3 Security Architecture
Oracle Identity Manager controls access to the application by the users to allow or prevent the users to perform various operations in the application. This is controlled by the authorization engine embedded in Oracle Identity Manager with the help of authorization policies. The purpose of authorization policies is to control user's access to Oracle Identity Manager application, which includes data, UI, and API. The authorization policies determine at runtime whether or not a particular action is allowed. Authorization policies can be defined that satisfy the authorization requirements within Oracle Identity Manager.
In Oracle Identity Manager, authorization policy management is centralized as an administrative feature. Oracle Identity Manager's authorization policy management and enforcement engine is based on an embedded version of Oracle Entitlements Server (OES), which is Oracle's entitlements administration product. These authorization policies secure access control to the Oracle Identity Manager application, thereby defining 'who can do what on what data' inside the application.
Oracle Identity Manager supports the following:
-
Use standard ADF security model for functional security and use OES best practices for data security.
-
Use a consistent architecture that supports delegated administration of various entities in Oracle Identity Manager, such as roles, organizations, entitlements, application instances, and LDAP groups.
-
Use a consistent architecture that lets backend make various security decisions, for example, who can request what, who can have what, and who needs to go through approval. This architecture facilitates the security of catalog-based request module and of converged UI and backend of self service and delegated-administration.
-
Support for a scoping mechanism for delegated administration and data security of various entities. All entities are scoped by the organization structure defined as Oracle Identity Manager metadata.
Figure 3-1 shows the architecture of OES-based authorization service:
Figure 3-1 OES-Based Authorization Service
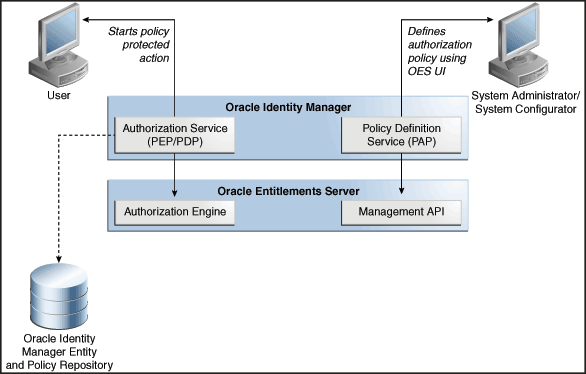
Description of "Figure 3-1 OES-Based Authorization Service"
The authorization and security model is described in the following sections:
3.1 Security Model
The security model is described in the following sections:
3.1.1 Admin Role Assignment
The new authorization model works on the basis of the admin role assignment to a user. There are two types of admin roles, global and scoped. Global admin roles, such as System Administrator, System Configuration Administrator, Catalog System Administrator, and SPML Admin, can only be assigned in the context of the Top organization only. Scoped admin roles can be assigned in the context of both Top as well as other organizations.
The Top organization is at the root of the organization hierarchy in Oracle Identity Manager. Authorization policies are created according to the admin roles. Admin roles are predefined in Oracle Identity Manager, and new admin roles cannot be added. Admin roles cannot be created, updated, deleted, searched, or requested.
Admin roles are predefined for each entity. For the users, there is no system administrator role because users must be managed by the designated delegated administrators. Each entity has the following admin roles defined for it:
-
Entity Administrator: Can manage the entire lifecycle of the entity and perform any operation on the entity.
-
Entity Viewer: Can view the entity in the catalog or request profile and request for the entity.
-
Entity Authorizer: Can view the entity in the catalog or request profiles and request for it, but does not require approval. There is no authorizer on the organization entity because organization membership cannot be requested. Similarly, there is no authorizer for the user. The user admin and user authorizer are the same.
Note:
-
Entity refers to role, user, organization, entitlement, and application instance.
-
See "Admin Roles" in the Oracle Fusion Middleware User's Guide for Oracle Identity Manager for a description of each admin role
-
Admin roles have no hierarchy. However, admin role membership organization scoping is hierarchy-aware, and can be cascaded downwards to the child organizations. Admin role membership is always given in an organization scope, and can only be assigned by the System Administrator or System Configuration Administrator. Admin roles do not have autogroup membership or role membership rules.
Note:
-
Admin roles are stored only in Oracle Identity Manager database and are not stored or synchronized in LDAP data store.
-
The admin roles cannot be requested and are never exposed to the users.
The System Administrator and System Configuration Administrator admin roles are available only to the Top organization. Therefore, only System Administrators and System Configuration Administrators can assign System Administrator and System Configuration Administrator roles because they have access to the Top organization.
The permissions a user has on a entity can be of the following types:
-
Inherent permissions: The organization to which a user is a member is referred as the Home organization for that user. A user has certain implicit permissions on the entities available to the Home organization. These permissions are automatically assigned to a user. For example, a Role Administrator does not need explicit Role Viewer privileges to view and request for roles available to the Home organization. However, to view and request for roles in another organization, Role Viewer privileges must be explicitly assigned to the same Role Administrator.
-
Management hierarchy: If User A is the manager of User B and User C, then User A has implicit permissions on User B and User C. If User B and User C are in a different organization, then User A has implicit permissions on User B and User C. User A does not need explicit privileges on the direct reports, irrespective of which organization the direct reports belong. Privileges through management hierarchy is applicable globally, and every manager is able to perform user administration operations on their reports.
Each admin role in Oracle Identity Manager has one-to-one mapping to the application roles in the OES. The application roles have associated policies that govern what permissions are allowed for users who belong to this role. If you want to change the functional and data constraints on these policies, then you must open the respective policy in Authorization Policy Management (APM) UI in OES, and modify the policy. Table 3-1 lists the admin roles in Oracle Identity Manager and the corresponding permissions allowed provided by the admin roles.
Note:
In Table 3-1, you will come across implicit permissions called org basic info, role basic info, entitlement basic info, and appinstance basic info. The basic-info permission gives the permission only to view-search the given entity. Consider the following examples:-
View Org permission provides all the permissions defined for the Organization Viewer admin role, but org basic info provides the permissions only to search and view the organization attributes.
-
The User Viewer admin role provides the basic info permission on roles, organizations, application instances, and entitlements in that scoped organization.
Table 3-1 Admin Roles and Permissions
| Admin Role in Oracle Identity Manager | Implicit Permissions | Organization Scoped Permissions | Request or Direct Operation |
|---|---|---|---|
|
User Administrator |
Organization Viewer |
Search User (attribute-level security) |
NA |
|
Role Viewer |
View User (attribute-level security) |
NA |
|
|
Entitlement Viewer |
Create User |
Direct |
|
|
AppInstance Viewer |
Delete User |
Direct |
|
|
Modify User (attribute-level security) |
Direct |
||
|
Lock User |
NA |
||
|
Unlock User |
NA |
||
|
Enable User |
Direct |
||
|
Disable User |
Direct |
||
|
Grant Role |
Direct |
||
|
Revoke Role |
Direct |
||
|
Grant Accounts |
Direct |
||
|
Revoke Accounts |
Direct |
||
|
Grant Entitlements |
Direct |
||
|
Revoke Entitlements |
Direct |
||
|
Change User Password |
NA |
||
|
Change Account Passwords |
NA |
||
|
Modify User Account |
Direct |
||
|
Enable User Account |
Direct |
||
|
Disable User Account |
Direct |
||
|
View Org |
NA |
||
|
View Role |
NA |
||
|
View Entitlements |
NA |
||
|
View Application Instance |
NA |
||
|
View Requests |
NA |
||
|
View Admin Role Memberships |
NA |
||
|
View Role Memberships |
NA |
||
|
View User Accounts |
NA |
||
|
View User Entitlements |
NA |
||
|
View Proxy |
NA |
||
|
Add Proxy |
Direct |
||
|
Delete Proxy |
Direct |
||
|
Help Desk |
Org Basic Info |
Search User (attribute-level security) |
NA |
|
Role Basic Info |
View User (attribute-level security) |
NA |
|
|
Entitlement Basic Info |
Enable User |
Request |
|
|
AppInstance Basic Info |
Disable User |
Request |
|
|
Unlock User ONLY IF locked out due to failed logins |
Direct |
||
|
Change User Password |
Direct |
||
|
View Org |
NA |
||
|
View Role |
NA |
||
|
View Entitlements |
NA |
||
|
View Application Instance |
NA |
||
|
View Requests |
NA |
||
|
View Role Memberships |
NA |
||
|
View Proxy |
NA |
||
|
View User Accounts |
NA |
||
|
View User Entitlements |
NA |
||
|
User Viewer |
Organization Viewer |
Create User |
Request |
|
Role Viewer |
Delete User |
Request |
|
|
Entitlement Viewer |
Modify User (attribute-level security) |
Request |
|
|
AppInstance Viewer |
Search User (attribute-level security) |
NA |
|
|
View User (attribute-level security) |
NA |
||
|
Enable User |
Request |
||
|
Disable User |
Request |
||
|
Grant Role |
Request |
||
|
Revoke Role |
Request |
||
|
Grant Accounts |
Request |
||
|
Revoke Accounts |
Request |
||
|
Grant Entitlements |
Request |
||
|
Revoke Entitlements |
Request |
||
|
Modify User Account |
Request |
||
|
View Org |
NA |
||
|
View Role |
NA |
||
|
View Entitlements |
NA |
||
|
View Application Instance |
NA |
||
|
View Requests |
NA |
||
|
View Role Memberships |
NA |
||
|
View Proxy |
NA |
||
|
Enable User Account |
Request |
||
|
Disable User Account |
Request |
||
|
View Admin Role Memberships |
NA |
||
|
Add Admin roles |
NA |
||
|
Delete Admin roles |
NA |
||
|
Modify Admin Role membership |
NA |
||
|
View User Accounts |
NA |
||
|
View User Entitlements |
