| Oracle® Fusion Middleware Enterprise Deployment Guide for Oracle WebCenter Content 11g Release 1 (11.1.1) Part Number E15483-07 |
|
|
PDF · Mobi · ePub |
| Oracle® Fusion Middleware Enterprise Deployment Guide for Oracle WebCenter Content 11g Release 1 (11.1.1) Part Number E15483-07 |
|
|
PDF · Mobi · ePub |
This chapter describes how to integrate Oracle WebCenter Content with Oracle Identity Management. It contains the following sections:
Section 15.1, "Overview of Integrating with Oracle Identity Management"
Section 15.5, "Validating Access Through Oracle HTTP Server and SSO"
You can integrate an Oracle Fusion Middleware enterprise deployment with Oracle Identity Manager 10g or 11g. The following sections describe how to first configure credential and policy stores, reassociate those credential and policy stores, and then integrate with Oracle Identity Manager 10g or 11g.
Table 15-1 lists the high-level steps for integrating Oracle Identity Manager 10g with an Oracle WebCenter Content enterprise deployment.
Table 15-2 lists the high-level steps for integrating Oracle Identity Manager 11g with an Oracle WebCenter Content enterprise deployment.
Note:
When integrating with Oracle Identity Management, use the transport mode currently in use by the Oracle Identity Management servers. For example, Open, Simple or Cert.
Table 15-1 Steps for Integrating with Oracle Identity Manager 10g
| Step | Description | More Information |
|---|---|---|
|
Configure the credential store |
Configure the Oracle Internet Directory LDAP as a credential store for the Oracle WebCenter Content enterprise deployment topology. |
|
|
Configure the policy store |
Configure the Oracle Internet Directory LDAP as the policy store for the Oracle WebCenter Content enterprise deployment topology. |
|
|
Run the OAM Configuration Tool |
The OAM Configuration Tool (oamcfg) starts a series of scripts and sets up the required policies. |
|
|
Install and configure WebGate |
Install WebGate on each of the WEBHOSTn machines to secure the Web tier. |
|
|
Configure IP validation for the Webgate |
Configure the IP validation for the Webgate using Access System Console. |
Section 15.3.5, "Configuring IP Validation for the EDG Webgate" |
|
Set Up WebLogic Authenticators |
Set up the WebLogic authenticators by backing up the configuration files, setting up the Oracle Access Manager ID Asserter, and setting the order of providers. |
Table 15-2 Steps for Integrating with Oracle Identity Manager 11g
| Step | Description | More Information |
|---|---|---|
|
Configure the credential store |
Configure the Oracle Internet Directory LDAP as a credential store for the Oracle WebCenter Content Enterprise Deployment topology. |
|
|
Configure the policy store |
Configure the Oracle Internet Directory LDAP as the policy store for the Oracle WebCenter Content Enterprise Deployment topology. |
|
|
Install WebGate |
Install WebGate on each of the WEBHOST machines where an HTTP Server has already been installed. |
|
|
Register the WebGate agent |
Register the Webgate agent using the RREG tool. |
|
|
Set Up WebLogic Authenticators |
Set up the WebLogic authenticators by backing up the configuration files, setting up the Oracle Access Manager ID Asserter, and setting the order of providers. |
The following topics describe credential and policy store configuration in detail:
Oracle Fusion Middleware allows using different types of credential and policy stores in a WebLogic domain. Domains can use stores based on an XML file or on different types of LDAP providers. When a domain uses an LDAP store, all policy and credential data is kept and maintained in a centralized store. However, when using XML policy stores, the changes made on managed servers are not propagated to the Administration Server unless they use the same domain home. The enterprise deployment topology for Oracle WebCenter Content uses different domain homes for the Administration Server and the managed servers, which means that Oracle requires the use of an LDAP store as policy and credential store for integrity and consistency. By default, Oracle WebLogic Server domains use an XML file for the policy store. The following sections describe the steps required to change the default store to Oracle Internet Directory LDAP for credentials or policies.
Note:
The backend repository for the policy store and the credential store must use the same kind of LDAP server. To preserve this coherence, note that reassociating one store implies reassociating the other one, that is, the reassociation of both the credential and the policy stores is accomplished as a unit using the Fusion Middleware Control or the WLST command reassociateSecurityStore. For more information, see Section 15.2.4, "Reassociation of Credentials and Policies."
A credential store is a repository of security data (credentials). A credential can hold user name and password combinations, tickets, or public key certificates. Credentials are used during authentication, when principals are populated in subjects, and, further, during authorization, when determining what actions the subject can perform. This section provides steps to configure Oracle Internet Directory LDAP as a credential store for the Oracle WebCenter Content enterprise deployment topology. For more details on credential store configuration, see the "Configuring the Credential Store" chapter in the Oracle Fusion Middleware Security Guide.
The following section describe credential store configuration:
Section 15.2.2.2, "Moving the WebLogic Administrator to LDAP"
Section 15.2.2.3, "Reassociating the Domain Credential Store"
To be safe, before you create the LDAP authenticator, you should first back up the relevant configuration files:
ORACLE_BASE/admin/domain_name/aserver/domain_name/config/config.xml ORACLE_BASE/admin/domain_name/aserver/domain_name/config/fmwconfig/jps-config.xml ORACLE_BASE/admin/domain_name/aserver/domain_name/config/fmwconfig/system-jazn-data.xml
Also back up the boot properties file for the Administration Server:
ORACLE_BASE/admin/domain_name/aserver/domain_name/servers/AdminServer/security/boot.properties
Follow these steps to set the proper authenticator:
Log in to the WebLogic Server Administration Console.
Click the Security Realms link on the left navigational bar.
Click the myrealm default realm entry to configure it.
Open the Providers tab within the realm.
Observe that there is a DefaultAuthenticator provider configured for the realm.
Click Lock & Edit.
Click the New button to add a new provider.
Enter a name for the provider such as OIDAuthenticator or OVDAuthenticator depending on whether Oracle Internet Directory or Oracle Virtual Directory will be used.
Select the OracleInternetDirectoryAuthenticator or OracleVirtualDirectoryAuthenticator type from the list of authenticators depending on whether Oracle Internet Directory or Oracle Virtual Directory will be used.
Click OK.
In the Providers screen, click the newly created Authenticator.
