Oracle Contract Lifecycle Management for Public Sector Command Center Setup
This chapter covers the following topics:
- Setting Up CLM Command Center
- Setup and Configuration Steps for CLM Command Center
- Setting Profile Options for CLM Command Center
- Loading CLM Procurement Data
- Reviewing Security Rules and Document-Level Security for CLM Procurement Documents
Contract Lifecycle Management for Public Sector Command Center Configuration
Setting Up CLM Command Center
See Contract Lifecycle Management (CLM) for Public Sector Command Center Overview, Oracle Contract Lifecycle Management for Public Sector Purchasing User Guide.
The CLM Command Center configuration setup must be completed after the installation and common configurations are completed as described in My Oracle Support Knowledge Document 2495053.1, Installing Oracle Enterprise Command Center Framework, 12.2.
See Setup and Configuration Steps for CLM Command Center.
Setup and Configuration Steps for CLM Command Center
See Contract Lifecycle Management (CLM) for Public Sector Command Center Overview, Oracle Contract Lifecycle Management for Public Sector Purchasing User Guide.
To complete setup of the CLM Command Center:
-
Grant the PO ECC Perform Deobligation Role to the required contracting officer users to perform the "Deobligate" action that is available from the Awards dashboard, Funding tab. See CO Awards Dashboard, Oracle Contract Lifecycle Management for Public Sector Purchasing User Guide.
Setting Profile Options for CLM Command Center
See Contract Lifecycle Management (CLM) for Public Sector Command Center Overview, Oracle Contract Lifecycle Management for Public Sector Purchasing User Guide and Setup and Configuration Steps for CLM Command Center.
Set a value for the profile options to specify how CLM Command Center controls processes data.
| Profile Option Name | Description | Default Value |
|---|---|---|
| PO CLM Dashboard Data Load Cut-off date (YYYY/MM/DD) | Determines the date from which transactional data is extracted and loaded to the CLM Command Center. If you do not set the profile value, then all the records in the metadata are extracted when you run the PO CLM ECC Data Load program with the Full Load option. For federal agencies, the fiscal year begins from 01-October. Therefore, if a value is not set for the profile option, then the program extracts data for the current fiscal year and the previous fiscal year. Important: For correct display of the metrics data on the Requisitions dashboards for PMO managers and contracting officers, you must set a value for the profile option. |
No default value |
Loading CLM Procurement Data
See Contract Lifecycle Management (CLM) for Public Sector Command Center Overview, Oracle Contract Lifecycle Management for Public Sector Purchasing User Guide and Setup and Configuration Steps for CLM Command Center.
To process the data from Oracle E-Business Suite to CLM Command Center, run the PO CLM ECC Data Load concurrent request. This program is available under the following menu:
CLM Purchasing Super User responsibility > Reports > Schedule Requests
Run the concurrent program from the Schedule Request: Define page.
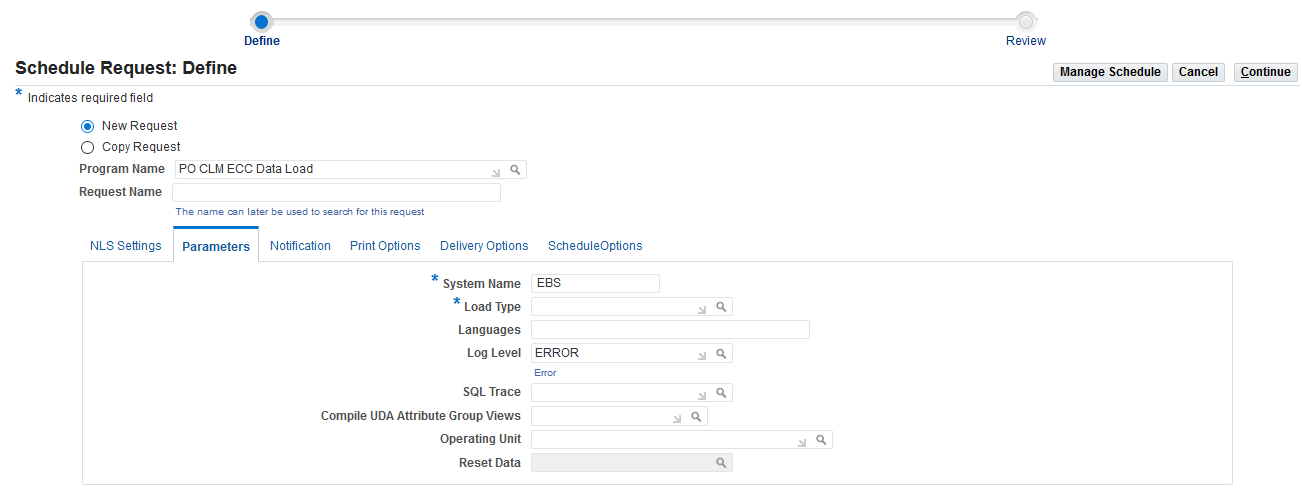
To load CLM procurement data
-
Select New Request.
