18 Coexistence of Sun OpenSSO Enterprise 8.0 with Oracle Access Management Access Manager 11.1.2
This chapter describes how to set up an environment where both Sun OpenSSO Enterprise 8.0 (OpenSSO Enterprise) and Oracle Access Management Access Manager (Access Manager) 11g Release 2 (11.1.2) deployments coexist, after you migrate Sun OpenSSO Enterprise 8.0 to Oracle Access Management Access Manager 11.1.2.
This chapter contains the following sections:
-
Protecting the End-Point URL of Access Manager 11.1.2 Server Using Agent-2
-
Creating an Authentication Policy in Access Manager 11.1.2 to Protect Resource-1
-
Updating the Profile of Agent-2 in OpenSSO Enterprise 8.0 Server
18.1 Coexistence Overview
During the process of migration from OpenSSO Enterprise 8.0 to Oracle Access Manager 11.1.2.0.0, you can have both OpenSSO Enterprise 8.0 and Access Manager 11.1.2 deployments coexisting, such that some applications are protected by OpenSSO Enterprise 8.0 while others are protected by Access Manager 11.1.2. It is desirable for end-users to have a seamless single sign-on experience when they navigate between these applications. This is called coexistence mode.
In this mode, Access Manager 11.1.2 protects the migrated applications and any new applications registered with Access Manager 11g; whereas OpenSSO Enterprise 8.0 continues to protect the applications that are not migrated to Access Manager 11.1.2.
In this coexistence mode, OpenSSO Enterprise 8.0 performs the authentication for all the resources protected by Access Manager 11.1.2.
18.2 Coexistence Topology
Figure 18-1 illustrates how the authentication is done by the OpenSSO Enterprise 8.0 server when a user requests to access a protected resource.
Figure 18-1 Coexistence of OpenSSO Enterprise 8.0 with Access Manager 11.1.2
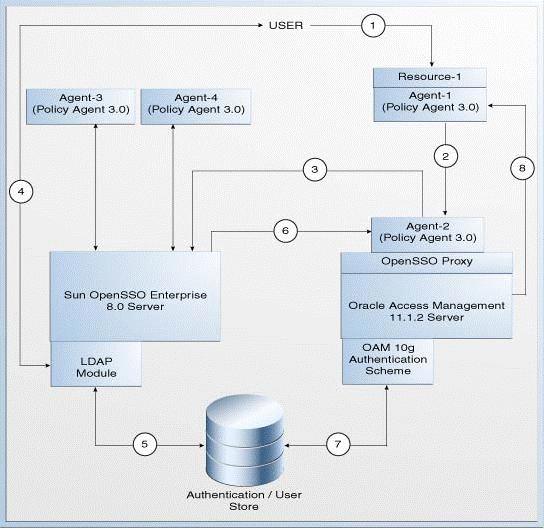
Description of "Figure 18-1 Coexistence of OpenSSO Enterprise 8.0 with Access Manager 11.1.2"
The topology consists of disjoint OpenSSO Enterprise 8.0 and Access Manager 11.1.2 environments. The numbers 1-8 in the topology show the sequence in which a request flows in the coexistence environment. See Table 18-2 for the request flow.
-
Agent-1: This is an OpenSSO agent (Policy Agent 3.0) registered with Access Manager 11.1.2 Server. It protectsResource-1. -
Agent-2: This is an OpenSSO agent (Policy Agent 3.0) registered with OpenSSO Enterprise 8.0 Server, which protects the end point URL of the Access Manager 11.1.2 server. This agent must be configured in the OpenSSO Enterprise 8.0 server. You must create a profile for this agent in OpenSSO Enterprise 8.0 Server, and freshly install a new Policy Agent (3.0). -
Agent-3andAgent-4: These are the OpenSSO Agents (Policy Agents 3.0) registered with the OpenSSO Enterprise 8.0 Server. -
Resource-1: This is a resource which is protected byAgent-1which communicates with the Access Manager 11.1.2 Server. -
Policy-1: This is the authentication policy created on the Access Manager 11.1.2 Server for protectingResource-1. This policy is created as part of the task: Creating an Authentication Policy in Access Manager 11.1.2 to Protect Resource-1. -
Policy-2: This is the authentication policy created on OpenSSO Enterprise 8.0 server for Access Manager's opensso proxy endpoints protected byAgent-2. This policy is created as part of the task: Protecting the End-Point URL of Access Manager 11.1.2 Server Using Agent-2.