Set the control flag to SUFFICIENT. This indicates that if a user can be authenticated successfully by this authenticator, then it should accept that authentication and should not continue to invoke any additional authenticators. If the authentication fails, it will fall through to the next authenticator in the chain. Make sure all subsequent authenticators also have their control flag set to SUFFICIENT; in particular, check the DefaultAuthenticator and set that to SUFFICIENT.
Click Save to save this setting.
Open the Provider Specific tab to enter the details for the LDAP server.
Enter the details specific to your LDAP server, as shown in the following table.
| Parameter | Value | Value Description |
|---|---|---|
|
Host |
For example: |
The LDAP server's server ID. |
|
Port |
For example: |
The LDAP server's port number. |
|
Principal |
For example: |
The LDAP user DN used to connect to the LDAP server. |
|
Credential |
NA |
The password used to connect to the LDAP server. |
|
SSL Enabled |
Checked |
Specifies whether SSL protocol is used when connecting to LDAP server. |
|
User Base DN |
For example: |
Specify the DN under which your Users start. |
|
Group Base DN |
For example: |
Specify the DN that points to your Groups node. |
|
Use Retrieved User Name as Principal |
Checked |
Must be turned on. |
Click Save when done.
Click Activate Changes to propagate the changes.
Reorder the OID/OVD Authenticator and Default Authenticator and ensure that the control flag for each authenticator is set in the following order:
OID LDAP Authenticator: SUFFICIENT
Default Authenticator: SUFFICIENT
To set the order of providers:
Log in to the WebLogic Server Administration Console, if not already logged in.
Click Lock & Edit.
Navigate to SecurityRealms, then the default realm name, and then Providers.
Reorder the OID/OVD Authenticator, and Default Authenticator by ensuring that the control flag for each authenticator is set as follows:
OID LDAP Authenticator (or OVD LDAP Authenticator): SUFFICIENT
Default Authenticator: SUFFICIENT
Click OK.
Click Activate Changes to propagate the changes.
Restart the Administration Server and all managed servers.
This section provides details for provisioning a new administrator user and group for managing Oracle WebCenter Content's WebLogic domain in the enterprise deployment topology. This section describes the following tasks:
Section 15.2.2.2.1, "Provisioning Admin Users and Groups in an LDAP Directory"
Section 15.2.2.2.2, "Assigning the Admin Role to the Admin Group"
Section 15.2.2.2.3, "Updating the boot.properties File and Restarting the System"
As mentioned in the introduction to this section, users and groups from multiple WebLogic Server domains may be provisioned in a central LDAP user store. In such a case, there is a possibility that one WebLogic Server administration user may have access to all the domains within an enterprise. This is not a desirable situation. To avoid this, the users and groups provisioned must have a unique, distinguished name within the directory tree. In this guide, the administration user and group for the WebCenter Content WebLogic Server domain will be provisioned with the following DNs:
Admin User DN:
cn=weblogic_ecm,cn=Users,dc=us,dc=mycompany,dc=com
Admin Group DN:
cn=ECM Administrators,cn=Groups,dc=us,dc=mycompany,dc=com
Follow these steps to provision the admin user and admin group in Oracle Internet Directory:
Create an LDIF file named admin_user.ldif with the contents shown below depending on the Oracle Access Manager version used, and then save the file:
Oracle Access Manager 10g:
dn: cn=weblogic_ecm, cn=Users, dc=us, dc=mycompany, dc=com orclsamaccountname: weblogic_ecm givenname: weblogic_ecm sn: weblogic_ecm userpassword: Welcome1 obver: 10.1.4.0 mail: weblogic_ecm objectclass: top objectclass: person objectclass: organizationalPerson objectclass: inetorgperson objectclass: orcluser objectclass: orcluserV2 objectclass: oblixorgperson uid: weblogic_ecm cn: weblogic_ecm description: Admin User for the Oracle WebCenter Content Domain
Oracle Access Manager 11g:
dn: cn=weblogic_ecm, cn=Users, dc=us, dc=mycompany, dc=com orclsamaccountname: weblogic_ecm givenname: weblogic_ecm sn: weblogic_ecm userpassword: Welcome1 obver: 10.1.4.0 mail: weblogic_ecm objectclass: top objectclass: person objectclass: organizationalPerson objectclass: inetorgperson objectclass: orcluser objectclass: orcluserV2 uid: weblogic_ecm cn: weblogic_ecm description: Admin User for the Oracle WebCenter Content Domain
Run the ldapadd command on the Oracle Internet Directory host located under the ORACLE_HOME/bin directory to provision the user in Oracle Internet Directory.
Note:
The ORACLE_HOME used here is the ORACLE_HOME for the Identity Management installation where Oracle Internet Directory resides.
For example:
ORACLE_HOME/bin/ldapadd -h oid.mycompany.com -p 389 -D cn="orcladmin" -w welcome1 -c -v -f admin_user.ldif
Create an ldif file named admin_group.ldif with the contents shown below and then save the file:
dn: cn=ECM Administrators, cn=Groups, dc=us, dc=mycompany, dc=com displayname: ECM Administrators objectclass: top objectclass: groupOfUniqueNames objectclass: orclGroup uniquemember: cn=weblogic_ecm, cn=users, dc=us, dc=mycompany, dc=com cn: ECM Administrators description: Administrators Group for the Oracle WebCenter Content Domain
Run the ldapadd command on the Oracle Internet Directory host located under the ORACLE_HOME/bin directory to provision the group in Oracle Internet Directory:
ORACLE_HOME/bin/ldapadd -h oid.mycompany.com -p 389 -D cn="orcladmin" -w welcome1 -c -v -f admin_group.ldif
After adding the users and groups to Oracle Internet Directory, the group must be assigned the Admin role within the WebLogic domain security realm. This enables all users that belong to the group to be administrators for that domain. Follow these steps to assign the Admin role to the Admin group:
Log in to the WebLogic Administration Server Console.
In the left pane of the console, click Security Realms.
On the Summary of Security Realms page, click myrealm under the Realms table.
On the Settings page for myrealm, open the Roles & Policies tab.
On the Realm Roles page, expand the Global Roles entry under the Roles table. This brings up the entry for Roles. Click the Roles link to bring up the Global Roles page.
On the Global Roles page, click the Admin role to bring up the Edit Global Role page:
On the Edit Global Roles page, under the Role Conditions table, click the Add Conditions button.
On the Choose a Predicate page, select Group from the drop down list for predicates and click Next.
