| Skip Navigation Links | |
| Exit Print View | |
|
ONC+ Developer's Guide Oracle Solaris 11.1 Information Library |
| Skip Navigation Links | |
| Exit Print View | |
|
ONC+ Developer's Guide Oracle Solaris 11.1 Information Library |
1. Introduction to ONC+ Technologies
4. Programmer's Interface to RPC
5. Advanced RPC Programming Techniques
6. Porting From TS-RPC to TI-RPC
7. Multithreaded RPC Programming
8. Extensions to the Oracle Solaris RPC Library
B. RPC Protocol and Language Specification
Binding and Rendezvous Independence
Other Uses of the RPC Protocol
AUTH_DES Authentication Verifiers
Nicknames and Clock Synchronization
Example Service Described in the RPC Language
RPCL Fixed-Length Array Declarations
Authentication parameters are opaque but open-ended to the rest of the RPC protocol. This section defines some flavors of authentication that have already been implemented. Other sites are free to invent new authentication types, with the same rules of flavor number assignment for program number assignment. Oracle maintains and administers a range of authentication flavors. To have authentication numbers like RPC program numbers allocated or registered to them, contact the Oracle RPC Administrator.
Calls are often made in which the caller does not authenticate itself and the server disregards who the caller is. In these cases, the flavor value of the RPC message's credentials, verifier, and response verifier is AUTH_NONE. The flavor value is the “discriminant” of the opaque_auth “union.” The body length is zero when AUTH_NONE authentication flavor is used.
AUTH_SYS This is the same as the authentication flavor previously known as AUTH_UNIX. The caller of a remote procedure might wish to identify itself using traditional UNIX process permissions authentication. The flavor of the opaque_auth of such an RPC call message is AUTH_SYS. The bytes of the body encode the following structure:
struct auth_sysparms {
unsigned int stamp;
string machinename<255>;
uid_t uid;
gid_t gid;
gid_t gids<10>;
};is an arbitrary ID that the caller machine can generate.
is the name of the caller's machine.
is the caller's effective user ID.
is the caller's effective group ID.
is a counted array of groups in which the caller is a member.
The flavor of the verifier accompanying the credentials should be AUTH_NONE.
When using AUTH_SYS authentication, the flavor of the response verifier received in the reply message from the server might be AUTH_NONE or AUTH_SHORT.
If AUTH_SHORT, the bytes of the response verifier's string encode a short_hand_verf structure. This opaque structure can now be passed to the server instead of the original AUTH_SYS credentials.
The server keeps a cache that maps the shorthand opaque structures to the original credentials of the caller. These structures are passed back by way of an AUTH_SHORT style response verifier. The caller can save network bandwidth and server CPU cycles by using the new credentials.
The server can flush the shorthand opaque structure at any time. If a flush occurs, the remote procedure call message is rejected because of an authentication error. The reason for the failure is AUTH_REJECTEDCRED. At this point, the caller might try the original AUTH_SYS style of credentials, as shown in the following figure.
Figure B-1 Authentication Process Map
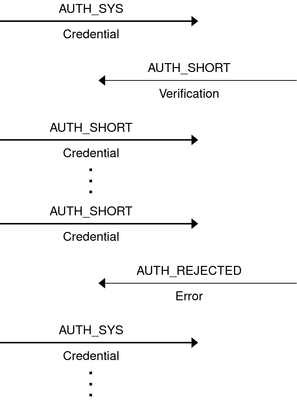
You might encounter the following situations with AUTH_SYS authentication:
Caller identification cannot be guaranteed to be unique if machines with differing operating systems are on the same network.
No verifier exists, so credentials can easily be faked.
AUTH_DES authentication attempts to fix these two problems.
The first issue is handled by addressing the caller by a simple string of characters instead of by an operating system-specific integer. This string of characters is known as the net name or network name of the caller. The server should not interpret the caller's name in any way other than as the identity of the caller. Thus, net names should be unique for every caller in the naming domain.
Each operating system's implementation of AUTH_DES authentication generates net names for its users that ensure this uniqueness when they call remote servers. Operating systems already distinguish users local to their systems. Extending this mechanism to the network is usually a simple matter.
For example, a user with a user ID of 515 might be assigned the following net name: UNIX.515@oracle.com. This net name contains three items that serve to ensure it is unique. Backtracking, only one naming domain is called oracle.com in the Internet. Within this domain, only one UNIX user has the user ID 515. However, there might be another user on another operating system, for example VMS, within the same naming domain who, by coincidence, happens to have the same user ID. To ensure that these two users can be distinguished, you add the operating system name. So one user is UNIX.515@oracle.com and the other is VMS.515@oracle.com.
