29 Managing Password Policies
Password policies are sets of rules that govern how passwords are used. This chapter contains these topics:
-
Section 29.2, "Managing Password Policies by Using Oracle Directory Services Manager"
-
Section 29.3, "Managing Password Policies by Using Command-Line Tools"
Note:
All references to Oracle Delegated Administration Services in this chapter refer to Oracle Delegated Administration Services 10g (10.1.4.3.0) or later.
29.1 Introduction to Managing Password Policies
A password policy is a set of rules governing how passwords are used. When a user attempts to bind to the directory, the directory server ensures that the password meets the various requirements set in the password policy.
When you establish a password policy, you set the following types of rules, to mention just a few:
-
The maximum length of time a given password is valid
-
The minimum number of characters a password must contain
-
The number of numeric characters required in a password
This section contains these topics:
29.1.1 What a Password Policy Is
Password polices are sets of rules that govern password syntax and how passwords are used. Password policies enforced by Oracle Internet Directory include:
-
The maximum length of time a given password is valid
-
The minimum number of characters a password must contain
-
The minimum number of numeric characters required in a password
-
The minimum number of alphabetic characters
-
The minimum number of repeated characters
-
The use of uppercase and lowercase
-
The minimum number of non-alphanumeric characters (that is, special characters)
-
That users change their passwords periodically
-
The minimum and maximum time between password changes
-
The grace period for logins after password expiration, by time or by number of logins
-
That users cannot reuse previously used passwords
29.1.2 Steps Required to Create and Apply a Password Policy
In general, establishing a password policy requires the following steps:
-
Create a password policy entry in the appropriate container and associate it with the
pwdpolicyobject. (Default entries exists when you first install Oracle Internet Directory.) -
Create the desired policy by setting values for attributes defined under the
pwdpolicyobject class for the entry created in step 1. -
Enable the policy by setting the
orclepwdpolicynableattribute to 1. If this is not set to 1, Oracle Internet Directory ignores the policy. -
Determine the subtree to be governed by the policy. Add and populate a
pwdpolicysubentryattribute with the policy's DN, at the root of that subtree.See Also:
"Object Class Reference" in Oracle Fusion Middleware Reference for Oracle Identity Management for a list and descriptions of the attributes of the
pwdPolicyobject class, and those of thetopobject class that pertain to password policies
29.1.3 Fine-Grained Password Policies
In 10g (10.1.4.0.1) and later, Oracle Internet Directory supports multiple password policies in each realm. You can apply these policies to any subtree within that realm. This means that you can have entry-specific password policies.
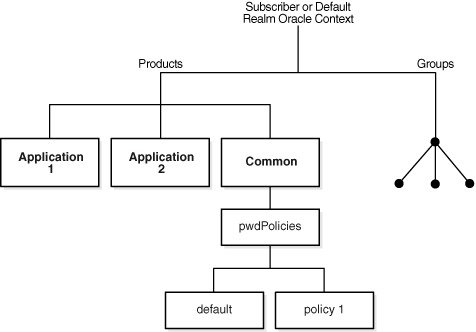
You can specify password policies as realm-specific or directory-wide in scope. To achieve the desired scope, you must create the password policy entry in the appropriate container. Password policies are populated under a "cn=pwdPolicies" container created under the "cn=common" entry in each realm. By default these containers contain a password policy with the RDN "cn=default". The directory specific default password policy, for example, has the DN: cn=default,cn=pwdPolicies,cn=Common,cn=Products, cn=OracleContext.
You can create other policies under the pwdPolicies container, with different RDNs. Figure 29-1 illustrates this scenario.
At run time, Oracle Internet Directory resolves the applicable password policy on an entry by looking for a populated pwdpolicysubentry attribute in the entry and applying the policy pointed to by its value. If a populated pwdPolicysubentry attribute does not exist, Oracle Internet Directory traverses up the directory tree until it finds the nearest ancestor entry with a populated pwdPolicysubentry. Oracle Internet Directory applies the password policy pointed to by the value at that entry.
