2 Setting Up the OAAM Environment
When you install Oracle Adaptive Access Manager, you install the binary files, such as executable files, jar files, and libraries. Then, you use configuration tools to configure the software.
This chapter presents details on setting up the Oracle Adaptive Access Manager environment for first time users. For information on how to upgrade an existing Oracle Adaptive Access Manager 10g (10.1.4.5) to Oracle Adaptive Access Manager 11g Release 2 (11.1.2), see Oracle Fusion Middleware Upgrade and Migration Guide for Oracle Identity and Access Management.
2.1 Prerequisites
All tasks in this book presume that you have Oracle Adaptive Access Manager 11g installed with initial configuration completed as described in the Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management.
2.2 Setting Up the Base Environment
After completing the installation process, including post-installation steps, you must set up the Oracle Adaptive Access Manager base environment before you can use the graphical user interfaces or command-line tools to manage authentication mechanisms, risk based challenge methods, policy administration, and integration. Setting up the base environment involves the following tasks:
Table 2-1 Tasks to Set Up OAAM Base Environment
| No. | Task | Description |
|---|---|---|
|
1 |
Set up the CLI environment |
The Oracle Adaptive Access Manager Command-Line Interface (CLI) scripts enable users to perform various tasks instead of using the Oracle Adaptive Access Manager Administration Console. You will need to set up the CLI environment before setting up encryption and database credentials. For information on setting up the CLI environment, see Section 2.3, "Setting Up the CLI Environment." |
|
2 |
Set up encryption and database credentials |
For information, see Section 2.4, "Setting Up Encryption and Database Credentials for Oracle Adaptive Access Manager." |
|
3 |
Create OAAM users |
For information, see Section 2.5, "Creating OAAM Users." |
|
4 |
Import OAAM base snapshot |
For information, see Section 2.6, "Importing the OAAM Snapshot." |
|
5 |
Import IP location data |
For information, see Section 2.7, "Importing IP Location Data." |
|
6 |
Enable OTP |
For information, see Section 2.8, "Enabling OTP." |
|
7 |
Set the time zone for time stamps in the OAAM Administration Console |
For information, see Section 2.9, "Setting the Time Zone Used for All Time Stamps in the OAAM Administration Console." |
2.3 Setting Up the CLI Environment
The Oracle Adaptive Access Manager Command-Line Interface (CLI) scripts enable users to perform various tasks instead of using the Oracle Adaptive Access Manager Administration Console.
Setting up the CLI environment involves the following tasks:
-
Set up the CLI work folder
-
Set up the Credential Store Framework (CSF) configuration
-
Set up the Oracle Adaptive Access Manager database credentials
2.3.1 Set up the CLI Work Folder
In this section, you will copy the CLI folder $IDM_ORACLE_HOME/oaam/cli to a working directory, for example, oaam_cli.
Note:
This task is required since it is not recommended to edit or change any files that are inside theIDM_ORACLE_HOME folder (the folder where you installed the Oracle Identity Management software).-
Create a working directory.
mkdir workcd workmkdir oaam_cli -
Copy the
oaam_clifolder to the working directory by executing the following command:
Execute the following command:
cp -r <IDM_ORACLE_HOME>/oaam/cli ~/work/oaam_cli
Execute the following command:
xcopy/s <IDM_ORACLE_HOME>\oaam\cli c:\work\oaam_cli
Select D=directory when it prompts so that entire folder can be copied.
2.3.2 Set Up the Credential Store Framework (CSF) Configuration
A credential store is a repository that can hold user name and password combinations, symmetric keys, tickets, or public key certificates. Oracle Platform Security Services includes the Credential Store Framework (CSF), a set of APIs that applications can use to create, read, update, and manage credentials securely. OAAM uses the CSF APIs to access credentials. Credentials are stored in the CSF of the Oracle WebLogic Server domain and managed using Oracle Fusion Middleware Enterprise Manager Control or Oracle WebLogic Scripting Tool (WLST).
Select one of the following mechanisms to access the OAAM encryption keys stored in the CSF:
-
CSF without Mbeans
-
CSF with MBeans
2.3.2.1 Configure OAAM Database Details with CSF without MBeans
Important notes about this approach are listed as follows:
-
This method requires that you run the Oracle Adaptive Access Manager command-line utility scripts on the same computer as the WebLogic Server.