The first field is actually a naming method rather than an operating system name. It just happens that almost a one-to-one correspondence exists between naming methods and operating systems. If there was a common worldwide naming standard, the first field could be a name from that standard, instead of an operating system name.
Unlike AUTH_SYS authentication, AUTH_DES authentication does have a verifier so the server can validate the client's credential, and the reverse. The contents of this verifier are primarily an encrypted timestamp. The server can decrypt this timestamp, and if it is close to its current real time, then the client must have encrypted it correctly. The only way the client could encrypt the timestamp correctly is to know the conversation key of the RPC session. If the client knows the conversation key, it must be the real client.
The conversation key is a DES [5] key that the client generates and notifies the server of in its first RPC call. The conversation key is encrypted using a public-key scheme in this first transaction. The particular public-key scheme used in AUTH_DES authentication is Diffie-Hellman [3] with 192-bit keys. The details of this encryption method are described in Diffie-Hellman Encryption.
The client and the server need the same notion of the current time for the verification to work. If network time synchronization cannot be guaranteed, then the client can synchronize with the server before beginning the conversation. rpcbind provides a procedure, RPCBPROC_GETTIME, which can be used to obtain the current time.
A server can determine if a client timestamp is valid. For any transaction after the first, the server checks for two things:
The timestamp is greater than the one previously seen from the same client.
The timestamp has not expired. A timestamp is expired if the server's time is later than the sum of the client's timestamp plus what is known as the client's window. The window is an encrypted number the client passes to the server in its first transaction. The window can be thought of as a lifetime for the credential.
For the first transaction, the server checks that the timestamp has not expired. As an added check, the client sends an encrypted item in the first transaction known as the window verifier. This verifier must be equal to the window minus 1, or the server rejects the credential.
The client must check the verifier returned from the server to be sure it is legitimate. The server sends back to the client the encrypted timestamp it received from the client, minus one second. If the client gets any result other than this one, the verifier is rejected.
After the first transaction, the server's AUTH_DES authentication subsystem returns in its verifier to the client an integer nickname. The client can use this nickname in its further transactions instead of passing its net name, encrypted DES key, and window every time. The nickname is most likely an index into a table on the server that stores for each client its net name, decrypted DES key, and window. It should however be treated as opaque data by the client.
Though originally synchronized, client and server clocks can get out of sync. If this situation occurs, the client RPC subsystem most likely receives an RPC_AUTHERROR at which point it should resynchronize.
A client can still get the RPC_AUTHERROR error even though it is synchronized with the server. The server's nickname table is a limited size, and it can flush entries as needed. The client should resend its original credential and the server gives the client a new nickname. If a server crashes, the entire nickname table is flushed, and all clients have to resend their original credentials.
Credentials are explained in the following example.
Example B-2 AUTH_DES Authentication Protocol
/*
* There are two kinds of credentials: one in which the client
* uses its full network name, and one in which it uses its
* “nickname” (just an unsigned integer) given to it by the
* server. The client must use its full name in its first
* transaction with the server, in which the server returns
* to the client its nickname. The client may use its nickname
* in all further transactions with the server. There is no
* requirement to use the nickname, but it is wise to use it for
* performance reasons.
*/
enum authdes_namekind {
ADN_FULLNAME = 0,
ADN_NICKNAME = 1
};
/*
* A 64-bit block of encrypted DES data
*/
typedef opaque des_block[8];
/*
* Maximum length of a network user's name
*/
const MAXNETNAMELEN = 255;
/*
* A fullname contains the network name of the client, an
* encrypted conversation key and the window. The window
* is actually a lifetime for the credential. If the time
* indicated in the verifier timestamp plus the window has
* passed, then the server should expire the request and
* not grant it. To insure that requests are not replayed,
* the server should insist that timestamps be greater
* than the previous one seen, unless it is the first transaction.
* In the first transaction, the server checks instead that the
* window verifier is one less than the window.
*/
struct authdes_fullname {
string name<MAXNETNAMELEN>; /* name of client */
des_block key; /* PK encrypted conversation key */
unsigned int window; /* encrypted window */
}; /* NOTE: PK means "public key" */
/*
* A credential is either a fullname or a nickname
*/
unionauthdes_credswitch(authdes_namekindadc_namekind){
case ADN_FULLNAME:
authdes_fullname adc_fullname;
case ADN_NICKNAME:
unsigned int adc_nickname;
};
/*
* A timestamp encodes the time since midnight, January 1, 1970.