NA |
||
|
Role Viewer |
Org Basic Info |
Grant Role |
Request |
|
User Basic Info |
Revoke Role |
Request |
|
|
View Org |
NA |
||
|
View Role |
NA |
||
|
View Users |
NA |
||
|
View Role Memberships |
NA |
||
|
Organization Viewer |
Org Basic Info |
Search Org |
NA |
|
User Basic Info |
View Org |
NA |
|
|
AppInstance Info |
View Users |
NA |
|
|
Entitlement Info |
View Role |
NA |
|
|
View AppInstance |
NA |
||
|
View Entitlement |
NA |
||
|
View All Publications |
NA |
||
|
View All Org Members |
NA |
||
|
View Admin Role & memberships |
NA |
||
|
View Accounts Provisioned to Org |
NA |
||
|
Application Instance Viewer |
User Basic Info |
Search Application Instance |
NA |
|
Org Basic Info |
View Application Instance (excluding passwords) |
NA |
|
|
Entitlement Info |
Grant Account |
Request |
|
|
Revoke Accounts |
Request |
||
|
Modify User Account |
Request |
||
|
Enable User Account |
Request |
||
|
Disable User Account |
Request |
||
|
View Org |
NA |
||
|
View User |
NA |
||
|
View AppInstance |
NA |
||
|
View Entitlements |
NA |
||
|
View User Accounts |
NA |
||
|
View User Entitlements |
NA |
||
|
Entitlement Viewer |
User Basic Info |
Search Entitlement |
NA |
|
Org Basic Info |
View Entitlement |
NA |
|
|
AppInstance Basic Info |
Grant Entitlement |
Request |
|
|
Revoke Entitlement |
Request |
||
|
View Orgs |
NA |
||
|
View Users |
NA |
||
|
View AppInstance |
NA |
||
|
View User Accounts |
NA |
||
|
View User Entitlements |
NA |
||
|
Role Administrator Note: The Role Administrator admin role can only manage the lifecycle of roles within their organization scope but does not have the permissions to grant/revoke roles to/from any user. If Role administrator needs this functionality, either assign the Role Viewer admin role if request needs to be approved, or the Role Authorizer admin role if request needs no approval, within the scope of the organizations in which they need this functionality. |
User Basic Info |
Search Role |
NA |
|
Org Basic Info |
View Role |
NA |
|
|
Create Role |
Direct |
||
|
Modify Role |
Direct |
||
|
Delete Role |
Direct |
||
|
View Role Members |
NA |
||
|
Manage Role Hierarchy |
Direct |
||
|
Publish role (only to allowed orgs) |
Direct |
||
|
Unpublish role (only to allowed orgs) |
Direct |
||
|
Manage Role Membership Rules |
Direct |
||
|
Create Role Category |
Direct |
||
|
Update Role Category |
Direct |
||
|
Delete Role Category |
Direct |
||
|
View Users |
NA |
||
|
View Orgs |
NA |
||
|
View Role Memberships |
NA |
||
|
Application Instance Administrator Note: The Application Instance Administrator admin role can only manage the lifecycle of application instances within their organization scope but does not have the permissions to grant/revoke application instances to/from any user. If Application Instance administrator needs this functionality, either assign the Application Instance Viewer admin role if request needs to be approved, or the Application Instance Authorizer admin role if request needs no approval, within the scope of the organizations in which they need this functionality. |
User Basic Info |
Create Application instance |
Direct |
|
Org Basic Info |
Modify Application instance |
Direct |
|
|
Entitlement Administrator |
Delete Application instance |
Direct |
|
|
Search Application Instance |
NA |
||
|
View Application Instance |
NA |
||
|
Publish Application Instance (only to allowed orgs) |
Direct |
||
|
Unpublish Application Instance (only to allowed orgs) |
Direct |
||
|
Publish Entitlements (only to allowed orgs) |
Direct |
||
|
Unpublish Entitlements (only to allowed orgs) |
Direct |
||
|
Access Advanced UI |
NA |
||
|
View accounts |
NA |
||
|
View Users |
NA |
||
|
View Orgs |
NA |
||
|
View User Accounts |
NA |
||
|
View User Entitlements |
NA |
||
|
Organization Administrator |
User Basic Info |
Search Org |
NA |
|
AppInstance Basic Info |
View Org |
NA |
|
|
Entitlement Basic Info |
Create Organization |
Direct |
|
|
Role Basic Info |
Modify Organization |
Direct |
|
|
Delete Organization |
Direct |
||
|
All Role Admin Privileges for Admin Roles. |
Direct |
||
|
Update Organization Hierarchy (for a specific organization) |
Direct |
||
|
Associate password policy |
Direct |
||
|
View members |
NA |
||
|
View roles published |
NA |
||
|
View app instances published |
NA |
||
|
View entitlements published |
NA |
||
|
View accounts (provisioned to org) Note: Provisioning resources to organization is allowed only to the System Administrator. |
NA |
||
|
Entitlement Administrator Note: The Entitlement Administrator admin role can only manage the lifecycle of entitlements within their organization scope but does not have the permissions to grant/revoke entitlements to/from any user. If Entitlement administrator needs this functionality, either assign the Entitlement Viewer admin role if request needs to be approved, or the Entitlement Authorizer admin role if request needs no approval, within the scope of the organizations in which they need this functionality. |
User Basic Info |
Search Entitlements |
NA |
|
AppInstance Basic Info |
View Entitlements |
NA |
|
|
Org Basic Info |
add Entitlements (API) |
Direct |
|
|
delete Entitlements (API) |
Direct |
||
|
update Entitlements (API) |
Direct |
||
|
Publish Entitlement (only to allowed orgs) |
Direct |
||
|
Unpublish Entitlement (only from allowed orgs) |
Direct |
||
|
View orgs |
NA |
||
|
View User |
NA |
||
|
View app instance |
NA |
||
|
View accounts |
NA |
||
|
View Entitlement Members |
NA |
||
|
View Published Entitlements (API) org data security applies |
NA |
||
|
Catalog System Administrator |
AppInstance Basic Info |
Edit Catalog metadata |
Direct |
|
Entitlement Basic Info |
Create Request Profiles |
Direct |
|
|
Role Basic Info |
Modify Request Profiles |
Direct |
|
|
Delete Request Profiles |
Direct |
||
|
View application instances |
NA |
||
|
View entitlements |
NA |
||
|
View roles |
NA |
||
|
Role Authorizer |
User Basic Info |
View Role |
NA |
|
Org Basic Info |
Grant Role |
Direct |
|
|
Revoke Role |
Direct |
||
|
View Orgs |
NA |
||
|
View Users |
NA |
||
|
View Role Memberships |
NA |
||
|
Application Instance Authorizer |
User Basic Info |
Search Application Instance |
NA |
|
Org Basic Info |
View Application Instance (excluding passwords) |
NA |
|
|
Grant account |
Direct |
||
|
Revoke account |
Direct |
||
|
Modify account |
Direct |
||
|
Enable account |
Direct |
||
|
Disable account |
Direct |
||
|
View Org |
NA |
||
|
View Entitlements |
NA |
||
|
View Users |
NA |
||
|
View User Accounts |
NA |
||
|
View User Entitlements |
NA |
||
|
Entitlement Authorizer |
User Basic Info |
Search Entitlement |
NA |
|
Org Basic Info |
View Entitlement |
NA |
|
|
AppInstance Basic Info |
Grant Entitlement |
Direct |
|
|
Revoke Entitlement |
Direct |
||
|
View Users |
NA |
||
|
View Orgs |
NA |
||
|
View Application Instance |
NA |
||
|
View User Accounts |
NA |
||
|
View User Entitlements |
NA |
||
|
Catalog System Administrator |
App Instance Basic Info |
Edit Catalog metadata |
Direct |
|
Entitlement Basic Info |
Create Request Profiles |
Direct |
|
|
Role Basic Info |
Modify Request Profiles |
Direct |
|
|
Delete Request Profiles |
Direct |
||
|
View Application Instances |
NA |
||
|
ViewRentitlements |
NA |
||
|
View Roles |
NA |
||
|
System Configuration Administrator |
Role Basic Info |
View Forms |
NA |
|
Org Basic Info |
Create Forms |
NA |
|
|
Application Instance Basic Info |
Modify Forms |
NA |
|
|
Entitlement Basic Info |
Delete Forms |
NA |
|
|
Import Connector |
NA |
||
|
Export Connector |
NA |
||
|
View Resource Object |
NA |
||
|
Create Resource Object |
NA |
||
|
Modify Resource Object |
NA |
||
|
Delete Resource Object |
NA |
||
|
View Application Instance |
NA |
||
|
Create Application Instance |
NA |
||
|
Modify Application Instance |
NA |
||
|
Delete Application Instance |
NA |
||
|
Publish Application Instance |
NA |
||
|
View Entitlement |
NA |
||
|
Publish Entitlement |
NA |
||
|
Delete Entitlement (using APIs) |
NA |
||
|
Modify Entitlement (using APIs) |
NA |
||
|
Add Entitlement (using APIs) |
NA |
||
|
View Approval Policies |
NA |
||
|
Create Approval Policies |
NA |
||
|
Modify Approval Policies |
NA |
||
|
Delete Approval Policies |
NA |
||
|
Access Advanced UI |
NA |
||
|
View Password Policy |
NA |
||
|
Create Password Policy |
NA |
||
|
Modify Password Policy |
NA |
||
|
Delete Password Policy |
NA |
||
|
View Notification |
NA |
||
|
Create Notification |
NA |
||
|
Delete Notification |
NA |
||
|
Modify Notification |
NA |
||
|
Add Locale to Notification |
NA |
||
|
Remove Locale To Notification |
NA |
||
|
Complete Async Event Handlers |
NA |
||
|
Orchestration Operation |
NA |
||
|
Register Plugin |
NA |
||
|
Unregister Plugin |
NA |
||
|
View scheduled Jobs |
NA |
||
|
Start Scheduler |
NA |
||
|
Stop Scheduler |
NA |
||
|
Add Task |
NA |
||
|
Modify Task |
NA |
||
|
Delete Task |
NA |
||
|
Create Trigger |
NA |
||
|
Delete Trigger |
NA |
||
|
Modify Trigger |
NA |
||
|
View Jobs |
NA |
||
|
Create Jobs |
NA |
||
|
Modify Jobs |
NA |
||
|
Delete Jobs |
NA |
||
|
Enable Jobs |
NA |
||
|
Disable Jobs |
NA |
||
|
Run-now Jobs |
NA |
||
|
Pause Jobs |
NA |
||
|
Resume Jobs |
NA |
||
|
Stop Jobs |
NA |
||
|
Reset Status |
NA |
||
|
View System Properties |
NA |
||
|
Create System Properties |
NA |
||
|
Modify System Properties |
NA |
||
|
Delete System Properties |
NA |
||
|
View Attributes |
NA |
||
|
Add Attributes |
NA |
||
|
Modify Attributes |
NA |
||
|
Delete Attributes |
NA |
||
|
Add Derived Attributes |
NA |
||
|
SPML Admin |
Create, modify, and delete users |
Request |
|
|
Search users on all the attributes |
NA |
||
|
Enable user status |
Request |
||
|
Disable user status |
Request |
||
|
Add role memberships |
Request |
||
|
Delete role memberships |
Request |
||
|
Search roles on all the attributes |
NA |
||
|
Create, modify, and delete roles |
Request |
Note:
The following permissions in Oracle Identity Manager are not governed by OES policies:-
Create / Update / Delete Access Policies
-
Add / Modify / Remove Lookup
-
Import / Export using the Deployment Manager
-
Attestation Administration
3.1.2 Attribute-Level Security for the User Attributes
Oracle Identity Manager supports attribute-level security only for user attributes. The security for all other entities is supported at the entity-instance level.