Table 18-2 describes the request flow. The numbers in the Step column correspond to the numbers in Figure 18-1.
| Step | Description |
|---|---|
|
1 |
User requests to access |
|
2 |
|
|
3 |
The Access Manager 11.1.2 server end point is protected by Therefore, |
|
4 |
The OpenSSO Enterprise 8.0 Server's LDAP authentication module prompts the user for LDAP user name and password. User must enter the valid LDAP credentials. |
|
5 |
The OpenSSO Enterprise 8.0 Server validates the user credentials against authentication store, and creates user session as OpenSSO Enterprise 8.0 session and sets the OpenSSO Enterprise 8.0 SSO cookie1 with this session ID. |
|
6 |
The OpenSSO Enterprise 8.0 Server redirects the user to the Access Manager 11.1.2 Server ( |
|
7 |
The Access Manager 11.1.2 Server invokes the authentication scheme (OAM10gAuthScheme) as per step 2 ( |
|
8 |
The Access Manager 11.1.2 server creates the Access Manager session and sets headers. It also sets OAM_ID cookie and OpenSSO SSO cookie2 (via OpenSSO Proxy) and redirects the user to The user can now access |
18.3 Task Roadmap
Table 18-2 lists the steps to configure the coexistence environment.
Table 18-2 Tasks to be Completed
| Task No | Task | For More Information |
|---|---|---|
|
1 |
Understand and get familiar with the coexistence topology before you start the configuration process. |
See, Coexistence Topology |
|
2 |
Complete the prerequisites. |
|
|
3 |
Create Also, create an authentication policy on OpenSSO Enterprise 8.0 to protect the end point URL of the Access Manager 11.1.2 Server using |
See, Protecting the End-Point URL of Access Manager 11.1.2 Server Using Agent-2 |
|
4 |
Configure the data sources for Access Manager 11.1.2. |
|
|
5 |
Update the authentication module in Access Manager 11.1.2, and point the user identity store to the data source that is configured in Section 18.6. |
See, Updating LDAPNoPasswordAuthModule in Access Manager 11.1.2 |
|
6 |
Create the profile of |
See, Creating the Profile of Agent-1 in Access Manager 11.1.2 |
|
7 |
Create an authentication policy in Access Manager 11.1.2 server to protect |
See, Creating an Authentication Policy in Access Manager 11.1.2 to Protect Resource-1 |
|
8 |
Change the default cookie name of Access Manager 11.1.2, so that the cookie names of Access Manager 11.1.2 and OpenSSO Enterprise 8.0 are different. |
See, Modifying the OpenSSO Cookie Name in Access Manager 11.1.2 |
|
9 |
Update the profile of |
See, Updating the Profile of Agent-2 in OpenSSO Enterprise 8.0 Server |
|
10 |
Configure logout setting to initiate logout from both OpenSSO Enterprise 8.0 server and Access Manager 11.1.2 Server. |
|
|
11 |
Verify the configuration. |
18.4 Prerequisites for Coexistence
Complete the following prerequisites before you start performing the tasks described in this chapter:
-
Read the Oracle Fusion Middleware System Requirements and Specifications document to ensure that your environment meets the minimum requirements for the products you are installing, upgrading, and migrating.
Note:
For information about Oracle Fusion Middleware concepts and directory structure, see "Understanding Oracle Fusion Middleware Concepts and Directory Structure" in the Oracle Fusion Middleware Installation Planning Guide for Oracle Identity and Access Management.
-
Verify that the version of OpenSSO Enterprise that you are using is supported for coexistence. For more information about supported starting points for OpenSSO Enterprise 8.0 coexistence, see Section 11.8, "Supported Starting Points for Coexistence of Sun OpenSSO Enterprise With Oracle Access Management Access Manager 11.1.2".
-
Ensure that the Sun OpenSSO Enterprise 8.0 and Oracle Access Management Access Manager 11g Release 2 (11.1.2) installations are complete, and the servers are running.
If you have not installed and configured Oracle Access Management Access Manager 11g Release 2 (11.1.2), you must do it before you start with the next task. For more information on installing and configuring Oracle Access Management Access Manager 11g Release 2 (11.1.2), see "Installing Oracle Identity and Access Management (11.1.2.0.0)" and "Configuring Oracle Access Management" in the Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management.
