Fundamental Oracle E-Business Suite Setup Tasks
Oracle E-Business Suite Setup Steps
Oracle E-Business Suite is installed using the Rapid Install tool. Refer to Oracle E-Business Suite Installation Guide: Using Rapid Install for detailed information on running Rapid Install.
The following steps are carried out as part of, or after, Oracle E-Business Suite installation:
-
Run Rapid Install
-
Test Web listener virtual directories
-
Test Oracle HTTP Server configuration
-
Create DBC files
-
Test Java Servlet setup
-
Set Web Server profile options
The above is not an inclusive list of the installation and post-installation tasks that may be needed on a particular system. Additional Oracle E-Business Suite features and options may need to be set up. These are detailed in the following sections.
Secure Configuration of Oracle E-Business Suite
Refer to About Oracle E-Business Suite Secure Configuration, Oracle E-Business Suite Security Guide for important information on securing your Oracle E-Business Suite installation.
Administering Oracle HTTP Server
Oracle HTTP Server Powered by Apache provides the communication services within Oracle Application Server. This facilitates deployment of HTML-based applications within a multi-tiered computing environment.
Oracle HTTP Server
All incoming client requests to Oracle Internet Application Server (AS) are handled by the Communication Services component of AS. The Oracle HTTP Server accepts and processes these requests. The Apache technology adopted by Oracle HTTP Server provides an extremely stable, scalable, and extensible platform on which to deploy web-based applications. The modular design of the Apache server allows for extension of the capabilities of the Oracle HTTP Server. In addition to the standard Apache modules (often referred to as modules, or simply mods), a number of Oracle specific modules are provided along with an extension to the functionality of several standard modules.
These modules include:
-
mod_ossl - This module provides secure HTTPS listener communications using Oracle-provided encryption libraries which support TLS versions 1.0, 1.1, and 1.2 . The mod_ossl module replaces mod_ssl. In contrast to the OpenSSL module, mod_ossl is based on the Oracle implementation of TLS, and uses Oracle Wallet files for certificate storage. An example for the location of the Apache HTTP Server SSL configuration file, ssl.conf, is
/u02/FMW_Home/webtier/instances/EBS_web_MYDB/config/OHS/EBS_web_component. -
mod_perl - This module forwards Perl requests to the Perl Interpreter. The Perl Interpreter is embedded within the Oracle HTTP Server, removing the necessity to spawn an external interpreter as well as providing a caching mechanism such that modules and scripts need only be loaded or compiled once. Oracle E-Business Suite does not currently utilize mod_perl.
For Oracle E-Business Suite Release 12.2, the Oracle HTTP Server is powered by version 2.2 of Apache. A number of books have been published describing the operation of the Apache server. To further add to your knowledge of the Apache server, you may wish to consult one of these.
Note: Refer to the Oracle HTTP Server documentation for a more detailed description of the operation and configuration of the Oracle HTTP Server. The information in this section is supplementary to that provided in the Oracle HTTP Server books.
Oracle E-Business Suite Installation Guide: Using Rapid Install should be consulted for additional information on directory structures and file locations referred to in this guide.
Configuration Files
Apache is configured through directives contained in one or more configuration files. The directives necessary for operating Apache within the Oracle environment will be entered into the configuration files during the install process. It should not be necessary to modify these files unless the system is being re-configured.
Warning: An invalid directive entered into a configuration file will prevent Apache from starting. An incorrect definition provided to a directive may cause Apache to behave in an unintended fashion.
Location
The Apache configuration files are installed as part of the Oracle E-Business Suite Rapid Install process. For example, the files could be placed in /u02/FMW_Home/webtier/instances/EBS_web_VIS1012_al1/config/OHS/EBS_web_component (on UNIX).
Transport Layer Security Configuration
Transport Layer Security (TLS) allows the Apache listener to encrypt web traffic and transmit it securely on the network using the HTTPS protocol.
TLS uses an encrypting method called public key cryptography, where the server provides the client with a public key for encrypting information. The server's private key is required to decrypt this information. The client uses the public key to encrypt and send information to the server, including its own key which identifies it to the server.
In order for the Oracle HTTP Server, powered by Apache, to function in secure mode it is also necessary to use certificates which validate the server's identity. These certificates are used to ensure that the owner of a public key is who they say they are. Typically you will want to use a private key with an officially signed certificate, validated by a Certificate Authority (CA). The CA performs validation depending on the type of certificate. The most common certificate type, domain-validated (DV), only requires the CA to validate proof of control over a domain or the fully qualified domain name (FQDN) in the certificate; organization validated (OV) and extended validation (EV) certificates require validation of company details. The CA also sets expiration dates on the certificates and may place usage restriction policies within the certificate. A number of CAs exist, and include such authorities as Comodo, IdenTrust, and DigiCert.
To obtain a CA signed certificate, it is necessary to generate a certificate request (CSR). This CSR is then sent to the CA, validated, signed, and returned.
For detailed instructions for enabling TLS, refer to My Oracle Support Knowledge Document Enabling TLS in Oracle E-Business Suite Release 12.2 (Note 1367293.1).
Test Startup of Apache and Oracle E-Business Suite Sign-On
Restart the application tier Apache services using the adapcctl.sh script in the $ADMIN_SCRIPTS_HOME directory. Ensure that Apache can startup successfully, and that you successfully get an SSL connection to the default Apache banner screen using https:/<host.domain>:<SSL_port>, where <host.domain> is the fully qualified name of the machine running Apache, and <SSL_port> is the SSL port number defined in ssl.conf.
Once you have signed on to Oracle E-Business Suite, select a responsibility and process that will launch a Forms-based application. For example, System Administrator responsibility and the Define User process.
Note: For further details of using SSL, see My Oracle Support Knowledge Document 1367293.1, Enabling SSL in Oracle E-Business Suite Release 12.2, and Knowledge Document 376694.1, Using the Oracle Wallet Manager Command Line Interface with Oracle E-Business Suite Release 12.
AdminAppServer Utility
Using the AdminAppServer Utility
The Java script AdminAppServer is used to create .dbc files and to enable or disable application server security.
Prior to running AdminAppServer you must ensure that:
-
JDBC classes are in the classpath
-
$JAVA_TOP is in the classpath
For UNIX platforms, the script is run as:
java oracle.apps.fnd.security.AdminAppServer [parameters]
For Windows platforms, the script is run as:
jre -classpath %CLASSPATH% \ oracle.apps.fnd.security.AdminAppServer [parameters]
The following commands are supported:
-
ADD - create a new .dbc file
-
UPDATE - update an existing .dbc file
-
DELETE - delete an existing .dbc file
-
STATUS - check the serverID status for a database
-
AUTHENTICATION - toggle authentication mode
Additional parameters depend on the operation. These include:
-
DBC - The .dbc file to modified, or used to connect to the database. Used with UPDATE, DELETE, STATUS, AND AUTHENTICATION.
-
SECURE_PATH - Used with ADD. This parameter specifies in which directory the .dbc file should be created, and defaults to the current directory if not provided. This parameter should always point to $FND_TOP/secure.
-
DB_HOST - Required. The host machine of database.
