18 Integrating with Oracle Identity Management
This chapter describes how to integrate Oracle WebCenter Content with Oracle Identity Management.
This chapter includes the following sections:
-
Section 18.1, "Overview of Integrating with Oracle Identity Management"
-
Section 18.4, "Validating Access Through the Load Balancer and SSO"
18.1 Overview of Integrating with Oracle Identity Management
Oracle Access Manager is the recommended single sign-on solution for Oracle Fusion Middleware 11g Release 1. You can integrate an Oracle Fusion Middleware enterprise deployment with Oracle Identity Management 11g or 10g. The following sections describe how to integrate the policy store and identity store for the Oracle WebCenter Content domain with Oracle Identity Management 11g or 10g.
Note:
When integrating with Oracle Identity Management, use the transport mode currently in use by the Oracle Access Management servers; for example, Open, Simple, or Cert.
Table 18-1 lists the high-level steps for integrating Oracle Identity Management 11g with an Oracle WebCenter Content enterprise deployment.
Table 18-1 Steps for Integrating with Oracle Identity Management 11g
| Step | Description | More Information |
|---|---|---|
|
Register the WebGate agent |
Register the Webgate agent using the RREG tool. |
|
|
Install and configure WebGate |
Install WebGate on each of the WEBHOST machines, where Oracle HTTP Server has already been installed. |
|
|
Set up WebLogic Server authentication providers |
Set up the WebLogic Server authentication providers by backing up the configuration files, setting up the Oracle Access Manager identity assertion provider, and setting the order of providers. |
Section 18.2.5, "Setting Up the WebLogic Server Authentication Providers" |
Table 18-2 lists the high-level steps for integrating Oracle Identity Management 10g with an Oracle WebCenter Content enterprise deployment.
Table 18-2 Steps for Integrating with Oracle Identity Management 10g
| Step | Description | More Information |
|---|---|---|
|
Configure Oracle Access Manager |
The OAM Configuration Tool (oamcfg) starts a series of scripts and sets up the required policies. |
|
|
Install and configure WebGate |
Install WebGate on each of the WEBHOSTn machines to secure Oracle Web Tier. |
|
|
Configure IP address validation for the Webgate |
Configure the IP address validation for the Webgate using Access System Console. |
Section 18.3.5, "Configuring IP Address Validation for the Enterprise Deployment Webgate" |
|
Set up the Oracle Access Manager identity assertion provider |
Back up the configuration files, set up the identity assertion provider, and set the order of providers. |
Section 18.3.6, "Setting up the Oracle Access Manager Identity Assertion Provider" |
18.2 Integrating with Oracle Access Manager 11g
This section describes how to set up Oracle Access Manager 11g as the single sign-on solution for the Oracle WebCenter Content enterprise deployment topology. It contains the following sections:
-
Section 18.2.1, "Overview of Oracle Access Manager Integration"
-
Section 18.2.5, "Setting Up the WebLogic Server Authentication Providers"
18.2.1 Overview of Oracle Access Manager Integration
This section explains the procedure for configuring the Oracle WebCenter Content installation with an existing Oracle Access Manager 11g installation, with Oracle Internet Directory as the underlying directory service. For more information about installing and configuring an Oracle Access Manager installation, see the Oracle Fusion Middleware Enterprise Deployment Guide for Oracle Identity Management.
Note:
The Oracle WebCenter Content enterprise deployment topology described in this guide uses a single sign-on configuration in which both the Oracle WebCenter Content system and the single sign-on system are in the same network domain (mycompany.com). For a multidomain configuration, see the required configuration steps in "Introduction to the OAM Policy Model, Single Sign-On" in the Oracle Fusion Middleware Administrator's Guide for Oracle Access Manager with Oracle Security Token Service.
18.2.2 Prerequisites for Oracle Access Manager
The setup for Oracle Access Manager assumes an existing Oracle Access Manager 11g installation. For more information on installing and configuring an Oracle Access Manager installation, see Oracle Fusion Middleware Enterprise Deployment Guide for Oracle Identity Management. This setup includes Oracle Internet Directory as the directory service.
In addition, the Oracle Access Manager installation should have its own Web server configured with WebGate.
18.2.3 Registering the WebGate Agent
This section describes the procedures for registering the WebGate Agent on each of the WEBHOST machines:
-
Section 18.2.3.2, "Updating the Oracle Access Manager 11g Request File"
-
Section 18.2.3.4, "Changing the inspection.wsil Resource to Use the Basic Authentication Scheme"
-
Section 18.2.3.6, "Copying Access Files to WEBHOST Machines"
18.2.3.1 Extracting and Using the RREG Tool
The RREG tool is part of the Oracle Access Manager 11g installation. If it is not already available, extract it on each of the Oracle Identity Management machines.
To extract the RREG tool:
-
After installing and configuring Oracle Access Manager, navigate to the following location:
IDM_Home/oam/server/rreg/client -
On the command line, untar the
RREG.tar.gzfile usinggunzip, as in the following example:gunzip RREG.tar.gz tar -xzvf RREG.tar
-
Open the
RREG_HOME/bin/oamreg.shscript, and change theOAM_REG_HOMEparameter according to your setup, if necessary.
The RREG Configuration Tool provides a way to register protected and public resources into the Oracle Access Manager system. The list of protected resources to be added to the Oracle Access Manager system is as follows:
/adfAuthentication /imaging/faces /em /console /DefaultToDoTaskFlow /sdpmessaging/userprefs-ui /integration/worklistapp /workflow/sdpmessagingsca-ui-worklist /soa/composer /soa-infra /soa-infra/deployer /soa-infra/events/edn-db-log /soa-infra/cluster/info /inspection.wsil /dc-console/adfAuthentication /dc-client/adfAuthentication
The list of public resources follows:
/cs /_ocsh /imaging /soa-infra/directWSDL /dc-console /dc-client
The list of excluded resources follows:
/wsm-pm /soa-infra/services /ucs/messaging/webservice
18.2.3.2 Updating the Oracle Access Manager 11g Request File
The RREG_Home/input/ directory contains a template file named OAM11gRequest.xml. Copy this file to WCCOAM11gRequest.xml, and edit that file to create the policies for the Oracle WebCenter Content installation.
Note:
Replace OAM_HOST, OAM_ADMINSERVER_PORT,
WCC_EDG_AGENT, and WCC_EDG_DOMAIN with their respective values in your installation.