-
Ensure that the OpenSSO Enterprise 8.0 and Access Manager 11.1.2 share the same user store.
-
If OpenSSO Enterprise 8.0 and Access Manager 11.1.2 servers are running on different machines, make sure the time of these machines are synchronized.
18.5 Protecting the End-Point URL of Access Manager 11.1.2 Server Using Agent-2
You must create a profile for Agent-2 in OpenSSO Enterprise 8.0, and freshly install a policy agent 3.0 to protect the end-point URL of the Access Manager 11.1.2 server. Also, you must create a policy for protecting the end-point URL of the Access Manager 11.1.2 Server in OpenSSO Enterprise 8.0 Server. To do this, complete the following tasks:
-
Creating Agent-2 Profile for Access Manager 11.1.2 on OpenSSO Enterprise 8.0 Server
-
Updating Web Applications to Include Agent Filter Configurations
-
Creating Authentication Policy on OpenSSO Enterprise 8.0 Server for Access Manager 11.1.2
18.5.1 Creating Agent-2 Profile for Access Manager 11.1.2 on OpenSSO Enterprise 8.0 Server
Create Agent-2 profile (as shown in Figure 18-1) on the OpenSSO Enterprise 8.0 Server by doing the following:
-
Log in to the OpenSSO Enterprise 8.0 Server administration console using the URL:
http://host:port/opensso
In this URL,
-
hostrefers to the fully qualified domain name of the machine hosting the OpenSSO Enterprise 8.0 console -
portrefers to the designated bind port for the OpenSSO Enterprise 8.0 console, which is the same as the bind port for the Administration Server
-
-
Go to the Access Control tab.
-
Click the top realm under Realm Name column in Realms table.
-
Click Agents tab.
-
Click the Web/J2EE tab according to the type of agent that you wish to create and configure in the OpenSSO Enterprise 8.0 Server.
-
Click New to create the new
Agent-2, and provide the necessary information such as Name, Password, Configuration, Server URL, and Agent URL. -
Click Create.
18.5.2 Installing Agent-2 (Policy Agent 3.0)
Install Agent-2 (Policy Agent 3.0) in front of the Access Manager 11.1.2 server. This should be a J2EE agent for WebLogic.
For more information about installing Policy Agent 3.0, see the respective sections in the Sun OpenSSO Enterprise Policy Agent 3.0 Guide for Oracle WebLogic Server/Portal 10
18.5.3 Updating Web Applications to Include Agent Filter Configurations
You must update the web applications ngsso-web.war and openssoproxy-urlapper.war to include the agent filter configurations in the web.xml file for Access Manager 11.1.2 Server to be protected by Agent-2. To do this, complete the following steps:
-
Unzip the
oam-server.earfile from theIAM_HOME/oam/server/apps/oam-server.eardirectory, and extract the contents to a temporary directory. -
Extract the contents of the
ngsso-web.warfile, and then extract the contents ofweb.xmlfile. Update theweb.xmlfile with the appropriate agent filter configuration for the Access Manager 11.1.2 Server to be protected byAgent-2. Update the filter definition with the URL:/server/opensso/login/*inurl-pattern.For example:
<filter> <filter-name>Agent</filter-name> <filter-class>com.sun.identity.agents.filter.AmAgentFilter</filter-class> </filter> <filter-mapping> <filter-name>Agent</filter-name> <url-pattern>/server/opensso/login/*</url-pattern> </filter-mapping>
-
Extract the contents of the
openssoproxy-urlmapper.warfile at the same locationIAM_HOME/oam/server/apps/oam-server.ear. Update theweb.xmlfile with the appropriate agent filter configuration for the Access Manager 11.1.2 server to be protected byAgent-2. Update the filter definition with the URL/UI/*inurl-pattern.For example:
<filter> <filter-name>Agent</filter-name> <filter-class>com.sun.identity.agents.filter.AmAgentFilter</filter-class> </filter> <filter-mapping> <filter-name>Agent</filter-name> <url-pattern>/UI/*</url-pattern> </filter-mapping>
-
Re-package the
oam-server.earfile to include the updatedngsso-web.warandopenssoproxy-urlapper.warfiles. -
Redeploy the updated
oam-server.earfile.