-
This method does not require you to specify the WebLogic Administrator and password.
-
This method is not recommended if Oracle Adaptive Access Manager is deployed in a clustered environment
To use this mechanism, go to the work folder where you copied the cli folder and open the file, conf/bharosa_properties/oaam_cli.properties in a text editor and then set the following properties:
| Property Name | Notes about Property Value |
|---|---|
| oaam.csf.useMBeans | false |
| oaam.jps.config.filepath | Set the absolute file path of jps-config-jse.xml. Usually, it resides in $DOMAIN_HOME/config/fmwconfig folder |
| oaam.db.url | Specify valid JDBC URL of the Oracle Adaptive Access Manager database. Make sure there are no typos. |
| oaam.db.additional.properties.file | Leave this as blank if there are no additional Oracle Toplink properties.
Otherwise specify the name of the properties file that has additional Oracle Toplink properties. Make sure the file is in the same folder as |
| oaam.db.driver | oracle.jdbc.driver.OracleDriver (Change this value only if the Oracle Adaptive Access Manager schema is in non-oracle database) |
| oaam.db.min.read-connections | 1 (Do not change this value unless required) |
| oaam.db.max.read-connections | 25 (Do not change this value unless required) |
| oaam.db.min.write-connections | 1 (Do not change this value unless required) |
| oaam.db.max.write-connections | 25 (Do not change this value unless required) |
2.3.2.2 Configure OAAM Database Details with CSF with MBeans
Important notes about this approach:
-
This method is recommended if Oracle Adaptive Access Manager is deployed in a clustered environment.
-
This method permits you to remotely connect to the Oracle Adaptive Access Manager WebLogic Server.
-
This method requires you to specify the Oracle Adaptive Access Manager WebLogic Administrator user and password.
To configure the Oracle Adaptive Access Manager Database details with CSF with MBeans, go to the work folder where you copied the cli folder and open the file conf/bharosa_properties/oaam_cli.properties in a text editor and then set the following properties:
| Property Name | Notes about Property Value |
|---|---|
| oaam.csf.useMBeans | true (Keep it as true) |
| oaam.adminserver.hostname | <Host name where WebLogic Administration Server runs> |
| oaam.adminserver.port | <Port number of WebLogic Administration Server. Usually it is 7001> |
| oaam.adminserver.username | <User name of the WebLogic Administrator user. Usually it is WebLogic> |
| oaam.adminserver.password | <Password of the WebLogic Administrator user> |
| oaam.db.url | Specify valid JDBC URL of the Oracle Adaptive Access Manager database. Make sure there are no typos. |
| oaam.db.additional.properties.file | Leave this as blank if there are no additional Oracle Toplink properties.
Otherwise specify the name of the properties file that has additional Oracle Toplink properties. Make sure the file is in the same folder as |
| oaam.db.driver | oracle.jdbc.driver.OracleDriver (Change this value only if the Oracle Adaptive Access Manager schema is in non-oracle database) |
| oaam.db.min.read-connections | 1 (Do not change this value unless required) |
| oaam.db.max.read-connections | 25 (Do not change this value unless required) |
| oaam.db.min.write-connections | 1 (Do not change this value unless required) |
| oaam.db.max.write-connections | 25 (Do not change this value unless required) |
2.3.3 Setting Up Oracle Adaptive Access Manager Database Credentials
Configuring database credentials in the Credential Store Framework involves the following steps:
-
Use the Oracle Enterprise Manager Fusion Middleware Control to add database credentials (user name and password) in the Credential Store Framework in the domain where Oracle Adaptive Access Manager is installed. These credentials are used by the Oracle Adaptive Access Manager command-line utilities.
-
Configure the properties files that are used by the Oracle Adaptive Access Manager CLI utilities with details of the WebLogic administration server and Oracle Adaptive Access Manager database.