On the Edit Arguments Page, specify ECM Administrators in the Group Argument field and click Add.
Click Finish to return to the Edit Global Rule page.
The Role Conditions table now shows the ECM Administrators Group as an entry.
Click Save to finish adding the Admin Role to the ECM Administrators Group.
Validate that the changes were successful by bringing up the WebLogic Administration Server Console using a web browser. Log in using the credentials for the weblogic_ecm user.
Note:
Each Oracle application in the Oracle WebCenter Content enterprise deployment topology may have its own predefined roles and groups defined for administration and monitoring purposes. By default, the Administrators group will allow these operations. However, this group may be too broad. For example, it may be undesirable that SOA administrators are also administrators for the Oracle WebLogic Server domain where Oracle SOA, Oracle WebCenter Content, and Oracle WebCenter Content: Imaging are running. This is why it may be desirable, as suggested in this section, to create a more specific group such as ECM Administrators. In order for the various applications to allow the ECM Administrators group to administer the different systems, you need to add the required roles to that group. For example, for SOA Worklistapp's administration, add the SOAAdmin role. Refer to each component's specific roles for the required roles in each case.
The boot.properties file for the Administration Server should be updated with the WebLogic admin user created in Oracle Internet Directory. Follow the steps below to update the boot.properties file:
On SOAHOST1, go the following directory:
cd ORACLE_BASE/admin/domain_name/aserver/domain_name/servers/AdminServer/security
Rename the existing boot.properties file:
mv boot.properties boot.properties.backup
Use a text editor to create a file called boot.properties under the security directory. Enter the following lines in the file:
username=weblogic_ecm password=welcome1
Save the file.
Stop the Administration Server using the following command:
wls:/nm/domain_name>nmKill("AdminServer")
Start the Administrator Server using the procedure in Section 8.4.4, "Starting the Administration Server on SOAHOST1."
The reassociation of both the credential and the policy stores is accomplished as a unit using Fusion Middleware Control or the WLST command reassociateSecurityStore. See Section 15.2.4, "Reassociation of Credentials and Policies" for detailed steps.
The domain policy store is the repository of system and application-specific policies. In a given domain, there is one store that stores all policies that all applications deployed in the domain may use. This section provides the steps to configure Oracle Internet Directory LDAP as the policy store for the Oracle WebCenter Content enterprise deployment topology. For more details on policy store configuration, refer to the "OPSS Authorization and the Policy Store" chapter in the Oracle Fusion Middleware Security Guide.
In order to ensure the proper access to an LDAP server directory (Oracle Internet Directory) used as a policy store, you must set a node in the server directory.
An Oracle Internet Directory administrator must follow these steps to create the appropriate node in an Oracle Internet Directory Server:
Create an LDIF file (assumed to be jpstestnode.ldif in this example) specifying the following DN and CN entries:
dn: cn=jpsroot_ecm cn: jpsroot_ecm objectclass: top objectclass: OrclContainer
The distinguished name of the root node (illustrated by the string jpsroot_ecm above) must be distinct from any other distinguished name. One root node can be shared by multiple WebLogic Server domains. It is not required that this node be created at the top level, as long as read and write access to the subtree is granted to the Oracle Internet Directory administrator.
Import this data into Oracle Internet Directory server using the ldapadd command on the OID server, as illustrated in the following example:
ORACLE_HOME/bin/ldapadd -h ldap_host -p ldap_port -D cn=orcladmin -w password -c -v -f jpstestnode.ldif
Verify that the node has been successfully inserted using the ldapsearch command on the Oracle Internet Directory server, as illustrated in the following example:
ORACLE_HOME/bin/ldapsearch -h ldap_host -p ldap_port -D cn=orcladmin -w password -b "cn=jpsroot_ecm" objectclass="orclContainer"
When using Oracle Internet Directory as the LDAP-based policy store, run the oidstats.sql utility in the INFRADBHOST servers to generate database statistics for optimal database performance:
ORACLE_HOME/bin/sqlplus
Enter ODS as a user name. You will be prompted for credentials for the ODS user. Inside SQL*Plus, enter the command to gather the statistics info:
@ORACLE_HOME/ldap/admin/oidstats.sql
The oidstats.sql utility must be run just once after the initial provisioning. For details about this utility, consult the Oracle Fusion Middleware User Reference for Oracle Identity Management.
Reassociating the policy store consists in migrating policy data from a file-based or LDAP-based repository to an LDAP-based repository; that is, reassociation changes the repository preserving the integrity of the data stored. For each policy in the source policy store, reassociation searches the target LDAP directory and, if it finds a match, it updates the matching policy as appropriate. If none is found, it simply migrates the policy as is.
At any time, after a domain policy store has been instantiated, a file-based or LDAP-based policy store can be reassociated into an LDAP-based policy store storing the same data. To support it, the domain has to be configured, as appropriate, to use an LDAP policy store.
The reassociation of both the credential and the policy stores is accomplished as a unit using Oracle Enterprise Manager Fusion Middleware Control or the WLST reassociateSecurityStore command. See Section 15.2.4, "Reassociation of Credentials and Policies" for detailed steps.
To reassociate the policy and credential store with Oracle Internet Directory, use the WLST reassociateSecurityStore command. Follow these steps:
From SOAHOST1, start the wlst shell:
cd ORACLE_COMMON_HOME/common/bin
./wlst.sh
Connect to the WebLogic Administration Server using the wlst connect command shown below:
Syntax:
connect("Admin_User","Admin_User_Password","t3://hostname:port")
For example:
connect("weblogic","welcome1","t3://ADMINVHN:7001")
Run the reassociateSecurityStore command as shown below:
Syntax:
reassociateSecurityStore(domain="domain_name",admin="cn=orcladmin", password="orclPassword",ldapurl="ldap://LDAP_HOST:LDAP_PORT",servertype="OID", jpsroot="cn=jpsroot_ecm")
For example:
wls:/domain_name/serverConfig>reassociateSecurityStore(domain="domain_name", admin="cn=orcladmin",password="welcome1",ldapurl="ldap://oid.mycompany.com:389",servertype="OID",jpsroot="cn=jpsroot_ecm")
The output for the command is shown below:
{servertype=OID,jpsroot_ecm=cn=jpsroot_ecm_idm_idmhost1,admin=cn=orcladmin,
domain=IDMDomain,ldapurl=ldap://oid.mycompany.com:389,password=welcome1}
Location changed to domainRuntime tree. This is a read-only tree with DomainMBean as the root.
