In This Section:
Configuring SSL When Configuring Analytics Link Server
Configuring SSL When Configuring Data Synchronization Server
Directory Objects Created When Configuring SSL
Importing Certificates to Existing Wallets or Keystores
Enabling an SSL Connection Between Analytics Link and Administration Services Console
Secure Sockets Layer (SSL) is a cryptographic protocol used to secure data exchange over the network. For more information about enabling Secure Sockets Layer (SSL) for EPM System products, see the Oracle Hyperion Enterprise Performance Management System Security Administration Guide.
To provide secure and private Web networking over TCP/IP using the https protocol, you can enable Secure Socket Layer (SSL) for Analytics Link.
In the beginning of an SSL interaction, the client sends a secure session request, known as a “handshake,” to the server. The handshake contains encryption information and a request for an certificate of authenticity from the server. The server returns a certificate, and the client validates it against a known list of certificate authorities (CA). The verification is one-way: The server does not verify the client.
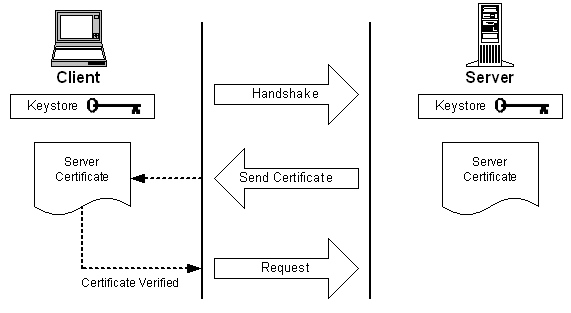
After the client verifies the certificate from the server, the client and server can now communicate securely using encrypted keys known only to the client and server.
Analytics Link Configuration Tool creates two kinds of storage for certificates during the SSL activation process: Oracle Wallet and Java Keystore. Both types of certificates are created to enable an SSL connection between the C++-based and Java-based components of Analytics Link Server and the C++-based components of Data Synchronization Server.
Oracle Wallet is used to store security certificates for C++-based components. During activation of SSL for Analytics Link, the configuration tool creates two wallets into which it imports certificates:
Analytics Link Server Wallet—The Data Synchronization Server credentials are imported into this wallet as a trusted certificate. These credentials enable the Analytics Link Server library hrAPI.dll to connect to Data Synchronization Server.
Data Synchronization Server Wallet—The Data Synchronization Server credentials are imported into this wallet as trusted certificates. Additionally, to enable Data Synchronization Server to connect to Analytics Link Server, Analytics Link Server credentials are imported into this wallet as trusted certificates.
Note: | To set up Oracle Wallet, you need the Oracle public key infrastructure (PKI) command line tool, orapki. You use the orapki utility to manage public key infrastructure elements such as wallets and certificate revocation lists. |
For information about setting up Oracle Wallet, see the Oracle Hyperion Enterprise Performance Management System Security Administration Guide.
Java Keystore is used to store security certificates for Java-based components. During activation of SSL for Analytics Link, the configuration tool creates a custom keystore for Analytics Link Server, and imports Analytics Link Server certificates and Data Synchronization Server certificates into the custom keystore as trusted entries.
Note: | No separate keystore is necessary for Data Synchronization Server. |
On the Components to Configure page in Analytics Link Configuration Tool, when you select to configure Analytics Link Server, you can also select these options to enable SSL:
Analytics Link Server and Data Synchronization Server—See Enabling SSL for Analytics Link Server and Data Synchronization Server.
RDBMS—See Enabling SSL for RDBMS.
Shared Services—See Enabling SSL for Shared Services.
In selecting this option, all Analytics Link components connect to each other using an SSL connection:
Analytics Link Server
Data Synchronization Server
Analytics Link Financial Management Connector
During the Analytics Link Server configuration process, Analytics Link Server connects to Data Synchronization Server and Analytics Link Financial Management Connector; therefore, the latter two components must be SSL-enabled.
The configuration process automatically deploys Analytics Link Server and Data Synchronization Server in SSL mode . Non-SSL mode is not supported.
Configuring the Data Synchronization Server SSL connection:
If Analytics Link Server and Data Synchronization Server are installed locally (on the same computer with a shared file system and same HFS_HOME environment variable), the configuration tool automatically creates and imports the local Data Synchronization Server certificates. No additional configuration is needed to activate SSL between these components after running the configuration tool.
If Data Synchronization Server is installed on a different computer than the one on which Analytics Link Server is installed, from the Data Synchronization Server computer, you must import the following certificates in the order listed:
Import the CERT_DIR\dss_cert.hostName.cer file into the HFS_HOME\conf\security\jks directory.
Import the CERT_DIR\dss_ca_root_cert.hostName.cer file into the HFS_HOME\conf\security\wallet directory.
Import the CERT_DIR\dss_cert.hostName.cer file into the HFS_HOME\conf\security\wallet directory.
For the location of the certificate files, see Directory Objects Created When Configuring SSL.
Configuring the Analytics Link Financial Management Connector SSL connection:
Analytics Link Financial Management Connector runs in Microsoft IIS (Internet Information Services) Web Server, which is the web server on which the Financial Management Application Server runs. IIS must be SSL enabled.
You must import the IIS certificate into the HFS_HOME\conf\security\jks directory.