After editing, the file should look as follows:
<?xml version="1.0" encoding="UTF-8"?>
<OAM11GRegRequest>
<serverAddress>http://OAM_HOST:OAM_ADMINSERVER_PORT</serverAddress>
<agentName>WCC_EDG_AGENT</agentName>
<applicationDomain>WCC_EDG_DOMAIN</applicationDomain>
<cachePragmaHeader>private</cachePragmaHeader>
<cacheControlHeader>private</cacheControlHeader>
<ipValidation>1</ipValidation>
<ValList ListName="ipValidationExceptions">
<ValListMember Value="10.1.1.1"/>
</ValList>
<logOutUrls>
<url>/oamsso/logout.html</url>
</logOutUrls>
<protectedResourcesList>
<resource>/adfAuthentication</resource>
<resource>/imaging/faces</resource>
<resource>/em</resource>
<resource>/console</resource>
<resource>/DefaultToDoTaskFlow</resource>
<resource>/sdpmessaging/userprefs-ui</resource>
<resource>/integration/worklistapp</resource>
<resource>/workflow/sdpmessagingsca-ui-worklist</resource>
<resource>/soa/composer</resource>
<resource>/soa-infra/deployer</resource>
<resource>/soa-infra/events/edn-db-log</resource>
<resource>/soa-infra/cluster/info</resource>
<resource>/inspection.wsil</resource>
<resource>/soa-infra</resource>
<resource>/dc-console/adfAuthentication</resource>
<resource>/dc-client/adfAuthentication</resource>
</protectedResourcesList>
<publicResourcesList>
<resource>/cs</resource>
<resource>/_ocsh</resource>
<resource>/imaging</resource>
<resource>/soa-infra/directWSDL</resource>
<resource>/dc-console</resource>
<resource>/dc-client</resource>
</publicResourcesList>
<excludedResourcesList>
<resource>/wsm-pm</resource>
<resource>/soa-infra/services</resource>
<resource>/ucs/messaging/webservice</resource>
</excludedResourcesList>
<userDefinedParameters>
<userDefinedParam>
<name>filterOAMAuthnCookie</name>
<value>false</value>
</userDefinedParam>
</userDefinedParameters>
</OAM11GRegRequest>
Notes:
-
The
resource_name/.../*resources will be automatically added during the registration. -
This guide describes the validation field entry in request files for Oracle Access Manager 11g (11.1.1.2) and later. The validation exception list is defined differently in earlier versions of Oracle Access Manager 11g. For earlier versions, instead of using the
<ValList>entry as shown in the preceding text, use the following syntax after the</publicResourcesList>entry.<userDefinedParameters> <userDefinedParam> <name>ipValidationExceptions</name> <value>10.1.1.1</value> </userDefinedParam> </userDefinedParameters>For more information about adding validation exceptions, see the Oracle Fusion Middleware Administrator's Guide for Oracle Access Manager with Oracle Security Token Service.
18.2.3.3 Running the oamreg Tool
Run the oamreg tool with the following command:
$ ./RREG_Home/bin/oamreg.sh inband input/WCCOAM11gRequest.xml
The run should look as follows:
------------------------------------------------ Welcome to OAM Remote Registration Tool! Parameters passed to the registration tool are: Mode: inband Filename: ORACLE_BASE/product/fmw/iam/oam/server/rreg/client/rreg/input/WCCOAM11GRequest.xml Enter admin username:oamadmin Username: your_oamadmin_user Enter admin password: your_oamadmin_password Do you want to enter a Webgate password?(y/n): y Enter webgate password: your_webgate_password Enter webgate password again: your_webgate_password Password accepted. Proceeding to register.. Apr 18, 2011 12:22:36 PM oracle.security.am.engines.rreg.client.handlers.request.OAM11GRequestHandler getWebgatePassword INFO: Passwords matched and accepted. Do you want to import an URIs file?(y/n): n ---------------------------------------- Request summary: OAM11G Agent Name:WCC_EDG_AGENT URL String:WCC_EDG_AGENT Registering in Mode:inband Your registration request is being sent to the Admin server at: http://oamserver.mycompany.com:7001 ---------------------------------------- Inband registration process completed successfully! Output artifacts are created in the output folder.
18.2.3.4 Changing the inspection.wsil Resource to Use the Basic Authentication Scheme
By default, the inspection.wsil resource is set to use the form authentication scheme. For the connection between the workflow and Oracle WebCenter Content: Imaging to work, this resource must be updated on each of the WEBHOST machines to use the basic authentication scheme instead.
To change the inspection.wsil resource to use the basic authentication scheme:
-
Log in to the Oracle Access Manager console at
http://OAM_HOST:OAM_ADMINSERVER_PORT/oamconsole. -
Using the navigation tree on the left, click Application Domains and then the application domain name to navigate to the application domain created (
WCC_EDG_DOMAIN). -
Expand your application domain's name.
-
Expand Authentication Policies.
-
Double-click Protected Resource Policy.
-
Select the
inspection.wsilandinspection.wsil/.../*resources, and click the Delete icon in the Resources pane to remove them. -
Click Apply, and confirm the action when prompted.
-
In the navigation tree, click Authentication Policies again, and click the Create button in the tool bar above the navigation tree:
-
Enter a name for the policy (for example,
New Basic Policy). -
Select BasicSessionlessScheme as the authentication scheme.
-
Click Apply.
You will see the newly created policy under Authentication Policies in the navigation tree.
-
Open the newly created policy.
-
On the Resources pane, click the add icon (plus sign) on the right, and add the
inspection.wsilandinspection.wsil/.../*resources. -
Click Apply.
-
-
Click the refresh icon on the navigation tree, and verify the new authentication policy (click it, and make sure the
inspection.wsilandinspection.wsil/.../*resources were added).
Note:
Do not forget to create a new credential for the new user. See Section 14.5.14, "Configuring a BPEL CSF Credential" for further details. (This book uses the weblogic_ecm user as an example for SSO.)
18.2.3.5 Updating the Oracle Access Manager 11g Server Configuration to Support the Basic Cookieless Scheme
You must set the NoUniqueSessionsFor10gAgents parameter in the Oracle Access Manager 11g configuration to true on each of the OAMHOST machines. To do this, edit the oam-config.xml file located in the IDM_Home/oam/server/config/ directory, and change the line
<Setting Name="NoUniqueSessionsFor10gAgents" Type="xsd:string">false</Setting>
to
<Setting Name="NoUniqueSessionsFor10gAgents" Type="xsd:string">true</Setting>
Save the file, and restart the Oracle Access Manager server in your Oracle Identity Management system for the change to take effect.