For more help, use help(domainRuntime)
Starting Policy Store reassociation.
LDAP server and ServiceConfigurator setup done.
Schema is seeded into LDAP server
Data is migrated to LDAP server
Service in the server after migration has been tested to be available
Update of jps configuration is done
Policy Store reassociation done.
Starting credential Store reassociation
LDAP server and ServiceConfigurator setup done.
Schema is seeded into LDAP server
Data is migrated to LDAP server
Service in LDAP server after migration has been tested to be available
Update of jps configuration is done
Credential Store reassociation done
Starting keystore reassociation
The server and ServiceConfigurator setup done.
Schema is seeded into the server
Data is migrated to the server
Service in the server after migration has been tested to be available
Update of jps configuration is done
keystore reassociation done
Jps Configuration has been changed. Please restart the server.
Restart the Administration Server after the command completes successfully.
To restart the Administration Server, use the procedure in Section 8.4.4, "Starting the Administration Server on SOAHOST1."
Note:
For credential and policy changes to take effect, the servers in the domain must be restarted.
An Oracle Internet Directory attribute used in a search filter must be indexed. The indexing is an optional procedure used to enhance performance. If not done yet in this OID, use the catalog tool to index attributes:
catalog connect="orcl" add=true attribute="orclrolescope" verbose="true"
Optionally, the attribute names can be placed in a file and processed in a batch as follows:
orclrolescope orclassignedroles orclApplicationCommonName orclAppFullName orclCSFAlias orclCSFKey orclCSFName orclCSFDBUrl orclCSFDBPort orclCSFCredentialType orclCSFExpiryTime modifytimestamp createtimestamp orcljpsassignee
For more information on indexing OID attributes, see the Oracle Fusion Middleware Reference for Oracle Identity Management.
This section describes how to set up Oracle Access Manager 10g as the single sign-on solution for the Oracle WebCenter Content enterprise deployment topology. It contains the following sections:
Section 15.3.1, "Overview of Oracle Access Manager Integration"
Section 15.3.5, "Configuring IP Validation for the EDG Webgate"
Oracle Access Manager is the recommended single sign-on (SSO) solution for Oracle Fusion Middleware 11g Release 1. For more information on installing and configuring an Oracle Access Manager installation, see Oracle Fusion Middleware Enterprise Deployment Guide for Oracle Identity Management. This section explains the procedure for configuring the Oracle WebCenter Content installation with an existing Oracle Access Manager 10g installation and the underlying directory service. Oracle recommends using either Oracle Internet Directory or Oracle Virtual Directory or both of these directory services.
Note:
The Oracle WebCenter Content enterprise deployment topology described in this book uses a single sign-on configuration where both the Oracle WebCenter Content system and the single sign-on system are in the same network domain (mycompany.com). For a multidomain configuration, see the required configuration steps in "Configuring Single Sign-On" in the Oracle Access Manager Access Administration Guide.
The setup for Oracle Access Manager assumes an existing Oracle Access Manager 10g installation complete with Access Managers and a policy protecting the Policy Manager. For more information on installing and configuring an Oracle Access Manager installation, see Oracle Fusion Middleware Enterprise Deployment Guide for Oracle Identity Management. This setup includes a directory service such as Oracle Internet Directory, either stand-alone or as part of an Oracle Virtual Directory configuration. This section provides the necessary steps for configuring your enterprise deployment with either Oracle Internet Directory or Oracle Virtual Directory.
In addition, the Oracle Access Manager installation should have its own Web server configured with WebGate. This section also provides the steps for using the Oracle Access Manager Web server as a delegated authentication server.
This section covers the following topics:
Section 15.3.3.1, "Collecting the Information for the OAM Configuration Tool"
Section 15.3.3.4, "Verifying Successful Creation of the Policy Domain and AccessGate"
Section 15.3.3.9, "Configuring Delegated Form Authentication"
The OAM Configuration Tool (oamcfg) starts a series of scripts and sets up the required policies for Oracle Access Manager. It requires various parameters as inputs. Specifically, it creates the following:
A form authentication scheme in Oracle Access Manager
Policies to enable authentication in Oracle WebLogic Server
A WebGate entry in Oracle Access Manager to enable Oracle HTTP Server WebGates (from your Web Tier) to protect your configured application
A host identifier, depending on the scenario chosen (a default host identifier would be used, if not provided)
A host identifier, depending on the scenario chosen (a default host identifier would be used, if not provided)
Policies to protect and unprotect application specific URLs.
The following information should be collected or prepared prior to running the OAM Configuration Tool:
Password: Create a secure password. This will be used as the password for the WebGate installation created later.
LDAP Host: host name of the directory server or load balancer address in the case of a high-availability or enterprise deployment configuration.
LDAP Port: port of the directory server.
LDAP USER DN: DN of the LDAP admin user. This will be a value such as cn=orcladmin.
LDAP password: password of the LDAP admin user.
oam_aaa_host: host name of an Oracle Access Manager.
oam_aaa_port: port of the Oracle Access Manager.
Before running the OAM Configuration Tool, you must first add the required resources to Oracle Access Manager 10g for the Oracle WebCenter Content components. Create a file containing the list of URIs you want to protect with the following content:
######################################### #Product Name: Oracle WebCenter Content ######################################### ######################################### protected_uris ######################################### /adfAuthentication /imaging/faces /em /console /DefaultToDoTaskFlow /sdpmessaging/userprefs-ui /integration/worklistapp /workflow/sdpmessagingsca-ui-worklist /soa/composer /soa-infra/deployer /soa-infra/events/edn-db-log /soa-infra/cluster/info #"Policy using Basic Authn Scheme" is the name of the policy #"Basic Over LDAP" is the authentication scheme configured for this #policy # Note that the name of the policy and the scheme name in the URIs file # is tab-separated. In other words, there must be a tab between # "Basic Authn Scheme" and "OraDefaultBasicAuthNScheme" below. Policy using Basic Authn Scheme OraDefaultBasicAuthNScheme /inspection.wsil ######################################### public_uris ######################################### /soa-infra/services /soa-infra/directWSDL
Note:
In Oracle Access Manager 10g, all resources under a URL prefix are protected by the default rules of a policy domain unless more specific rules are applied to them through policies. Refer to the Oracle Access Manager Access Administration Guide for details on the different patterns that can be used if more specialized protection patterns need to be used.
