that you create. It is recommended that you define either alphanumeric business units or numeric business units.
Before defining a business unit range, always print a list of Business Units (P0006P) which selects MCU values in the desired BUSINESS UNIT security range and ordered by the MCMCU column. The user running the report must have access to all business units in the F0006 file. This report lists the business units defined in the desired range and displays any discrepancies.
If you already have a mix of alphanumeric and numeric business units set up, you can block out and define specific ranges of business units as either all alpha or all numeric within those business unit definition ranges. You can then run P0006P to validate that the business units that you created follow the guidelines that you have defined. This will assist you in defining business unit security ranges so that both World applications and SQL based reporting will recognize the same business unit range data.
60.2.3 Business Unit Ranges
Business unit security compares business units in the application file to be secured against ranges defined in the Business Unit Security file. There are three types of ranges: numeric, alphanumeric, and *BLANK:
| Type of Range | From | Through |
|---|---|---|
| Numeric | 1 | 999999999999 (entire numeric range) |
| Numeric | 100 | 9999 (numeric BUs between 100 and 9999) |
| Alphanumeric | A | 99999999999Z (entire alphanumeric range) |
| Alphanumeric | AA | Z9 (alphanumeric BUs between AA and Z9) |
| Blank business unitq | *BLANKS | *BLANKS (only when the business unit is blank |
Avoid mixing numeric and alphanumeric business units in the same range, but you can have both numeric ranges and alphanumeric ranges for the same user/group ID and file ID.
The *BLANKS business unit range is used when securing a file for which the business unit is optional, and therefore might be blank on some records.
When you create a business unit security rule in the Business Unit Security program (P00011), you must define a start and end value for each specific rule. Both the start and end values must be of the same type: Either they are both alphanumeric or they are both numeric.
An alphanumeric business unit security range is a rule in P00011 where the start and end MCU values of the ranges are both alphanumeric. An alphanumeric business unit security range authorizes only alphanumeric business units within that range. Any numeric values in the range are not authorized.
Similarly, a numeric business unit security range is a rule in P00011 where the start and end MCU values of the ranges are both numeric. A numeric business unit security range authorize only numeric business units within that range. Any alphanumeric values in the range will not be authorized.
60.3 Checking Business Unit Security
Business unit security is checked in the following order:
-
User Profile ID and File ID
-
User Profile ID and File ID = blank (all files)
-
Group Profile ID (if any) and File ID
-
Group Profile ID (if any) and File ID = blank
-
*PUBLIC and File ID
-
*PUBLIC and File ID = blank
At each check, if at least one business unit range is found, the program grants the user access to the business units that fall into the range or ranges found in the Business Unit Security File.
If you are using role- based security, a user signed on using a role may have access to the authority for multiple groups. In this case, the checks for group profile check all active groups for the role. If any group has authority, the role is granted authority. When a user is signed on using a role, the user profile's group, if any, is not checked. If you are not using role-based security, the system uses the group profile, if any, from the JD Edwards User Profile.
If you do not specify a particular file during setup, the system applies the ranges of business units that you designate by user ID to all secured files. The same applies to group and *PUBLIC records.
Conversely, if you do specify a file, the ranges of business units listed are applied to that particular file only. Please note that the default authorization is 'no access'. If no applicable record for a business unit check is found, the user is not granted access. The system secures anything that is not on their list for that file.
60.4 Technical Considerations for Business Unit Security
Set up business unit security for those master files that are relevant to the system that you want to secure. Since you only gain access to detail files through the master file, there is usually no need to apply business unit security to that level. Business unit security is checked in the following ways:
-
In DREAM Writer, business unit security adds additional selection criteria to the OPNQRYF statement.
-
In World Writer, business unit security adds additional selection criteria to the SQL SELECT statement.
-
In World interactive applications and in FASTR, business unit security is checked using a common security program.
Note:
Not all interactive applications are programmed to check business unit security. You should test to be sure business unit security is active for the files you want to secure.The system performs business unit security for master file, including
-
Business Unit Master
-
Address Book Master
-
General Ledger Account Master
-
Payroll Master
-
Property & Equipment Master
-
Lease Master
-
Contract Administration Master
-
Item Branch Master
-
Sales Order Header
-
Purchase Order Header