-
DB_PORT - Required. The port of database. The default is 1521.
-
DB_NAME - For thin drivers. The database SID.
-
APPS_JDBC_DRIVER_TYPE - THICK or THIN. This parameter must be set to THIN.
-
GUEST_USER_PWD - Any valid applications user. This parameter defaults to the value of GUEST_USER_PWD profile if not provided. If passed with no arguments to an UPDATE call, it will refresh with the value from database.
-
GWYUID - For thick drivers.
-
FNDNAM - For thick drivers.
-
TWO_TASK - For thick drivers. Name of database.
-
WALLET_PWD - Used with the TCF Socket Server in SSL mode.
-
SERVER_ADDRESS - Used with authentication.
-
SERVER_DESCRIPTION - Used with authentication.
-
FND_MAX_JDBC_CONNECTIONS - The maximum number of open connections in the JDBC connection cache. This number is dependent on the amount of memory available, number of processes specified in the init.ora file of the database and the per-processor file descriptor limit.
-
FND_IN_USE_CONNECTION_TIMEOUT - The maximum number of seconds a connection can be in use. In order to avoid connections being locked up for too long, the connection cache uses this parameter to forcibly close connections that have been locked for longer than this specified limit. If this parameter is unspecified, connections in use will not be cleaned up. This should be set to a number larger than the time taken to complete the largest transaction.
-
FND_UNUSED_CONNECTION_TIMEOUT - The maximum number of seconds an unused connection can remain in the cache. The connection cache will close and remove from the cache any connection that has been idle for longer than this specified limit.
Important: The following parameters are required: APPS_JDBC_DRIVER_TYPE (must be set to THIN), DB_HOST, and DB_PORT.
Administering .dbc Files
The .dbc file is contained on the web/applications server and holds information used by the database for authentication. The web/application server passes the information from the .dbc file, as well as login information, to the database server to authenticate the user. The authentication process is handled by the standard applications security feature.
The .dbc files required by the application server security system are not part of the delivered product and must be created after installation.
The Java utility AdminAppServer is used to create the .dbc files.
Prior to running AdminAppServer you must ensure that:
-
JDBC classes are in the CLASSPATH
-
$JAVA_TOP is in the classpath
Creating a .dbc file
Use the AdminAppServer utility to create a .dbc file for the application server to access the database server. In addition to creating the .dbc file this utility registers the application server with the database for the Applications Server Security feature.
To access additional database servers from the same application server, you must rerun the AdminAppServer utility for each additional database. You must run the AdminAppServer utility each time you create a .dbc file, and each .dbc file only allows access to one database.
To create a .dbc file for an application server:
-
You must set the username/password value for the GUEST_USER_PWD parameter. Create a valid username ("guest", for example) and password in Oracle E-Business Suite. Then use the username/password combination as the value for GUEST_USER_PWD. The syntax is illustrated in the following example:
GUEST_USER_PWD=guest/password
Oracle recommends that you do not assign any responsibilities for this user.
-
From the command line, enter the appropriate command for your platform:
For UNIX platforms:
java oracle.apps.fnd.security.AdminAppServer \ ADD DB_HOST=database_host_name DB_PORT=database_port \ DB_NAME=database_sid \ [env_name=env_value] SECURE_PATH=$FND_TOP/secureFor Windows platforms:
jre -classpath %CLASSPATH% \ oracle.apps.fnd.security.AdminAppServer \ ADD DB_HOST=database_host_name DB_PORT=database_port \ DB_NAME=database_sid \ [env_name=env_value] SECURE_PATH=$FND_TOP/secure
You will be prompted for the APPS username and password using standard I/O.
GWYUID, FNDNAM, and GUEST_USER_PWD will be defaulted if not provided explicitly. dbc files should be located in $FND_TOP/secure, so SECURE_PATH should always be set to that, or this should be run directly out of of the $FND_TOP/secure area.
Updating a .dbc file (or Server ID)
When updating the .dbc file you can change as many parameters as you want, including the server ID, but you must enter at least one. Settings that you do not update retain their value.
To update a .dbc file or server ID:
Enter from the command line:
UNIX
java oracle.apps.fnd.security.AdminAppServer \ UPDATE DBC=$FND_TOP/secure/file.dbc APPL_SERVER_ID \ [env_name=env_value]
Windows
jre -classpath %CLASSPATH% \ oracle.apps.fnd.security.AdminAppServer \ UPDATE DBC=$FND_TOP/secure/file.dbc APPL_SERVER_ID \ [env_name=env_value]
You will be prompted for the APPS username and password using standard I/O.
If APPL_SERVER_ID is not passed, AdminAppServer will attempt to synchronize the current server ID value in the .dbc file and the database, generating a new one if neither contains a value at all. Passing in APPL_SERVER_ID by itself will force a brand new application server ID to be created always, overwriting any existing one.
Deleting a .dbc file
To delete a .dbc file, enter on the command line:
UNIX
java oracle.apps.fnd.security.AdminAppServer \ DELETE DBC=$FND_TOP/secure/file.dbc
Windows
jre -classpath %CLASSPATH% \ oracle.apps.fnd.security.AdminAppServer \ DELETE DBC=$FND_TOP/secure/file.dbc
You will be prompted for the APPS username and password using standard I/O.
This command deletes the .dbc file and disallows access to the indicated database if Server Security is active.
JDBC Parameters
Note that in the DBC files, any line that starts with JDBC\: indicates that there parameters that are passed directly to the JDBC drivers when a connection is opened. You should refer to the JDBC documentation for more information on these parameters and how they are used.
For example,
JDBC\:oracle.jdbc.maxCachedBufferSize
is a parameter used to limit the amount of memory available to the drivers that perform this caching. By default it has been configured to better control the memory used by the drivers to cache results from queries. If this parameter is not set, the JDBC drivers will use all the unused memory on any JVM retaining weak references to available memory.
For more information specifically on memory management in JDBC drivers, refer to the technical reference paper Oracle JDBC Memory Management located at https://www.oracle.com/technetwork/database/enterprise-edition/memory.pdf.
Troubleshooting
The following are possible problems you may encounter and suggested solutions.
-
Database connection failed.
Check to see if your JDBC environment is correct. See: AdminAppServer Utility.
-
File I/O error while adding the server.
Check to see if the path you supplied as SECURE_PATH exists and that you have write permissions on it.
-
Unable to read environment file.
A value for SECURE_PATH may not have been specified. If a value is not specified, the AdminAppServer utility assumes you are running from JAVA_TOP and looks for the file $JAVA_TOP/oracle/apps/env.html to find the value of FND_TOP. Retry the command specifying the value of SECURE_PATH.
-
Database error: Unique constraint violated.
There can be only one entry for each application server per database. If you do not specify the value for SERVER_ADDRESS, the AdminAppServer utility will default the IP address of the machine from which you are running the command. To resolve this issue, run the STATUS command of AdminAppServer to ensure you are not trying to create a duplicate entry. Delete the old entry if you want to replace it. Retry, supplying the correct value for SERVER_ADDRESS.