The OAM Configuration Tool resides in the ORACLE_COMMON_HOME/modules/oracle.oamprovider_11.1.1 directory (ORACLE_COMMON_HOME depends on the machine where you are running the configuration tool). The tool can be run from any machine with the required installation files. In this case, we run it from WCCHOST1. Run the OAM Configuration Tool for Oracle Access Manager 10g registration as follows (all on a single command line):
MW_HOME/jrockit_160_version/bin/java -jar oamcfgtool.jar mode=CREATE app_domain="ECM_EDG" uris_file="full_path_to_file_containing_uri_definitions" app_agent_password=password_to_be_provisioned_for_App_Agent ldap_host=OID.MYCOMPANY.COM ldap_port=389 ldap_userdn="cn=orcladmin" ldap_userpassword=Password_of_LDAP_admin_user oam_aaa_host=OAMHOST1 oam_aaa_port=OAMPORT1
If your command ran successfully, you should see the following output:
Date,Time oracle.security.oam.oamcfg.OAMCfgGlobalConfigHandler constructGlobalConfig INFO: Processed input parameters May 9, 2011 5:09:40 AM oracle.security.oam.oamcfg.OAMCfgGlobalConfigHandler constructGlobalConfig INFO: Initialized Global Configuration Date,Time oracle.security.oam.oamcfg.create.impl.OAMCfgConfigCreator doCreate INFO: Successfully completed the Create operation. Date,Time oracle.security.oam.oamcfg.create.impl.OAMCfgConfigCreator doCreate INFO: Operation Summary: Date,Time oracle.security.oam.oamcfg.create.impl.OAMCfgConfigCreator doCreate INFO: Policy Domain : ECM_EDG Date,Time oracle.security.oam.oamcfg.create.impl.OAMCfgConfigCreator doCreate INFO: Host Identifier: ECM_EDG Date,Time oracle.security.oam.oamcfg.create.impl.OAMCfgConfigCreator doCreate INFO: Access Gate ID : ECM_EDG_AG
For applications invoked by Oracle WebCenter Content and Oracle WebCenter Content: Imaging to comply with Oracle Access Manager logout guidelines (in particular, applications that invoke a logout through /adfAuthentication?logout=true&end_url=some_URI), integration with an Oracle Access Manager 10g environment requires additional configuration on the WebGate to handle the end_url. Without this additional configuration, you are logged out, but not redirected to the end URL because Oracle Access Manager 10g WebGate does not process end_url. For information about configuration procedures, see Oracle Fusion Middleware Security Guide.
When integrating Oracle WebCenter Content with Oracle Access Manager 10g, you must add the URL /oamsso/logout.html to the logout URL setting for the Access Gate for the single sign-on logout to work properly. See "Configuring a Single Sign-On Logout URL" and "AccessGate Configuration Parameters" in the Oracle Access Manager Access Administration Guide for more information.
Verifying the Policy Domain
To verify the policy domain:
Log in to Oracle Access Manager:
http://OAMADMINHOST:port/access/oblix/
Click Policy Manager.
Click the My Policy Domains link on the left panel. You will see a list of all policy domains, which includes the domain you just created. It will have the suffix _PD (for example, ECM_EDG_PD). In the third column (URL prefixes), you will also see the URIs you specified during the creation of this domain).
Click the link to the policy domain you just created to go to the General area of this domain.
Open the Resources tab and you will see the URIs you specified. You can also click other tabs to view other settings.
Verifying the AccessGate Configuration
To verify the AccessGate configuration:
Click the Access System Console link on the top right-hand side (this acts like a toggle; after you click it, it becomes the Policy Manager link).
Open the Access System Configuration tab.
Click the AccessGate Configuration link on the left panel.
Enter ECM_EDG as the search criterion (or any other substring you may have used as the app_domain name in Section 15.3.3.2, "Running the OAM Configuration Tool"), and click Go.
Once the access gate for the domain you just created shows up (this will have the suffix _AG (for example, ECM_EDG_AG), click it, and you will see the details of the access gate you just created.
To verify that the cookieless basic authorization scheme has been properly assigned:
Log in to Oracle Access Manager:
http://OAMADMINHOST:port/access/oblix/
Click Policy Manager.
Click the My Policy Domains link on the left panel. You will see a list of all policy domains that have been created.
Click ECM_EDG.
Open the Policies tab and then click Policy using Basic Authn Scheme.
Open the General section.
The inspection.wsil resource should be listed.
Open the Authentication Rule section.
The OraDefaultBasicAuthNScheme authentication scheme should be listed.
The OAM Configuration Tool uses the value of the app_domain parameter to create a host identifier for the policy domain. This host identifier must be updated with all the host name variations for the host so that the configuration works correctly.
To update the host identifier created by the OAM Configuration Tool:
Navigate to the Access System Console by specifying the following URL in your web browser:
http://host_name:port/access/oblix
where host_name refers to the host where the WebPass Oracle HTTP Server instance is running and port refers to the HTTP port of the Oracle HTTP Server instance.
When prompted for a user name and password, log in as an administrator. Click OK.
On the Access System main page, click the Access System Console link.
On the Access System Console page, open the Access System Configuration tab.
On the Access System Configuration page, click Host Identifiers at the bottom left.
On the List all host identifiers page, click the host identifier created by the OAM Configuration Tool (for example, ECM_EDG).
On the Host Identifier Details page, click Modify.
Add the Preferred HTTP Host value used in the Access System Configuration. The following is a list of all the possible host name variations using SSO/ WebGate:
webhost1.mydomain.com:7777 webhost2.mydomain.com:7777 soahost1vhn1.mycompany.com:8001 soahost2vhn1.mycompany.com:8001 soainternal.mycompany.com:80 wcchost1vhn1.mycompany.com:16000 wcchost2vhn1.mycompany.com:16000 wcchost1.mycompany.com:16200 wcchost2.mycompany.com:16200 wcc.mycompany.com:443 wccinternal.mycompany.com:80 admin.mycompany.com:80 adminvhn.mycompany.com:7001 sso.mycompany.com:7779 [WebGate access with Oracle IDM port]
Select the Update Cache checkbox, and then click Save.
A message box with the following message is displayed: Updating the cache at this point will flush all the caches in the system. Are you sure?
Click OK to finish saving the configuration changes.
Verify the changes on the Host Identifier Details page.