18.2.3.6 Copying Access Files to WEBHOST Machines
The following two files are generated in RREG_Home/output/WCC_EDG_AGENT:
-
ObAccessClient.xml -
cwallet.sso
Copy these files to the WebGate instance location on each of the WEBHOST machines:
scp ObAccessClient.xml oracle@WEBHOSTN:ORACLE_BASE/admin/webN/config/OHS/ohsN/ webgate/config/ scp cwallet.sso oracle@WEBHOSTN:ORACLE_BASE/admin/webN/config/OHS/ohsN/ webgate/config/
In the scp command, N is a sequential number for your installation; for example, 1 for WEBHOST1 or 2 for WEBHOST2.
18.2.4 Setting Up WebGate
You must set up a WebGate on each of the WEBHOST machines where Oracle HTTP Server has already been installed.
This section covers the following topics:
18.2.4.1 Installing GCC Libraries
You must download and install third-party GCC libraries on each of the WEBHOST machines before installing WebGate. You can download the appropriate GCC library from the following third-party website:
http://gcc.gnu.org
Note:
The setup in this guide uses Oracle Identity and Access Management 11g (11.1.1.6.0). For version 11.1.1.7.0 or later, installation of third-party GCC libraries is not necessary.
For 32-bit Linux, the required libraries are libgcc_s.so.1 and libstdc++.so.5 with a version number of 3.3.2. Table 18-3 lists the versions of third-party GCC libraries for Linux and Solaris operating systems.
Table 18-3 Versions of GCC Third-Party Libraries for Linux and Solaris Systems
| Operating System | Architecture | GCC Libraries | Required Library Version |
|---|---|---|---|
|
Linux 32-bit |
x86 |
libgcc_s.so.1 libstdc++.so.5 |
3.3.2 |
|
Linux 64-bit |
x64 |
libgcc_s.so.1 libstdc++.so.6 |
3.4.6 |
|
Solaris 64-bit |
SPARC |
libgcc_s.so.1 libstdc++.so.5 |
3.3.2 |
18.2.4.2 Installing WebGate
This section describes the procedures for installing WebGate. You must install WebGate on each of the WEBHOST machines.
18.2.4.2.1 Launching the Installer
The installer program for Oracle HTTP Server 11g Webgate for Oracle Access Manager is included in the webgate.zip file.
To launch the installation wizard:
-
Extract the contents of the
webgate.zipfile to a directory. By default, this directory is namedwebgate. -
Move to the Disk1 subdirectory under the webgate directory.
-
Set the WEB_HOME environment variable to the Middleware home for Oracle Web Tier:
export MW_HOME=ORACLE_BASE/product/fmw export WEB_HOME=MW_HOME/web
-
Start the installer using the following command:
$ ./runInstaller -jreLoc MW_HOME/jdkNote:
When you install Oracle HTTP Server, the
jdkdirectory is created under the Middleware home directory. You must enter the absolute path of the JRE folder located in this JDK when launching the installer.After the installer starts, the Welcome screen opens.
18.2.4.2.2 Installation Flow and Procedure
If you need additional help with any of the installation screens, click Help to access the online help.
To install Oracle HTTP Server 11g Webgate for Oracle Access Manager:
-
In the Welcome screen, click Next.
-
In the Prerequisite Checks screen, click Next.
-
In the Specify Installation Location screen, specify the Oracle Middleware Home and Oracle Home Directory locations:
-
ORACLE_BASE/product/fmw -
Oracle_OAMWebGate1(leave the default name)
Note:
The Middleware home contains an Oracle home for Oracle Web Tier. The default name is
Oracle_OAMWebGate1for this Oracle home directory, which will be created under the Middleware home.Click Next.
-
-
In the Specify GCC Library screen, specify the directory that contains the GCC libraries, or click Browse to navigate to their location on your local computer (see Section 18.2.4.1, "Installing GCC Libraries"), and click Next.
-
In the Installation Summary screen, verify the information on this screen and click Install to begin the installation.
-
In the Installation Progress screen, you may be prompted to run the
ORACLE_HOME/oracleRoot.shscript to set up the proper file and directory permissions.Click Next to continue.
-
In the Installation Complete screen, click Finish to exit the installer.
18.2.4.3 Postinstallation Steps
Complete the following procedure on each of the WEBHOST machines after installing Oracle HTTP Server 11g Webgate for Oracle Access Manager.
To do postinstallation steps:
-
Move to the following directory under your Oracle Home for Webgate:
$ cd Webgate_Oracle_Home/webgate/ohs/tools/deployWebGateWebgate_Oracle_Homeis the directory where you have installed Oracle HTTP Server Webgate and created the Oracle Home for Webgate; for example:WEB_ORACLE_HOME/Oracle_OAMWebGate1Note:
Oracle_OAMWebGate1is the default. -
On the command line, run the following command (on a single line) to copy the required bits of agent from the
Webgate_Oracle_Homedirectory to the Webgate Instance location:$ ./deployWebGateInstance.sh -w ORACLE_BASE/admin/webN/config/OHS/ohsN -oh Webgate_Oracle_Home
The
ORACLE_BASE/admin/webN/config/OHS/ohsNdirectory is the instance home of an Oracle HTTP Server (whereNis a sequential number for your installation; for example,1forWEBHOST1or2forWEBHOST2).Note:
An instance home for Oracle HTTP Server is created after you configure Oracle HTTP Server.
