In This Section:
When security levels defined for applications, databases, users, and groups are insufficient, Essbase security filters give you more specific control. Filters enable you to control access to individual data within a database by defining what kind of access is allowed to which parts of the database, and to whom these settings apply.
If you have Administrator permissions, you can define and assign any filters to any users or groups. Filters do not affect you.
If you have Create/Delete Applications permissions, you can assign and define filters for applications that you created.
If you have Application Manager or Database Manager permissions, you can define and assign filters within your applications or databases.
Filters control security access to data values, or cells. You create filters to accommodate security needs for specific parts of a database. When you define a filter, you designate restrictions on particular database cells. When you save the filter, you give it a unique name to distinguish it from other filters, and the server stores it in the essbase.sec security file. You can then assign the filters to any users or groups on Essbase Server.
For example, a manager designs a filter named RED and associates it with a database to limit access to cells containing profit information. The filter is assigned to a visiting group called REVIEWERS, so that they can read, but cannot alter, most of the database; they have no access to Profit data values.
Filters comprise one or more access settings for database members. You can specify the following access levels and apply them to data ranging from a list of members to one cell:
None: No data can be retrieved or updated for the specified member list.
Read: Data can be retrieved but not updated for the specified member list.
Write: Data can be retrieved and updated for the specified member list.
Metaread: Metadata (dimension and member names) can be retrieved and updated for the corresponding member specification.
Any cells that are not specified in the filter definition inherit the database access level. Filters can, however, add or remove access assigned at the database level, because the filter definition, being more data-specific, indicates a greater level of detail than the more general database access level.
Data values not covered by filter definitions default first to the access levels defined for users and, when Essbase is in native security mode, second to the global database access levels.
Calculation access is controlled by permissions granted to users and groups. Users who have calculate access to the database are not blocked by filters—they can affect all data elements that the execution of their calculations would update. When Essbase is in native security mode, calculation access is also controlled by minimum global permissions for the application or database.
Note: | During the calculation of MDX calculated members, cells to which a user does not have access are treated as #MISSING cells. |
You can create a filter for each set of access restrictions you need to place on database values. You need not create separate filters for users with the same access needs. After you have created a filter, you can assign it to multiple users or groups of users. However, only one filter per database can be assigned to a user or group.
If you use a calculation function that returns a set of members, such as children or descendants, and it evaluates to an empty set, the security filter is not created. An error is written to the application log stating that the region definition evaluated to an empty set. |
Before creating a filter, perform the following actions:
Connect to the server and select the database associated with the filter.
Check the naming rules for filters in Limits.
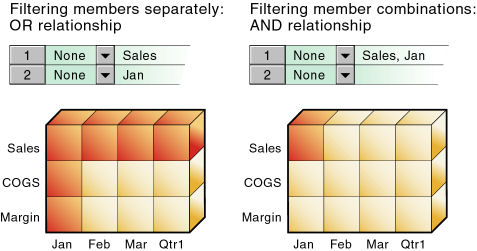
Figure 144, How Filters Affect Data AND/OR Relationships illustrates different ways to control access to database cells. Data can be protected by filtering entire members or by filtering member combinations.
Filtering on member combinations (AND relationship) does not apply to metaread. Metaread filters each member separately (OR relationship). |
To filter all the data for one or more members, define access for each member on its own row in Filter Editor. Filter definitions on separate rows of a filter are treated with an OR relationship.
For example, to block access to Sales or Jan, assume that user KSmith is assigned the following filter:
Access: None. Member specification: Sales.
Access: None. Member specification: Jan.
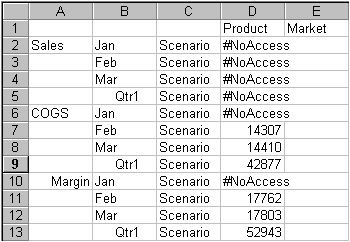
The next time user KSmith connects to Sample.Basic, her spreadsheet view of the profit margin for Qtr1 (Figure 145, Results of Filter Blocking Access to Sales or Jan) shows that she has no access to data values for the member Sales or the member Jan, which are marked with #NOACCESS. All data for Sales is blocked from view, as well as all data for January, inside and outside of the Sales member. Data for COGS (Cost of Goods Sold), a sibling of Sales and a child of Margin, is available, with the exception of COGS for January.
To filter data for member combinations, define the access for each member combination using a row in Filter Editor. In filter definitions, two member sets separated by a comma are treated as union of those two member sets (an AND relationship).
For example, assume that user RChinn is assigned the following filter: Access: None. Member specification: Sales, Jan.
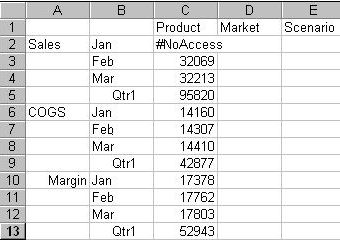
The next time user RChinn connects to Sample.Basic, her spreadsheet view of the profit margin for Qtr1 (Figure 146, Results of Filter Blocking Access to Sales, Jan) shows that she has no access to the data value at the intersection of members Sales and Jan, which is marked with #NoAccess. Sales data for January is blocked from view. However, Sales data for other months is available, and non-Sales data for January is available.