The OAM Configuration Tool populates the Preferred_HTTP_Host and hostname attributes for the WebGate profile that is created with the value of the app_domain parameter. Both these attributes must be updated with the proper values for the configuration to work correctly.
To update the WebGate profile created by the OAM Configuration Tool:
Navigate to the Access System Console by specifying the following URL in your web browser:
http://host_name:port/access/oblix
where host_name refers to the host where the WebPass Oracle HTTP Server instance is running and port refers to the HTTP port of the Oracle HTTP Server instance.
On the Access System main page, click the Access System Console link, then log in as an administrator.
On the Access System Console main page, click Access System Configuration, and then click the Access Gate Configuration Link in the left pane to display the AccessGates Search page.
Enter the proper search criteria and click Go to display a list of access gates.
Select the access gate created by the OAM Configuration Tool (for example, ECM_EDG_AG).
On the AccessGate Details page, select Modify to display the Modify AccessGate page.
On the Modify AccessGate page, update the following:
Hostname: Update the hostname with the name of the computer where WebGate is running, for example: webhost1.mycompany.com.
Preferred HTTP Host: Update the Preferred_HTTP_Host with one of the hostname variations specified in the previous section, for example: admin.mycompany.com:80.
Primary HTTP Cookie Domain: Update the Primary HTTP Cookie Domain with the domain suffix of the host identifier, for example: mycompany.com
Click Save.
A message box with the following message is displayed: Are you sure you want to commit these changes?
Click OK to finish updating the configuration.
Verify the values displayed on the Details for AccessGate page to confirm that the updates were successful.
To assign an access server to the WebGate:
Log in as the Administrator on the Access System Console.
Navigate to the Details for AccessGate page, if necessary. From the Access System Console, select Access System Configuration, then AccessGate Configuration, then the link for the WebGate (ECM_EDG_AG).
On the Details for AccessGate page, click List Access Servers.
A page appears showing the primary or secondary Access Servers currently configured for this WebGate.
Click Add.
On the Add a New Access Server page, select an Access Server from the Select Server list, specify Primary Server, and define two connections for the WebGate.
Click the Add button to complete the association.
A page appears, showing the association of the Access Server with the WebGate. Click the link to display a summary and print this page for later use.
Repeat steps 3 through 6 to associate more access servers to the WebGate.
To configure the form authentication to redirect to the WebGate that was installed with the Oracle Access Manager installation:
Open the Access System Console.
In the Access System Configuration screen, select Authentication Management from the left-hand bar.
Select OraDefaultFormAuthNScheme.
Click Modify.
In the Challenge Redirect field, enter the host and port of the IDM installation; for example: http://sso.mycompany.com. Click Save when you are done.
A WebGate should already be installed in the IDM installation. Refer to Oracle Fusion Middleware Enterprise Deployment Guide for Oracle Identity Management for details.
WebGate needs to be installed on both WEBHOST1 and WEBHOST2 to secure the web tier:
Note:
There is a known issue with the Oracle Access Manager installer that sometimes manifests as a hang at install time on Linux. This is a third-party issue caused by InstallShield. To work around this issue, follow these steps:
Copy and paste the following in the shell where you start the installer:
cd /tmp mkdir bin.$$ cd bin.$$ cat > mount <<EOF #! /bin/sh exec /bin/true EOF chmod 755 mount export PATH=`pwd`:$PATH
Run the installation.
When the installer is finished running, clean the temporary directory using this command:
rm -r /tmp/bin.$$
Launch the WebGate installer (see Section 2.4, "Identifying the Software Components to Install" for information on where to obtain it) using the following command on WEBHOSTn:
./Oracle_Access_Manager10_1_4_3_0_linux_OHS11g_WebGate –gui
In the Welcome screen, click Next.
In the Customer Information screen (Figure 15-1), enter the user name and user group that the web server is running as. Click Next to continue.
In the installation target screen (Figure 15-2), specify the directory where WebGate should be installed. Click Next to continue.
In the installation summary screen, click Next.
Download the required GCC runtime libraries for WebGate as instructed in the WebGate configuration screen (Figure 15-3), and use Browse to point to their location on the local computer. Click Next to continue.
The installer now creates the required artifacts. After that is completed, click Next to continue.
In the transport security mode screen (Figure 15-4), select Open Mode: No Encryption and click Next to continue.
Figure 15-4 Transport Security Mode Screen

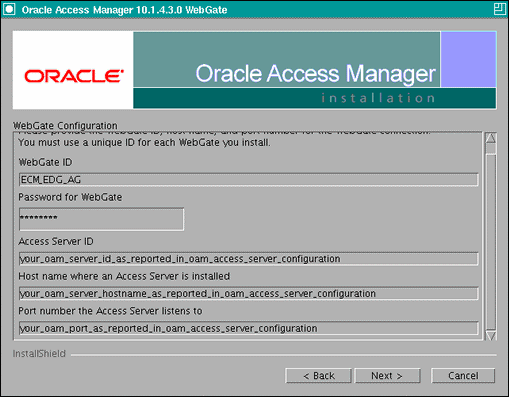
In the WebGate configuration screen, provide the details of the access server that will be used. You must provide the following information:
WebGate ID, as provided when the OAM Configuration Tool was executed
Password for WebGate
Access Server ID, as reported by the Oracle Access Manager Access Server configuration
Access Server host name, as reported by the Oracle Access Manager Access Server configuration
Access Server port number, as reported by the Oracle Access Manager Access Server configuration
Note:
The Access Server ID, host name, and port are all required.
You can obtain these details from your Oracle Access Manager administrator. Click Next to continue.
Figure 15-5 Access Server Configuration Screen
In the Configure Web Server screen, click Yes to automatically update the web server. Click Next to continue.
In the next Configure Web Server screen, specify the full path of the directory containing the httpd.conf file. This file is located in the following directory:
ORACLE_BASE/admin/OHS_Instance/config/OHS/OHS_Component_Name
For example:
/u01/app/oracle/admin/ohs_instance2/config/OHS/ohs2/httpd.conf
Click Next to continue.
In the next Configure Web Server page, a message informs you that the Web server configuration has been modified for WebGate. Click Yes to confirm.
Stop and start your Web server for the configuration updates to take effect. Click Next to continue.
In the next Configure Web Server screen, the following message is displayed: If the web server is set up in SSL mode, then the httpd.conf file needs to be configured with the SSL related parameters. To manually tune your SSL configuration, please follow the instructions that come up.
