Cryptographic Optimizations in SPARC T-4 Systems
Beginning with the SPARC T4 microprocessor, new instructions to perform cryptography functions have become available directly in hardware. The instructions are non-privileged. Thus, any program can use the instructions without requiring any kernel environment, root permissions, or other special setup. Cryptography is performed directly on the hardware instead of using numerous low-level instructions. Cryptographic operations are therefore faster compared to operations on systems whose previous SPARC processors had separate processing units for cryptography.
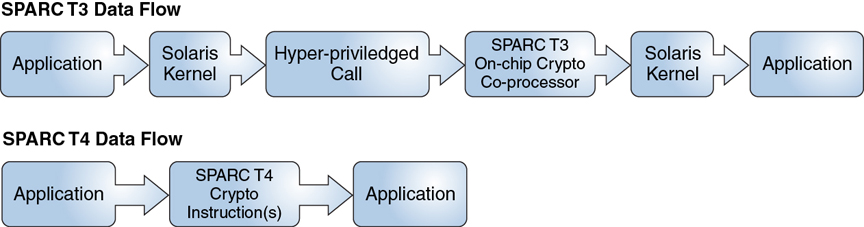
The following comparison shows the differences in the data flow between SPARC T-3 systems and SPARC T-4 systems with cryptographic optimizations.
Figure 2-1 Data Flow Comparison Between SPARC T-Systems
The following table provides a detailed comparison of cryptographic functions in SPARC T microprocessor units combined with specific Oracle Solaris releases.
|
-
aes_kexpand0, aes_kexpand1, aes_kexpand2
These instructions perform key expansion. They expand the 128-bit, 192-bit, or 256-bit user-provided key into a key schedule that is used internally during encryption and decryption. The aes_kexpand2 instruction is used only for AES-256. The other two aes_kexpand instructions are used for all three key lengths: AES-128, AES-192, and AES-256.
-
aes_eround01, aes_eround23, aes_eround01_l, aes_eround_23_l
These instructions are used for AES encryption rounds or transformations. According to the AES standard in FIPS 197, the number of rounds used (for example 10, 12, or 14) varies according to AES key length because using larger keys presumably indicates a desire for more robust encryption at the cost of more computation.
-
aes_dround01, aes_dround23, aes_dround01_l, aes_dround_23_l
These instructions are used for AES decryption rounds in a similar way as with encryption.
-
Instructions for DES/DES-3, Kasumi, Camellia, Montgomery multiply/square root (for RSA Bignum), and CRC32c checksums
-
MD5, SHA1, and SHA2 digest instructions
The T4 crypto instructions include the following:
The SPARC T4 hardware cryptographic instructions are available and used automatically on SPARC T4 systems running Oracle Solaris 11 by means of the built-in t4 engine on the system's T4 microprocessor. Beginning with Oracle Solaris 11.2, those instructions are now embedded in the OpenSSL upstream code. Thus, in this release, OpenSSL 1.0.1e is delivered with a patch to enable it to use those instructions.
-
"Exciting Crypto Advances with the T4 processor and Oracle Solaris 11"
For more information about the T4 instructions, refer to the following articles.
Determining Whether the System Supports SPARC T4 Optimizations
To determine whether the T4 optimizations are being used, use the isainfo command. The inclusion of sparcv9 and aes in the output indicates that the system is using the optimizations.
$ isainfo -v
64-bit sparcv9 applications
crc32c cbcond pause mont mpmul sha512 sha256 sha1 md5 camellia kasumi
des aes ima hpc vis3 fmaf asi_blk_init vis2 vis popc
Determining Your System's OpenSSL Version
To check the version of OpenSSL that is running on your system, type openssl version. The output is similar to the following:
OpenSSL 1.0.0j 10 May 2012
Verifying That Your System Has OpenSSL with SPARC T4 Optimizations
To determine whether your system supports OpenSSL with SPARC T4 optimizations, check the libcrypto.so library as follows:
# nm /lib/libcrypto.so.1.0.0 | grep des_t4 [5239] | 504192| 300|FUNC |GLOB |3 |12 |des_t4_cbc_decrypt [5653] | 503872| 300|FUNC |GLOB |3 |12 |des_t4_cbc_encrypt [4384] | 505024| 508|FUNC |GLOB |3 |12 |des_t4_ede3_cbc_decrypt [2963] | 504512| 508|FUNC |GLOB |3 |12 |des_t4_ede3_cbc_encrypt [4111] | 503712| 156|FUNC |GLOB |3 |12 |des_t4_key_expand
If the command does not generate any output, then your system does not support the SPARC T4 optimizations for OpenSSL.