18.5.4 Creating Authentication Policy on OpenSSO Enterprise 8.0 Server for Access Manager 11.1.2
You must create an authentication policy (referred to as Policy-1) on OpenSSO Enterprise 8.0 Server to protect the end point URL of the Access Manager 11.1.2 Server. To do this, complete the following steps:
-
Log in to the OpenSSO Enterprise 8.0 Server administration console using the URL:
http://host:port/opensso
In this URL,
-
hostrefers to the fully qualified domain name of the machine hosting the OpenSSO Enterprise 8.0 console (Administration Server) -
portrefers to the designated bind port for the OpenSSO Enterprise 8.0 console, which is the same as the bind port for the Administration Server
-
-
Go to the Access Control tab.
-
Click the top realm under Realm Name column in Realms table.
-
Click the Policies tab.
-
Click New Policy, and provide the details of the new policy for protecting the end point URL of Access Manager 11.1.2 server with Rule as
OAM_server_protocol://OAM_managed_server_host:OAM_managed_server_port/opensso/UI/Login*?*andOAM_server_protocol://OAM_managed_server_host:OAM_managed_server_port/oam/server/opensso/login*, and Subject as Authenticated Users. -
Click OK.
18.6 Configuring Data Source for Access Manager 11.1.2
Configure the data source for Access Manager 11.1.2 by completing the following steps:
-
Log in to the Oracle Access Manager 11.1.2 console using the following URL:
http://host:port/oamconsole
In this URL,
-
hostrefers to the fully qualified domain name of the machine hosting the Oracle Access Manager console (Administration Server) -
portrefers to the designated bind port for the Oracle Access Manager console, which is the same as the bind port for the Administration Server
-
-
Go to the System Configuration tab.
-
Select Common Configuration.
-
Expand Data Sources., and select User Identity Stores
-
Under User Identity Stores, create a new data source by clicking the Create icon on the top of the left panel. This data source must be of type Open LDAP (or OUD). You must specify the user store details of OpenDS of OpenSSO Enterprise 8.0 for this new data source.
18.7 Updating LDAPNoPasswordAuthModule in Access Manager 11.1.2
LDAPNoPasswordAuthModule is the authentication module used by OAM10gScheme that protects Resource-1.
You must update the authentication module LDAPNoPasswordAuthModule to point to the data source created in Section 18.6 as its User Identity Store. To do this, complete the following steps:
-
Log in to the Oracle Access Management 11.1.2 console using the following URL:
http://host:port/oamconsole
In this URL,
-
hostrefers to the fully qualified domain name of the machine hosting the Oracle Access Manager console (Administration Server) -
portrefers to the designated bind port for the Oracle Access Management 11.1.2 console, which is the same as the bind port for the Administration Server
-
-
Go to the System Configuration tab.
-
Expand Access Manager, and then expand Authentication Modules.
-
Expand LDAP Authentication Module.
-
Click LDAPNoPasswordAuthModule, and update the User Identity Stores to point to the data source that you created in Section 18.6.
18.8 Creating the Profile of Agent-1 in Access Manager 11.1.2
You must create the profile of Agent-1 in Access Manager 11.1.2, and install a new Policy Agent 3.0 (Agent-1) pointing to Access Manager 11.1.2 server.
For information about creating the profile of agent in Access Manager 11.1.2, see "Registering and Managing OpenSSO Policy Agents Using the Console" in the Oracle Fusion Middleware Administrator's Guide for Oracle Access Management.
For information about installing Policy Agent 3.0, see the respective guide in the Sun OpenSSO Enterprise 8.0 Documentation Library.
18.9 Creating an Authentication Policy in Access Manager 11.1.2 to Protect Resource-1
Create an authentication policy (referred to as Policy-2) under the appropriate Application Domain to protect Resource-1 with the authentication scheme named OAM10gAuthScheme.
Also, create an authorization policy for Resource-1 with the condition TRUE. The resource URLs configured should be "/" and "/.../*".
For more information about creating and managing authentication and authorization policies, see "Managing Policies to Protect Resources and Enable SSO" in the Oracle Fusion Middleware Administrator's Guide for Oracle Access Management.
