61 Work with Function Key Security
This chapter contains these topics:
61.1 About Function Key Security
Function key security allows you to secure function key and selection options in a particular video or *ALL videos by user, group, or *PUBLIC profiles.
Function key security accommodates role-based security. In addition to user and group level security, users may be assigned to a security role. When users sign on with a security role, all the groups tied to that security role will be considered when determining authorization to function keys and selection options.
Important:
The Function Key Security program by default denies access if you have not set up records for function keys and selection options with the Allow Usage flag set to 'Y'. TO allow access to function key security, you mut set up records for individual users, groups, or *PUBLIC with the appropriate authorization.Secured function keys/options do not display in the Available Functions/Options screen F24 or when you use F1 on the Selection Options column.
Secured function keys still display on Line 24. Use the Vocabulary Overrides program (P9220) to remove them if you have locked all users out of a particular function key.
Use function key security to restrict menu level function keys. Use video V00MENU.
From Master Directory (G), choose Hidden Selection 27
From Advanced & Technical Operations (G9), choose Security & System Admin
From Security & System Administration (G94), choose Security Officer
From Security Officer (G9401), choose Function Keys
Function Key security allows you to set up security for function keys and/or options by screen or user:
-
Secured function keys/options do not display in Available Functions/Options screen F24 or F1.
-
Secured function keys still display on Line 24. Use Vocabulary Overrides to remove them.
-
Use Function Key security to restrict menu level function keys. Use screen V00MENU.
-
Use Data Dictionary item #JDEFNC to modify run-time text on *ALL security.
The function key security file is F9612 and is in the common library.
61.2 Working with Function Key Security
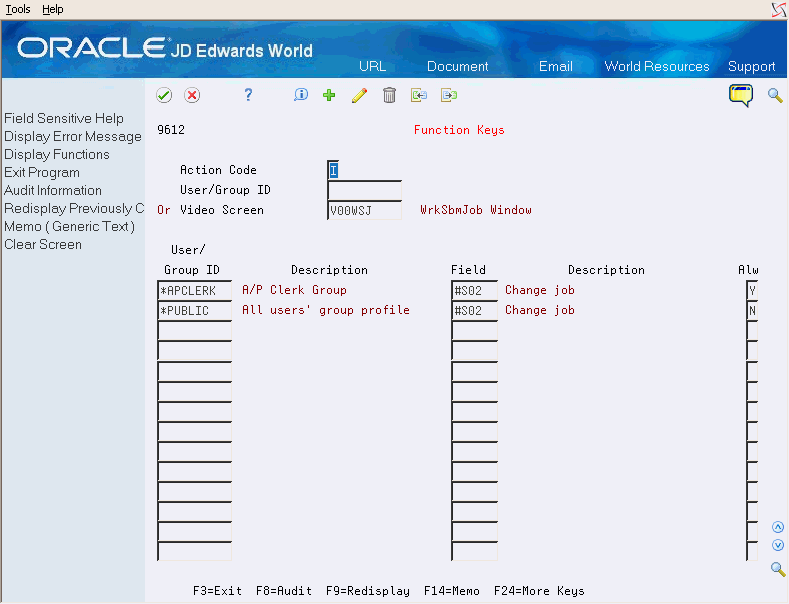
To work with function key security
In the top half of the screen, you may enter either User/Group ID or Video Screen ID. After you press Enter, the subfile displays all videos associated with a particular user or group ID, or all users and groups associated with a particular video.
The following function keys are available on the screen - note that your cursor must be on a subfile record in order to use these options:
-
F14 - Memo: Use this option to enter free-form text with any notes, comments or explanations about the security record. If a memo exists for a record, the subfile values in the User/Group ID or Video Screen column will highlight and See Memo displays above that column.
-
F8 - Audit Information: Use this option to retrieve audit information for a security record.
Press F9 to display an inquiry again after an update.
61.2.1 General Guidelines
To add new lines to an existing user or video, inquire first. You may then place a 'C' in the Action Code field and enter new information on either the first available blank space or over an existing ID. If you enter 'C' in the Action Code field and enter information in the first available blank space, the system adds the record. Regardless whether you enter a 'C' or an 'A' in the Action Code field, the record is changed if you type over an existing record.
After you set up a 'model' profile, you may use that model to add new profiles. Use the following steps to add profiles based on a model profile:
-
Inquire on the model
-
Roll to the end of the subfile to be sure all records are included.