Oracle Identity Manager contains the default User Viewer, User Administrator, and User HelpDesk admin roles along with the corresponding default authorization policies in OES. The default policies allow the User Viewer and User Administrator to view and modify all the user attributes including the attributes that are added as user-defined fields (UDFs), without requiring any changes to the default policies.
The User Viewer policy has the default constraint set as the deniedattributes obligation in the policy, and by default, it contains NULL list for the attributes. Therefore, all users belonging to the User Viewer role are allowed to view all user attributes by default.
The User Administrator policy has the default constraint set as the deniedattributes obligation in the policy with a NULL list of attributes, and all users belonging to the User Administrator role are allowed to view and modify all user attributes by default. The User HelpDesk policy also has the default constraint set as the deniedattributes obligation in the policy with a NULL list of attributes.
When you add a new UDF, there is no need to change the User Viewer policy. This is because, this policy has default constraint set as deniedattributes, and by default a NULL list for the attributes. This automatically enables the users belonging to the User Viewer role to view the UDFs. There is no need to change the User Administrator policy because the constraint to view and modify all attributes automatically enables the users belonging to the User Administrator role to view and modify these UDFs.
Only if you want to restrict certain attributes to be viewed or modified, then you can change the policies in OES to include such attributes in the deny list. When you want to restrict the list of attributes to be viewed by the User Viewer role or restrict the list of attributes to be viewed and modified by the User Administrator role, you must open the respective policy in the APM UI in OES, and include the list of attributes to be restricted in the deny attribute list of the policy. For example, if you want to restrict the Salary user attribute to be available only for the User Administrator role and not for the User Viewer role, then use the APM UI and modify the User Viewer role to include the Salary attribute in the deny list. When Oracle Identity Manager queries OES to provide a list of attributes for the User Viewer role, OES provides all user attributes but excludes the attributes specified in the Deny List, which is the Salary attribute in this example. Here, there are no changes required for User Admin policy because the 'View and Modify All Attributes' returns the Salary information to be viewed and modified by the users belonging to the User Administrator role.
To change the denied attributes, open the required OES policy in APM UI. In this example, an OES policy by name OrclOIMUserViewerDirectWithObligationPolicy has been opened that gives the permission to view-search user for the User Viewer admin role, as shown in Figure 3-2:
Figure 3-2 The OrclOIMUserViewerDirectWithObligationPolicy
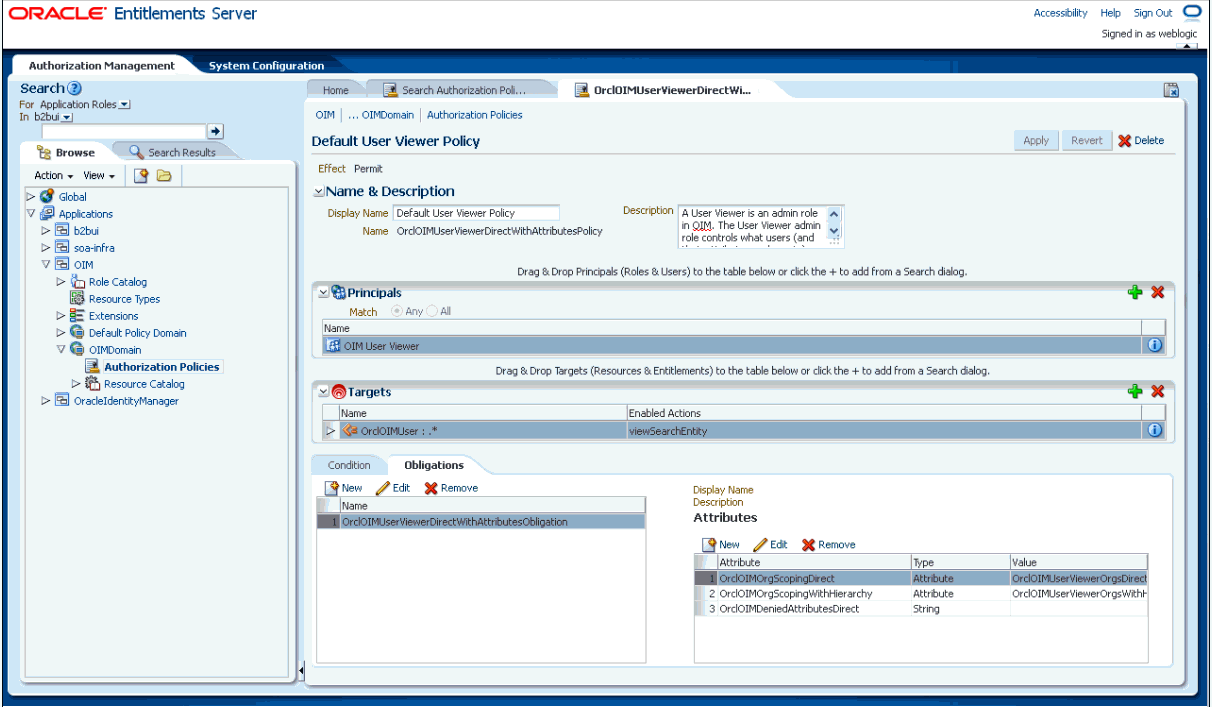
Description of "Figure 3-2 The OrclOIMUserViewerDirectWithObligationPolicy"
You can click the OrclOIMDeniedAttributesDirect attribute in edit mode, and then provide the denied attributes, separated by commas, as shown in :
Figure 3-3 The Edit Obligation Attribute Dialog Box
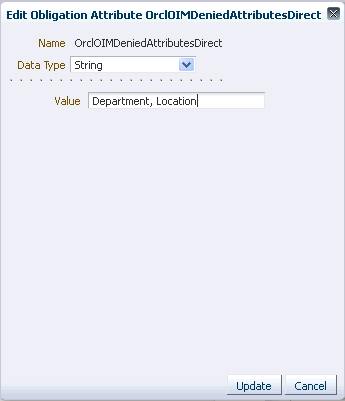
Description of "Figure 3-3 The Edit Obligation Attribute Dialog Box"
3.1.3 Policy Obligations
If a user has multiple roles that have different authorization policies applicable in the same context, then the user's access rights are the cumulative rights across those policies. For example, the authorization check for the permission to search for users returns a list of obligations. This is a list of obligations from each applicable authorization policy. These obligations from multiple policies are combined to get a unified search result.
The following types of obligations are returned as a result of multiple authorization policies:
-
OrclOIMOrgScopingDirect: This is used to search the given entity for the intent-based search. This is supported only for view-search.
-
OrclOIMOrgScopingWithHierarchy: This considers the hierarchy of the Admin Role organization scoping, and it can search entities in down hierarchy. This allows users to view and modify user profiles without approval as applicable for the organization in which the user has the appropriate admin role, and its suborganizations. This is controlled by the Hierarchy Aware data constraint.
-
OrclOIMNeedApproval: This obligation defines if the authorization policies are applicable, then the operation requires approval or not. If the value of this flag is true, then a request is created. If the value is false, then it is a direct operation.
-
OrclOIMUserManagementScoping: This is used for making the search criteria to search in the management chain of the user.
-
OrclOIMDeniedAttributesWithoutApproval: This defines the obligation for the user attributes that are denied for modification without a request approval.
-
OrclOIMDeniedAttributesDirect: This defined the obligation for the user attributes that are denied for the view user operation as a direct operation.
-
OrclOIMDeniedAttributesWithApproval: This defines the obligation for the user attributes that are denied for modification with a request approval.
The following are examples of policy obligations returned as a result of multiple authorization policies:
-
The user with role viewer admin role for an organization need approval to grant a role to the user. The role viewer can view all users in the organization with hierarchy as a result of OrgScopingWithHierarchy policy obligation. For the same organization, granting a role to a user is a direct operation for a user with the role authorizer admin role.
-
Suppose there are two admin roles assigned to a user in the same organization scoping, User Viewer and User Administrator. When both the users try to modify a user, the first admin role policy returns approval-required, and other policy returns that approval is not required. As a result, no request would be raised, and the cumulative effect of two approval-required obligations is NO-approval required.
-
As a result of the OrgScopingDirect policy obligation, a user with the role authorizer admin role can view all users in an organization. The same user with role authorizer admin role can be denied modifying a few attributes by the DeniedAttributesWithApproval policy obligation, and as a result, the attributes are not displayed to the user.
-
Suppose a user is a Role Viewer in Org1 and Role Authorizer in Org2. Then if the user searches for the roles, then the obligation returned from policy1 is OrgScopingDirect = org1 and OrgScopingDirect = org2. Therefore, roles will be returned from both the organizations.
3.2 Functional and Data Security Mapping
Table 3-2 lists the admin roles and the corresponding application roles, default authorization policies, and policy obligations.