18.10 Modifying the OpenSSO Cookie Name in Access Manager 11.1.2
You must change the default cookie name of OpenSSO Cookie in Access Manager 11.1.2 server to a new name in order to avoid conflict between the cookie names of Access Manager 11.1.2 and OpenSSO Enterprise 8.0 servers. To do this, complete the following steps:
-
Open the
IAM_HOME/user_projects/domains/base_domain/config/fmwconfig/oam-config.xml. -
Under the section openssoproxy, modify the value of openssoCookieName from the default cookie name iPlanetDirectoryPro to a different value (for example,
OAMOpenSSOCookie). -
Log in to the Oracle Access Management 11.1.2 console using the following URL:
http://host:port/oamconsole
-
Go to the System Configuration tab.
-
Expand Access Manager, and then expand SSO Agents.
-
Expand OpenSSO Agents.
-
Select the required
Agent-1, and update the cookie name with the new value (for example: OAMOpenSSOCookie). -
Restart the Access Manager 11.1.2 Server.
18.11 Updating the Profile of Agent-2 in OpenSSO Enterprise 8.0 Server
After you create a policy on the OpenSSO Enterprise 8.0 Server for Access Manager 11.1.2, you must update the profile of Agent-2 (that you created in Task 6) in OpenSSO Enterprise 8.0 Server. To do this, complete the following steps:
-
Log in to the OpenSSO Enterprise 8.0 server administration console using the URL:
http://host:port/opensso
In this URL,
-
<host>refers to the fully qualified domain name of the machine hosting the OpenSSO Enterprise 8.0 console (administration server) -
<port>refers to the designated bind port for the OpenSSO Enterprise 8.0 console, which is the same as the bind port for the administration server
-
-
Go to the Access Control tab.
-
Click /(Top Level Realm) under Realm Name column in Realms table.
-
Click the Agents tab.
-
Click the Web/J2EE tab according to the type of
Agent-2. -
Click the
Agent-2. -
Click the Application tab.
-
Click Session Attributes Processing.
-
Select HTTP_HEADER as the Session Attribute Fetch Mode.
-
Set the value of OAM_REMOTE_USER header to UserToken to map the session attributes of this agent. To do this, enter UserToken as the Map Key, and OAM_REMOTE_USER as the Corresponding Map Value under the Session Attribute Map.
18.12 Configuring Logout Settings
You must configure logout settings to have single logout across OpenSSO Enterprise 8.0 and Access Manager 11.1.2 in coexistence mode. To do this, you must follow the procedure described in the following two sections:
-
Settings to Initiate Logout from OpenSSO Enterprise 8.0 Server
-
Settings to Initiate Logout from Access Manager 11.1.2 Server
18.12.1 Settings to Initiate Logout from OpenSSO Enterprise 8.0 Server
To initiate logout from the OpenSSO Enterprise 8.0 Server, you must write a post authentication plug-in, and implement onLogout() method, and set the query parameter goto to the redirect URL <OAM_server_protocol>://<OAM_server_host>:<OAM_managed_server_port>/opensso/UI/Logout. This URL redirects the user to the end point URL of the Access Manager 11.1.2 Server.
18.12.2 Settings to Initiate Logout from Access Manager 11.1.2 Server
To initiate logout from the Access Manager 11.1.2 Server, you must update the Logout URL in the respective Policy Agent 3.0 (Agent-1) configured with Access Manager 11.1.2 server to redirect to the OpenSSO Enterprise 8.0 server logout end point. To do this, complete the following steps:
-
Log in to the Oracle Access Management 11.1.2 console using the following URL:
http://host:port/oamconsole
-
Go to the System Configuration tab.
-
Expand Access Manager, and then expand SSO Agents.
-
Expand OpenSSO Agents.
-
Select the
Agent-1, (that is configured with Access Manager 11.1.2 and is protectingResource-1), and set the Logout URL to redirect to OpenSSO Enterprise 8.0 server logout end point (OpenSSO8.x_server_protocol://OpenSSO8.x_server_host:OpenSSO8.x_managed_server_port/opensso/UI/Logout), withgotoquery parameter set to redirect URL configured for theAgent-1.
18.13 Verifying the Configuration
To verify the configuration, complete the following steps:
-
Access
Resource-1. Observe that you are redirected to the OpenSSO Enterprise 8.0 Server for authentication. After the authentication, you can accessResource-1. -
Access any resource protected by
Agent-3(as shown in Figure 18-1), and observe that an explicit login is required to successfully access the resource. -
Initiate logout from both OpenSSO Enterprise 8.0 Server and Access Manager 11.1.2 Server, and observe that all the three cookies (cookie1, cookie2, and OAM_ID cookie) are cleared.