Notes:
-
Password policies applied to groups are not automatically applied to group members. You must apply the policy to individual entries or to an ancestor entry.
-
You can disable a password policy by setting
orclpwdpolicyenableto 0. Doing so leaves that portion of the directory without an applicable password policy. Oracle Internet Directory does not traverse up the DIT to find an enabled policy that is applicable. Setting this attribute to0enables you to leave portions of the directory free of password policies when necessary. However you should consider the implications of making such a change before doing so. -
You must protect password policy entries from anonymous access using Oracle Internet Directory's ACI infrastructure, described in Chapter 30, "Managing Directory Access Control". This is particularly important when a password policy is weak, as that information can assist an attacker in compromising the directory.
29.1.4 Default Password Policy
The default password policy for Oracle Internet Directory enforces:
-
Account lockout after 10 login failures. Except for the superuser account, all accounts remain locked for a duration of 24 hours unless the passwords are reset by the directory administrator. A user account stays locked even after the lockout duration has passed unless the user binds with the correct password
If the superuser account,
cn=orcladmin, becomes locked, it stays locked until you unlock it by using the OID Database Password utility. This utility prompts you for the ODS user password. After you enter the ODS password, it unlocks the account.See Also:
-
The
oidpasswdcommand-line tool reference in Oracle Fusion Middleware Reference for Oracle Identity Management for information on unlocking a superuser account
-
-
A minimum password length of five characters with at least one numeric character
Beginning in Oracle Internet Directory, Release 9.0.4, the password policy entry in the Root Oracle Context applies to the superuser, but only the password policy governing account lockout is enforced on that account.
Note:
Oracle Identity Management has two distinct types of privileged user. Both privileged user accounts can be locked if certain password policies are activated.
The first type of privileged user, the superuser with the DN cn=orcladmin, is represented as a special user entry found within the default identity management realm. It enables directory administrators to make any modifications to the DIT and any changes to the configuration of Oracle Internet Directory servers. If the superuser (orcladmin) account is locked—for example, as a result of too many attempts to bind with an incorrect password—then an administrator with DBA privileges to the Oracle Internet Directory repository can unlock it by using the oidpasswd tool. To unlock the orcladmin account execute the command:
oidpasswd connect="connt_String" unlock_su_acct=TRUE
The second privileged user, a realm-specific privileged user, governs capabilities such as creation and deletion of users and groups within a realm and all the functionality related to Oracle Delegated Administration Services. This account is represented by an entry with the DN cn=orcladmin,cn=users,realm DN. Note that, in contrast to the single superuser account, each realm has its own realm-specific privileged user. To unlock the realm-specific privileged account, the first type of privileged user, cn=orcladmin, can modify the account password by using Oracle Directory Services Manager.
The Oracle Internet Directory password policy is applicable to simple binds (based on the userpassword attribute), compare operations on the userpassword attribute, and SASL binds. It does not apply to SSL and proxy binds.
29.1.5 Password Policy Attributes
The following attributes affect password policy:
Table 29-1 Password Policy Attributes
29.1.6 Password Policy-Related Operational Attributes
The Oracle Internet Directory server stores user-specific password policy-related information in operational attributes of the user entry. Only the server can modify these attributes. They are shown in Table 29-2.
Table 29-2 Password Policy-Related Operational Attributes
To determine the last login attempt, compare orcllastlogintime with the last timestamp in pwdfailuretime. The most recent of these is the time of the last login attempt.