Administering Server Security
Oracle E-Business Suite is deployed in a multi-tier configuration with one database server and many possible application-tier servers. The application servers can include Apache JSP/Servlet, Forms, other servers, and some client programs such as Application Desktop Integrator. Any program which makes a SQL*Net connection to the Oracle E-Business Suite database needs to be trusted at some level. Oracle E-Business Suite uses the Server Security feature to ensure that such SQL*Net connections are coming from trusted machines and/or trusted programs.
The Server Security feature of Oracle Application Object Library supports authentication of application server machines and code modules in order to access the database. When Server Security is activated, application servers are required to supply server IDs (like passwords) and/or code IDs to access a database server. Server IDs identify the machine from which the connection is originating. Code IDs identify the module and patch level from which the connection is originating. Code IDs are included in applications code by development. The database server can be set to allow access only from specific machines and/or by code at a desired patch level.
The application server security feature is not initially activated. You should activate it by using the commands described in this section.
Application Server Security can be in one of three states:
-
SECURE - Full trust is required for access to the database. Only registered application server machines may connect to the database, and only trusted code modules may connect to the database. This is the default setting for Release 12 and higher.
-
OFF - Server security is not checked. Any application server machine can access the database. Code IDs are also not checked. Use this option on test systems or if you have full control over the software on all machines which can physically access your database.
-
ON - Some level of trust is required to access the database. Either the application server must be registered with the database or the code must pass a module and version ID known to be trusted. Use this option only if you wish to maintain compatibility with application servers that you cannot yet patch to the code level required for best security.
Server Security Status
You can check the Server Security status for a particular database using the STATUS command in the AdminAppServer utility, and providing the dbc file corresponding to that database. The STATUS command will display whether server security is turned on and whether the server ID in the dbc file is currently valid.
To check the Server Security status for a database:
On UNIX:
java oracle.apps.fnd.security.AdminAppServer \
STATUS DBC=<dbc file path>
On Windows:
jre -classpath %CLASSPATH% \
oracle.apps.fnd.security.AdminAppServer \
STATUS DBC=<dbc file path>
You will be prompted for the APPS username and password using standard I/O.
Important: Check the Server Security status of your databases before you activate server security and ensure that all desired application servers have been registered.
Adding, Updating, or Deleting Server IDs
Application servers can be registered as trusted machines with a database server. This works by generating a large random ID number and storing that in both the application server and the database. When the application server attempts to connect to the database it will supply its server ID and the database will verify that it matches a trusted machine. The server ID is stored as a parameter in the DBC file for each application server. It can also be defined as an environment variable. The AdminAppServer utility is used to generate server IDs and then register them with a database server.
To add a server ID
Server ID values are generated by the AdminAppServer utility, and therefore cannot be supplied on the command line. They will be added to the database automatically when the AdminAppServer is used to create a dbc file.
On UNIX:
java oracle.apps.fnd.security.AdminAppServer \ ADD [SECURE_PATH=$FND_TOP/secure] \ DB_HOST=<database host> \ DB_PORT=<database port> \ DB_NAME=<database sid>
On Windows:
jre -classpath %CLASSPATH% \ oracle.apps.fnd.security.AdminAppServer \ ADD [SECURE_PATH=$FND_TOP/secure] \ DB_HOST=<database host> \ DB_PORT=<database port> \ DB_NAME=<database sid>
You will be prompted for the APPS username and password using standard I/O.
To update a server ID
You can update an application server's server ID at any time. From the command line enter:
On UNIX:
java oracle.apps.fnd.security.AdminAppServer \ UPDATE DBC= <dbc file path> APPL_SERVER_ID
On Windows:
jre -classpath %CLASSPATH% \ oracle.apps.fnd.security.AdminAppServer \ UPDATE DBC= <dbc file path> APPL_SERVER_ID
You will be prompted for the APPS username and password using standard I/O.
By providing the APPL_SERVER_ID argument, you will force a new server ID to be generated and added to your DBC file. If the APPL_SERVER_ID argument is not provided, AdminAppServer will take care of syncing up the server ID's of your dbc file and your database automatically, if required.
To delete a server ID
Server IDs can be deleted. This must be done using the AdminAppServer utility as follows:
On UNIX:
java oracle.apps.fnd.security.AdminAppServer \ DELETE DBC= <dbc file path> APPL_SERVER_ID
On Windows:
jre -classpath %CLASSPATH% \ oracle.apps.fnd.security.AdminAppServer \ DELETE DBC= <dbc file path> APPL_SERVER_ID
You will be prompted for the APPS username and password using standard I/O.
Activating Server Security
You can turn the server security feature to OFF, ON, or SECURE mode using the AdminAppServer utility. When you turn off server security, you will not change or delete your server IDs. You can re-enable server security without having to recreate server IDs for existing registered application servers.
On UNIX:
To activate basic server security on UNIX, enter on the command line:
java oracle.apps.fnd.security.AdminAppServer \
AUTHENTICATION ON DBC=<dbc file path>
To activate full server security (SECURE mode) on UNIX, enter:
java oracle.apps.fnd.security.AdminAppServer \
AUTHENTICATION SECURE DBC=<dbc file path>
To deactivate server security on UNIX, enter:
java oracle.apps.fnd.security.AdminAppServer \
AUTHENTICATION OFF DBC=<dbc file path>
You will be prompted for the APPS username and password using standard I/O.
On Windows:
jre -classpath %CLASSPATH% \ oracle.apps.fnd.security.AdminAppServer \ AUTHENTICATION ON DBC=<dbc file path>
To activate full server security (SECURE mode), from the command line, enter:
jre -classpath %CLASSPATH% \
oracle.apps.fnd.security.AdminAppServer \
AUTHENTICATION SECURE DBC=<dbc file path>
To deactivate server security, from the command line, enter:
jre -classpath %CLASSPATH% \
oracle.apps.fnd.security.AdminAppServer \
AUTHENTICATION OFF DBC=<dbc file path>
You will be prompted for the APPS username and password using standard I/O.
Restricting Access to Responsibilities Based on User's Web Server
Oracle E-Business Suite has the capability to restrict access to a responsibility based upon the Web server from which the user logs in. This capability is provided by tagging Web servers with a "server trust level."
The server trust level indicates the level of trust associated with the Web server. Currently, three trust levels are supported: 1) administrative, 2) normal, and 3) external. Web servers marked as "administrative" are typically those used exclusively by system administrators. These servers are considered secure and may access restricted responsibilities and information. Servers marked as "normal" are those used by employees within a company's firewall. Users logging in from normal servers have access to only a limited set of responsibilities. Lastly, servers marked as "external" are those used by customers or employees outside of a company's firewall. These servers have access to an even smaller set of responsibilities.
Setting the Server Trust Level for a Server
To assign a trust level to a Web server, set the Node Trust Level profile option. The Node Trust Level profile option uses the Server profile hierarchy type, meaning that the value of the profile depends on the particular application-tier server accessing the profile. This profile option can be set to either 1, 2, or 3, with the following meanings:
-
1 - Administrative
-
2 - Normal
-
3 - External
To avoid having to set the Node Trust Level profile option for every Web server, you may wish to set it to a default level of trust at the site level. Oracle recommends that the Node Trust Level profile option be set at the site level to provide a default trust level; specifically set the profile at the site level to ‘2-Normal’ and externally-facing (DMZ) nodes to ‘3-External’ at the server level.