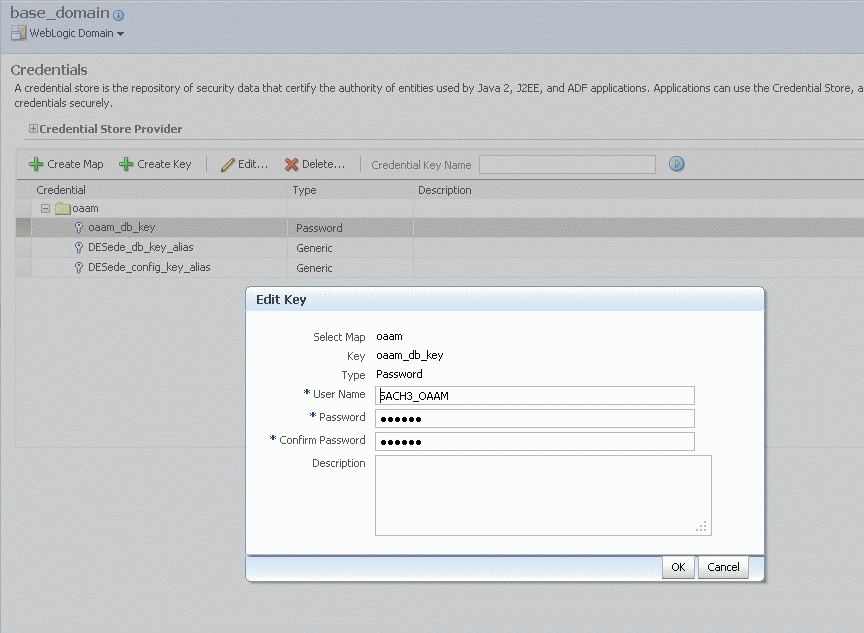
For information on the credential store, see Oracle Fusion Middleware Application Security Guide. Figure 2-1 shows the database credential setup.
For instructions on setting up database credentials in the CSF, see Section 2.4.6, "Setting Up Oracle Adaptive Access Manager Database Credentials in the Credential Store Framework."
2.3.4 Using Persistence Instead of Setting Database Credentials in the Credential Store Framework
If you want to use persistence.xml instead of setting the Oracle Adaptive Access Manager database credentials in CSF, go through the following steps. However this approach is not recommended and supported.
-
Go to the work folder where you copied the
clifolder. Open the fileconf/bharosa_properties/oaam_cli.propertiesin a text editor and set the property value ofoaam.db.toplink.useCredentialsFromCSFtofalse. -
Update the Oracle Adaptive Access Manager database connection details in the
META-INF/persistence.xmlfile by editing the relevanteclipselink.jdbcproperties, as in the following examples:<property name="eclipselink.jdbc.driver" value="oracle.jdbc.driver.OracleDriver"/> <property name="eclipselink.jdbc.url" value="jdbc:oracle:thin:@<dbhost.mydomain.com>:1521/<SERVICE_NAME>"/> <property name="eclipselink.jdbc.user" value="<OAAM DB USER>"/> <property name="eclipselink.jdbc.password" value="< DB Password >"/>
2.4 Setting Up Encryption and Database Credentials for Oracle Adaptive Access Manager
Out-of-the-box, encryption keys are automatically generated if they do not exist when oaam_server and oaam_admin are started for the first time.
Oracle Adaptive Access Manager uses secret keys to encrypt data stored in the credential store framework. Encryption protects data within Oracle Adaptive Access Manager from unauthorized access. The process uses methods and a key or keys to encode plain text into a non-readable form. A key is required to decrypt the encrypted information and make it readable again. Authorized persons who own the key can decrypt information that is encrypted with the same key.
Oracle Adaptive Access Manager requires that secret keys be set up to encrypt data stored in the credential store framework. These secret keys can be added to the WebLogic Server Credential Store Framework using Oracle Enterprise Manager Fusion Middleware Control.
There are three keys that need to be created for OAAM to work.
-
oaam_db_key
-
DESede_db_key_alias
-
DESede_config_key_alias
The oaam_db_key is used to access the database and must be added manually. For information on oaam_db_key, see Section 2.3.3, "Setting Up Oracle Adaptive Access Manager Database Credentials."
The DESede keys are used to encrypt data. As noted in the introduction to this section, if they do not exist, the OAAM servers will create them when it is first started. You can accept these DESede keys or create your own.