-
Run the following command to ensure that the
LD_LIBRARY_PATHvariable containsOracle_Home_for_Oracle_HTTP_Server/lib:$ export LD_LIBRARY_PATH=$LD_LIBRARY_PATH:ORACLE_BASE/product/fmw/webN/lib -
From your present working directory, move up one directory level:
$ cd Webgate_Oracle_Home/webgate/ohs/tools/setup/InstallTools -
On the command line, run the following command (on a single line) to copy apache_webgate.template from the
Webgate_Oracle_Homedirectory to the Webgate Instance location (renamed towebgate.conf) and update the httpd.conf file to add one line to include the name ofwebgate.conf:$ ./EditHttpConf -w ORACLE_BASE/admin/webN/config/OHS/ohsN [-oh Webgate_Oracle_Home] [-o output_file]
Note:
The
-ohWebGate_Oracle_Homeand-ooutput_fileparameters are optional.In the command,
WebGate_Oracle_Homeis the directory where you have installed Oracle HTTP Server Webgate for Oracle Access Manager. This directory is the Oracle home for Webgate; for example:MW_HOME/Oracle_OAMWebGate1The
ORACLE_BASE/admin/webN/config/OHS/ohsN/directory is the instance home of Oracle HTTP Server, whereNis a sequential number for your installation; for example,1forWEBHOST1or2forWEBHOST2.The
output_filevalue is the name of the temporary output file used by the tool; for example:Edithttpconf.log
18.2.5 Setting Up the WebLogic Server Authentication Providers
This section is based on the assumption that you have already set up the LDAP authentication provider by following the steps in Section 10.3.2, "Creating the LDAP Authentication Provider." If you have not already created the LDAP authentication provider, do it before continuing with this section.
This section covers the following topics:
18.2.5.1 Backing Up Configuration Files
To be safe, first back up the relevant configuration files:
ORACLE_BASE/admin/domain_name/aserver/domain_name/config/config.xml ORACLE_BASE/admin/domain_name/aserver/domain_name/config/fmwconfig/jps-config.xml ORACLE_BASE/admin/domain_name/aserver/domain_name/config/fwmconfig/system-jazn-data.xml
In addition, back up the boot.properties file for the Administration Server.
18.2.5.2 Setting Up the Oracle Access Manager Identity Assertion Provider
Set up an Oracle Access Manager identity assertion provider in the Oracle WebLogic Server Administration Console.
To set up the Oracle Access Manager identity assertion provider:
-
Log in to the WebLogic Server Administration Console, if not already logged in.
-
Click Lock & Edit.
-
Navigate to SecurityRealms, then the default realm name, and then Providers.
-
Name the asserter (for example,
OAM ID Asserter) and click OK. -
Click New, and select the asserter type OAMIdentityAsserter from the dropdown menu.
-
Click the newly added asserter to see the configuration screen for the Oracle Access Manager identity assertion provider.
-
Set the control flag to
REQUIRED. -
Select both the ObSSOCookie and OAM_REMOTE_USER options under Chosen types.
-
Save the settings, and click Activate Changes to propagate the changes.
Finally, log in to the WLST console as an administrator, and run the following command:
addOAMSSOProvider(loginuri="/${app.context}/adfAuthentication",logouturi="/oamsso/logout.html")
18.2.5.3 Setting the Order of Providers
Set the order of identity assertion and authentication providers in the WebLogic Server Administration Console.
To set the order of the providers:
-
Log in to the WebLogic Server Administration Console, if not already logged in.
-
Click Lock & Edit.
-
Navigate to SecurityRealms, then the default realm name, and then Providers.
-
Reorder the Oracle Access Manager identity assertion provider, the Oracle Internet Directory authentication provider, and the default authentication provider by ensuring that the control flag for each provider is set as follows:
-
Oracle Access Manager identity assertion provider: REQUIRED
-
Oracle Internet Directory authentication provider: SUFFICIENT
-
DefaultAuthenticator: SUFFICIENT
-
-
Click OK.
-
Click Activate Changes to propagate the changes.
-
Restart the Administration Server and all Managed Servers.
Stop the Administration Server with the
nmKillcommand, or with the Administration Console, and then starting it with thenmStartcommand, as described in Section 11.3, "Restarting the Administration Server."Before the restart, stop all Managed Servers in the domain through the Administration Console, and then start them after the restart. Log in to the Administration Console using the credentials for the
weblogic_ecmuser.
18.3 Integrating with Oracle Access Manager 10g
This section describes how to set up Oracle Access Manager 10g as the single sign-on solution for the Oracle WebCenter Content enterprise deployment topology. It contains the following sections:
-
Section 18.3.1, "Overview of Oracle Access Manager Integration"
-
Section 18.3.2, "Prerequisites for Oracle Access Manager 10g"
-
Section 18.3.5, "Configuring IP Address Validation for the Enterprise Deployment Webgate"
-
Section 18.3.6, "Setting up the Oracle Access Manager Identity Assertion Provider"
18.3.1 Overview of Oracle Access Manager Integration
This section explains the procedure for configuring the Oracle WebCenter Content installation with an existing Oracle Access Manager 10g installation and Oracle Internet Directory as the underlying directory service. For information about installing and configuring an Oracle Access Manager installation, see Oracle Fusion Middleware Enterprise Deployment Guide for Oracle Identity Management.
Note:
The Oracle WebCenter Content enterprise deployment topology described in this book uses a single sign-on configuration in which both the Oracle WebCenter Content system and the single sign-on system are in the same network domain (mycompany.com). For a multidomain configuration, see the required configuration steps in "Introduction to the OAM Policy Model, Single Sign-On" in the Oracle Fusion Middleware Administrator's Guide for Oracle Access Manager with Oracle Security Token Service.
18.3.2 Prerequisites for Oracle Access Manager 10g
The setup for Oracle Access Manager assumes an existing Oracle Access Manager 10g installation. For more information on installing and configuring an Oracle Access Manager installation, see the Oracle Fusion Middleware Enterprise Deployment Guide for Oracle Identity Management. This setup includes Oracle Internet Directory as the directory service.
In addition, the Oracle Access Manager installation should have its own Web server configured with WebGate.
18.3.3 Configuring Oracle Access Manager 10g
This section covers the following topics:
-
Section 18.3.3.1, "Collecting the Information for the OAM Configuration Tool"
-
Section 18.3.3.4, "Verifying Creation of the Policy Domain and AccessGate"
-
Section 18.3.3.9, "Configuring Delegated Form Authentication"
18.3.3.1 Collecting the Information for the OAM Configuration Tool
The OAM Configuration Tool (oamcfg) starts a series of scripts and sets up the required policies for Oracle Access Manager. It requires various parameters as inputs. Specifically, it creates the following:
-
A form authentication scheme in Oracle Access Manager
-
Policies to enable authentication in WebLogic Server
-
A WebGate entry in Oracle Access Manager to enable Oracle HTTP Server WebGates (from your Web Tier) to protect your configured application
-
A host identifier, depending on the scenario chosen (a default host identifier would be used, if not provided)
-
A host identifier, depending on the scenario chosen (a default host identifier would be used, if not provided)
-
Policies to protect and unprotect application specific URLs.