-
Enter 'A' in the Action Code field, enter the new profile, and press Enter.
-
Inquire on the new profile that you just added to verify the additions.
Use the same approach for videos.
Use the 'D' action code cautiously. If you enter 'D' in the Action Code field after you have inquired into a profile or video screen, all function key security coding for this profile or video is deleted. To delete just one record in the subfile, place a 'C' in the Action Code field, scroll down and clear the video screen or user/group ID in the line that has to be deleted, and press Enter.
61.2.2 Function Code Security - Helpful Hints
When working with function code security, the following considerations apply:
-
If you do not use role-based security, the system uses the group profile from the JD Edwards user profile, if a use profile exists.
-
The system checks for security records in the following order:
-
User Profile ID, Video and Field
-
User Profile ID, Video and Field = *STD (Standard Keys)
-
User Profile ID, Video and Field = *ALL (All Function Keys)
-
User Profile ID, Video = *ALL and Field = *ALL
-
Group Profile ID, Video and Field
-
Group Profile ID, Video and Field = *STD (Standard Keys)
-
Group Profile ID, Video and Field = *ALL (All Function Keys)
-
Group Profile ID, Video = *ALL and Field = *ALL
-
*PUBLIC, Video and Field
-
*PUBLIC, Video and Field = *STD (Standard Keys)
-
*PUBLIC, Video and Field = *ALL (All Function Keys)
-
*PUBLIC, Video = *ALL and Field = *ALL
-
When the system locates an appropriate record, the application stops checking and uses the authority on the record it has found. Thus records higher in the order override lower records.
61.3 Standard Function Keys
The standard function keys for a video are F1, F3, F7, F24, Rollup, Rolldown, and Help keys. Standard function keys are made available automatically whenever the user has any other access to the video.
Use of '*STD' in Field allows the user or group to use the standard function keys in the video. You can enter the value 'Y' in the Allow Usage field only if Field = '*STD'.
To lock out a video completely, use '*ALL' in Field with the Allow Usage field set to 'N', with no other security records that grant access to the video. If users try to access the video they are notified of a security violation and are not able to see the video.
-
On Function Keys, enter a screen ID in the Video Screen field, such as V01051 - Address Book Information.
-
Add *PUBLIC or a group profile record with the Field field set to *ALL and the A (allow) field set to N.
-
Add a user record with the Field field set to *STD and the A (allow) field set to Y.
61.3.1 Examples
The following examples illustrate function code security.
61.3.1.1 Example 1
In this example, the user does not belong to a group and is not associated with a security role.The following setup demonstrates the setup for authorization to the standard function keys in video V01051 in addition to function key F6. This setup does not allow access to any other videos:
| User/Group | Video | Field | Function Key | Allow Usage |
|---|---|---|---|---|
| SALLYJONES | V01051 | #F14 | F6 | Y |
| *PUBLIC | *PUBLIC | *ALL | *ALL | N |
The user has access to the standard function keys because they are automatically authorized whenever any other function key or selection option is authorized.
61.3.1.2 Example 2
In this example, the user belongs to GROUPONE, defined onthe user's JD Edwards User Profile. The user does not belong to a security role, so has access to security defined for his user ID or group ID. The following setup demonstrates the setup for authorization to the standard function keys in all videos except V01051, where the is locked out completely:
| User/Group | Video | Field | Function Key | Allow Usage |
|---|---|---|---|---|
| JOHNDOE | V01051 | *ALL | All functions | N |
| GROUPONE | *ALL | *STD | Standard keys | Y |
| *PUBLIC | *ALL | *ALL | *ALL | N |
61.3.1.3 Example 1
ROLEONE is a security role with associated groups GROUPONE, GROUPTWO and GROUPTHREE. The following setup demonstrates the setup for authorization to the standard function keys in video V01051, when signed on under role ROLEONE:
| User/Group | Video | Field | Function Key | Allow Usage |
|---|---|---|---|---|
| GROUPONE | V01051 | *ALL | All functions | N |
| GROUPTWO | V01051 | *ALL | All functions | N |
| GROUPTHREE | V01051 | *STD | Standard keys | Y |
| *PUBLIC | *ALL | *ALL | *ALL | N |
The user has access to the standard function keys because they are automatically authorized whenever any other function key or selection option is authorized.