Table 3-2 Default Authorization Policies
| Admin Role in Oracle Identity Manager | Application Role in OES | Policy Name | Description | Obligation |
|---|---|---|---|---|
|
Authenticated Role |
authenticated-role |
Role Category View Policy |
This Policy controls if authenticated users can view role categories. |
|
|
Role Administrator |
OIM Role Administrator |
OIM RoleCategory RoleAdmin Policy |
This policy controls the creation, modification, and deletion of role categories by the Role Administrator admin role. |
|
|
Catalog Administrator |
OIM Catalog Administrator Role |
Catalog Administration Policy |
Catalog Administrator is a global admin role. Catalog Administrators are responsible for managing catalog items and their metadata. This Policy specifies the actions that a member of the role can take. |
|
|
Organization Administrator |
OIM Organization Administrator |
Organization Administration Policy |
This policy specifies the actions that an Organization Administrator can perform. This policy can also be configured to require an approval. |
OrclOIMOrgScopingWithHierarchy=OrclOIMOrganizationAdminOrgsWithHierarchy OrclOIMOrgScopingDirect=OrclOIMOrganizationAdminOrgsDirect |
|
Organization Administrator |
OIM Organization Administrator |
OIM OrgAdministrator Basic Info Application Instance Direct Policy |
This policy specifies the direct view and search permissions on application instances by Organization Administrators. |
OrclOIMOrgScopingDirect=OrclOIMOrganizationAdminOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMOrganizationAdminOrgsWithHierarchy |
|
Organization Administrator |
OIM Organization Administrator |
OIM OrgAdministrator Basic Info IT Resource Entitlement Direct Policy |
This policy specifies the direct view and search permissions on entitlements by Organization Administrators. |
OrclOIMOrgScopingWithHierarchy=OrclOIMOrganizationAdminOrgsWithHierarchy OrclOIMOrgScopingDirect=OrclOIMOrganizationAdminOrgsDirect |
|
Organization Administrator |
OIM Organization Administrator |
OIM OrgAdministrator Basic Info Role Direct Policy |
This policy specifies the direct view and search permissions on roles by Organization Administrators. |
OrclOIMOrgScopingWithHierarchy=OrclOIMOrganizationAdminOrgsWithHierarchy OrclOIMOrgScopingDirect Attribute=OrclOIMOrganizationAdminOrgsDirect |
|
Organization Administrator |
OIM Organization Administrator |
OIM OrgAdministrator Basic Info User Direct WithAttributes Policy |
This policy specifies the direct view and search permissions on users and user attributes by Organization Administrators. |
OrclOIMOrgScopingDirect=OrclOIMOrganizationAdminOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMOrganizationAdminOrgsWithHierarchy OrclOIMDeniedAttributesDirect= |
|
Organization Viewer |
OIM Organization Viewer |
Organization Viewer Policy for View Actions |
Organization Viewer is an organization-scoped admin role. This policy specifies the actions that members of this role can take, which do not require approval. By default, the policy specifies that all view actions do not require approval. |
OrclOIMOrgScopingDirect=OrclOIMOrganizationViewerOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMOrganizationViewerOrgsWithHierarchy |
|
Organization Viewer |
OIM Organization Viewer |
OIM OrgViewer Basic Info Application Instance Direct Policy |
This policy specifies the direct view and search permissions on application instances by Organization Viewers. |
OrclOIMOrgScopingDirect=OrclOIMOrganizationViewerOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMOrganizationViewerOrgsWithHierarchy |
|
Organization Viewer |
OIM Organization Viewer |
OIM OrgViewer Basic Info IT Resource Entitlement Direct Policy |
This policy specifies the direct view and search permissions on entitlements by Organization Viewers. |
OrclOIMOrgScopingWithHierarchy=OrclOIMOrganizationViewerOrgsWithHierarchy OrclOIMOrgScopingDirect=OrclOIMOrganizationViewerOrgsDirect |
|
Organization Viewer |
OIM Organization Viewer |
OIM OrgViewer Basic Info Role Direct Policy |
This policy specifies the direct view and search permissions on roles by Organization Viewers. |
OrclOIMOrgScopingDirect=OrclOIMOrganizationViewerOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMOrganizationViewerOrgsWithHierarchy |
|
Organization Viewer |
OIM Organization Viewer |
OIM OrgViewer Basic Info User Direct WithAttributes Policy |
This policy specifies the direct view and search permissions on users and user attributes by Organization Viewers. |
OrclOIMOrgScopingDirect=OrclOIMOrganizationViewerOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMOrganizationViewerOrgsWithHierarchy OrclOIMDeniedAttributesDirect= |
|
Application Instance Administrator |
OIM Application Instance Administrator Role |
Application Instance Administrator Policy |
The Application Instance Administrator admin role is an organization-scoped role. This policy controls the actions that members of the role can perform and whether or not the actions require approval. |
OrclOIMOrgScopingDirect=OrclOIMApplicationInstanceAdminOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMApplicationInstanceAdminOrgsWithHierarchy |
|
Application Instance Administrator |
OIM Application Instance Administrator Role |
OIM ApplicationInstanceAdministrator Basic Info User Direct WithAttributes Policy |
This policy specifies the direct view and search permissions on users and user attributes by Application Instance Administrators. |
OrclOIMOrgScopingWithHierarchy=OrclOIMApplicationInstanceAdminOrgsWithHierarchy OrclOIMOrgScopingDirect=OrclOIMApplicationInstanceAdminOrgsDirect OrclOIMDeniedAttributesDirect= |
|
Application Instance Administrator |
OIM Application Instance Administrator Role |
OIM ApplicationInstanceAdministrator Basic Info Organization Direct Policy |
This policy specifies the direct view and search permissions on organizations by Application Instance Administrators. |
OrclOIMOrgScopingDirect=OrclOIMApplicationInstanceAdminOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMApplicationInstanceAdminOrgsWithHierarchy |
|
Application Instance Authorizer |
OIM Application Instance Authorizer Role |
Application Instance Authorizer Policy |
An Application Instance Authorizer is an admin role in Oracle Identity Manager. Application Instance Authorizers can grant/revoke/modify application instances to user accounts without approval. This policy controls whether or not an Application Instance Authorizer can view/search application instances and application instance attributes. |
OrclOIMOrgScopingWithHierarchy=OrclOIMApplicationInstanceAuthorizerOrgsWithHierarchy OrclOIMOrgScopingDirect=OrclOIMApplicationInstanceAuthorizerOrgsDirect |
|
Application Instance Authorizer |
OIM Application Instance Authorizer Role |
Application Instance Authorizer Policy |
Application Instance Authorizers can grant/revoke/modify application instances to user accounts without approval. This policy controls whether or not an Application Instance Authorizer can view/search application instances and application instance attributes. |
OrclOIMOrgScopingWithHierarchy=OrclOIMApplicationInstanceAuthorizerOrgsWithHierarchy OrclOIMOrgScopingDirect=OrclOIMApplicationInstanceAuthorizerOrgsDirect OrclOIMNeedApproval=false |
|
Application Instance Authorizer |
OIM Application Instance Authorizer Role |
OIM ApplicationInstanceAuthorizer Basic Info User Direct WithAttributes Policy |
This policy specifies the direct view and search permissions on users and user attributes by Application Instance Authorizers. |
OrclOIMDeniedAttributesDirect= OrclOIMOrgScopingWithHierarchy=OrclOIMApplicationInstanceAuthorizerOrgsWithHierarchy OrclOIMOrgScopingDirect=OrclOIMApplicationInstanceAuthorizerOrgsDirect |
|
Application Instance Authorizer |
OIM Application Instance Authorizer Role |
OIM ApplicationInstanceAuthorizer Basic Info Organization Direct Policy |
This policy specifies the direct view and search permissions on organizations by Application Instance Authorizers. |
OrclOIMOrgScopingDirect=OrclOIMApplicationInstanceAuthorizerOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMApplicationInstanceAuthorizerOrgsWithHierarchy |
|
Application Instance Viewer |
OIM Application Instance Viewer Role |
OIM Application Instance Viewer Direct Policy |
This policy specifies the operations that Application Instance Viewers can perform directly. |
OrclOIMOrgScopingWithHierarchy=OrclOIMApplicationInstanceViewerOrgsWithHierarchy OrclOIMOrgScopingDirect=OrclOIMApplicationInstanceViewerOrgsDirect |
|
Application Instance Viewer |
OIM Application Instance Viewer Role |
Application Instance Viewer Policy for Request actions |
The Application Instance Viewer admin role is an organization-scoped role. This policy controls the actions that members of the role can perform and whether or not the actions require approval. |
OrclOIMOrgScopingDirect=OrclOIMApplicationInstanceViewerOrgsDirect OrclOIMNeedApproval=true OrclOIMOrgScopingWithHierarchy=OrclOIMApplicationInstanceViewerOrgsWithHierarchy |
|
Application Instance Viewer |
OIM Application Instance Viewer Role |
OIM ApplicationInstanceViewer Basic Info IT Resource Entitlement Direct Policy |
This policy specifies the direct view and search permissions on entitlements by Application Instance Viewers. |
OrclOIMOrgScopingDirect=OrclOIMApplicationInstanceViewerOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMApplicationInstanceViewerOrgsWithHierarchy |
|
Application Instance Viewer |
OIM Application Instance Viewer Role |
OIM ApplicationInstanceViewer Basic Info User Direct WithAttributes Policy |
This policy specifies the direct view and search permissions on users and user attributes by Application Instance Viewers. |
OrclOIMDeniedAttributesDirect= OrclOIMOrgScopingWithHierarchy=OrclOIMApplicationInstanceViewerOrgsWithHierarchy OrclOIMOrgScopingDirect=OrclOIMApplicationInstanceViewerOrgsDirect |
|
Application Instance Viewer |
OIM Application Instance Viewer Role |
OIM ApplicationInstanceViewer Basic Info Organization Direct Policy |
This policy specifies the direct view and search permissions on organizations by Application Instance Viewers. |
OrclOIMOrgScopingWithHierarchy=OrclOIMApplicationInstanceViewerOrgsWithHierarchy OrclOIMOrgScopingDirect=OrclOIMApplicationInstanceViewerOrgsDirect |
|
Authenticated Role |
authenticated-role |
Home Org Policy for Application Instances |
This Policy allows a user to implicitly view the application instances and application instance attributes that have been published to the user's home organization. |
OrclOIMOrgScopingDirect=OrclOIMUserHomeOrgs |
|
Authenticated Role |
authenticated-role |
Application Instance Policy for Home Org |
This policy controls the actions that a user can take on accounts in the user's Home Organization and whether these actions require approval. By default, actions by non-User Administrators on accounts in the same Home Organization require approval. |
OrclOIMOrgScopingDirect=OrclOIMUserHomeOrgs OrclOIMNeedApproval=true |
|
System Configuration Administrator |
OIM System Configurator |
Password Policy Management Policy |
This policy controls the password policy management actions that members of the System Administrator or System Configuration Administrator can take. |
|
|
Organization Administrator |
OIM Organization Administrator |
OIM Password Policy OrgAdmin ViewSearch Policy |
This policy specifies the view and search permissions on password policies by Organization Administrators. |
|
|
Entitlement Administrator |
OIM Entitlement Administrator |
Entitlement Administrator Policy for entitlement management actions |
An Entitlement Administrator is an organization scoped admin role in Oracle Identity Manager. This policy controls the actions a member of this role can perform without requiring approval. |
OrclOIMOrgScopingDirect=OrclOIMEntitlementAdminOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMEntitlementAdminOrgsWithHierarchy |
|
Entitlement Administrator |