Click Next to continue.
In the next Configure Web Server screen, a message with the location of the document that has information on the rest of the product setup and Web server configuration is displayed. Choose No and click Next to continue.
The final Configure Web Server screen appears with a message to manually launch a browser and open the HTML document for further information on configuring your Web server. Click Next to continue.
The Oracle COREid Readme screen appears. Review the information on the screen and click Next to continue.
A message appears (along with the details of the installation) informing you that the installation was successful.
IP validation determines if a client's IP address is the same as the IP address stored in the ObSSOCookie cookie generated for single sign-on. IP validation can cause issues in systems using load balancer devices configured to perform IP termination or when the authenticating webgate is front-ended by a different load balancing router (LBR) or proxy than the one front-ending the enterprise deployment.
To make sure your enterprise deployment's LBR or proxy are not validated in these cases:
Open the Access System Console and log in as an administrator at the following URL:
http://host_name:port/access/oblix
where host_name refers to the host where the WebPass Oracle HTTP Server instance is running and port refers to the HTTP port of the Oracle HTTP Server instance.
On the Access System main page, click the Access System Console link.
On the Access System Console main page, click Access System Configuration, and then click the Access Gate Configuration link in the left pane to display the AccessGates Search page.
Enter the appropriate search criteria and click Go to display a list of access gates.
Select the access gate created by the OAM Configuration Tool.
Click Modify at the bottom of the page.
In the IPValidationException field, enter the IP address of the load balancer or proxy front-ending the enterprise deployment.
Click Save at the bottom of the page.
This section assumes that you have already set up the LDAP authenticator by following the steps in Section 15.2.2.1, "Creating the LDAP Authenticator." If you have not already created the LDAP authenticator, do it before continuing with this section.
This section covers the following topics:
To be safe, first back up the relevant configuration files:
ORACLE_BASE/admin/domain_name/aserver/domain_name/config/config.xml ORACLE_BASE/admin/domain_name/aserver/config/fmwconfig/jps-config.xml ORACLE_BASE/admin/domain_name/aserver/domain_name/config/fmwconfig/ system-jazn-data.xml
Also back up the boot.properties file for the Administration Server.
To set up the OAM ID Asserter:
Log in to Weblogic Console, if not already logged in.
Click Lock & Edit.
Navigate to SecurityRealms, then the default realm name, and then Providers.
Click New and select OAMIdentityAsserter from the dropdown menu.
Name the asserter (for example, OAM ID Asserter) and click OK.
Click the newly added asserter to see the configuration screen for OAM Identity Asserter.
Set the control flag to REQUIRED and click Save.
Open the Provider Specific tab to configure the following required settings:
Primary Access Server: provide Oracle Access Manager server endpoint information in host:port format.
AccessGate Name: name of the AccessGate (for example, ECM_EDG_AG).
AccessGate Password: password for the AccessGate (optional).
Save the settings.
Reorder the OAM Identity Asserter, OID/OVD Authenticator, and Default Authenticator by ensuring that the control flag for each authenticator is set as follows:
OAM Identity Asserter: REQUIRED
OID LDAP Authenticator (or OVD LDAP Authenticator): SUFFICIENT
Default Authenticator: SUFFICIENT
DefaultIdentityAsserter
After reordering, save the settings, activate the changes, and restart all servers.
Note:
Do not forget to create a new credential for the new user. See Section 11.17, "Configuring BPEL CSF Credentials" for further details. (This book uses the weblogic_ecm user as an example for SSO.)
This section describes how to set up Oracle Access Manager 11g as the single sign-on solution for the Oracle WebCenter Content enterprise deployment topology. It contains the following sections:
Oracle Access Manager is the recommended single sign-on solution for Oracle Fusion Middleware 11g Release 1. For more information on installing and configuring an Oracle Access Manager installation, see Oracle Fusion Middleware Enterprise Deployment Guide for Oracle Identity Management. This section explains the procedure for configuring the Oracle WebCenter Content installation with an existing Oracle Access Manager 11g installation and the underlying directory service. Oracle recommends using either Oracle Internet Directory (OID) or Oracle Virtual Directory (OVD) or both of these directory services.
Note:
The Oracle WebCenter Content enterprise deployment topology described in this guide uses a single sign-on configuration where both the Oracle WebCenter Content system and the single sign-on system are in the same network domain (mycompany.com). For a multidomain configuration, see the required configuration steps in "Configuring Single Sign-On" in the Oracle Access Manager Access Administration Guide.
The setup for Oracle Access Manager assumes an existing Oracle Access Manager 11g installation complete with Access Managers and a policy protecting the Policy Manager. For more information on installing and configuring an Oracle Access Manager installation, see Oracle Fusion Middleware Enterprise Deployment Guide for Oracle Identity Management. This setup includes a directory service such as Oracle Internet Directory, either stand-alone or as part of an Oracle Virtual Directory configuration. This section provides the necessary steps for configuring your enterprise deployment with either Oracle Internet Directory or Oracle Virtual Directory.
In addition, the Oracle Access Manager installation should have its own Web server configured with WebGate. This section also provides the steps for using the Oracle Access Manager Web server as a delegated authentication server.
You must set up a WebGate on each of the WEBHOST machines where Oracle HTTP Server has already been installed. Sections (UNKNOWN STEP NUMBER) and (UNKNOWN STEP NUMBER) should be repeated for each WEBHOSTn in the deployment environment.
This section covers the following topics:
You must download and install third-party GCC libraries on your machine before installing WebGate. You can download the appropriate GCC library from the following third-party web site:
http://gcc.gnu.org
For 32-bit Linux, the required libraries are libgcc_s.so.1 and libstdc++.so.5 with a version number of 3.3.2. Table 15-3 lists the versions of third-party GCC libraries for Linux and Solaris.
This section describes the procedures for installing WebGate.
Launching the Installer
The installer program for Oracle HTTP Server 11g Webgate for Oracle Access Manager is included in the webgate.zip file.
To start the installation wizard:
Extract the contents of the webgate.zip file to a directory. By default, this directory is named webgate.
Move to the Disk1 subdirectory under the webgate directory.
Set the MW_HOME environment variable to the Middleware Home for the web tier:
export MW_HOME=ORACLE_BASE/product/fmw/web
Start the installer using the following command:
$ ./runInstaller -jreLoc MW_HOME/jdk
Note:
When you install Oracle HTTP Server, the jdk directory is created under the Middleware home directory. You must enter the absolute path of the JRE folder located in this JDK when launching the installer.