-
In the Program Name field, enter PO CLM ECC Data Load.
-
Select the appropriate load type.
-
Full Load: Loads all CLM procurement data and is required to be run for the first data load. If you run full load for subsequent requests, then this program clears all CLM procurement data from ECC and loads fresh data.
Important: If there are Document Style name related configuration changes, then you must run the program with the Full Load option. This action ensures that the changes are reflected in the Document Style attribute of Available Refinements in the IDVs and Awards dashboards.
-
Incremental Load: Loads only the data modified since the previous load. Schedule incremental loads to run as often as required to keep the ECC dashboards current.
-
Metadata Load: Loads Descriptive Flexfield (DFF) metadata. Currently, this option is not applicable to CLM Command Center.
-
-
In the Languages field, enter one or more language codes for the output. For multiple language codes, use the format AA,BB,NN. If the field is blank, then the data will be loaded for the base language only (usually US).
-
Select the log level that you want the program to report. The default value is Error.
-
Select True to enable SQL trace. Otherwise, select False.
-
In the Compile UDA Attribute Group Views field, select Yes or No. Important: If you are running Full Load for the first time, then you must select Yes. Otherwise, full load will fail.
-
Select the operating unit for which you want to load data. The following rules apply to the load type if you leave the Operating Unit field blank.
-
For the full load type, the request loads data for all the operating units.
-
For the incremental load, the request loads data only for those operating units for which full load was previously submitted.
-
-
Use the Reset Data parameter with caution. The default value is FALSE. If you run full load for the first time or want to reset the data, then set the parameter value to TRUE. If set to TRUE, this action wipes out all the data that was loaded earlier, and loads the new data for the selected operating unit. After the completion of full load, data of only one operating unit will be available in the ECC data store.
-
For subsequent full loads, to append the new data to the data set, set this value to FALSE.
-
For incremental loads, you need not select a value, because the value is always FALSE regardless of the selected value.
-
-
Submit the concurrent request.
-
Review your request using the Requests page.
-
Monitor data loading using the Data Load Tracking page of the ECC Developer responsibility.
Reviewing Security Rules and Document-Level Security for CLM Procurement Documents
See Contract Lifecycle Management (CLM) for Public Sector Command Center Overview, Oracle Contract Lifecycle Management for Public Sector Purchasing User Guide and Setup and Configuration Steps for CLM Command Center.
Important: Security rules and document security affect the calculation of metrics and plotting of charts, which use only the data to which the user has access. When implementing the CLM for Public Sector Command Center, administrators must consider the security structure and ensure that the concerned procurement team members (program management office managers, contracting officers, and contracting specialists) have appropriate access to CLM procurement documents. If there are inconsistencies, then these inconsistencies will impact data display and the ability of the procurement team to improve responsiveness. The operating unit (OU) security and document security applies to all the dashboards of the command center.
The following table explains the security rules, operating unit security, and document security that the application uses when PMO managers and contracting officers access procurement documents and perform tasks.
| Procurement Documents, Tasks | Rules Common to PMO Managers and Contracting Officers | Applicable to PMO Managers | Applicable to Contracting Officers |
|---|---|---|---|
| Acquisition Plans | Not Applicable | Any one of the following rules is applied, if the user is the:
|
|
| Solicitations (offers, forms, elapsed time, deliverables) | The following security filters are applied:
|
||
| Awards, IDVs (deliverables, open protests, closeout tasks, post award requests) | The following security filters are applied:
|
PMO managers can:
|
If the user is the contracting officer of the award or the IDV, then the document is accessible. |
| Requisitions | The following security filters are applied:
|