If you choose to use your own DESede keys you have two choices for creating and encoding them:
-
Provide your own secret key (a string of characters), encode it using
encodeKey.sh, and then store that value, or -
Use
generateEncodedKey.shto generate a key and encodes it in one step
Note that if you allow the server to generate the value or use generateEncodedKey.sh, you do not know the "secret phrase." You know only the encoded value. This value should be backed up. If you use your own secret key, you can regenerate the encoded value.
Setting up encryption involves the following steps:
-
Ensure the secret keys (symmetric keys) for both the configuration value and database are available. If you do not have a secret key, generate an encoded symmetric key using the
genEncodedKeycommand. -
Encode the key using the
base64encodeoption of theencodeKeycommand. This step is not required if thegenEncodedKeycommand was used to generate the key. -
Use the Oracle Enterprise Manager Fusion Middleware Control to add the encoded secret key to an alias in the Credential Store Framework in the domain where Oracle Adaptive Access Manager is installed.
A credential store is a repository to store user name/password or generic credentials (a certificate). The value of using a credential store is that the application does not store passwords in clear text and does not have to invent its own solutions for protecting passwords, allowing administrators and developers alike to work with a consistent credential repository.
2.4.1 Prerequisites for Setting Up Encryption and Database Credentials
Prerequisites for setting up encryption and database credentials for Oracle Adaptive Access Manager are as follows:
-
If you do not have access to the Oracle Adaptive Access Manager installation folder, make sure Oracle Adaptive Access Manager 11g is configured with Oracle Enterprise Manager Fusion Middleware Control while creating the domain.
-
If you have access to the Oracle Adaptive Access Manager installation folder then make sure you have access to running the command-line scripts in the MW_HOME\IDM_ORACLE_HOME
\oaam\clifolder. -
Make sure the JDK is installed and check that the
javacommand is in the path by executing thejavacommand.
Note:
If you are upgrading from Oracle Adaptive Access Manager 10.1.4.5 to Oracle Adaptive Access Manager 11g, you can skip Section 2.4.2, "Setting up the Encoded Secret Key for Encrypting Configuration Values,", Section 2.4.3, "Setting Up Encoded Secret Key for Encrypting Database Values,"and Section 2.4.4, "Generating an Encoded Secret Key," since the Upgrade Assistant automatically migrates the secret keys from Oracle Adaptive Access Manager 10.1.4.5 to the Credential Store Framework in Oracle Adaptive Access Manager 11g.2.4.2 Setting up the Encoded Secret Key for Encrypting Configuration Values
To set up the encoded secret key for encrypting configuration values, proceed as follows:
-
Go to the Oracle Adaptive Access Manager command-line folder MW_HOME\IDM_ORACLE_HOME
\oaam\cli. -
Create a file
config_secret_key.fileand add the secret key to the file by entering:tobase64=<secret-key>
Note:
- If you do not have any secret key and need instructions to generate an encoded secret key, see Section 2.4.4, "Generating an Encoded Secret Key."
-
This is your key to the encryption algorithm.
-
Note that 3DES accepts any key, but it must be a minimum of 24 characters.
-
Encode the key using the Base64 algorithm by executing the following command.
-
In Unix
encodeKey.sh config_secret_key.file
-
In Windows
encodeKey.cmd config_secret_key.file
If the encoding command was successful, you see output similar to the following:
base64encode is done! Base64 Encoded value =<encoded_value>
If the
KeyStorecommand was not successful, you might see the following error:Exception in thread "main" java.lang.NoClassDefFoundError: while resolving class: com.bharosa.vcrypt.common.util.KeyStoreUtil at java.lang.VMClassLoader.resolveClass(java.lang.Class) (/usr/lib/libgcj.so.5.0.0) at java.lang.Class.initializeClass() (/usr/lib/libgcj.so.5.0.0) at java.lang.Class.forName(java.lang.String, boolean, java.lang.ClassLoader) (/usr/lib/libgcj.so.5.0.0) at java.lang.Class.forName(java.lang.String) (/usr/lib/libgcj.so.5.0.0)
-
-
Note down the encoded value of the key printed on the screen. Make sure there are no spaces. You need this to add to the Credential Store Framework.