Restricting Access to a Responsibility
To restrict access to a responsibility, set the security-based Responsibility Trust Level (internal name APPL_SERVER_TRUST_LEVEL) profile option value for that responsibility to be the number 1, 2, or 3. Setting this profile value ensures that only Web servers with the same or greater privileged trust level may access that responsibility.
The default value for the Responsibility Trust Level is 1.
When fetching the list of valid responsibilities for a user, Oracle E-Business Suite checks to find only responsibilities with a Responsibility Trust Level value greater than or equal to the Web server's Node Trust Level. In this way, a responsibility with Responsibility Trust Level set to 1 would only be available if the Web server has the Node Trust Level set to 1 as well. A responsibility with Responsibility Trust Level set to 2 would only be available if the Web server has Node Trust Level set to either 1 or 2.
Oracle Application Object Library AOL/J Setup Test Suite
The AOL/J Setup Test Suite consists of Java Server Pages (JSPs) and can be used to diagnose AOL/J setup issues. These JSPs exercise various features of AOL/J and provide feedback on the results. The test suite is accessed from the URL:
http://<host_name>:<port_number>/OA_HTML/jsp/fnd/aoljtest.jsp
where host_name and port_number correspond to the host name and port number of your instance's Apache listener. The host name and port number values are normally found in the APPS_SERVLET_AGENT profile option.
When you access the test suite, you will be asked to provide login information for your instance:
-
Applications Schema Name
-
Applications Schema Password
-
TWO_TASK
-
Host Name
-
Port Number
The following is a list of functions and tests you can run with your instance.
-
Connection Test
-
Locate DBC File
-
Verify DBC Settings
-
AOL/J Connection Test
-
-
Virtual Directory settings
-
APPS_WEB_AGENT
-
Virtual Directory Settings
-
FND_WEB.PING
-
Custom Authentication
-
GFM (Generic File Manager)
-
-
APPS_SERVLET_AGENT
-
Virtual Directory Settings
-
Servlet Ping
-
Jsp Ping
-
-
APPS_FRAMEWORK_AGENT
-
Virtual Directory Settings
-
Servlet Ping
-
Jsp Ping
-
Cabo Setup Tests
-
X Server Accessibility
-
OA Framework System Info
-
Versions for Loaded Classes
-
-
HELP_WEB_AGENT
-
TCF
-
Test Connection
-
-
Tool Launcher Profile Settings
-
ICX_FORMS_LAUNCHER
-
ICX_REPORT_LAUNCHER
-
ICX_DISCOVERER_LAUNCHER
Additional Information: See also Oracle E-Business Suite Support Implications for Discoverer 11gR1, My Oracle Support Knowledge Document Doc ID 2277369.1.
-
-
Application Login
-
Login Page
-
Show Responsibilities
-
Show Session Properties
-
Configuring the Login Page for Oracle E-Business Suite
Oracle E-Business Suite uses a configurable login page, which can be tailored to suit the needs of different organizations.
Oracle E-Business Suite Login page
Users log in to Oracle E-Business Suite using a client web browser. From the Oracle E-Business Suite Login page, users access the Oracle E-Business Suite Home Page, which provides a single point of access to HTML-based applications and forms-based applications. Users access the Oracle E-Business Suite Login page from the following URL:
http://<server:port>/OA_HTML/AppsLogin
For example,
http://example.com:8000/OA_HTML/AppsLogin
From this URL, you will be redirected to the central login page, "AppsLocalLogin.jsp".
Central Login Page
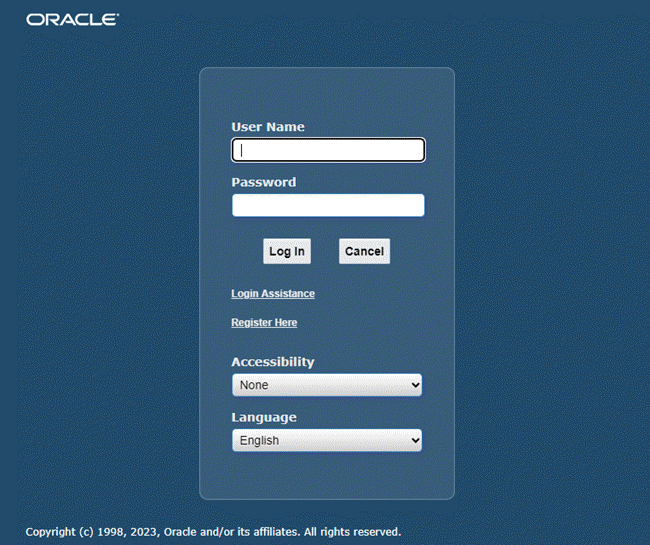
The following features are displayed in the default login page: Username field, Password field, Login button, Accessibility drop-down list, and the Language drop-down list (if more than one language is installed).
The ICX login page (http://server:port/OA_HTML/US/ICXINDEX.htm) redirects the user to the central login page, "AppsLocalLogin.jsp". If, in a previous release, you customized the ICX login page previously with a custom logo, you should make a copy of the new ICX login page and replace the existing image with your custom image in the copied file. The location for the company logo is $OA_MEDIA/FNDSSOCORP.gif. Ensure that the image is appropriately sized. Also, you should change the text of the message 'FND_ORACLE_LOGO' in Message Dictionary to the appropriate text. The following login URL is supported, but no new features are being added to it:
http://server:port/OA_HTML/jtflogin.jsp
If the Oracle E-Business Suite instance is Single Sign-On enabled, the servlet directs the user to the Single Sign-On login page.
Passwords
Note that in previous releases of Oracle E-Business Suite, user passwords were treated as case insensitive. Now, Oracle E-Business Suite user passwords can optionally be treated as case sensitive, depending on the mode you choose. Case-sensitivity in passwords is controlled by the profile option Password Case Option.
Language
The current browser language, if it exists in the applications database also, is used for the login page. The user can choose a different language on the login page (if the Language drop-down list is enabled) and refresh the page to have it appear in that language.
If the current browser language does not exist in the Oracle E-Business Suite installation, the language set in the site-level setting of the ICX_LANGUAGE profile option is used to render the login page.
A user can override the value of the ICX_LANGUAGE profile option for a given session only.
Oracle Applications Manager
Oracle Applications Manager uses this central login page as well to authenticate users.
Configuration for Oracle Application Framework Features
Oracle Application Framework is an Oracle E-Business Suite development and deployment platform. It is a 100% Java and XML, application-tier framework and services for the rapid development and deployment of HTML-based applications. This section describes the setup of some of its features.
Home Page
Beginning with Release 12.2.4, you have the option of displaying one of three possible Home page styles:
-
Simple Home page (new in Release 12.2.4)
-
Configurable Home page with tree-based Navigator
-
Home page with flat list Navigator
For information on how to set the Oracle Application Framework Home page style, refer to the Oracle Application Framework Developer's Guide, available from My Oracle Support Knowledge Document 1315485.1.
