| Skip Navigation Links | |
| Exit Print View | |
|
Oracle Identity Analytics User's Guide 11g Release 1 |
1. Oracle Identity Analytics Overview
Introducing the Role-Based Access Control Model
Understanding Oracle Identity Analytics Benefits
Understanding Oracle Identity Analytics Components and Terminology
Understanding Resources and Resource Types
Understanding Business Structures
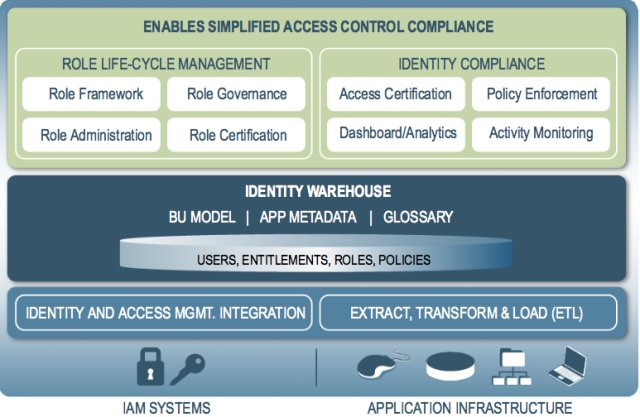
Oracle Identity Analytics is organized into the following modules: Identity Warehouse, Identity Certification, Role Engineering and Management, and Identity Auditing.
The Identity Warehouse is a central repository that contains data on user entitlements. This data is imported from one or more databases within your organization on a scheduled basis. The Oracle Identity Analytics import engine supports complex entitlement feeds saved as either text or XML files. Extract, Transform, and Load (ETL) processing capabilities are also available. Imported data is then correlated or mapped to various roles during the certification phase. A glossary description of each entitlement is also captured during the import process.
Managing and auditing enterprise-wide attestations is a major challenge to companies with a large number of employees. Because individual users may have access to a multitude of platforms, systems, and applications, organizations need an easy-to-use tool that managers can use to review user entitlements on a regular basis. Moreover, federal requirements require time-based certifications, granular entitlements, and so on.
The Oracle Identity Analytics identity certification module makes user entitlements easy to monitor and distribute. Managers can easily communicate with IT administrators to monitor, authorize, add, or revoke application access based on changes. The Oracle Identity Analytics identity certification module allows managers to collect, manage, and distribute user entitlements. In addition, these certifications can be scheduled depending upon the compliance requirements of the entitlement certification.
The identity certification module can perform four types of certifications:
User Entitlement Certification. Allows managers to certify employee access to roles and other related entitlements.
Role Entitlement Certification. Allows role owners to certify roles and role content.
Resource Entitlement Certification. Allows resource owners to certify user access to resources.
Data Owner Certification. Allows data owners to certify users.
Each certification addresses different audience types and ensures stringency at every step of the access management process.
Role-based access control is one of the complex and challenging efforts carried out in security administration. RBAC restricts access of the systems to authorized users by using predefined and approved roles. Within an organization, roles are seldom stationary. With a dynamic business environment, role management is also in a constant state of flux. New roles need to be created while old ones need to upgraded or managed on a regular basis.
Oracle Identity Analytics offers an end-to-end solution to define roles based on existing user entitlements. Roles can also be generated using the software's role mining module. The Oracle Identity Analytics role mining interface uses sophisticated algorithms to create new roles based on user entitlements, and cuts the role definition time by about fifty percent. Multiple rules and a combination of attributes (such as job codes, department, and location) can be used to assign role-based access to new and existing users.
The Oracle Identity Analytics software is a good alternative to manual access control methodologies because its superior framework facilitates easy management of users and their access to roles in a controlled and effective manner. Oracle Identity Analytics provides a complete setup of security, workflow, and auditing features to manage the lifecycle of roles. The built-in workflow engine provides the ability to configure the best suited workflow processes depending on the business requirements and allows stakeholders to call external functions from the workflows. This functionality enables greater efficiencies from a role-based access control model. Additionally, multiple rules and a combination of attributes (such as job codes, department, and location) can be used to assign role-based access to new and existing users.
Today, organizations need to manage Continuous Exception Monitoring, Segregation of Duty (SoD) Violations, Detective Scanning, Inter and Intra-Application SoD Enforcement, Actual vs. Assigned Exceptions, Exception Lifecycle Management, and so on. Organizations also tend to have numerous exceptions related to the access users have to target systems.