2.4.3 Setting Up Encoded Secret Key for Encrypting Database Values
To set up the secret key for encrypting database values, proceed as follows:
-
Go to the Oracle Adaptive Access Manager command-line folder MW_HOME\IDM_ORACLE_HOME
\oaam\cli. -
Create a
file db_secret_key.fileand add the secret key to the file by entering:tobase64=<secret-key>
Note:
- If you do not have any secret key and need instructions for generating an encoded secret key, see Section 2.4.4, "Generating an Encoded Secret Key."
-
This is your key to the encryption algorithm.
-
Note that 3DES accepts any key, but it must be a minimum of 24 characters.
-
Encode the key using Base64 algorithm by executing the following command.
-
In Unix
encodeKey.sh db_secret_key.file
-
In Windows
encodeKey.cmd db_secret_key.file
If the encoding command was successful, you see output similar to the following:
base64encode is done! Base64 Encoded value = <encoded_value>
If the
KeyStorecommand was not successful, you might see the following error:Exception in thread "main" java.lang.NoClassDefFoundError: while resolving class: com.bharosa.vcrypt.common.util.KeyStoreUtil at java.lang.VMClassLoader.resolveClass(java.lang.Class) (/usr/lib/libgcj.so.5.0.0) at java.lang.Class.initializeClass() (/usr/lib/libgcj.so.5.0.0) at java.lang.Class.forName(java.lang.String, boolean, java.lang.ClassLoader) (/usr/lib/libgcj.so.5.0.0) at java.lang.Class.forName(java.lang.String) (/usr/lib/libgcj.so.5.0.0)
-
-
Note down the encoded value of the key printed on the screen. Make sure there are no spaces. You need this to add to the Credential Store Framework.
2.4.4 Generating an Encoded Secret Key
To generate an encoded secret key, proceed as follows:
-
Execute the following command:
-
In Unix
genEncodedKey.sh sample.db_3des_input.properties
-
In Windows
genEncodedKey.cmd sample.db_3des_input.properties
-
-
If the command is successful you see output similar to the following:
Generated key = <encoded_key>
Note:
Encoding the generated key is not necessary since it is already encoded.2.4.5 Adding the Encoded Symmetric Key to the Credential Store Framework
OAAM Servers automatically generate the secret key if you start them after domain creation. You can choose to use those auto-generated secret keys if you do not want to use different secret keys.
To add a symmetric key to the Credential Store Framework, proceed as follows:
-
Log in to Oracle Enterprise Manager Fusion Middleware Control at http://weblogic_admin_server:port/em using the Web browser and use the WebLogic Administrator credentials to log in.
-
Expand the WebLogic Domain icon in the Navigation tree in the left panel.
-
Select OAAM domain and right-click and select the menu option Security, and then the option Credentials in the submenu.
-
Check to see whether there is a map with the name oaam. If not, click the Create Map option and enter the Map Name as
oaam. Click OK to save the map. -
Click oaam to select the map and then click Create Key.
-
In the popup dialog make sure Select Map is oaam.
-
Enter the following values:
-
Enter a description in the Description field.
-
Click OK to save the secret key to the Credential Store Framework.
-
Make sure you back up the alias and the secret key.
The backup is required if you must re-create the domain and point the domain to the existing Oracle Adaptive Access Manager database.
Note:
If you lose the secret key, all the existing data in the Oracle Adaptive Access Manager database becomes unusable since many important administrative operations involve encrypted data.
2.4.6 Setting Up Oracle Adaptive Access Manager Database Credentials in the Credential Store Framework
To set up the Oracle Adaptive Access Manager database credentials in the Credential Store Framework, proceed as follows:
-
Log in to Oracle Enterprise Manager Fusion Middleware Control at http://weblogic_admin_server:port/em using the Web browser and use the WebLogic Administrator credentials to log in.
-
Expand the WebLogic Domain icon in the Navigation tree in the left panel.
-
Select the OAAM domain and right-click and select the menu option Security and then the option Credentials in the submenu.
-
Check to see whether there is a map with the name oaam. If not click the Create Map option and enter the Map Name as
oaam. Click OK to save the map. -
Click oaam to select the map and then click Create Key.
-
In the popup dialog make sure Select Map is oaam.
-
Enter the following values:
-
Enter the description.
-
Click OK to save the secret key to the Credential Store Framework.