List Search
List Search is a sophisticated search tool that helps users quickly and easily retrieve information. Oracle Application Framework implements List Search on top of an existing Query Bean component.
Note: The List Search feature, as well as its individual capabilities, must be implemented within a specific page or application before it can be enabled for that page or application.
To implement list search on a page, a developer must turn on the property 'Enable List Search' for a specific query bean within the page. This query bean property is personalizable.
Administrators can enable list search for the pages where it has been implemented by setting the FND: Enable List Search (code FND_ENABLE_LIST_SEARCH) profile option to "True". This profile can be enabled at all levels: Site, Application, Responsibility, and User. Users cannot see or update this profile option.
List Search has two optional capabilities controlled by the profile option FND: Enable Quick Search for Query Beans (code FND_ENABLE_QUICK_SEARCH_QUERYBEANS; the default value is "True"):
-
Quick Search allows users to search quickly on a single field in List Search mode without opening the filters area.
-
Keyword Search allows users to search by keywords.
For pages with tiles (also called infotiles), the profile option FND: Enable Infotile View for Query Beans (code FND_ENABLE_INFOTILEVIEW_QUERYBEANS; the default value is "True") allows for saved searches to appear in the Infotile view with the total count of records matching the search criteria and the respective saved search name.
List Search has been selectively implemented across Oracle E-Business Suite products and product families, with an emphasis to improve user productivity on pages with high user interaction on key business transactions. Products using List Search include:
| Product | Pages |
|---|---|
| Installed Base | Transaction Interface Search |
| Inventory | Search Reservations |
| iProcurement | iProcurement Catalog Administration: Agreements |
| Lease and Finance Management | Contracts Funding Requests Manual Receipts Accounting Transactions Asset Return Requests Termination Quotes Manual Invoices Vendor Re-assignment Prefund Pool Investor Agreements Remarket Orders Invoices |
| Manufacturing Execution System for Discrete Manufacturing | MES Supervisor: Work Orders and Exceptions |
| Order Management | Orders |
| Project Costing | Expenditure Inquiry |
| Project Foundation | Project List Add Projects Project Requests |
| Project Management | Change Orders Change Requests Project Issues Deliverables Tasks Financial Tasks |
| Purchasing | Buyer Work Center |
| Shipping Execution | Shipping Operations |
| Sourcing | Demand Workbench |
For more information on using List Search, see: Querying and Viewing Data, Oracle E-Business Suite User's Guide.
For more information on enabling List Search and related features, refer to the Oracle Application Framework Developer's Guide, available from My Oracle Support Knowledge Document 1315485.1, and Oracle Application Framework Profile Options, My Oracle Support Knowledge Document 1315510.1.
For more information on personalization, see the Oracle Application Framework Personalization Guide.
Default Favorites
You can specify functions as Default Favorites. These default favorites appear as suggestions to the user through the Add Favorites icon on the Simple Home page.
To define Default Favorites, perform these steps:
-
Log in as a user with the Functional Administrator responsibility.
-
Navigate to Personalization, then Favorites.
-
In the Manage Default Favorites page, search for the desired function(s).
-
From the search results table, select a function or functions and click Add to Default Favorites.
-
Click Save to save your work and see these Favorites reflected in the suggestion window for the user.
-
Alternatively, click Apply to add these functions to users' Favorites lists directly.
Users can manage their favorite functions with these steps:
-
From the Simple Home page, click on the Add Favorites icon.
-
The Add Favorites window is shown with the following:
-
Suggested Favorites: contains suggested functions defined by an administrator (if any)
-
Popular Favorites: contains the top bookmarked functions of other users
-
-
Click on the Manage Favorites link to navigate to the traditional Manage Favorites page.
Attachments
This section describes features specific to attachments in Oracle Application Framework.
Inline Attachments
The default behavior for attachments in Oracle Application Framework pages is the use of Inline Attachments. The Inline Attachments feature allows a user to add or view attachments by hovering the mouse over an icon, button, or link. The alternate behavior is opening a separate Attachments window.
To enable the Inline Attachments feature, set the profile option FND: Disable Inline Attachments to "false" at the Site or Application level. The default value at the Site level is "false". You can also set the Inline Attachment Enabled property of your attachment region item to enable or disable the Inline Attachments feature for that particular attachment item. Valid values for the Inline Attachment Enabled property are "true", "false", or "default", where "default" means to default to the value set in the FND: Disable Inline Attachments profile option. Users may also personalize the Inline Attachment Enabled property at runtime.
The following table illustrates Inline Attachments behavior for the different combinations of values set for the profile option and the attachment item property.
| Value of 'Inline Attachment Enabled' property | Value of "FND: Disable Inline Attachments" profile option | End User Experience |
|---|---|---|
| Default | False | Mouse-click/Tap/Focus+Enter key: Inline Attachment pop-up appears. No other interaction is supported. |
| Default | True | Mouse-click/Tap/Focus+Enter key: Attachment page appears. No other interaction is supported. |
| True | False | Mouse-click/Tap/Focus+Enter key: Inline Attachment pop-up appears. No other interaction is supported. |
| True | True | Mouse-click/Tap/Focus+Enter key: Inline Attachment pop-up appears. No other interaction is supported. |
| False | False | Mouse-click/Tap/Focus+Enter key: Attachment page appears. |
| False | True | Mouse-click/Tap/Focus+Enter key: Attachment page appears. |
For more information on setting the "Inline Attachment Enabled" property, refer to the Oracle Application Framework Developer's Guide, available from My Oracle Support Knowledge Document 1315485.1. For more information on the "FND: Disable Inline Attachments" profile, refer to Oracle Application Framework Profile Options, My Oracle Support Knowledge Document 1315510.1.
Printing File-type Attachments with Autovue Document Print Service
The AutoVue Document Print Service feature can be used to print attachments of the type File. To enable this feature, the profile FND Attachment AutoVue Server (FND_AUTOVUE_SERVER) must be set to AutoVue web service's endpoint URL, in the form http://<host>:<port>/AutoVueWS/VueBeanWS.
With Release 12.2.6, Oracle E-Business Suite integration with AutoVue Document Print Service is certified only with Oracle Autovue Release 20.2.3.
Once the FND Attachment AutoVue Server profile is set, the following appears in the UI for Attachments:
-
In the Attachments page, a print column will be displayed in the Attachments table. This icon will be enabled only for File- type attachments and disabled for Text and URL type attachments.
-
Clicking on the Print icon shall invoke the Print Attachment window, in which the user can choose a printer from the list of available printers, choose the paper size from the list of available paper sizes, and specify the print orientation as portrait or landscape.
-
An error message is displayed if the web service could not be invoked to fetch the list of printers and paper sizes.
-
Clicking on Print button shall print the file with the selected setting. A processing icon shall be rendered while printing when invoked from the Attachment List popup.
Note: A user can only select the Print Attachment icon when the file-type attachment is committed to the database. If the Automatic Save property of an attachment region item is set to False, a user must explicitly commit the transaction of any newly-added file attachments before the user can print those attachments.
Note: For additional information about Oracle AutoVue, refer to the AutoVue Documentation Library.