OIM Entitlement Administrator |
OIM EntitlementAdministrator Basic Info Application Instance Direct Policy |
This policy specifies the direct view and search permissions on application instances by Entitlement Administrators. |
OrclOIMOrgScopingWithHierarchy=OrclOIMEntitlementAdminOrgsWithHierarchy OrclOIMOrgScopingDirect=OrclOIMEntitlementAdminOrgsDirect |
|
Entitlement Administrator |
OIM Entitlement Administrator |
OIM EntitlementAdministrator Basic Info User Direct WithAttributes Policy |
This policy specifies the direct view and search permissions on users and user attributes by Entitlement Administrators. |
OrclOIMOrgScopingWithHierarchy=OrclOIMEntitlementAdminOrgsWithHierarchy OrclOIMOrgScopingDirect=OrclOIMEntitlementAdminOrgsDirect OrclOIMDeniedAttributesDirect= |
|
Entitlement Administrator |
OIM Entitlement Administrator |
OIM EntitlementAdministrator Basic Info Organization Direct Policy |
This policy specifies the direct view and search permissions on organizations by Entitlement Administrators. |
OrclOIMOrgScopingWithHierarchy=OrclOIMEntitlementAdminOrgsWithHierarchy OrclOIMOrgScopingDirect=OrclOIMEntitlementAdminOrgsDirect |
|
Entitlement Authorizer |
OIM Entitlement Authorizer |
Entitlement Authorizer Policy for View Actions |
An Entitlement Authorizer is an admin role in Oracle Identity Manager. Entitlement Authorizers can grant/revoke/modify entitlements to user accounts without approval. This policy controls whether an Entitlement Authorizer can view/search entitlements and entitlement attributes. |
OrclOIMOrgScopingWithHierarchy=OrclOIMEntitlementAuthorizerOrgsWithHierarchy OrclOIMOrgScopingDirect=OrclOIMEntitlementAuthorizerOrgsDirect |
|
Entitlement Authorizer |
OIM Entitlement Authorizer |
Entitlement Authorizer Policy for Request Actions |
Entitlement Authorizers can grant/revoke/modify entitlements to user accounts without approval. This policy controls the actions that can be performed by an Entitlement Authorizer as part of a request. This policy is used by the request engine to determine if a particular action taken by the Entitlement Authorizer is direct or through request. |
OrclOIMOrgScopingDirect=OrclOIMEntitlementAuthorizerOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMEntitlementAuthorizerOrgsWithHierarchy OrclOIMNeedApproval=false |
|
Entitlement Authorizer |
OIM Entitlement Authorizer |
OIM EntitlementAuthorizer Basic Info Application Instance Direct Policy |
This policy specifies the direct view and search permissions on application instances by Entitlement Authorizers. |
OrclOIMOrgScopingDirect=OrclOIMEntitlementAuthorizerOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMEntitlementAuthorizerOrgsWithHierarchy |
|
Entitlement Authorizer |
OIM Entitlement Authorizer |
OIM EntitlementAuthorizer Basic Info User Direct WithAttributes Policy |
This policy specifies the direct view and search permissions on users and user attributes by Entitlement Authorizers. |
OrclOIMDeniedAttributesDirect= OrclOIMOrgScopingDirect=OrclOIMEntitlementAuthorizerOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMEntitlementAuthorizerOrgsWithHierarchy |
|
Entitlement Authorizer |
OIM Entitlement Authorizer |
OIM EntitlementAuthorizer Basic Info Organization Direct Policy |
This policy specifies the direct view and search permissions on organizations by Entitlement Authorizers. |
OrclOIMOrgScopingDirect=OrclOIMEntitlementAuthorizerOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMEntitlementAuthorizerOrgsWithHierarchy |
|
Entitlement Viewer |
OIM Entitlement Viewer |
Entitlement Viewer Policy for View Actions |
An Entitlement Viewer is an organization-scoped admin role in Oracle Identity Manager. This Policy specifies whether an entitlement viewer can search for entitlements and view its attributes without approval. By default, no approval is required. |
OrclOIMOrgScopingDirect=OrclOIMEntitlementViewerOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMEntitlementViewerOrgsWithHierarchy |
|
Entitlement Viewer |
OIM Entitlement Viewer |
OIM Entitlement Viewer Policy for Request Actions |
This policy is an organization-scoped policy, which allows members of the role to request granting, revoking, and modifying entitlements that are published to their organizations. An entitlement grant or revoke by an Entitlement Viewer results in a request. |
OrclOIMOrgScopingWithHierarchy=OrclOIMEntitlementViewerOrgsWithHierarchy OrclOIMOrgScopingDirect=OrclOIMEntitlementViewerOrgsDirect OrclOIMNeedApproval=true |
|
Entitlement Viewer |
OIM Entitlement Viewer |
OIM EntitlementViewer Basic Info Application Instance Direct Policy |
This policy specifies the direct view and search permissions on application instances by Entitlement Viewers. |
OrclOIMOrgScopingDirect=OrclOIMEntitlementViewerOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMEntitlementViewerOrgsWithHierarchy |
|
Entitlement Viewer |
OIM Entitlement Viewer |
OIM EntitlementViewer Basic Info User Direct WithAttributes Policy |
This policy specifies the direct view and search permissions on users and user attributes by Entitlement Viewers. |
OrclOIMOrgScopingWithHierarchy=OrclOIMEntitlementViewerOrgsWithHierarchy OrclOIMDeniedAttributesDirect= OrclOIMOrgScopingDirect=OrclOIMEntitlementViewerOrgsDirect |
|
Entitlement Viewer |
OIM Entitlement Viewer |
OIM EntitlementViewer Basic Info Organization Direct Policy |
This policy specifies the direct view and search permissions on organizations by Entitlement Viewers. |
OrclOIMOrgScopingDirect=OrclOIMEntitlementViewerOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMEntitlementViewerOrgsWithHierarchy |
|
Authenticated Role |
authenticated-role |
Home Org Policy for viewing Entitlements |
This Policy allows a user to implicitly view the entitlements and entitlement attributes that have been published to the user's home organization. |
OrclOIMOrgScopingDirect =OrclOIMUserHomeOrgs |
|
Authenticated Role |
authenticated-role |
HomeOrg Policy for actions on Entitlements |
This policy specifies the actions that a user can take on the entitlements provisioned to another user in the same home organization, and whether these actions require approval. By default, approval is required. |
OrclOIMNeedApproval=true OrclOIMOrgScopingDirect=OrclOIMUserHomeOrgs |
|
Catalog Administrator |
OIM Catalog Administrator Role |
Request Profile Management Policy |
This policy controls the actions that a member of the Catalog Administrator role can perform while managing request profiles. |
|
|
Authenticated Role |
authenticated-role |
OIM Request Profile All User ViewSearch Policy |
This policy controls the view and search permissions on requests catalogs by all users. |
|
|
System Configuration Administrator |
OIM System Configurator |
OIM Approval Policy Administrator Policy |
This policy controls the permissions for approval policy administration by the System Configuration Administrator. |
|
|
System Configuration Administrator |
OIM System Configurator |
Diagnostic Dashboard Administrator Policy |
The Diagnostic Dashboard is a diagnostic utility for Oracle Identity Manager. This policy specifies who can access the Diagnostic Dashboard and what actions they can perform. |
|
|
System Configuration Administrator |
OIM System Configurator |
OIM resource object administration Policy |
This policy controls the permissions for resource object administration by the System Configuration Administrators. |
|
|
System Configuration Administrator |
OIM System Configurator |
Notification Administrator Policy |
This policy specifies the actions that a notification administrator can perform. |
|
|
System Configuration Administrator |
OIM System Configurator |
OIM Platform Service Administrator Policy |
This policy specifies the actions that a platform service administrator can perform. |
|
|
System Configuration Administrator |
OIM System Configurator |
Plugin Administrator Policy |
This policy controls who can register and unregister plug-ins. By default, only members of the System Administrator and System Configuration Administrator admin roles can register and unregister plug-ins. |
|
|
System Configuration Administrator |
OIM System Configurator |
System Configurator Policy for System Admin Console |
This policy controls whether members of the System Configuration Administrator admin role can access Oracle Identity System Administration. |
|
|
Application Instance Administrator |
OIM Application Instance Administrator |
OIM UI App Instance Administrator Policy |
This policy specifies the actions that an Application Instance Administrator can perform in the UI. |
|
|
Entitlement Administrator |
OIM Entitlement Administrator |
OIM UI Entitlement Administrator Policy |
This policy specifies the actions that an Entitlement Administrator can perform in the UI. |
|
|
Application Instance Administrator System Configuration Administrator |
OIM Application Instance Administrator OIM System Configurator |
Request Dataset Policy |
This Policy is used to control the actions that members of the System Configuration Administrator role can perform on request datasets. |
OrclOIMOrgScopingDirect=OrclOIMSystemConfiguratorOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMSystemConfiguratorOrgsWithHierarchy |
|
System Configuration Administrator |
OIM System Configurator |
Reconciliation Administrator Policy |
A Reconciliation Administrator can perform actions on reconciliation events. This policy controls what actions a Reconciliation Administrator can perform. |
|
|
System Configuration Administrator |
OIM System Configurator |
OIM Scheduler Administrator Policy |
A Scheduler Administrator can perform actions on scheduled tasks. This policy controls what actions a Scheduler Administrator can perform. |
|
|
System Configuration Administrator |
OIM System Configurator |
System Properties Administration Policy |
This policy specifies the actions and determines who can perform them as part of managing the Oracle Identity Manager system properties. The default behavior allows only the System Configuration Administrators to manage the system properties. |
|
|
System Configuration Administrator |
OIM System Configurator |
OIM User Management Configuration Administrator Policy |
This policy controls what user configuration capabilities are available to a member of the System Configuration Administrator role. |
|
|
Authenticated Role |
authenticated-role |
Home Org Policy for Organizations |
This policy allows a user to implicitly view the application instances, accounts, entitlements and entitlement attributes, and users that have been published to the user's home organization. |
OrclOIMOrgScopingDirect=OrclOIMUserHomeOrgs OrclOIMNeedApproval=true |
|
User Administrator |
OIM User Admin |
User Admin Policy for user modification |
User Admin is an organization-scoped admin role. Members of this role manage users, and their actions do not require approval. This policy specifies whether User Administrators can modify user attributes, the attributes they cannot modify, and whether their modification requires approval. By default, members of this role can modify all user attributes, and their actions do not require approval. |
OrclOIMDeniedAttributesWithoutApproval= OrclOIMNeedApproval=false OrclOIMOrgScopingDirect=OrclOIMUserAdminOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMUserAdminOrgsWithHierarchy |
|
User Administrator |
OIM User Admin |
User Administrator Policy for Admin Actions |
A User Administrator is an organization-scoped admin role. Members of this role can perform actions on users in their organizations' scope without approval. This policy covers all actions other than view actions. It returns an obligation indicating that approval is not required for the enabled actions. |
OrclOIMNeedApproval=false OrclOIMOrgScopingWithHierarchy=OrclOIMUserAdminOrgsWithHierarchy OrclOIMOrgScopingDirect=OrclOIMUserAdminOrgsDirect |
|
User Administrator |
OIM User Admin |
OIM User Admin Policy direct with attributes |