The following information should be collected or prepared prior to running the OAM Configuration Tool:
-
Password: Create a secure password. This will be used as the password for the WebGate installation created later.
-
LDAP Host: host name of the directory server or load balancer address in the case of a high-availability or enterprise deployment configuration.
Note:
The load balancer host name is the one that was used to configure the virtual servers in Section 3.3, "Load Balancers."
-
LDAP Port: port of the directory server.
-
LDAP USER DN: DN of the LDAP admin user. This will be a value such as
cn=orcladmin. -
LDAP password: password of the LDAP admin user.
-
oam_aaa_host: host name of an Oracle Access Manager.
-
oam_aaa_port: port of the Oracle Access Manager.
18.3.3.2 Running the OAM Configuration Tool
Run the OAM Configuration Tool to add the required resources to Oracle Access Manager for the Oracle WebCenter Content components. Create a file containing the list of URIs you want to protect with the following content:
######################################### #Product Name: Oracle WebCenter Content ######################################### ######################################### protected_uris ######################################### /adfAuthentication /imaging/faces /em /console /DefaultToDoTaskFlow /sdpmessaging/userprefs-ui /integration/worklistapp /workflow/sdpmessagingsca-ui-worklist /soa/composer /soa-infra/deployer /soa-infra/events/edn-db-log /soa-infra/cluster/info #"Policy using Basic Authn Scheme" is the name of the policy #"Basic Over LDAP" is the authentication scheme configured for this #policy # Note that the name of the policy and the scheme name in the URIs file # is tab-separated. In other words, there must be a tab between # "Basic Authn Scheme" and "OraDefaultBasicAuthNScheme" below. Policy using Basic Authn Scheme OraDefaultBasicAuthNScheme /inspection.wsil ######################################### public_uris ######################################### /soa-infra/services /soa-infra/directWSDL
Note:
In Oracle Access Manager 10g, all resources under a URL prefix are protected by the default rules of a policy domain unless more specific rules are applied to them through policies. For details on the different patterns you can use if you need more specialized protection patterns, see the Oracle Fusion Middleware Administrator's Guide for Oracle Access Manager with Oracle Security Token Service.
The OAM Configuration Tool resides in the ORACLE_COMMON_HOME/modules/oracle.oamprovider_11.1.1/ directory (ORACLE_COMMON_HOME depends on the machine where you are running the configuration tool). The tool can be run from any machine with the required installation files. In this case, you run it from WCCHOST1. Run the OAM Configuration Tool for Oracle Access Manager 10g registration as follows (all on a single command line):
MW_HOME/jrockit_160_version/bin/java -jar oamcfgtool.jar mode=CREATE app_domain="ECM_EDG" uris_file="full_path_to_file_containing_uri_definitions" app_agent_password=password_to_be_provisioned_for_App_Agent ldap_host=OID.MYCOMPANY.COM ldap_port=389 ldap_userdn="cn=orcladmin" ldap_userpassword=Password_of_LDAP_admin_user oam_aaa_host=OAMHOST1 oam_aaa_port=OAMPORT1
Note:
The examples documented in this guide use Oracle JRockit. Any certified version of Java can be used for this procedure and is fully supported unless otherwise noted.
If your command ran successfully, you should see the following output:
Date,Time oracle.security.oam.oamcfg.OAMCfgGlobalConfigHandler constructGlobalConfig INFO: Processed input parameters May 9, 2011 5:09:40 AM oracle.security.oam.oamcfg.OAMCfgGlobalConfigHandler constructGlobalConfig INFO: Initialized Global Configuration Date,Time oracle.security.oam.oamcfg.create.impl.OAMCfgConfigCreator doCreate INFO: Successfully completed the Create operation. Date,Time oracle.security.oam.oamcfg.create.impl.OAMCfgConfigCreator doCreate INFO: Operation Summary: Date,Time oracle.security.oam.oamcfg.create.impl.OAMCfgConfigCreator doCreate INFO: Policy Domain : ECM_EDG Date,Time oracle.security.oam.oamcfg.create.impl.OAMCfgConfigCreator doCreate INFO: Host Identifier: ECM_EDG Date,Time oracle.security.oam.oamcfg.create.impl.OAMCfgConfigCreator doCreate INFO: Access Gate ID : ECM_EDG_AG
18.3.3.3 Oracle Access Manager Logout Guidelines
For applications invoked by Oracle WebCenter Content and Oracle WebCenter Content: Imaging to comply with Oracle Access Manager logout guidelines (in particular, applications that invoke a logout through /adfAuthentication?logout=true&end_url=some_URI), integration with an Oracle Access Manager 10g environment requires additional configuration on the WebGate to handle the end_url. Without this additional configuration, you are logged out, but not redirected to the end URL because Oracle Access Manager 10g WebGate does not process end_url. For information about configuration procedures, see the Oracle Fusion Middleware Application Security Guide.
When integrating Oracle WebCenter Content with Oracle Access Manager 10g, you must add the URL /oamsso/logout.html to the logout URL setting for the Access Gate for the single sign-on logout to work properly. For more information, see "Configuring a Single Sign-On Logout URL" and "AccessGate Configuration Parameters" in the Oracle Access Manager Access Administration Guide.
18.3.3.4 Verifying Creation of the Policy Domain and AccessGate
To verify successful creation of the policy domain and AccessGate, you need to verify the policy domain and then the AccessGate configuration.
18.3.3.4.1 Verifying the Policy Domain
Verify the policy domain in Oracle Access Manager.
To verify the policy domain:
-
Log in to Oracle Access Manager:
http://OAMADMINHOST:port/access/oblix/ -
Click Policy Manager.
-
Click the My Policy Domains link on the left. You will see a list of all policy domains, which includes the domain you just created. It will have the suffix _PD (for example, ECM_EDG_PD). In the third column (URL prefixes), you will also see the URIs you specified during the creation of this domain).
-
Click the link to the policy domain you just created to go to the General area of this domain.
-
Open the Resources tab and you will see the URIs you specified. You can also click other tabs to view other settings.
18.3.3.4.2 Verifying the AccessGate Configuration
Verify the AccessGate configuration in Oracle Access Manager.
To verify the AccessGate configuration:
-
Click the Access System Console link on the top right-hand side (this acts like a toggle; after you click it, it becomes the Policy Manager link).