URL-Type Attachment Validation
Set the profile option FND Attachment URL Validation (FND_ATTACHMENT_URL_VALIDATION) to enable the validation of URL-type attachments. Since URL-type attachments may point to external sites, this profile option allows you to enable a check to validate whether the URL is "safe". If the URL is not "safe", a confirmation dialog page appears ("You are being redirected to an external web page <URL>. Do you want to continue?"), prompting the user to review the URL before redirecting to the external site with an affirmative action.
This profile can be set at the Site level only. Valid values include:
-
Warn - validates whether the selected URL-type attachment is a "safe" URL and if it is, displays a warning message to the user and prompts the user before continuing.
-
None - does not validate the selected URL-type attachment and redirects immediately to the URL site.
For more information on this profile, refer to Oracle Application Framework Profile Options, My Oracle Support Knowledge Document 1315510.1.
Exporting Tables
Many tables allow you to export their data from the browser to PDF or Microsoft Excel. Only columns that are enabled or displayed by the user are exported.
This feature can be controlled at site level through the profile FND: Enable BNE Table Integration (code FND_ENABLE_BNE_TABLE_INTEGRATION). This profile is by default set to "False" and can be set at all levels.
Some tables do not support exporting to PDF or Excel. These include:
-
Tables rendered in the email facet.
-
Tables rendered in printable pages.
-
Inner Tables (table-in-table).
-
Tables in pages running in embedded mode, such as tables inside a JTT skin.
-
Tables in pages running in portlet mode.
-
List of Values (LOV) table web beans.
-
Attachment tables.
-
Tables whose view object is "dirty" at the time. Dirty view objects indicate ongoing transactions and export will be disabled.
-
Tables whose view object does not have any WHERE clause or WHERE clause parameters.
-
Tables whose view object binding style is not Oracle Positional (in which parameters are represented as colons followed by numbers).
For more information on the above characteristics, see: Oracle Application Framework Developer's Guide, available from My Oracle Support Document 1315485.1.
Be aware of the following points about exporting tables:
-
Oracle Application Framework will export records up to the limit controlled by the profile FND: View Object Max Fetch Size (code VO_MAX_FETCH_SIZE). There is currently no option to export all rows.
-
In addition, tables can be exported to Microsoft Excel only where the operating system is Windows. Export to Microsoft Excel is based on Web Applications Desktop Integrator, which requires Windows.
-
Every exported PDF document carries the same corporate branding image as the base page by default. If you want to apply a different corporate branding image, then set the profile option "FND: Export to PDF Corporate branding image location" (code FND_EXPORT_TO_PDF_CORP_BRANDING_IMG_LOC) to point to the file name of the image under the
$OA_MEDIAdirectory. -
Users can choose the font size to be used to render the PDF content. The default size is 10.
-
For Guest users, it is recommended that the profile FND_ENABLE_BNE_TABLE_INTEGRATION be turned off.
Using Semicolon as an Alternative CSV Separator
When exporting data using the Export button, the generated .csv file by default uses the comma as a field separator. However, in some locales, the expected .csv separator is the semicolon. Beginning with Release 12.2.11, you can use the semicolon as the CSV separator by setting the profile option "FND: Export CSV Separator" (code FND_EXPORT_CSV_SEPARATOR) to a value of 'semicolon'. (The other allowed value is 'comma', which as noted above is the default.) Note that this choice of CSV separator is only available for an Export button that is created explicitly, and not for the export option that is a part of Advanced Table. The .csv file is generated with the separator chosen as described above, and each field in the .csv file is enclosed within double quotes (" "). This means that the semicolon separator can appear in the table data without causing any problems.
Note: The changes applies only to the MIME datatype: text/comma-separated-values, and nesting of double quotes (" ") within the table data are not supported.
Setting Up Saved Search Notifications
Users can be notified of updates for their saved search results in email. The following functions are possible:
-
Users can get reports of their saved search results based on a schedule.
-
Users can be notified on row insert events on the saved search results.
-
Users can be notified when the record count goes beyond a threshold set for tracking purposes.
Administrators can monitor all such notification requests and take action in case of issues.
Steps to Enable the Notification Feature
-
First, the List Search feature must be enabled.
-
A search page with List Search enabled must be set up.
-
The Infotile (tile) feature is turned on with List Search
-
-
Set the profile FND: Enable Saved Search Notifications (code FND_ENABLE_SAVED_SEARCH_NOTIFICATIONS) to 'True'. By default, this profile is set to 'True'.
-
Set up an active SMTP server configuration if one is not set up already. Refer to Setting Up Notification Mailers, Oracle Workflow Administrator's Guide for more information.
-
Ensure that the end user has an active email ID. Refer to Registering User Accounts, Oracle E-Business Suite Security Guide for more information. Alternatively, for users originating from Oracle HRMS, refer to the Oracle HRMS documentation for details how to enter an email ID for a user.
-
Oracle Application Framework uses the predefined role with code FND_SAVED_SEARCH_NOTIFICATIONS. Assign this role to users in Oracle User Management. See: Registering User Accounts, Oracle E-Business Suite Security Guide.
Once the steps to enable notification for a user is done, the user can navigate to any search page with list search and infotile enabled to set up their specific notification preferences.
To do so, a user should:
-
Click Manage Saved Searches from the Saved Search list. This will open the Manage Saved Search dialog.
-
Click on the Notification icon in the last column. The Notification form opens.
-
There are 3 kind of notifications that user can subscribe to.
-
Option 1: Report of all records. Choose
Type = All RowsWhen subscribed with a start date/end date and repeat unit/interval, this kind of notification sends a report of all rows matching that criteria at the time of running the report. The user can choose the columns to be displayed in the report. This could be a subset of columns displayed in the table. Additionally, a user can get a bar chart as an attachment in the email. The bar chart can work on a maximum of two attributes.
-
Option 2: When new records added. Choose
Type = Rows InsertedWhen subscribed with a start date/end date and repeat unit/interval, this kind of notification sends a report of all rows that are inserted since the previous time the job ran. The user can choose the columns to be displayed in the report. This could be a subset of columns displayed in the table.
-
Option 3: When record count exceeds a set threshold value. Choose
Type = Threshold ExceededWhen subscribed with a start date/end date and repeat unit/interval, this kind of notification sends a report of all rows when the count of records exceed the set threshold by the user. The user can choose the columns to be displayed in the report. This could be a subset of columns displayed in the table.
-
Administrative Options
The following tasks can be done by system administrators.
Monitoring Saved Search Notifications
System administrators can monitor the saved search notifications requested by each user through an administration page, available from the Functional Administrator responsibility. Navigate to Personalization, and then Notifications.
Concurrent Manager Tuning
Oracle Application Framework uses a concurrent program (OA_SAVED_SEARCH_ALERTS_CP) to run each of the repeating saved search notification jobs. The concurrent manager OAF_CP_MGR runs this concurrent program with a cache size of 3 and can run only one request at a time. If there are more users for whom this feature is enabled then administrators could tune these parameters to suit their specific environment needs.