This policy controls the direct actions that the User Administrators can perform on users and user attributes. |
OrclOIMDeniedAttributesDirect= OrclOIMOrgScopingWithHierarchy=OrclOIMUserAdminOrgsWithHierarchy OrclOIMOrgScopingDirect=OrclOIMUserAdminOrgsDirect |
|
User Administrator |
OIM User Admin |
User Admin Policy for non-requestable actions |
User Administrator is an organization-scoped admin role. Members of this role manage users, and their actions do not require approval. This Policy specifies the actions a member of the role can perform on a user, which do not require approval. |
OrclOIMOrgScopingDirect=OrclOIMUserAdminOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMUserAdminOrgsWithHierarchy |
|
User Help Desk |
OIM User Password Admin |
Help Desk Policy for managing user status |
This policy controls the actions that member of the User Help Desk admin role can take as part of managing a user's account status and whether it requires approvals. By default, members of the role can enable/disable a user's status without approval. |
OrclOIMOrgScopingWithHierarchy=OrclOIMUserHelpDeskOrgsWithHierarchy OrclOIMOrgScopingDirect=OrclOIMUserHelpDeskOrgsDirect OrclOIMNeedApproval=true |
|
User Help Desk |
OIM User Password Admin |
OIM User HelpDesk Policy for modify user accounts |
This policy controls the actions that a member of the User Help Desk admin role can take as part of modifying a user's account. |
OrclOIMNeedApproval=false OrclOIMOrgScopingDirect=OrclOIMUserHelpDeskOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMUserHelpDeskOrgsWithHierarchy |
|
User Help Desk |
OIM User Password Admin |
Help Desk Admin Policy for User search |
User Help Desk is an organization-scoped admin role. Members of this role can search for users, modify user profiles, and change user passwords. This policy specifies whether members of the role can search for users and whether they can view any user attributes. By default, members of this admin role can see all user attributes. |
OrclOIMOrgScopingDirect=OrclOIMUserHelpDeskOrgsDirect OrclOIMDeniedAttributesDirect= OrclOIMOrgScopingWithHierarchy=OrclOIMUserHelpDeskOrgsWithHierarchy |
|
User Help Desk |
OIM User Password Admin |
Help Desk User Policy for Password Management |
Members of the User Help Desk admin role can search for users, modify user profiles, and change user passwords. This policy specifies whether members of the role can manage user passwords, lock/unlock accounts, and view requests raised by users |
OrclOIMOrgScopingDirect=OrclOIMUserHelpDeskOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMUserHelpDeskOrgsWithHierarchy |
|
User Help Desk |
OIM User Password Admin |
OIM User HelpDesk UnLockUser Policy direct |
This policy determines if the User Help Desk can directly unlock a user account. |
OrclOIMOrgScopingWithHierarchy=OrclOIMUserHelpDeskOrgsWithHierarchy OrclOIMOrgScopingDirect=OrclOIMUserHelpDeskOrgsDirect OrclOIMAllowOnlyIfLockedByFailLoginAttempts=true |
|
User Help Desk |
OIM User Password Admin |
OIM HelpDesk Basic Info Application Instance Direct Policy |
This policy specifies the direct view and search permissions on application instances by members of the User Help Desk admin role. |
OrclOIMOrgScopingDirect=OrclOIMUserHelpDeskOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMUserHelpDeskOrgsWithHierarchy |
|
User Help Desk |
OIM User Password Admin |
OIM HelpDesk Basic Info IT Resource Entitlement Direct Policy |
This policy specifies the direct view and search permissions on IT resource entitlements by members of the User Help Desk admin role. |
OrclOIMOrgScopingWithHierarchy=OrclOIMUserHelpDeskOrgsWithHierarchy OrclOIMOrgScopingDirect=OrclOIMUserHelpDeskOrgsDirect |
|
User Help Desk |
OIM User Password Admin |
OIM HelpDesk Basic Info Role Direct Policy |
This policy specifies the direct view and search permissions on roles by members of the User Help Desk admin role. |
OrclOIMOrgScopingWithHierarchy=OrclOIMUserHelpDeskOrgsWithHierarchy OrclOIMOrgScopingDirect=OrclOIMUserHelpDeskOrgsDirect |
|
User Help Desk |
OIM User Password Admin |
OIM HelpDesk Basic Info Organization Direct Policy |
This policy specifies the direct view and search permissions on organizations by members of the User Help Desk admin role. |
OrclOIMOrgScopingWithHierarchy=OrclOIMUserHelpDeskOrgsWithHierarchy OrclOIMOrgScopingDirect=OrclOIMUserHelpDeskOrgsDirect |
|
User Viewer |
OIM User Viewer |
User Viewer Policy for Request Actions |
User Viewer is an organization-scoped admin role. This policy controls whether a member of the admin role can modify a user's profile and whether the action requires approval or not. By default, user modification requests submitted by members of the User Viewer role require approval. |
OrclOIMNeedApproval=true OrclOIMDeniedAttributesWithApproval= OrclOIMOrgScopingDirect=OrclOIMUserViewerOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMUserViewerOrgsWithHierarchy |
|
User Viewer |
OIM User Viewer |
User Viewer Policy for User management |
This policy controls what actions can be performed by a member of the User Viewer role, and whether or not those actions require approval. |
OrclOIMOrgScopingWithHierarchy=OrclOIMUserViewerOrgsWithHierarchy OrclOIMOrgScopingDirect=OrclOIMUserViewerOrgsDirect OrclOIMNeedApproval=true |
|
User Viewer |
OIM User Viewer |
Default User Viewer Policy |
The User Viewer admin role controls what users and their attributes and grants an authenticated user can search for and view. |
OrclOIMOrgScopingDirect=OrclOIMUserViewerOrgsDirect OrclOIMDeniedAttributesDirect= OrclOIMOrgScopingWithHierarchy=OrclOIMUserViewerOrgsWithHierarchy |
|
User Viewer |
OIM User Viewer |
User Viewer Policy |
This policy controls the attributes and the relationships of a user that a member of the User Viewer admin role can view. |
OrclOIMOrgScopingDirect=OrclOIMUserViewerOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMUserViewerOrgsWithHierarchy |
|
Authenticated Role |
authenticated-role |
Management Chain Policy for user modification |
This policy specifies whether a user can modify another user in the user's management chain and if the action requires approval. The policy also specifies which user attributes do not require approval. By default, modification of any user attribute excluding password requires approval. |
OrclOIMUserManagementScoping=OrclOIMUserId OrclOIMNeedApproval=true OrclOIMDeniedAttributesWithApproval= |
|
Authenticated Role |
authenticated-role |
Management Chain Policy for actions on users |
This policy controls what actions a user can perform on other users in their management chain and whether those actions require approval. By default, approval is required. |
OrclOIMNeedApproval=true OrclOIMUserManagementScoping=OrclOIMUserId |
|
Authenticated Role |
authenticated-role |
Management Chain Policy for User search |
This policy allows users to search for other users in their management chain and view allowed attributes. By default, users can view all attributes of other users in their management chain. |
OrclOIMDeniedAttributesDirect= OrclOIMUserManagementScoping=OrclOIMUserId |
|
Authenticated Role |
authenticated-role |
Management Chain Policy for Admin Role actions |
This policy controls the actions that a user can take on admin roles granted to other users tin their management chain. |
OrclOIMUserManagementScoping=OrclOIMUserId |
|
Authenticated Role |
authenticated-role |
Home Organization Approval Policy |
A home organization is the default organization that a user belongs to. This policy controls what actions a user can take in the user's home organization, and it is used by the request engine to determine whether the action requires approval or not. |
OrclOIMOrgScopingDirect=OrclOIMUserHomeOrgs OrclOIMNeedApproval=true |
|
Authenticated Role |
authenticated-role |
Home Organization Approval with Attributes Policy |
This policy controls what actions a user can take in the user's home organization, and it is used by the request engine to determine whether the action requires approval or not. |
OrclOIMDeniedAttributesWithApproval=USR_PASSWORD OrclOIMNeedApproval=true OrclOIMOrgScopingDirect=OrclOIMUserHomeOrgs |
|
Authenticated Role |
authenticated-role |
Home Org Policy for User attributes |
This policy controls the user attributes that are not visible to users when searching for and viewing user profiles of other users in the same home organization. By default, users can view all attributes. |
OrclOIMOrgScopingDirect=OrclOIMUserHomeOrgs OrclOIMDeniedAttributesDirect= |
|
Authenticated Role |
authenticated-role |
Home Org Policy for viewing user access |
This policy controls the actions that a user can take while viewing the access of another user in the same home organization. |
OrclOIMOrgScopingDirectAttributeOrclOIMUserHomeOrgs |
|
Authenticated Role |
authenticated-role |
Policy for modification of self user profile |
This policy specifies the user attributes that a user can modify in the user's own user profile, and whether the modification needs approval. By default, a user can modify any attribute in the user's own profile, and the modification requires approval. |
OrclOIMNeedApproval=true OrclOIMDeniedAttributesWithApproval= |
|
Authenticated Role |
authenticated-role |
User Self Service Policy for Request Actions |
This policy controls the actions authenticated users can take in Identity Self Service, and whether or not approvals are required. |
OrclOIMNeedApproval=true |
|
Authenticated Role |
authenticated-role |
User attribute view Policy for self |
This policy specifies whether an authenticated user can view the user's own user attributes, and the attributes that cannot be viewed. By default, all user attributes can be viewed. |
OrclOIMDeniedAttributesDirect= |
|
Authenticated Role |
authenticated-role |
User Self Service Policy for view actions |
This policy specifies the actions that a user can take on the user's own profile, which does not initiate a request. |
|
|
SPML Admin |
OIM SPML Admin |
SPML Admin Policy for User updates |
SPML Admin is a global admin role. This admin role is used by the SPML web service to carry out user management operations. This policy specifies whether members of the role can modify users and if the action requires approval. By default, user modification by members of the role requires approval. |
OrclOIMOrgScopingDirect=OrclOIMSPMLAdminOrgsDirect OrclOIMNeedApproval=true OrclOIMDeniedAttributesWithApproval= OrclOIMOrgScopingWithHierarchy=OrclOIMSPMLAdminOrgsWithHierarchy |
|
SPML Admin |
OIM SPML Admin |
SPML Admin Policy for actions on Users |
This policy controls that actions that a member of the SPML Admin role can take while managing users and whether approval is required. By default, user management actions performed by members of this role require approval. |
OrclOIMOrgScopingDirect=OrclOIMSPMLAdminOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMSPMLAdminOrgsWithHierarchy OrclOIMNeedApproval=true |
|
SPML Admin |
OIM SPML Admin |
SPML Administrator Policy |
This policy specifies the actions that the SPML Admin can take on users. |
OrclOIMDeniedAttributesDirect= OrclOIMOrgScopingDirect=OrclOIMSPMLAdminOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMSPMLAdminOrgsWithHierarchy |
|
SPML Admin |
OIM SPML Admin |
SPML Admin Policy for role membership actions |
This policy controls the role membership actions that a member of the SPML Admin role can perform and whether the actions require approval. By default, the actions require approval. |
OrclOIMOrgScopingWithHierarchy=OrclOIMSPMLAdminOrgsWithHierarchy OrclOIMOrgScopingDirect=OrclOIMSPMLAdminOrgsDirect OrclOIMNeedApproval=true |
|
SPML Admin |
OIM SPML Admin |
OIM Role SPML Admin Policy direct with attributes |
This policy specifies the actions that the SPML Admin can directly take on roles and role attributes. |
|
|
Role Authorizer |
OIM Role Authorizer |
Role Authorizer Policy for View actions |