-
Open the Access System Configuration tab.
-
Click the AccessGate Configuration link on the left.
-
Enter
ECM_EDGas the search criterion (or any other substring you may have used as theapp_domainname in Section 18.3.3.2, "Running the OAM Configuration Tool"), and click Go. -
Once the access gate for the domain you just created shows up (this will have the suffix _AG (for example, ECM_EDG_AG), click it, and you will see the details of the access gate you just created.
18.3.3.5 Verifying That the Cookieless Basic Authorization Scheme Has Been Properly Assigned
Verify the assignment of the cookieless basic authorization scheme in Oracle Access Manager.
To verify that the cookieless basic authorization scheme has been properly assigned:
-
Log in to Oracle Access Manager:
http://OAMADMINHOST:port/access/oblix/ -
Click Policy Manager.
-
Click the My Policy Domains link on the left. You will see a list of all policy domains that have been created.
-
Click ECM_EDG.
-
Open the Policies tab and then click Policy using Basic Authn Scheme.
-
Open the General section.
The
inspection.wsilresource should be listed. -
Open the Authentication Rule section.
The
OraDefaultBasicAuthNSchemeauthentication scheme should be listed.
18.3.3.6 Updating the Host Identifier
The OAM Configuration Tool uses the value of the app_domain parameter to create a host identifier for the policy domain. This host identifier must be updated with all the host name variations for the host so that the configuration works correctly.
To update the host identifier created by the OAM Configuration Tool:
-
Navigate to the Access System Console by specifying the following URL in your web browser:
http://host_name:port/access/oblix
where
host_namerefers to the host where the WebPass Oracle HTTP Server instance is running andportrefers to the HTTP port of the Oracle HTTP Server instance. -
When prompted for a user name and password, log in as an administrator. Click OK.
-
On the Access System main page, click the Access System Console link.
-
On the Access System Console page, open the Access System Configuration tab.
-
On the Access System Configuration page, click Host Identifiers at the bottom left.
-
On the List all host identifiers page, click the host identifier created by the OAM Configuration Tool (for example, ECM_EDG).
-
On the Host Identifier Details page, click Modify.
-
Add the Preferred HTTP Host value used in Access System Configuration. A list of all the possible host name variations using SSO/WebGate follows:
webhost1.mydomain.com:7777 webhost2.mydomain.com:7777 wcchost1.mycompany.com:16200 wcchost2.mycompany.com:16200 adminvhn.mycompany.com:7001 wcchost1vhn1.mycompany.com:8001 wcchost1vhn2.mycompany.com:16000 wcchost1vhn3.mycompany.com:16400 wcchost2vhn1.mycompany.com:8001 wcchost2vhn2.mycompany.com:16000 wcchost2vhn3.mycompany.com:16400 admin.mycompany.com:80 wcc.mycompany.com:443 wccinternal.mycompany.com:80 sso.mycompany.com:7779 [WebGate access with Oracle Oracle Identity Management port]
-
Select the Update Cache checkbox, and then click Save.
A message box with the following message is displayed:
Updating the cache at this point will flush all the caches in the system. Are you sure?Click OK to finish saving the configuration changes.
-
Verify the changes on the Host Identifier Details page.
18.3.3.7 Updating the WebGate Profile
The OAM Configuration Tool populates the Preferred_HTTP_Host and hostname attributes for the WebGate profile that is created with the value of the app_domain parameter. Both these attributes must be updated with the proper values for the configuration to work correctly.
To update the WebGate profile created by the OAM Configuration Tool:
-
Navigate to the Access System Console by specifying the following URL in your web browser:
http://host_name:port/access/oblix
where
host_namerefers to the host where the WebPass Oracle HTTP Server instance is running andportrefers to the HTTP port of the Oracle HTTP Server instance. -
On the Access System main page, click the Access System Console link, then log in as an administrator.
-
On the Access System Console main page, click Access System Configuration, and then click the Access Gate Configuration link on the left to display the AccessGates Search page.
-
Enter the proper search criteria and click Go to display a list of access gates.
-
Select the access gate created by the OAM Configuration Tool (for example, ECM_EDG_AG).
-
On the AccessGate Details page, select Modify to display the Modify AccessGate page.
-
On the Modify AccessGate page, update the following:
-
Hostname: Update the host name with the name of the computer where WebGate is running, for example:
webhost1.mycompany.com. -
Preferred HTTP Host: Update the Preferred_HTTP_Host with one of the host name variations specified in the previous section; for example:
admin.mycompany.com:80. -
Primary HTTP Cookie Domain: Update the Primary HTTP Cookie Domain with the domain suffix of the host identifier; for example:
mycompany.com
-
-
Click Save.
A message box with the following message is displayed:
Are you sure you want to commit these changes?Click OK to finish updating the configuration.
-
Verify the values displayed on the Details for AccessGate page to confirm that the updates were successful.
18.3.3.8 Adding Additional Access Servers
You can add access servers to WebGate.
To assign an access server to WebGate:
-
Log in as the Administrator on the Access System Console.
-
Navigate to the Details for AccessGate page, if necessary. From the Access System Console, select Access System Configuration, then AccessGate Configuration, then the link for the WebGate (ECM_EDG_AG).
-
On the Details for AccessGate page, click List Access Servers.
-
A page appears showing the primary or secondary Access Servers currently configured for this WebGate.
Click Add.
-
On the Add a New Access Server page, select an Access Server from the Select Server list, specify Primary Server, and define two connections for the WebGate.
Click the Add button to complete the association.
-
A page appears, showing the association of the Access Server with the WebGate. Click the link to display a summary and print this page for later use.
-
Repeat steps 3 through 6 to associate more access servers to the WebGate.
18.3.3.9 Configuring Delegated Form Authentication
Configure the form authentication to redirect to the WebGate instance that was installed with the Oracle Access Manager installation.
To configure delegated form authentication:
-
Open the Access System Console.
-
In the Access System Configuration screen, select Authentication Management on the left.
-
Select OraDefaultFormAuthNScheme.
-
Click Modify.
-
In the Challenge Redirect field, enter the host and port of the Oracle Identity Management installation; for example:
http://sso.mycompany.com. Click Save when you are done.
A WebGate should already be installed in the Oracle Identity Management installation. For details, see the Oracle Fusion Middleware Enterprise Deployment Guide for Oracle Identity Management.