Email Customization
Customize the "From:" address and mail subject for notification emails by updating the following in Message Dictionary:
| Email Option | Message Code |
|---|---|
| Email Subject | FND_OA_ALERT_EMAIL_SUBJECT |
| Email "From" Address | FND_OA_ALERT_EMAIL_FROM_ADDR |
For more information, refer to: Message Dictionary, Oracle E-Business Suite Developer's Guide.
Simplified Table Toolbar
Beginning with Release 12.2.9, table actions and settings Refresh, Detach, Columns, Freeze, and Reset are consolidated and all displayed under the Actions menu button in the control bar which looks like an ellipsis (three dots, or '...').
A system administrator can set the FND: Enable Simplified Table Control Bar (code FND_ENABLE_SIMPLIFIED_TABLE_CONTROL_BAR) profile option to "False" to display the menu choices in the toolbar itself. This profile option can be set at the Site, Responsibility, or User level. By default, it is set to "True".
Instance Name
You can set the profile option FND: Show Instance Name (code FND_SHOW_INSTANCE_NAME) to 'True' to display the instance name on the home page for a specified user. By default this profile option can be set at the User level only. Users can also see and update this profile option.
Disabling Access Keys
End users have the option of disabling the access keys in all the accessibility modes using the Disable Access Keys checkbox in the Preferences page with name Disable Access Keys. When the box is checked, access keys will be disabled and when it is unchecked access keys are enabled for that user. By default the checkbox is unchecked.
Access keys can also be controlled through the profile option FND:Disable Access Keys (FND_DISABLE_ACCESS_KEYS). Valid values are:
-
Yes - Access keys are disabled in all the pages regardless of the accessibility mode.
-
No - Access keys are enabled in all the pages regardless of the accessibility mode.
The default value of this profile is "No".
The user setting in the Preferences page overrides the profile value setting.
Additional Selected Profile Options
Other user interface features are controlled by the profile options listed in the table below.
Refer to the Oracle E-Business Suite User's Guide and Oracle Application Framework Profile Options, My Oracle Support Knowledge Document 1315510.1, for more information on these and other features.
| Feature | Profile Option | Profile Option Values | Default Value on Site Level |
|---|---|---|---|
| Configurable Home Page | FND: Disable Configurable Home Page | True, False | False |
| Slideout Menu for Navigator and Favorites | FND: Disable Navigator and Favorites Rich Menu | True, False | False |
| Inline Attachments | FND: Disable Inline Attachments | True, False | False |
| Look-ahead LOV | FND: Disable Look Ahead LOV | True, False | False |
| Look Ahead in Search field for Navigator Menu | FND: Minimum Characters for Look Ahead | [Integer value] | 3 |
| AutoVue Document Print Service for File-type Attachments | FND Attachment AutoVue Server | AutoVue web service's endpoint URL | NULL |
| Number of Open Notifications Shown in Home Page | Sign-On:Notification | Yes, No | No |
| Disabling Access Keys in All Accessibility Modes | FND:Disable Access Keys | Yes, No | No |
| Top-Level Menu Display Style | FND: Top-Level Menu Display Mode | Links Only, Icons and Links, Icons and Links on Tablets Only | Links Only |
| Partial Page Rendering (PPR) Lockout Time | FND: PPR Lockout Time | [An integer value, specifying a duration in milliseconds] | 8000 |
The following profiles are retained for backward compatibility with Release 12.1.2:
-
Enable Configurable Homepage (FND_CONFIG_HOMEPAGE_ENABLED).
-
FND Slideout Menu (FND_SLIDEOUT_MENU)
To disable the Navigator and Favorites menus, the profile values should be set as follows:
-
FND Slideout Menu (FND_SLIDEOUT_MENU) = 'Disabled'. This profile provides backward compatibility with Release 12.1.2.
-
FND: Disable Navigator and Favorites Rich Menu (FND_DISABLE_NAVIGATOR_AND_FAVORITES_RICH_MENU) = "True"
Related Topics
Oracle Application Framework Developer's Guide, available from My Oracle Support Knowledge Document 1315485.1
Oracle Application Framework Profile Options, available from My Oracle Support Knowledge Document 1315510.1
OA Extension Component Reference, available from My Oracle Support Knowledge Document 1315505.1
Internet Content Adaptation Protocol (ICAP) Antivirus Software Configuration
Internet Content Adaption Protocol (ICAP) is a lightweight HTTP-like protocol specified in RFC 3507 which is used to extend transparent proxy servers. ICAP can be used for virus scanning and content filters in transparent HTTP proxy caches.
Oracle E-Business Suite Release 12.2 can scan attached and uploaded files when integrated with third-party antivirus software that supports ICAP. Oracle E-Business Suite Release 12.2 ICAP antivirus scanning integration with third-party antivirus servers is available for the following:
-
Oracle Application Framework attachments (both inline and page mode)
-
Forms attachments
-
File uploads
To enable, set the values for the three profile options described in the table below.
| Profile | Valid Values | Description |
|---|---|---|
| FND: Disable Virus Scan (internal code: FND_DISABLE_VIRUS_SCAN) |
|
To enable virus scanning, set this profile value to 'No'. To disable virus scanning, set this profile value to 'Yes'. |
| FND Attachment Antivirus Software Type (internal code: FND_ANTIVIRUS_SOFTWARE) |
|
Enter a value for the antivirus server you wish to configure. |
| FND Attachment Antivirus Server (internal code: FND_ANTIVIRUS_SERVER) | The parameters to configure a connection to the antivirus software. For example, icap.example.com:1344:avscanIf the FND_ANTIVIRUS_SOFTWARE profile is set to "ICAP", then enter <domain name>:<port>:<ICAP service name> for this profile. If the ICAP server is configured with Transport Layer Security (TLS) and uses a certificate issued by a generally trusted CA, then enter <domain name>:<port>:<ICAP service name>:SSL for this profile. If the ICAP server is configured with a certificate issued by a Private CA, then enter <domain name>:<port>:<ICAP service name>:SSL:<truststore location> for this profile. See Additional Configuration for a TLS-Enabled ICAP server for more details. |
This profile value is used to configure the domain name or IP address, port number, and service name to connect to the antivirus software. Enter each one of these values separated by a colon.
If the ICAP server is configured with TLS, enter the abbreviation "SSL" after a colon. Optionally, you might need to specify the truststore location of the ICAP server. See Additional Configuration for a TLS-Enabled ICAP server for more details. |
Configuration Examples
The following table is a list of example settings for the profiles to enable the integration of Oracle E-Business Suite Release 12.2 with an ICAP antivirus scanning server.
| Example | FND_DISABLE_VIRUS_SCAN | FND_ANTIVIRUS_SOFTWARE | FND_ANTIVIRUS_SERVER | Scanning Request Handled By |
|---|---|---|---|---|
| 1 | Yes | None | N/A | No virus scanning. |
| 2 | No | SYMANTEC | <Domain Name>:<Port> | Symantec Virus Scanning Server. |
| 3 | No | ICAP | <Domain Name>:<Port>:<Service Name> | An ICAP server without SSL. |
| 4 | No | ICAP | <Domain Name>:<Port>:<Service Name>:SSL | An ICAP server with an SSL endpoint; Java's default truststore is used. |
| 5 | No | ICAP | <Domain Name>:<Port>:<Service Name>:SSL:<Truststore Location> | An ICAP server with an SSL endpoint; a custom truststore is used |
Additional Configuration for a TLS-Enabled ICAP Server
If your ICAP server is SSL/TLS enabled, then the Oracle E-Business Suite ICAP client must trust the certificate chain configured on the ICAP server. Scenarios in which this is the case are described below.