The Role Authorizer admin role is an organization-scoped role. This policy controls the actions a Role Authorizer can perform without requiring approval. Actions, such as viewing role memberships and searching for roles, do not require approval. Searching for roles that are organization-scoped and viewing role members do not require approval. |
OrclOIMOrgScopingDirect=OrclOIMRoleAuthorizerOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMRoleAuthorizerOrgsWithHierarchy |
|
Role Authorizer |
OIM Role Authorizer |
Role Authorizer Policy for Request actions |
This policy controls the actions a Role Authorizer can perform that require approval. By default, granting and revoking of role membership by a member of this role does not require approval. |
OrclOIMNeedApproval=false OrclOIMOrgScopingDirect=OrclOIMRoleAuthorizerOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMRoleAuthorizerOrgsWithHierarchy |
|
Role Authorizer |
OIM Role Authorizer |
OIM RoleAuthorizer Basic Info Organization Direct Policy |
This policy specifies the direct view and search permissions on organizations by Role Authorizers. |
OrclOIMOrgScopingWithHierarchy=OrclOIMRoleAuthorizerOrgsWithHierarchy OrclOIMOrgScopingDirect=OrclOIMRoleAuthorizerOrgsDirect |
|
Role Authorizer |
OIM Role Authorizer |
OIM RoleAuthorizer Basic Info User Direct WithAttributes Policy |
This policy specifies the direct view and search permissions on users and user attributes by Role Authorizers. |
OrclOIMOrgScopingDirect=OrclOIMRoleAuthorizerOrgsDirect OrclOIMDeniedAttributesDirect= OrclOIMOrgScopingWithHierarchy=OrclOIMRoleAuthorizerOrgsWithHierarchy |
|
Role Viewer |
OIM Role Viewer |
Role Viewer Policy |
A Role Viewer is an admin role in Oracle Identity Manager. This policy controls what actions a member of the role can perform. By default, this policy allows a member of this admin role to search for and view roles. |
OrclOIMOrgScopingDirect=OrclOIMRoleViewerOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMRoleViewerOrgsWithHierarchy |
|
Role Viewer |
OIM Role Viewer |
Role Viewer Policy for Role Membership |
This policy controls the actions that a role viewer can perform and whether those actions require approval. By default, approval is required. |
OrclOIMOrgScopingDirect=OrclOIMRoleViewerOrgsDirect OrclOIMNeedApproval=true OrclOIMOrgScopingWithHierarchy=OrclOIMRoleViewerOrgsWithHierarchy |
|
Role Viewer |
OIM Role Viewer |
OIM RoleViewer Basic Info Organization Direct Policy |
This policy specifies the direct view and search permissions on organizations by Role Viewers. |
OrclOIMOrgScopingDirect=OrclOIMRoleViewerOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMRoleViewerOrgsWithHierarchy |
|
Role Viewer |
OIM Role Viewer |
OIM RoleViewer Basic Info User Direct WithAttributes Policy |
This policy specifies the direct view and search permissions on users and user attributes by Role Viewers. |
OrclOIMDeniedAttributesDirect= OrclOIMOrgScopingDirect=OrclOIMRoleViewerOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMRoleViewerOrgsWithHierarchy |
|
Authenticated Role |
authenticated-role |
Home Org Policy for Role memberships |
This policy controls the grant role membership and revoke role membership actions that a user can perform in the user's home org and whether it requires approval. By default, approval is required. |
OrclOIMNeedApproval=true OrclOIMOrgScopingDirect=OrclOIMUserHomeOrgs |
|
Authenticated Role |
authenticated-role |
Home Org Policy for Roles |
This policy allows a user to implicitly view the roles and role attributes that have been published to the user's home organization. |
OrclOIMOrgScopingDirect=OrclOIMUserHomeOrgs |
|
Role Administrator |
OIM Role Administrator |
OIM Role Administrator Policy with approval |
Role Administrator is an organization-scoped admin role. This policy specifies the actions that the Role Administrator can perform with approval. |
OrclOIMOrgScopingDirect=OrclOIMRoleAdminOrgsDirect OrclOIMNeedApproval=false OrclOIMOrgScopingWithHierarchy=OrclOIMRoleAdminOrgsWithHierarchy |
|
Role Administrator |
OIM Role Administrator |
Role Administrator Policy |
This Policy controls what actions a member of the Role Administrator admin role can perform. |
OrclOIMOrgScopingWithHierarchy=OrclOIMRoleAdminOrgsWithHierarchy OrclOIMOrgScopingDirect=OrclOIMRoleAdminOrgsDirect |
|
Role Administrator |
OIM Role Administrator |
OIM RoleAdministrator Basic Info Organization Direct Policy |
This policy specifies the direct view and search permissions on organizations by Role Administrators. |
OrclOIMOrgScopingWithHierarchy=OrclOIMRoleAdminOrgsWithHierarchy OrclOIMOrgScopingDirect=OrclOIMRoleAdminOrgsDirect |
|
Role Administrator |
OIM Role Administrator |
OIM RoleAdministrator Basic Info User Direct WithAttributes Policy |
This policy specifies the direct view and search permissions on users and user attributes by Role Administrators. |
OrclOIMOrgScopingDirect=OrclOIMRoleAdminOrgsDirect OrclOIMDeniedAttributesDirect= OrclOIMOrgScopingWithHierarchy=OrclOIMRoleAdminOrgsWithHierarchy |
|
System Configuration Administrator |
OIM System Configurator |
System Configurator Policy for OIM entities |
The System Configuration Administrator admin role is a global role. This policy controls what actions a member of the role can perform on users, entitlements, roles, organizations, and application instances. Members can manage application instances in the Identity System Administration, but have viewer admin role capabilities in the Identity Self Service. |
OrclOIMOrgScopingWithHierarchy=OrclOIMSystemConfiguratorOrgsWithHierarchy OrclOIMOrgScopingDirect=OrclOIMSystemConfiguratorOrgsDirect |
|
System Configuration Administrator |
OIM System Configurator |
System Configurator Policy |
This policy controls the actions that members of the System Configuration Administrator admin role can perform. Members of this admin role carry out post-install product configuration activities, and can perform all configuration activities that a system administrator can. However, members of the System Configuration Administrator admin role do not have the implicit user, role, and application instance administrator capabilities that members of the System Administrator admin role have. |
|
|
System Configuration Administrator |
OIM System Configurator |
System Configurator Policy deny policy for User |
This policy controls the actions that a member of the System Configuration Administrator can perform for the user entity. |
|
|
Catalog Administrator |
OIM Catalog Administrator Role |
View Policy for Catalog Administrators |
This policy controls the view permission on catalog entities for the Catalog Administrator. |
OrclOIMOrgScopingDirect=OrclOIMCatalogAdminOrgsDirect OrclOIMOrgScopingWithHierarchy=OrclOIMCatalogAdminOrgsWithHierarchy |
|
Authenticated Role |
authenticated-role |
OIM Entity Assigned to User Direct Policy |
This policy controls the actions that authenticated users can perform on the assigned entities. |
|
|
Authenticated Role |
authenticated-role |
OIM Entity Assigned to User Approval Policy |
This policy controls the actions that authenticated users can perform on the assigned entities. |
OrclOIMNeedApproval=true |
There are some application roles in OES that cannot be granted to users in Oracle Identity Manager, and therefore, do not have corresponding admin roles in Oracle Identity Manager. The policies associated with these application roles are used for request-related operations. For example, the policies associated with the OIM Request Approver application role are used to control the operations of the approver of a request. Table 3-3 lists the application roles that do not have corresponding admin roles in Oracle Identity Manager, and the associated policies.
Table 3-3 OES Application Roles and Policies
| Application Role in OES | Policy Name | Description | Obligation |
|---|---|---|---|
|
OIM Request Approver |
OIM Request Approver Role Policy |
This policy specifies the permissions to view and search roles by the request approver. |
|
|
OIM Request Requestor |
OIM Request Requestor Role Policy |
This policy specifies the permissions to view and search roles by the requester. |
|
|
OIM Request Beneficiary |
OIM Request Beneficiary Role Policy |
This policy specifies the permissions to view and search roles by the beneficiary of a request. |
|
|
OIM Request Approver |
OIM Request Approver ApplicationInstance Policy |
This policy specifies the permissions to view and search application instances by the request approver. |
|
|
OIM Request Requestor |
OIM Request Requestor ApplicationInstance Policy |
This policy specifies the permissions to view and search application instances by the requester. |
|
|
OIM Request Beneficiary |
OIM Request Beneficiary ApplicationInstance Policy |
This policy specifies the permissions to view and search application instances by the beneficiary of a request. |
|
|
OIM Request Approver |
OIM Request Approver Entitlement Policy |
This policy specifies the permissions to view and search entitlements by the request approver. |
|
|
OIM Request Requestor |
OIM Request Requestor Entitlement Policy |
This policy specifies the permissions to view and search entitlements by the requester. |
|
|
OIM Request Beneficiary |
OIM Request Beneficiary Entitlement Policy |
This policy specifies the permissions to view and search entitlements by the beneficiary of a request. |
|
|
OIM Request Approver |
OIM Request Approver User Policy |
This policy specifies the permissions to view and search users by the request approver. |
OrclOIMDeniedAttributesDirect= |
|
OIM Request Requestor |
OIM Request Requestor User Policy |
This policy specifies the permissions to view and search users by the requester. |
OrclOIMDeniedAttributesDirect= |
|
OIM Request Beneficiary |
OIM Request Beneficiary User Policy |
This policy specifies the permissions to view and search users by the beneficiary of a request. |
OrclOIMDeniedAttributesDirect= |
|
OIM Request Delegated Admin |
OIM Request Delegated Admin Role Policy |
This policy specifies the permissions to view and search roles by the delegated administrators. |
|
|
OIM Request Target Entity |
OIM Request Target Entity Role Policy |
This policy specifies the permissions to view and search roles by the target users of a request. |
|
|
OIM Request Delegated Admin |
OIM Request Delegated Admin User Policy |
This policy specifies the permissions to view and search users by the delegated administrators. |
|
|
OIM Request Target Entity |
OIM Request Target Entity User Policy |
This policy specifies the permissions to view and search users by the target users of a request. |
|
|
OIM Request Delegated Admin |
OIM Request Delegated Admin ITResEntitlement Policy |
This policy specifies the permissions to view and search IT resource entitlements by the delegated administrators. |
|
|
OIM Request Target Entity |
OIM Request Target Entity ITResEntitlement Policy |
This policy specifies the permissions to view and search IT resource entitlements by the target users of a request. |
|
|
OIM Request Delegated Admin |
OIM Request Delegated Admin ApplicationInstance Policy |
This policy specifies the permissions to view and search application instances by the delegated administrators. |
|
|
OIM Request Target Entity |
OIM Request Target Entity ApplicationInstance Policy |
This policy specifies the permissions to view and search application instances by the target users of a request. |
There exist application-role hierarchies for application roles defined in OES. This means that a user that has been granted an application role on a given organization can perform all actions of application roles present in that given organization hierarchy. For example, if a user has the OrclOIMUserViewer application role (in other words, the User Viewer Admin role) on a given organization, then the user can perform all the actions of the OrclOIMApplicationInstanceViewerRole, OrclOIMEntitlementViewer, OrclOIMOrgViewer, and OrclOIMRoleViewer application roles present in that given organization.