Analytics Link connects to the following RDBMS components:
Analytics Link repository
Financial Management repository
Shared Services repository (Shared Services Release 11.1.2.0 or later)
Analytics Link bridge Data Store
These repositories may reside in different databases; however, Analytics Link supports only one connection mode for all repositories: SSL connection mode or non-SSL connection mode. Therefore, if one repository is SSL enabled, all of the repositories must be SSL enabled.
In selecting this option, you must import the RDBMS certificate for each of the repositories listed above into the HFS_HOME\conf\security\jks directory.
Analytics Link security is managed by Foundation Services (Oracle Hyperion Shared Services). If Foundation Services is SSL enabled, all EPM System products that use Foundation Services for security management must be SSL enabled.
In selecting this option, you must import the certificates for all Oracle Enterprise Performance Management System SSL-enabled products to which Analytics Link connects into the HFS_HOME\conf\security\jks directory:
Oracle Hyperion Foundation Services
Provider Services (the use of Oracle Hyperion Provider Services in your Analytics Link environment is optional)
On the Components to Configure page in Analytics Link Configuration Tool, when you select to configure Data Synchronization Server, you can also select these options to enable SSL:
Analytics Link Server and Data Synchronization Server—See Enabling SSL for Analytics Link Server and Data Synchronization Server.
RDBMS—See Enabling SSL for RDBMS.
In selecting this option, all Analytics Link components connect to each other using an SSL connection:
Analytics Link Server
Data Synchronization Server
Analytics Link Financial Management Connector
During the Data Synchronization Server configuration process, Analytics Link Server connects to Data Synchronization Server; therefore, Analytics Link Server must be SSL-enabled. See Configuring SSL When Configuring Analytics Link Server.
The configuration process automatically deploys Analytics Link Server and Data Synchronization Server in SSL mode . Non-SSL mode is not supported.
In configuring the Data Synchronization Server SSL connection:
If Data Synchronization Server and Analytics Link Server are installed locally (on the same computer with a shared file system and same HFS_HOME environment variable), the configuration tool automatically creates and imports the local Analytics Link Server certificates. No additional configuration is needed to activate SSL between these components after running the configuration tool.
If Data Synchronization Server is installed on a different computer than the one on which Analytics Link Server is installed, from the Analytics Link Server computer, you must import the CERT_DIR\eal_ca_root_cert.hostName.cer certificate file into the HFS_HOME\conf\security\wallet directory.
Data Synchronization Server connects to the Financial Management Server repository in order to read Financial Management application data. If the Financial Management Server repository resides on an SSL-enabled RDBMS, you must import the RDBMS certificate into the HFS_HOME\conf\security\wallet directory.
If you are not using a root certificate from a trusted third-party CA for the Oracle Hyperion Financial Management Server repository RDBMS, first, verify that your root CA certificate is loaded and then import the certificate into the HFS_HOME\conf\security\wallet directory.
Analytics Link Configuration Tool creates directories and objects related to certificate storage, as listed in Table 21. (CERT_DIR is a variable that refers to the HFS_HOME\conf\security\certs directory.)
Table 21. Directory Objects Created by Configuring SSL
| Object | Description |
|---|---|
| HFS_HOME\conf\security\wallet_root_tmp | Oracle wallet temp directory. Wallet password: ealpassword1. Contents of the wallet: Data Synchronization Server Self-Signed CA Certificate for the local Data Synchronization Server instance: CERT_DIR\dss_ca_root_cert.hostName.cer This certificate appears in the wallet as User Certificate and as Trusted Certificate (CN=testDSS-CA). |
| HFS_HOME\conf\security\wallet | Oracle Wallet directory. Wallet password: ealpassword1. Contents of the wallet:
|
| HFS_HOME\conf\security\jks\eal_identity.jks | Identity Java Keystore. Keystore password (for both storepass and keypass): ealpassword. Contents of the keystore: Self-Signed Analytics Link Server certificate: CERT_DIR\eal_ca_root_cert.hostName.cer This certificate appears in the keystore as PrivateKeyEntry (CN= testEAL). |
| HFS_HOME\conf\security\jks\eal_trusted.jks | Trusted Java Keystore. Keystore password (for both storepass and keypass): ealpassword. Contents of the keystore:
|
To add a Data Synchronization Server certificate to any Oracle Wallet, import the following files:
dss_ca_root_cert.hostName.cer dss_cert.hostName.cer
To add a Data Synchronization Server certificate to any Java Keystore, import the following file:
dss_cert.hostName.cerTo add an Analytics Link Server certificate to any Oracle Wallet or Java Keystore, import the following file:
eal_ca_root_cert.hostName.cerIf Analytics Link Server and Data Synchronization Server are SSL-enabled, the Analytics Link Administration Services Console plug-in in Administration Services Console can connect to Analytics Link Server with an SSL connection, even if Oracle Essbase Administration Services itself is not SSL enabled. To configure the SSL connection, you must import the CERT_DIR\eal_ca_root_cert.hostName.cer file into the Administration Services Console Java Keystore.
The full path to the Administration Services Console Java Keystore is defined in the EAS_HOME\console\bin\admincon.lax file as the value of the -Djavax.net.ssl.trustStore variable in the lax.nl.java.option.additional tag. For example:
lax.nl.java.option.additional=.-Djavax.net.ssl.trustStore=C:\Oracle\Middleware\EPMSystem11R1\common\JRE\Sun\1.6.0\lib\security\cacerts
If -Djavax.net.ssl.trustStore is not defined, you must define the path and then import the CERT_DIR\eal_ca_root_cert.hostName.cer file into the Java Keystore.