-
If the ICAP server is configured with a certificate issued by a generally trusted CA, then use Java's default truststore; that is, do not specify the <Truststore Location>.
-
If the ICAP server is configured with a certificate issued by a Private CA, you have two options:
-
Import the Private CA's root certificate into a new ICAP-only truststore and specify the <Truststore Location> in the FND_ANTIVIRUS_SERVER profile option value.
It is recommended that you use a new, ICAP-only truststore for Private CA roots. This avoids having to re-import the Private CA root following each quarterly Java update, you can place the ICAP truststore in the non-editioned filesystem
fs_ne. -
Import the Private CA's root certificate into Java's default truststore and do not specify the <Truststore Location>.
If you wish to add to Java's default truststore it is located at OACORE's JAVA_HOME
$COMMON_TOP/util/jdk64/jre/lib/security/cacerts. This JAVA_HOME exists in both the run and the patch filesystems so you must ensure your addition is present in both.If you must import a Private CA root certificate to a Java Keystore file (JKS), use the keytool command as shown below:
On UNIX and Windows:
$ keytool -import -keystore <name-of-keystore-file> -alias icap-server -file <name-of-root-CA-certificate-file>
-
AutoConfig and Oracle Applications Manager
Oracle Applications Manager (OAM) provides access to the AutoConfig configuration management tool via the AutoConfig tab in the Site Manager screen. Previous configuration settings can easily be compared with the current settings, allowing changed settings to be identified and rolled back as necessary. The configuration editor also helps you add custom variables to the context files, to allow AutoConfig and AutoPatch to preserve your system configuration customizations.
For more information on AutoConfig, see: Using AutoConfig to Manage Oracle E-Business Suite Services and Using AutoConfig Tools for System Configuration.
For more information on Oracle Applications Manager, see: Introduction to Oracle Applications Manager.
From the Oracle Applications Manager Site Map, AutoConfig is on the Administration tab under the System Configuration heading. Click on the AutoConfig link to go to the tool's home page.
From the AutoConfig home page, you can view details of a context file by clicking Show. For example, you can see Version, Path, Creation Date. Last Updated By, Status (for example, Write succeeded), and Comments.
You can select a context file and choose Edit Parameters. This is the only supported way to modify parameters that AutoConfig maintains: if you edit any context files manually, they will be overwritten the next time AutoConfig is run.
Under Edit Parameters, choosing the Local tab will open a screen that shows environment-related details, including local host machine name, virtual hostname (used to connect), local domain name, and platform type.
You can select a context file and click on Show History, to see details of any previous configurations.
The Custom tab under Edit Parameters allows you to add a new context variable (not maintained by AutoConfig) to the context file. This is the only supported way to add customizations.
Related Topics
Language Rule Determination
This feature, introduced in Release 12.2.6, provides greater flexibility for configuring the language rule in determining what language to use in an Oracle E-Business Suite session. A new language rule is introduced, which contains a comma-separated list of language sources and establishes the order of precedence for determining which language should be used. This option can be set using the FND_SESSION_MANAGEMENT APIs setLanguageRule and sameLanguageRuleForAll. Note that you should use only the FND_SESSION_MANAGE package to set and retrieve the language rule.
Possible language sources are:
-
DISPLAY: Use the language displayed in the login page.
-
USER_SESSION: Use the current session language, except when the user is GUEST.
-
LANG_PARAMETER: Use the value of the URL parameter langCode or lang_code.
-
BROWSER: From the list of browser preferred languages, use the first language installed in Oracle E-Business Suite.
-
PROFILE: Use a value from the ICX_LANGUAGE profile option, either the user level value, if found, or the server or site value.
-
SESSION: Use the current session language for a USER or GUEST session.
-
BASE: Explicitly force the BASE language.
The default language rule is: DISPLAY, USER_SESSION, LANG_PARAMETER, BROWSER, PROFILE, SESSION, BASE.
The language rule could be set as in the following examples:
SQL> exec FND_SESSION_MANAGEMENT.setLanguageRule('DISPLAY,USER_SESSION,LANG_PARAMETER,BROWSER,PROFILE,SESSION,BASE');
SQL> exec FND_SESSION_MANAGEMENT.setLanguageRule('DISPLAY,LANG_PARAMETER,SESSION,BROWSER,PROFILE,SESSION,BASE','SERVER',3208);
SQL> BEGIN
1> FND_SESSION_MANAGEMENT.sameLanguageRuleForAll(FALSE);
2> FND_SESSION_MANAGEMENT.setLanguageRule('PROFILE,BASE','USER','OPERATIONS');
END:
/
You can retrieve the Site-level default rule with the following command:
select fnd_session_management.getLanguageRule from dual;
Note: You should use only the FND_SESSION_MANAGEMENT package to set and retrieve the language rule.
FND_SESSION_MANAGEMENT.sameLanguageRuleForAll API
Determines whether the same language rule is used for all levels. If no parameter or null is passed, then the current setting is returned.
function FND_SESSION_MANAGEMENT.sameLanguageRuleForAll return BOOLEAN;
This function takes as a parameter:
-
option: BOOLEAN default null
FND_SESSION_MANAGEMENT.setLanguageRule API
Sets the language rule.
The USER level is ignored unless FND_SESSION_MANAGEMENT.sameLanguageRuleForAll is FALSE.
procedure FND_SESSION_MANAGEMENT.setLanguageRule;
This procedure takes as parameters:
-
rule: Rule to be set.
-
level: SITE, SERVER, or USER. The default is 'SITE'.
-
level_value_name: The server or the user name. The default is null.
FND_SESSION_MANAGEMENT.getLanguageRule API
Gets the language rule for the specified level.
fnd_session_management.getLanguageRule(level, level_value_name)
This API takes as parameters:
-
level: SITE, SERVER, or USER. The default is 'SITE'.
-
level_value_name: Can be server_name (from fnd_nodes) and user_name (from fnd_user)
Setup for Accessibility Features
Refer to the following documents for more information on setting up and using Oracle E-Business Suite accessibility features:
-
Oracle E-Business Suite Accessibility Features, Oracle E-Business Suite User's Guide
-
Oracle Application Framework Developer's Guide available from My Oracle Support Knowledge Document 1315485.1
User Desktop Setup
Refer to the following documents for information on setting up hardware and software on users' desktop clients for use with Oracle E-Business Suite:
-
"Oracle E-Business Suite Desktop Client Hardware and Software Requirements," My Oracle Support Document 1155883.1
-
"Recommended Browsers for Oracle E-Business Suite Release 12," My Oracle Support Document 389422.1
-
"Microsoft Office Integration with Oracle E-Business Suite 11i and R12," My Oracle Support Document 1077728.1