*/
struct timestamp {
unsigned int seconds; /* seconds */
unsigned int useconds; /* and microseconds */
};
/*
* Verifier: client variety
*/
struct authdes_verf_clnt {
timestamp adv_timestamp; /* encrypted timestamp */
unsigned int adv_winverf; /* encrypted window verifier */
};
/*
* Verifier: server variety
* The server returns (encrypted) the same timestamp the client gave
* it minus one second. It also tells the client its nickname to be
* used in future transactions (unencrypted).
*/
struct authdes_verf_svr {
timestamp adv_timeverf; /* encrypted verifier */
unsigned int adv_nickname; /* new nickname for clnt */};
In this scheme are two constants, PROOT and HEXMODULUS. The particular values chosen for these constants for the DES authentication protocol are:
const PROOT = 3; const HEXMODULUS = /* hex */ "d4a0ba0250b6fd2ec626e7efd637df76c716e22d0944b88b";
The way this scheme works is best explained by an example. Suppose there are two people, A and B, who want to send encrypted messages to each other. A and B each generate a random secret key that they do not disclose to anyone. Let these keys be represented as SK(A) and SK(B). They also publish in a public directory their public keys. These keys are computed as follows:
PK(A) = (PROOT ** SK(A)) mod HEXMODULUS PK(B) = (PROOT ** SK(B)) mod HEXMODULUS
The ** notation is used here to represent exponentiation.
Now, both A and B can arrive at the common key between them, represented here as CK(A,B), without disclosing their secret keys.
A computes:
CK(A, B) = (PK(B) ** SK(A)) mod HEXMODULUS
while B computes:
CK(A, B) = (PK(A) ** SK(B)) mod HEXMODULUS
These two computations can be shown to be equivalent: (PK(B)**SK(A)) mod HEXMODULUS = (PK(A)**SK(B)) mod HEXMODULUS. Drop the mod HEXMODULUS parts and assume modulo arithmetic to simplify the process:
PK(B) ** SK(A) = PK(A) ** SK(B)
Then replace PK(B) by what B computed earlier and likewise for PK(A).
((PROOT ** SK(B)) ** SK(A) = (PROOT ** SK(A)) ** SK(B)
which leads to:
PROOT ** (SK(A) * SK(B)) = PROOT ** (SK(A) * SK(B))
This common key CK(A,B) is not used to encrypt the timestamps used in the protocol. It is used only to encrypt a conversation key that is then used to encrypt the timestamps. This approach uses the common key as little as possible, to prevent a break. Breaking the conversation key is a far less serious compromise, because conversations are comparatively short lived.
The conversation key is encrypted using 56-bit DES keys, yet the common key is 192 bits. To reduce the number of bits, 56 bits are selected from the common key as follows. The middle-most 8 bytes are selected from the common key, and then parity is added to the lower-order bit of each byte, producing a 56-bit key with 8 bits of parity.
To avoid compiling Kerberos code into the operating system kernel, the kernel used in the S implementation of AUTH_KERB uses a proxy RPC daemon called kerbd. The daemon exports three procedures.
KGETKCRED is used by the server-side RPC to check the authenticator presented by the client.
KSETKCRED returns the encrypted ticket and DES session key, given a primary name, instance, and realm.
KGETUCRED is UNIX specific. It returns the user's ID, the group ID, and groups list, assuming that the primary name is mapped to a user name known to the server.
The best way to describe how Kerberos works is to use an example based on a service currently implementing Kerberos: the network file system (NFS). The NFS service on server s is assumed to have the well-known principal name nfs.s. A privileged user on client c is assumed to have the primary name root and an instance c. Note that, unlike AUTH_DES, when the user's ticket-granting ticket has expired, kinit() must be reinvoked. NFS service for Kerberos mounts fail until a new ticket-granting ticket is obtained.
This section follows an NFS mount request from start to finish using AUTH_KERB. Because mount requests are executed as root, the user's identity is root.c.
Client c makes a MOUNTPROC_MOUNT request to the server s to obtain the file handle for the directory to be mounted. The client mount program makes an NFS mount system call, handing the client kernel the file handle, mount flavor, time synchronization address, and the server's well-known name, nfs.s. Next the client kernel contacts the server at the time synchronization host to obtain the client-server time bias.
The client kernel makes the following RPC calls.
KSETKCRED to the local kerbd to obtain the ticket and session key.
NFSPROC_GETATTR to the server's NFS service, using the full name credential and verifier. The server receives the calls and makes the KGETKCRED call to its local kerbd to check the client's ticket.