2.4.7 Backing Up Database Credentials and Encoded Secret Keys for Encrypting the Database and Configuration Values
You must back up the encoded secret keys used. You may need these keys, if you have to re-create the Oracle Adaptive Access Manager 11g domain. Make sure you note the encoded secret key and the alias name.
-
Log in to Oracle Enterprise Manager Fusion Middleware Control.
-
Expand the WebLogic Domain on the left panel, and select OAAM domain.
-
From the OAAM Domain, select Security, and then Credentials.
-
Expand oaam and select the symmetric key related entries associated with the Type Generic.
-
Click Edit.
-
Go to the Credentials section then copy the symmetric key related entries and note the key name.
-
Repeat these steps to back up database and configuration keys.
Note:
If you delete and re-create the Oracle Adaptive Access Manager 11g domain, make sure you use the backed-up secret keys when setting the encryption keys so that the existing data in the Oracle Adaptive Access Manager database can be decrypted properly.2.5 Creating OAAM Users
The Oracle Adaptive Access Manager users can access functionality based on the roles they are assigned. These administrator roles have specific permissions assigned to them based on their responsibilities.
You can create new users and assign the relevant Oracle Adaptive Access Manager roles in your WebLogic administration domain by using the Oracle WebLogic Administration Console. Best practices is to refrain from assigning multiple roles to a single user. If a user has multiple roles assigned to him, the user will have all of the permissions from the different groups.
If you want to take care of user and group creation in the external LDAP store, see the Oracle Fusion Middleware Enterprise Deployment Guide for Oracle Identity Management.
To create an OAAM user, proceed as follows:
-
Log in to the Oracle WebLogic Administration Console for your WebLogic administration domain.
-
In the left panel, select Security Realms.
-
On the Summary of Security Realms page select the name of the realm (for example,
myrealm). -
On the Settings for Realm Name page select Users and Groups > Users.
-
Click New and provide the required information to create a user, such as
user1, in the security realm. -
Click the newly created user,
user1. -
Click the Groups tab.
-
Assign any of the groups with the
OAAMprefix to the user, user1. -
Click Save.
2.6 Importing the OAAM Snapshot
A full snapshot of policies, dependent components and configurations is shipped with Oracle Adaptive Access Manager. The oaam_base_snapshot.zip file is located in the MW_HOME/IDM_ORACLE_HOME/oaam/init directory.
-
Log in to the Oracle Adaptive Access Manager Administration Console (OAAM Admin) using the following URL:
http://host:port/oaam_admin
-
Load the snapshot file into the system by following these instructions:
-
Open System Snapshot under Environment in the Navigation tree.
-
Click the Load from File button.
A Load and Restore Snapshot dialog appears.
-
Deselect Back up current system now and click Continue.
A dialog appears with the message that you have not chosen to back up the current system, and do you want to continue?
-
When the dialog appears with the message that you have not chosen to back up the current system, and do you want to continue, click Continue.
The Load and Restore Snapshot page appears for you to choose a snapshot to load.
-
Browse for
oaam_base_snapshot.zipand click the Load button to load the snapshot into the system database. -
Click OK and then Restore.
-
The snapshot contains the following items that must be imported into OAAM:
-
Challenge questions for English (United States)
During registration, which could be enrollment, opening a new account, or another events such as a reset, the user selects different questions from a list of questions and enters answers to them. These questions, called challenge questions, are used to authenticate users.
Questions for the languages you want to support must be in the system before users can be asked to register. These questions may also be required to log in to OAAM Server.
-
The actors that are tracked during authentication are called authentication entities and include user, city, device, and so on. These base entities are required to enable conditions that are used for patterns.
-
Patterns are used by Oracle Adaptive Access Manager to either define one bucket or dynamically create buckets. Oracle Adaptive Access Manager collects data and populates these buckets with members based on pattern parameters, and rules perform risk evaluations on dynamically changing membership and distributions of the buckets.
-
Out-of-the-box configurable actions
Configurable actions are actions that are triggered based on the result action or risk scoring or both after a checkpoint execution. The configurable actions are built using action templates.
Note:
If you are upgrading from Oracle Adaptive Access Manager 10.1.4.5 to Oracle Adaptive Access Manager 11g, you see that the names and descriptions of the out-of-the-box action templates are slightly different, since the action templates in Oracle Adaptive Access Manager 11g are globalized and hence the difference. -
Policies are designed to help evaluate and handle business activities or potentially risky activities that are encountered in day-to-day operation.