29.1.7 Directory Server Verification of Password Policy Information
As explained in Section 29.1.3, "Fine-Grained Password Policies," Oracle Internet Directory determines the applicable policy for an entry by locating the appropriate populated pwdPolicysubentry. To ensure that the user password meets the requirements of a given policy, the directory server verifies:
-
That the password policy is enabled. It does this by checking the value of the attribute
orclpwdpolicyenablein the password policy entry. A value of 1 indicates that the password policy is enabled. A value of 0 indicates that it is disabled. -
Correctness of password policy syntax information, which includes, for example, the correct number of alphabetic and numeric characters, or the correct password length. The directory server checks the syntax during
ldapaddandldapmodifyoperations on the userpassword attribute. -
Password policy state information, which, for example, includes:
-
The timestamp of the user password creation or modification
-
That the minimum password age is greater than the current time minus the time of password creation
-
The timestamp of consecutive failed login attempts by the user
-
The time at which the user account was locked
-
Indicator that the password has been reset and must be changed by the user on first authentication
-
A history of user's previously used passwords
-
Time stamps of grace logins
If the grace login is set by time period, the server checks the time discrepancy between the current time and the expiration.
The directory server checks the state information during
ldapbindandldapcompareoperations, but does so only if theorclpwdpolicyenableattribute is set to 1.To enable password value syntax checking, set the attributes
orclpwdpolicyenableandpwdchecksyntaxin the password policy entry toTRUE. -
29.1.8 Password Policy Error Messages
Whenever there are password policy violations, the directory server sends to the client various error and warning messages. In Oracle Internet Directory, 10g (10.1.4.0.1) or later, the directory server can send these messages as LDAP controls only if the client sends a password policy request control as a part of an LDAP bind or compare operation. If the client does not send the request control, then the directory server does not send the response controls. Instead, it sends errors and warnings as part of additional information.
See:
Section S.1.6, "Troubleshooting Password Policies" for a list of the messages and information about how to resolve them
29.1.9 Releases Before 10g (10.1.4.0.1)
In releases before 10g (10.1.4.0.1), password policies were controlled by the orclcommonusersearchbase attribute in a realm-specific Common Entry. If you upgraded from an earlier release, the existing password policies were migrated to the new architecture during the upgrade. With the new architecture, simply adding a DN to the orclcommonusersearchbase no longer guarantees that the realm's default password policy is applied to the subtree rooted at that DN.
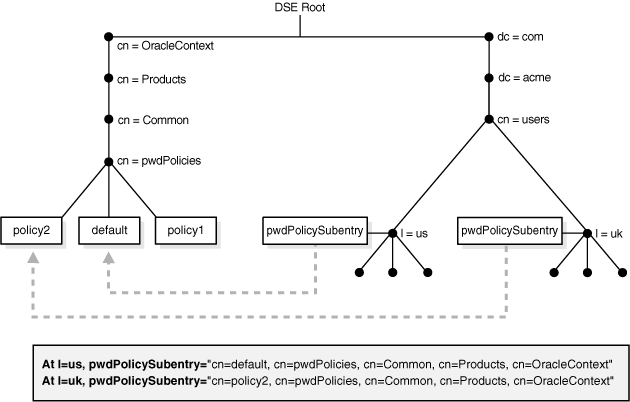
In Oracle Internet Directory 10g (10.1.4.0.1) and later, when you define a password policy, you must perform a second step to apply the password policy to a subtree of the directory. You must populate the pwdPolicysubentry attribute with the DN of the desired password policy on an entry that is the root of a subtree you want the policy to be applicable to. Figure 29-2 illustrates this. The pwdPolicy at l=us contains the DN of the default policy, "cn=default,cn=pwdPolicies,cn=Common,cn=Products, cn=OracleContext", so the default policy applies to the users in the US. The pwdPolicysubentry at l=uk contains the DN of the policy "cn=policy2,cn=pwdPolicies,cn=Common,cn=Products, cn=OracleContext", so policy2 applies to the users in the UK.
Note:
Password policy entries for subtrees and users are replicated. Replicating the 11g Release 1 (11.1.1) or 10g (10.1.4.0.1) policies to a pre-10g (10.1.4.0.1) node does not adversely impact the functionality of that node. A pre-10g (10.1.4.0.1) node, however, cannot meaningfully interpret the new password policies. It continues to enforce the password policy in the realm Oracle context.