The server's kerbd and the Kerberos library decrypt the ticket and return, among other data, the principal name and DES session key. The server checks that the ticket is still valid, uses the session key to decrypt the DES-encrypted portions of the credential and verifier, and checks that the verifier is valid.
The possible Kerberos authentication errors returned at this time are:
AUTH_BADCRED is returned if the verifier is invalid because the decrypted win in the credential and win +1 in the verifier do not match, or the timestamp is not within the window range.
AUTH_REJECTEDCRED is returned if a replay is detected.
AUTH_BADVERF is returned if the verifier is garbled.
If no errors are received, the server caches the client's identity and allocates a nickname, which is a small integer, to be returned in the NFS reply. The server then checks if the client is in the same realm as the server. If so, the server calls KGETUCRED to its local kerbd to translate the principal's primary name into UNIX credentials. If the previous name is not translatable, the user is marked anonymous. The server checks these credentials against the file system's export information. Consider these three cases:
If the KGETUCRED call fails and anonymous requests are allowed, the UNIX credentials of the anonymous user are assigned.
If the KGETUCRED call fails and anonymous requests are not allowed, the NFS call fails with the AUTH_TOOWEAK.
If the KGETUCRED call succeeds, the credentials are assigned, and normal protection checking follows, including checking for root permission.
Next, the server sends an NFS reply, including the nickname and server's verifier. The client receives the reply, decrypts and validates the verifier, and stores the nickname for future calls. The client makes a second NFS call to the server, and the calls to the server described previously are repeated. The client kernel makes an NFSPROC_STATVFS call to the server's NFS service, using the nickname credential and verifier described previously. The server receives the call and validates the nickname. If it is out of range, the error AUTH_BADCRED is returned. The server uses the session key just obtained to decrypt the DES-encrypted portions of the verifier and validates the verifier.
The possible Kerberos authentication errors returned at this time are:
AUTH_REJECTEDVERF, which is returned if the timestamp is invalid, a replay is detected, or if the timestamp is not within the window range
AUTH_TIMEEXPIRE, which is returned if the service ticket is expired
If no errors are received, the server uses the nickname to retrieve the caller's UNIX credentials. Then it checks these credentials against the file system's export information, and sends an NFS reply that includes the nickname and the server's verifier. The client receives the reply, decrypts and validates the verifier, and stores the nickname for future calls. Last, the client's NFS mount system call returns, and the request is finished.
The following example of AUTH_KERB has many similarities to the one for AUTH_DES, shown in the following code example. Note the differences.
Example B-3 AUTH_KERB Authentication Protocol
#define AUTH_KERB 4
/*
* There are two kinds of credentials: one in which the client
* sends the (previously encrypted)
Kerberos ticket, and one in
* which it uses its “nickname” (just an unsigned integer)
* given to it by the server. The client must use its full name
* in its first transaction with the server, in which the server
* returns to the client its nickname. The client may use
* its nickname in all further transactions with the server
* (until the ticket expires). There is no requirement to use
* the nickname, but it is wise to use it for performance reasons.
*/
enum authkerb_namekind {
AKN_FULLNAME = 0,
AKN_NICKNAME = 1
};
/*
* A fullname contains the encrypted service ticket and the
* window. The window is actually a lifetime
* for the credential. If the time indicated in the verifier
* timestamp plus the window has passed, then the server should
* expire the request and not grant it. To insure that requests
* are not replayed, the server should insist that timestamps be
* greater than the previous one seen, unless it is the first
* transaction. In the first transaction, the server checks
* instead that the window verifier is one less than the window.
*/
struct authkerb_fullname {
KTEXT_ST ticket; /* Kerberos service ticket */
unsigned long window; /* encrypted window */
};
/*
* A credential is either a fullname or a nickname
*/
union authkerb_credswitch(authkerb_namekind akc_namekind){
case AKN_FULLNAME:
authkerb_fullname akc_fullname;
case AKN_NICKNAME:
unsigned long akc_nickname;
};
/*
* A timestamp encodes the time since midnight, January 1, 1970.
*/
struct timestamp {
unsigned long seconds; /* seconds */
unsigned long useconds; /* and microseconds */
};
/*
* Verifier: client variety
*/
struct authkerb_verf_clnt {
timestamp akv_timestamp; /* encrypted timestamp */
unsigned long akv_winverf; /* encrypted window verifier */
};
/*
* Verifier: server variety
* The server returns (encrypted) the same timestamp the client
* gave it minus one second. It also tells the client its
* nickname to be used
in future transactions (unencrypted).
*/
struct authkerb_verf_svr {
timestamp akv_timeverf; /* encrypted verifier */
unsigned long akv_nickname; /* new nickname for clnt */
};