18.3.4 Installing and Configuring WebGate
WebGate needs to be installed on both WEBHOST1 and WEBHOST2 to secure Oracle Web Tier.
Note:
There is a known issue with the Oracle Access Manager installer that sometimes manifests as a hang at install time on Linux. This is a third-party issue caused by InstallShield. To work around this issue, follow these steps:
-
Copy and paste the following in the shell where you start the installer:
cd /tmp mkdir bin.$$ cd bin.$$ cat > mount <<EOF #! /bin/sh exec /bin/true EOF chmod 755 mount export PATH=`pwd`:$PATH
-
Run the installation.
-
When the installer is finished running, clean the temporary directory using this command:
rm -r /tmp/bin.$$
To install and configure WebGate:
-
Launch the WebGate installer (see Section 2.4, "Software Components to Install," for information on where to obtain it) using the following command on WEBHOSTn:
./Oracle_Access_Manager10_1_4_3_0_linux_OHS11g_WebGate –gui
-
In the Welcome screen, click Next.
-
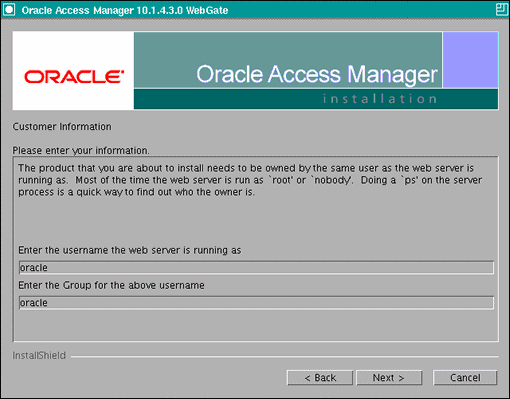
In the Customer Information screen (Figure 18-1), enter the user name and user group that the web server is running as. Click Next to continue.
-
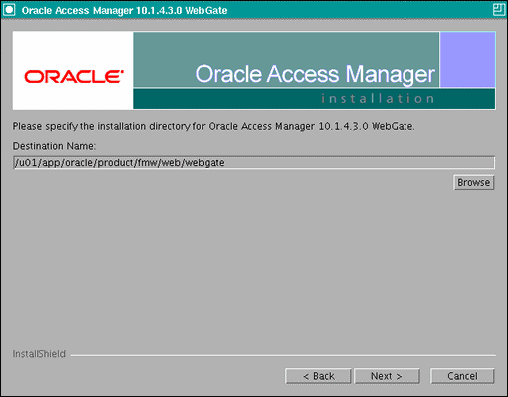
In the installation target screen (Figure 18-2), specify the directory where WebGate should be installed. Click Next to continue.
-
In the installation summary screen, click Next.
-
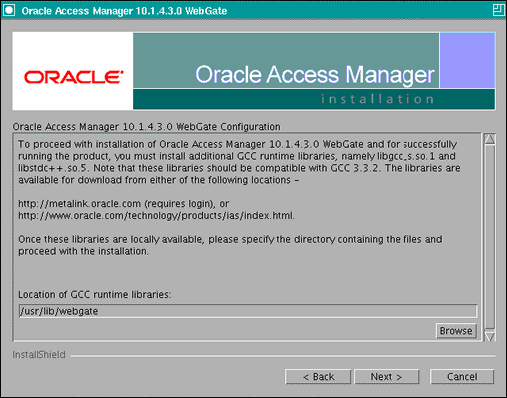
Download the required GCC runtime libraries for WebGate as instructed in the WebGate configuration screen (Figure 18-3), and use Browse to point to their location on the local computer. Click Next to continue.
-
The installer now creates the required artifacts. After that is completed, click Next to continue.
-
In the transport security mode screen (Figure 18-4), select Open Mode: No Encryption and click Next to continue.
Figure 18-4 Transport Security Mode Screen

Description of "Figure 18-4 Transport Security Mode Screen"
-
In the WebGate configuration screen, provide the details of the access server that will be used. You must provide the following information:
-
WebGate ID, as provided when the OAM Configuration Tool was executed
-
Password for WebGate
-
Access Server ID, as reported by the Oracle Access Manager Access Server configuration
-
Access Server host name, as reported by the Oracle Access Manager Access Server configuration
-
Access Server port number, as reported by the Oracle Access Manager Access Server configuration
Note:
The Access Server ID, host name, and port are all required.
You can obtain these details from your Oracle Access Manager administrator. Click Next to continue.
Figure 18-5 Access Server Configuration Screen
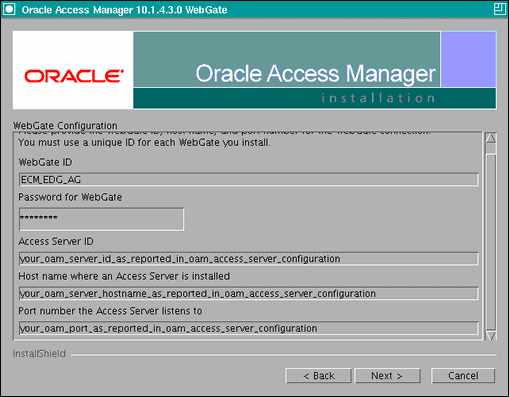
Description of "Figure 18-5 Access Server Configuration Screen"
-
-
In the Configure Web Server screen, click Yes to automatically update the web server. Click Next to continue.
-
In the next Configure Web Server screen, specify the full path of the directory containing the
httpd.conffile. This file is located in the following directory:ORACLE_BASE/admin/OHS_Instance/config/OHS/OHS_Component_Name
For example:
/u01/app/oracle/admin/ohs_instance2/config/OHS/ohs2/httpd.conf
Click Next to continue.
-
In the next Configure Web Server page, a message informs you that the Web server configuration has been modified for WebGate. Click Yes to confirm.
-
Stop and start your Web server for the configuration updates to take effect. Click Next to continue.
-
In the next Configure Web Server screen, the following message is displayed:
If the web server is set up in SSL mode, then the httpd.conf file needs to be configured with the SSL related parameters. To manually tune your SSL configuration, please follow the instructions that come up.Click Next to continue.
-
In the next Configure Web Server screen, a message with the location of the document that has information on the rest of the product setup and Web server configuration is displayed. Choose No, and click Next to continue.