29.2 Managing Password Policies by Using Oracle Directory Services Manager
You can use Oracle Directory Services Manager to create, assign, and modify password policies.
This section contains these topics:
-
Section 29.2.1, "Viewing Password Policies by Using Oracle Directory Services Manager"
-
Section 29.2.2, "Modifying Password Policies by Using Oracle Directory Services Manager"
-
Section 29.2.3, "Creating a Password Policy and Assigning it to a Subtree by Using ODSM"
29.2.1 Viewing Password Policies by Using Oracle Directory Services Manager
-
Invoke Oracle Directory Services Manager and connect to the Oracle Internet Directory server as described in Section 7.4.5, "Invoking Oracle Directory Services Manager."
-
From the task selection bar, select Security.
-
Expand Password Policy in the left pane. All of the password policies appear in the left pane, listed by relative DN. Mouse over an entry to see the full DN.
-
Select a password policy to display its information in the right pane.
29.2.2 Modifying Password Policies by Using Oracle Directory Services Manager
To modify the password policies:
-
Invoke Oracle Directory Services Manager and connect to the Oracle Internet Directory server as described in Section 7.4.5, "Invoking Oracle Directory Services Manager."
-
From the task selection bar, select Security.
-
Expand Password Policy in the left pane. All of the password policies appear in the left pane.
-
Select the password policy you want to modify. Five tab pages appear in the right pane.
-
In the General tab page, modify the editable attribute fields as needed.
-
Select the Account Lockout tab page and, to modify the fields, select Global Lockout. Modify the editable attribute fields as needed.
-
Select the IP Lockout tab page and, to modify the fields, select IP Lockout. Modify the editable attribute fields as needed.
-
Select the Password Syntax tab page and, to modify the fields, select Check Password Syntax. Modify the editable attribute fields as needed.
-
Select the Effective Subtree tab page to modify the subtree to which the policy applies. To add a subtree, select the Add icon. Either enter the DN, or select Browse, then use the Select Distinguished Name (DN) Path window to navigate to the subtree to which you want the policy to apply.
-
When you are finished, choose Apply.
29.2.3 Creating a Password Policy and Assigning it to a Subtree by Using ODSM
To create a new password policy:
-
Invoke Oracle Directory Services Manager and connect to the Oracle Internet Directory server as described in Section 7.4.5, "Invoking Oracle Directory Services Manager."
-
From the task selection bar, select Security.
-
Expand Password Policy in the left pane. All of the password policies appear in the left pane.
-
To create a new policy, select Create. Alternatively, select an existing password policy in the left pant and select Create Like.
-
In the General tab page, set or modify the editable attribute fields as needed.
-
Select the Account Lockout tab page and, to modify the fields, select Global Lockout. Modify the editable attribute fields as needed.
-
Select the IP Lockout tab page and, to modify the fields, select IP Lockout. Modify the editable attribute fields as needed.
-
Select the Password Syntax tab page and, to modify the fields, select Check Password Syntax. Modify the editable attribute fields as needed.
-
To assign the password policy to a subtree, select the Effective Subtree tab page, then select Add. Either enter the DN, or select Browse, then use the Select Distinguished Name (DN) Path window to navigate to the subtree to which you want the policy to apply.
-
When you are finished, choose Apply.