-
Collections of items used in rules, user groups, and action and alert groups are shipped with OAAM.
If you need to customize any properties, you should import the snapshot into your new test system, make the changes, export the snapshot, and import it into your new system. Alternatively you can import the snapshot on the new system and make the property changes directly, thereby eliminating the test system completely.
Note:
For customers who are upgrading from 11.1.1.3.0 to 11.1.2: Do not import the snapshot. This procedure is only for first time initial setup. Importing a snapshot overwrites the existing environment and replaces it with a new one. For upgrades, import separate zip files for the entities, definitions, or policies.For upgrading policies, components, and configurations, perform a backup, and then import the separate file. The following are available:
-
Base policies are shipped in the
oaam_policies.zipfile, which is located in the MW_HOME/IDM_ORACLE_HOME/oaam/initdirectory -
Configurable action templates are shipped in the
OOTB_Configurable_Actions.zipfile, which is located in the MW_HOME/IDM_ORACLE_HOME/oaam/initdirectory. -
Base-authentication required entities are shipped in the
Auth_EntityDefinition.zipfile, which is located in the MW_HOME/IDM_ORACLE_HOME/oaam/initdirectory. -
Default patterns are shipped in the
OOB_Patterns.zipfile, which is located in the MW_HOME/IDM_ORACLE_HOME/oaam/initdirectory
2.7 Importing IP Location Data
IP location data is used by risk policies to determine the risk of fraud associated with a given IP address (location).
To be able to determine location of the login or transaction, this data must be uploaded to an OAAM database. For information on loading the data into the OAAM database, see Section 26.3, "Importing IP Location Data."
2.8 Enabling OTP
For information on enabling OTP, see Section 8, "Setting Up OTP Anywhere."
2.9 Setting the Time Zone Used for All Time Stamps in the OAAM Administration Console
A time zone identifies an area that always shares the same local time.
Time zones are used throughout Oracle Adaptive Access Manager for a variety of purposes. A time stamp can indicate when an alert was generated, the process start and end dates of a job, search pages, and so on. Users often are most comfortable working in their local time zones. As the administrator, you can configure the preferred time zones for the OAAM Administration Console.
The property is a system wide time zone setting and not a per-user one. All users must be in the single time zone.
Note that time zone and the browser locale formatting are independent of each other. For example, if you set your browser to en-gb, but set your oaam.adf.time zone to America/Los_Angeles, the time stamps are formatted as per British locale formatting but the time zone is still Pacific Time.
Use the Property Editor to set oaam.adf.timezone to the desired time zone.
For example,
oaam.adf.timezone = Atlantic/Reykjavik
For instructions on using the Properties Editor, see Chapter 25, "Using the Properties Editor."
Time zone as listed in Section C.1.17, "Time Zone Properties."
2.10 Using Different Encryption Algorithms and Adding New Encryption Extensions
Out of the box supported encryption algorithms
-
AES
-
DES
-
DESede (Triple DES)
DESede is the default
To switch to different encryption
Set the property bharosa.cipher.encryption.algorithm.system.default to one of the following:
-
DES
-
AES
To use a new encryption algorithm follow these steps:
-
Write a java a class that implements the interface
com.bharosa.common.util.Password. -
Implement the methods
encrypt()anddecrypt(). -
Add an element to the
bharosa.cipher.encryption.algorithm.enumenum with the following attributes tooaam_custom.propertiesfile:-
name: Name of the algorithm
-
description: Description of the algorithm
-
classname: Fully qualified Class name of the java class developed in Step 1
-
keyRetrieval.className: Set this to
com.bharosa.common.util.cipher.CSFKeyRetrieval -
prefix.system: Prefix that will be used while encrypting (Optional)
-
alias: Alias of the encryption algorithm
-
-
Set the property
bharosa.cipher.encryption.algorithm.system.defaultto the newly added element name. -
Compile and build the jar and related property files
-
Package them as OAAM extensions war
-
Deploy the OAAM extensions war and target it to both oaam_admin and oaam_server
For details on using the OAAM extensions shared library, see Oracle Fusion Middleware Developer's Guide for Oracle Adaptive Access Manager.