-
The final Configure Web Server screen appears with a message to manually launch a browser and open the HTML document for further information on configuring your Web server. Click Next to continue.
-
The Oracle COREid Readme screen appears. Review the information on the screen and click Next to continue.
-
A message appears (along with the details of the installation) informing you that the installation was successful.
18.3.5 Configuring IP Address Validation for the Enterprise Deployment Webgate
IP address validation determines if a client's IP address is the same as the IP address stored in the ObSSOCookie cookie generated for single sign-on. IP address validation can cause issues in systems using load-balancer devices configured to perform IP address termination or when the authenticating Webgate is front-ended by a different load-balancing router (LBR) or proxy than the one front-ending the enterprise deployment.
To make sure your enterprise deployment LBR or proxy is not validated in these cases:
-
Open the Access System Console and log in as an administrator at the following URL:
http://host_name:port/access/oblix
where
host_namerefers to the host where the WebPass Oracle HTTP Server instance is running andportrefers to the HTTP port of the Oracle HTTP Server instance. -
On the Access System main page, click the Access System Console link.
-
On the Access System Console main page, click Access System Configuration, and then click the Access Gate Configuration link on the left to display the AccessGates Search page.
-
Enter the appropriate search criteria, and click Go to display a list of access gates.
-
Select the access gate created by the OAM Configuration Tool.
-
Click Modify at the bottom of the page.
-
In the IPValidationException field, enter the IP address of the load balancer or proxy front-ending the enterprise deployment.
Note:
The load balancer host name is the one that was used to configure the virtual servers in Section 3.3, "Load Balancers."
-
Click Save at the bottom of the page.
18.3.6 Setting up the Oracle Access Manager Identity Assertion Provider
This section is based on the assumption that you have already set up the LDAP authentication provider by following the steps in Section 10.3.2, "Creating the LDAP Authentication Provider." If you have not already created the LDAP authentication provider, do it before continuing with this section.
This section covers the following topics:
18.3.6.1 Back Up Configuration Files
To be safe, first back up the relevant configuration files:
ORACLE_BASE/admin/domain_name/aserver/domain_name/config/config.xml ORACLE_BASE/admin/domain_name/aserver/config/fmwconfig/jps-config.xml ORACLE_BASE/admin/domain_name/aserver/domain_name/config/fmwconfig/ system-jazn-data.xml
Also back up the boot.properties file for the Administration Server.
18.3.6.2 Setting Up the Oracle Access Manager Identity Assertion Provider
Set up an Oracle Access Manager identity assertion provider in the WebLogic Server Administration Console.
To set up the Oracle Access Manager identity assertion provider:
-
Log in to the WebLogic Server Administration Console, if not already logged in.
-
Click Lock & Edit.
-
Navigate to SecurityRealms, then the default realm name, and then Providers.
-
Click New and select OAMIdentityAsserter from the dropdown menu.
-
Name the asserter (for example,
OAM ID Asserter) and click OK. -
Click the newly added asserter to see the configuration screen for the Oracle Access Manager identity assertion provider.
-
Set the control flag to
REQUIREDand click Save. -
Open the Provider Specific tab to configure the following required settings:
-
Primary Access Server: provide Oracle Access Manager server endpoint information in host:port format.
-
AccessGate Name: name of the AccessGate (for example,
ECM_EDG_AG). -
AccessGate Password: password for the AccessGate (optional).
-
-
Save the settings.
18.3.6.3 Setting the Order of Providers
Reorder the Oracle Access Manager identity assertion provider, the Oracle Internet Directory authentication provider, and the default authentication provider by ensuring that the control flag for each provider is set as follows:
-
Oracle Access Manager identity assertion provider:
REQUIRED -
Oracle Internet Directory LDAP authentication provider:
SUFFICIENT -
DefaultAuthenticator:SUFFICIENT -
DefaultIdentityAsserter
After reordering, save the settings, activate the changes, and restart all servers. Stop the Administration Server with the nmKill command, or with the Administration Console, and then starting it with the nmStart command, as described in Section 11.3, "Restarting the Administration Server." Before the restart, stop all Managed Servers in the domain through the Administration Console, and then start them after the restart. Log in to the Administration Console using the credentials for the weblogic_ecm user.
Note:
Do not forget to create a new credential for the new user. See Section 14.5.14, "Configuring a BPEL CSF Credential" for further details. (This book uses the weblogic_ecm user as an example for SSO.)
18.4 Validating Access Through the Load Balancer and SSO
Validate single sign-on through the front end (using the SSO user name and password):
-
http://admin.mycompany.com/console -
http://admin.mycompany.com/em -
http://wcc.mycompany.com/cs -
http://wcc.mycompany.com/imaging -
https://wcc.mycompany.com/dc-console
18.5 Backing Up the Installation
After you have verified that the extended domain is working, back up the installation. This is a quick backup for the express purpose of immediate restore in case of problems in the further steps. The backup destination is the local disk. This backup can be discarded once the enterprise deployment setup is complete. At that point, the regular deployment-specific backup and recovery process can be initiated. The Oracle Fusion Middleware Administrator's Guide provides further details. For information about describing the Oracle HTTP Server data that must be backed up and restored, see the "Backup and Recovery Recommendations for Oracle HTTP Server" section in this guide. For information on how to recover components, see the "Recovery of Components" and "Recovery After Loss of Component" sections in the guide. For recommendations specific to recovering from the loss of a host, see the "Recovering Oracle HTTP Server to a Different Host" section in the guide. For information about database backup, see the Oracle Database Backup and Recovery User's Guide.
To back up the installation at this point:
-
Back up Oracle Web Tier:
-
Shut down the instance using
opmnctl:ORACLE_BASE/admin/instance_name/bin/opmnctl stopall -
Back up the Middleware home on Oracle Web Tier using the following command (as root):
tar -cvpf BACKUP_LOCATION/web.tar $MW_HOME
-
Back up the Instance Home on Oracle Web Tier using the following command (as root):
tar -cvpf BACKUP_LOCATION/web_instance.tar $ORACLE_INSTANCE
-
Start the instance using
opmnctl:ORACLE_BASE/admin/instance_name/bin/opmnctl startall
-
-
Back up the AdminServer domain directory on WCCHOST1. Perform a backup to save your domain configuration. The configuration files all exist under the
ORACLE_BASE/ admin/domain_name/directory.tar -cvpf edgdomainback.tar ORACLE_BASE/admin/domain_name