29.3 Managing Password Policies by Using Command-Line Tools
This section contains these topics:
-
Section 29.3.1, "Viewing Password Policies by Using Command-Line Tools"
-
Section 29.3.2, "Creating a New Password Policy by Using Command-Line Tools"
-
Section 29.3.3, "Applying a Password Policy to a Subtree by Using Command-Line Tools"
-
Section 29.3.4, "Setting Password Policies by Using Command-Line Tools"
-
Section 29.3.5, "Making a Password Policy Entry Specific by Using Command-Line Tools"
29.3.1 Viewing Password Policies by Using Command-Line Tools
The following example retrieves password policies under a specific password policy container:
ldapsearch -p port -h host \ -b "cn=pwdPolicies,cn=common,cn=products,cn=OracleContext, \ o=my_company,dc=com" \ -s sub "(objectclass=pwdpolicy)"
The following example retrieves all password policy entries:
ldapsearch -p port -h host -b " " -s sub "(objectclass=pwdpolicy)"
29.3.2 Creating a New Password Policy by Using Command-Line Tools
You create a new password policy by adding a policy entry to the appropriate container. A good way to do this is as follows:
-
Dump the contents of the default entry,
cn=default,cn=pwdPolicies,cn=Common,cn=Products, cn=OracleContext, to an LDIF file, usingldapmodify. For example:ldapsearch -p port -h host -D cn=orcladmin -q -L \ -b 'cn=default,cn=pwdPolicies,cn=Common,cn=Products, cn=OracleContext' \ -s base '(objectclass=pwdpolicy)' >> pwdpolicy.ldif
As an alternative to
ldapsearch, you could useldifwrite. EnsureORACLE_INSTANCEis set, then type:ldifwrite connect="conn_str" \ baseDN="cn=default,cn=pwdPolicies,cn=Common,cn=Products, cn=OracleContext" \ ldiffile="pwpolicy.ldif"
-
Modify the LDIF file so that it has the common name and desired values for the new policy. For example, you might change
cn=defaulttocn=policy1and changepwdMaxFailurefrom10to5. -
Add the new entry by using
ldapadd. You would use a command line of the form:ldapadd -p port_number -h host -D cn=orcladmin -q -f pwdpolicy.ldif
29.3.3 Applying a Password Policy to a Subtree by Using Command-Line Tools
To apply the new password policy to the subtree "dn: cn=accounting,c=us" you would use a command line such as:
ldapmodify -D "cn=orcladmin" -q -p port -h host -f my_file.ldif
with an LDIF file such as this:
dn: cn=accounting,c=us changetype: modify replace: pwdPolicysubentry pwdPolicysubentry:cn=policy1,cn=pwdPolicies,cn=common,cn=products, cn=OracleContext,o=my_company,dc=com
29.3.4 Setting Password Policies by Using Command-Line Tools
The following example disables the pwdLockout attribute in the default password policy. It changes the attribute from its default setting of 1 to 0.
The file my_file.ldif contains:
dn: cn=default,cn=pwdPolicies,cn=common,cn=products,cn=OracleContext, o=my_company,dc=com changetype:modify replace: pwdlockout pwdlockout: 0
The following command loads this file into the directory:
ldapmodify -D "cn=orcladmin" -q -p port -h host -f my_file.ldif
The following example modifies pwdMaxAge in the default password policy entry.
ldapmodify -D "cn=orcladmin" -q -p port -h host -q -f file
dn: cn=default,cn=pwdPolicies,cn=common,cn=products,cn=OracleContext, o=my_company,dc=com changetype: modify replace: pwdMaxAge pwdMaxAge: 10000
29.3.5 Making a Password Policy Entry Specific by Using Command-Line Tools
If the password policy is reset for a large number of users, Oracle Internet Directory server must refresh its passwordPolicySubentry cache, which can affect performance by causing a large number of SQL query requests to the Oracle database.
Beginning with Oracle Internet Directory 11g Release 1 (11.1.1.7.0), you can make a password policy entry specific by subtyping the entrylevel. For example, the following command adds a password policy to A_user:
ldapmodify -D "cn=orcladmin" -q -p port -h host -q -f pwdpolicy.ldif
where pwdpolicy.ldif contains:
dn: A_user,cn=users,dc=us,dc=mycompany,dc=com changetype: modify add: pwdpolicysubentry;entrylevel pwdpolicysubentry;entrylevel: cn=pwdpolicies,dc=us,dc=mycompany,dc=com
The password policy applies only to A_user. If the entrylevel subtype is missing in the entry for the pwdpolicysubentry attribute, then the password policy applies to the entire subtree.