Substitution variables enable you to more easily manage information that changes regularly. Each substitution variable has an assigned name and value. The Database Manager can change the value anytime. Where a substitution variable is specified in a filter, the substitution variable value at that time is used.
For example, if you want a group of users to see data only for the current month, you can set up a substitution variable named CurMonth and define a filter (MonthlyAccess) wherein you specify access, using &CurMonth for the member name. Using an ampersand (&) at the beginning of a specification identifies it as a substitution variable instead of a member name to Essbase. Assign the MonthlyAccess filter to the appropriate users.
Each month, you need to change only the value of the CurMonth substitution variable to the member name for the current month, such as Jan, Feb, and so on. The new value will apply to all assigned users.
You can use filters to restrict access to data for base members sharing a particular attribute. To filter data for members with particular attributes defined in an attribute dimension, use the attribute member in combination with the @ATTRIBUTE function or the @WITHATTR function.
@ATTRIBUTE and @WITHATTR are member set functions. Most member set functions can be used in filter definitions. |
For example, assume that user PJones is assigned this filter: Access: None. Member specification: @ATTRIBUTE(“Caffeinated_False”).
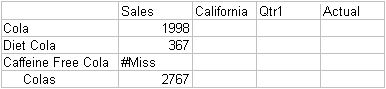
The next time user PJones connects to Sample.Basic, his spreadsheet view of first-quarter cola sales in California (Figure 147, Results of Filter Blocking Access to Caffeine-free Products) shows that he has no access to the data values for any base dimension members associated with Caffeinated_False. Sales data for Caffeine Free Cola is blocked from view. Note that Caffeine Free Cola is a base member, and Caffeinated_False is an associated member of the attribute dimension Caffeinated (not shown in the above spreadsheet view).
Metadata filtering provides data filtering and an additional layer of security. With metadata filtering, an administrator can remove outline members from a user's view, providing access only to those members that are of interest to the user.
When a filter is used to apply MetaRead permission on a member:
Data for all ancestors of that member are hidden from the filter user’s view.
Data and metadata (member names) for all siblings of that member are hidden from the filter user’s view.
You can copy filters to applications and databases on any Essbase Server, according to your permissions. You can also copy filters across servers as part of application migration.
After you define filters, you can assign them to users or groups, which lets you manage multiple users who require the same filter settings. Modifications to the definition of a filter are automatically inherited by users of that filter.
Filters do not affect users who have the Administrator role. Only one filter per database can be assigned to a user or group.
In EPM System security mode, you assign filters through Oracle's Hyperion® Shared Services Console.
 To assign a filter to a user or group, see Assigning Database Calculation and Filter Access in Shared Services.
To assign a filter to a user or group, see Assigning Database Calculation and Filter Access in Shared Services.
If a filter contains rows that have overlapping member specifications, the inherited access is set by the following rules, listed in order of precedence:
For example, this filter contains overlap conflicts:
Access: Write. Member specification: Actual.
Access: None. Member specification: Actual.
Access: Read. Member specification: Actual, @IDESCENDANTS(“New York”).
The third specification defines security at a greater level of detail than the other two. Therefore, read access is granted to all Actual data for members in the New York branch.
Because write access is a higher access level than none, the remaining data values in Actual are granted write access.
All other cells, such as Budget, are accessible according to the minimum database permissions.
You should define a MetaRead filter using multiple rows only when the affected member set in any given row (the metaread members and their ancestors) has no overlap with MetaRead members in other rows. It is recommended that you specify one dimension per row in filters that contain MetaRead on multiple rows. However, as long as there is no overlap between the ancestors and MetaRead members, it is still valid to specify different member sets of one dimension into multiple MetaRead rows.
For example, in Sample Basic, the following filter definition has overlap conflicts:
Access: MetaRead. Member specification: California.
Access: MetaRead. Member specification: West.
In the first row, applying MetaRead to California has the effect of allowing access to California but blocking access to its ancestors. Therefore, the MetaRead access to West is ignored; users who are assigned this filter will have no access to West.
If you wish to assign MetaRead access to West, as well as California, the appropriate method is to combine them into one row: Access: MetaRead. Member specification: California, West.
When the access rights of user and group definitions overlap, the following rules, listed in order of precedence, apply:
User Fred is defined with the following database access:
FINPLAN R CAPPLAN W PRODPLAN N
He is assigned to Group Marketing, which has the following database access:
FINPLAN N CAPPLAN N PRODPLAN W
His effective rights are set as:
FINPLAN R CAPPLAN W PRODPLAN W
User Mary is defined with the following database access:
FINPLAN R PRODPLAN N
She is assigned to Group Marketing, which has the following database access:
FINPLAN N PRODPLAN W
Her effective rights are set as:
FINPLAN R PRODPLAN W
In addition, Mary uses the filter artifact RED (for the database FINPLAN). The filter has two filter rows:
Access: Read. Member specification: Actual.
Access: Write. Member specification: Budget, @IDESCENDANTS(“New York”).
The Group Marketing also uses a filter artifact BLUE (for the database FINPLAN). The filter has two filter rows:
Access: Read. Member specification: Actual, Sales.
Access: Write. Member specification: Budget, Sales.
Mary’s effective rights from the overlapping filters, and the permissions assigned to her and her group:
R: Entire FINPLAN database.
W: For all Budget data in the New York branch.
W: For data values that relate to Budget and Sales.