Table 3-4 lists the mapping between an application role and the corresponding application roles in a given organization. Note that a user that has been granted an application role listed in the second column can perform all the actions by the corresponding application role in the first column.
Table 3-4 Application Role Mapping
| Application Role | Application Role Mapped To |
|---|---|
|
OrclOIMRoleViewer |
OrclOIMUserAdmin, OrclOIMUserViewer |
|
OrclOIMOrgViewer |
OrclOIMUserAdmin, OrclOIMUserViewer, OrclOIMSPMLAdmin |
|
OrclOIMEntitlementViewer |
OrclOIMUserAdmin, OrclOIMUserViewer |
|
OrclOIMEntitlementAdministrator |
OrclOIMApplicationInstanceAdministratorRole |
|
OrclOIMApplicationInstanceViewerRole |
OrclOIMUserAdmin, OrclOIMUserViewer |
In Oracle Identity Manager 11g Release 2 (11.1.2), some of the roles from the earlier release have either been removed or replaced with another role. Table 3-5 provides a mapping between the legacy and new roles.
Table 3-5 Mapping Between Legacy and New Roles
| Legacy Role | New Role |
|---|---|
|
SCHEDULER ADMINISTRATORS |
SYSTEM CONFIGURATORS |
|
DEPLOYMENT MANAGER ADMINISTRATORS |
SYSTEM CONFIGURATORS |
|
NOTIFICATION TEMPLATE ADMINISTRATORS |
SYSTEM CONFIGURATORS |
|
SOD ADMINISTRATORS |
SYSTEM ADMINISTRATORS |
|
GENERATE_USERNAME_ROLE |
SYSTEM ADMINISTRATORS |
|
IDENTITY USER ADMINISTRATORS |
USER ADMIN |
|
USER CONFIGURATION ADMINISTRATORS |
SYSTEM CONFIGURATORS |
|
ACCESS POLICY ADMINISTRATORS |
SYSTEM CONFIGURATORS |
|
RECONCILIATION ADMINISTRATORS |
SYSTEM ADMINISTRATORS |
|
RESOURCE ADMINISTRATORS |
SYSTEM CONFIGURATORS |
|
GENERIC CONNECTOR ADMINISTRATORS |
SYSTEM CONFIGURATORS |
|
APPROVAL POLICY ADMINISTRATORS |
SYSTEM CONFIGURATORS |
|
REQUEST ADMINISTRATORS |
SYSTEM ADMINISTRATORS |
|
REQUEST TEMPLATE ADMINISTRATORS |
SYSTEM CONFIGURATORS |
|
PLUGIN ADMINISTRATORS |
SYSTEM CONFIGURATORS |
|
ATTESTATION CONFIGURATION ADMINISTRATORS |
SYSTEM CONFIGURATORS |
|
ATTESTATION EVENT ADMINISTRATORS |
SYSTEM ADMINISTRATORS |
|
ROLE ADMINISTRATORS |
ROLE ADMIN |
|
USER NAME ADMINISTRATOR |
The legacy role has been removed and there is no corresponding role in the current release. Will rely on Admin roles. |
|
IDENTITY ORGANIZATION ADMINISTRATORS |
ORGANIZATION ADMIN |
|
IT RESOURCE ADMINISTRATORS |
APPLICATION INSTANCE ADMIN |
|
REPORT ADMINISTRATORS |
The legacy role has been removed and there is no corresponding role for the current release because there are no links to reports from Oracle Identity Manager. |
|
SPML_APP_ROLE |
SPML_APP_ROLE There is no change to this enterprise role. However, a corresponding role with the privileges is seeded in OES. Note: This role is not used in Oracle Identity Manager. |
|
ALL USERS |
ALL USERS This role will remain as an enterprise role. Therefore, there is no corresponding application role in OES. This role is required in Oracle Identity Manager Enterprise Edition for the access policy-based provisioning operations. |
|
SYSTEM CONFIGURATION ADMINISTRATORS |
SYSTEM CONFIGURATORS This role has all privileges as the SYSTEM ADMINISTRATORS role, except for the ability to manage users, roles, organizations, and provisioning. This admin role is used for system configuration tasks for which a complete access to the system as the SYSTEM ADMINISTRATORS role is not required. |
|
SYSTEM ADMINISTRATORS |
SYSTEM ADMINISTRATORS This role remains as is to provide full privileges on the system. This role allows unrestricted permissions enforced at the code level (no declarative security model for this role). Therefore, there are no corresponding policies in OES for this role. |
3.3 Publishing Entities to Organizations
Publishing en entity to an organization is making the entity available to that organization. The enterprise roles, entitlements, or application instances can be published by respective administrators to a list of organizations to enable these to be granted to the users of those organizations. Enterprise roles, entitlements, and application instances are published to a list of organizations to make these:
-
Requestable to users under the list of organizations
-
Manageable to the list of organization administrators to manage these roles
When an entity administrator creates an entity, then that entity is automatically made available to all the organizations for which the administrator has entity admin role. For example, when a user with Role Administrator privilege creates an enterprise role, the newly created role is automatically made available to all the organizations on which the user is the Role Administrator. This avoids the need to create and then publish the entities for administrators in their respective organizations (or organization hierarchies). However, if the entity is required to be published to other organizations, then the entity must be manually published.
Entity administrators can publish the entities to organizations by using the entity detail pages. For example, publishing a role to a set of organizations is done from the Organizations tab of the Role Details page.
For information about how to publish the following entities to organizations:
-
Publishing a role to an organization: See "Publishing Roles to an Organization" in the Oracle Fusion Middleware User's Guide for Oracle Identity Manager.
-
Publishing an application instance with or without entitlements to an organization: See "Publishing an Application Instance to Organizations" in the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Manager.
3.4 Managing OES Policies
As listed in Table 3-2, each admin role in Oracle Identity Manager has a one-to-one mapping with a policy role in OES, which has a corresponding OES policy. To customize the default authorization policies, you can modify the OES policies by using the Authorization Policy Management (APM) UI. For example, to restrict the list of attributes to be viewed by a specific admin role, you can update the OrclOIMDeniedAttributes policy obligation in APM in the corresponding OES policies. Similarly, to restrict the list of attributes to be edited by a specific admin role, you can update the OrclOIMDeniedAttributesWithApproval obligation.
For information about managing OES policies by using the APM UI, see "Managing Policies and Policy Objects" in the Oracle Fusion Middleware Oracle Authorization Policy Manager Administrator's Guide (Oracle Fusion Applications Edition).
3.5 Enforcing Functional Security
You can enforce security by the following ways:
-
UI-level security: This is used for UI-level validations to enforce security. For example, you can implement field-level security to ensure that only users with permissions to view and edit fields are able to access the fields. The fields are disabled or not displayed for users who do not have permissions on the fields. This type of security enforcement is at the UI level, and can be overridden if you use APIs to perform the validation.
Note:
To enforce functional security at the UI level, you must be aware of the following:-
UI components and how to customize the components. See "Customizing the Interface" for details.
-
Expression Language (EL) syntax and usage. See "Using Expression Language in UI Customization" for details.
-
-
Backend security: To enforce security at the backend, you can modify the OES policies by using the APM UI.
For implementing functional security, first a JAVA authorization file is created in PlatformUI. This file contains the UIPermission variables for all the permissions defined in PolicyConstants (OES policies) for each functionality or page or module. All the authorization files have an entry in the adfc-config.xml file in the MainUI project in JDeveloper.
Implementing functional security involves the following:
3.5.1 Implementing Task Flow or Region
This level of implementation determines if the taskflow region is to be hidden or disabled to the user based on the permissions of the user. For securing a region, consider the following example:On the my-access-accounts.jsff page, the taskflow details-information-tf is rendered selectively to the end users by using an expression that follows the Expression Language (EL) syntax, as shown:
rendered="#{oimappinstanceAuth.view[bindings.appInstanceKey].allowed}"
Here:
-
oimappinstanceAuth is the mapped name of the ApplicationInstanceAuthz.java authorization bean in the adfc-config.xml file.
-
view is the name of the UIPermission that is to be checked, where the permission defined in ApplicationInstanceAuthz.java, which is the actual bean file for reference of oimappinstanceAuth, is the following:
private UIPermission view = new UIPermission(PolicyConstants.Resources.APPLICATION_INSTANCE.getId(), PolicyConstants.ApplicationInstanceActions.VIEW_SEARCH.getId());
-
appInstanceKey is the ID of the application instance that the user is trying to view passed as a parameter.
3.5.2 Defining Actions
If actions, such as create, modify, disable, enable, revoke, delete, and withdraw request, are to be hidden or disabled for the user based on the user's permissions. For example, the Create button is displayed only to users with permission to create users.
Permissions defined in UserAuthz.java based on PolicyConstants is:
private UIPermission create = new UIPermission (PolicyConstants.Resources.USER.getId(), PolicyConstants.UserActions.CREATE.getId());
Mapping entry for UserAuthz.java in adfc-config.xml in the MainUI project is as follows:
<managed-bean id="__30"> <managed-bean-name id="__36">oimuserAuth</managed-bean-name> <managed-bean-class id="__29">oracle.iam.ui.platform.view.authz.UserAuthz</managed-bean-class> <managed-bean-scope id="__31">session</managed-bean-scope> </managed-bean>
Now, you can define EL expression for permission that is defined in the JSFF page. In search-users.jsff, use the following EL expression in the rendered attribute, which is the Create button in this example:
<af:commandToolbarButton rendered="#{oimuserAuth.create.allowed}"
The EL expression defined in the rendered attribute hides or shows the button based on the Boolean value returned. Otherwise, the button can be made to read-only by defining the EL expression as disabled attribute instead of rendered. The Create button is now only shown to users whose role have permission defined in policies.
Similarly, you can define EL expressions for other actions, such as modify, enable, and disable. Another example of using EL expressions is to specify that reset password will be available to HelpDesk Admin only, and it will be hidden or read-only for other users.
3.5.3 Implementing Field-Level Security
Fields are displayed based on whether the user has permission to view those fields. For securing display fields, consider the following example:
On the userdetails.jsff page, under the Attributes tab, the user attributes, such as First Name, Last Name, and so on, have been secured by using the following EL expression:
rendered="#{oimuserAuth.viewSearch.attributes[bindings.firstName.hints.OIM_ATTRIBUTE]}"
Here:
-
oimuserAuth is the mapped name of UserAuthz.java in the adfc-config.xml.
-
viewsearch is the UIPermission name, and the Oracle Identity Manager attribute name for the field to be secured is passed as a parameter.