After the installer starts, the Welcome screen opens.
Installation Flow and Procedure
If you need additional help with any of the installation screens, click Help to access the online help.
To install Oracle HTTP Server 11g Webgate for Oracle Access Manager:
In the Welcome screen, click Next.
In the Prerequisite Checks screen, click Next.
In the Specify Installation Location screen, specify the Oracle Middleware Home and Oracle Home Directory locations:
ORACLE_BASE/product/fmw
Oracle_OAMWebGate1 (leave the default name)
Note:
The Middleware Home contains an Oracle home for Oracle Web Tier. The default name is Oracle_OAMWebGate1 for this Oracle home directory, which will be created under the Middleware Home.
Click Next.
In the Specify GCC Library screen, specify the directory that contains the GCC libraries, or click Browse to navigate to their location on your local computer (see Section 15.4.3.1, "Installing GCC Libraries"), and click Next.
In the Installation Summary screen, verify the information on this screen and click Install to begin the installation.
In the Installation Progress screen, you may be prompted to run the ORACLE_HOME/oracleRoot.sh script to set up the proper file and directory permissions.
Click Next to continue.
In the Installation Complete screen, click Finish to exit the installer.
Complete the following procedure after installing Oracle HTTP Server 11g Webgate for Oracle Access Manager:
Move to the following directory under your Oracle Home for Webgate:
$ cd Webgate_Oracle_Home/webgate/ohs/tools/deployWebGate
Webgate_Oracle_Home is the directory where you have installed Oracle HTTP Server Webgate and created as the Oracle Home for Webgate, for example:
MW_HOME/Oracle_OAMWebGate1
Note:
Oracle_OAMWebGate1 is the default.
On the command line, run the following command (on a single line) to copy the required bits of agent from the Webgate_Oracle_Home directory to the Webgate Instance location:
$ ./deployWebGateInstance.sh -w ORACLE_BASE/admin/webN/config/OHS/ohsN -oh Webgate_Oracle_Home
The ORACLE_BASE/admin/webN/config/OHS/ohsN directory is the Instance Home of an Oracle HTTP Server (where N is a sequential number for your installation; for example, 1 for WEBHOST1 or 2 for WEBHOST2).
Note:
An instance home for Oracle HTTP Server is created after you configure Oracle HTTP Server.
Run the following command to ensure that the LD_LIBRARY_PATH variable contains Oracle_Home_for_Oracle_HTTP_Server/lib:
$ export LD_LIBRARY_PATH=$LD_LIBRARY_PATH:ORACLE_BASE/product/fmw/webN/lib
From your present working directory, move up one directory level:
$ cd Webgate_Oracle_Home/webgate/ohs/tools/setup/InstallTools
On the command line, run the following command (on a single line) to copy apache_webgate.template from the Webgate_Oracle_Home directory to the Webgate Instance location (renamed to webgate.conf) and update the httpd.conf file to add one line to include the name of webgate.conf:
$ ./EditHttpConf -w ORACLE_BASE/admin/webN/config/OHS/ohsN [-oh Webgate_Oracle_Home] [-o output_file]
Note:
The -oh WebGate_Oracle_Home and -o output_file parameters are optional.
In the command, WebGate_Oracle_Home is the directory where you have installed Oracle HTTP Server Webgate for Oracle Access Manager and created as the Oracle Home for Webgate, for example:
MW_HOME/Oracle_OAMWebGate1
The ORACLE_BASE/admin/webN/config/OHS/ohsN directory is the instance home of Oracle HTTP Server, where N is a sequential number for your installation; for example, 1 for WEBHOST1 or 2 for WEBHOST2.
The output_file value is the name of the temporary output file used by the tool; for example:
Edithttpconf.log
This section describes the procedures for registering the WebGate Agent:
Section 15.4.4.2, "Updating the Oracle Access Manager 11g Request File"
Section 15.4.4.4, "Changing the inspection.wsil Resource to Use the Basic Authentication Scheme"
The RREG tool is part of the Oracle Access Manager 11g installation. If it is not already available, extract it using the following procedure:
After installing and configuring Oracle Access Manager, navigate to the following location:
IDM_Home/oam/server/rreg/client
On the command line, untar the RREG.tar.gz file using gunzip, as in the following example:
gunzip RREG.tar.gz tar -xzvf RREG.tar
Edit the oamreg.sh script in the RREG_HOME/bin directory and change the OAM_REG_HOME parameter according to your setup:
OAM_REG_HOME=RREG_Home
(where RREG_Home is the directory to which you extracted the contents of RREG.tar.gz and rreg).
Save the script file.
The RREG Configuration Tool provides a way to register protected and public resources into the Oracle Access Manager system. The list of protected resources to be added to the Oracle Access Manager system is as follows:
/adfAuthentication /adfAuthentication/…/* /imaging/faces /imaging/faces/…/* /em /em/…/* /console /console/…/* /DefaultToDoTaskFlow /DefaultToDoTaskFlow/…/* /sdpmessaging/userprefs-ui /sdpmessaging/userprefs-ui/…/* /integration/worklistapp /integration/worklistapp/…/* /workflow/sdpmessagingsca-ui-worklist /workflow/sdpmessagingsca-ui-worklist/…/* /soa/composer /soa/composer/…/* /soa-infra /soa-infra/.../* /soa-infra/deployer /soa-infra/deployer/…/* /soa-infra/events/edn-db-log /soa-infra/events/edn-db-log/…/* /soa-infra/cluster/info /soa-infra/cluster/info/…/* /inspection.wsil /inspection.wsil/…/*
The list of public resources follows:
/cs /cs/…/* /_ocsh /_ocsh/…/* /imaging /imaging/…/* /soa-infra/services/.../* /soa-infra/directWSDL /soa-infra/directWSDL/…/* /ucs/messaging/webservice /ucs/messaging/webservice/…/*
In these lists, "/…/*" implies all resources under the base URL context.
Before running the oamreg tool, you must first add the required resources to Oracle Access Manager 11g for the Oracle WebCenter Content components, listed under Section 15.4.4.1, "Extracting and Using the RREG Tool."
The RREG_Home/input directory contains a template file named OAM11gRequest.xml. Copy this file to WCCOAM11gRequest.xml and edit that file to create the policies for the Oracle WebCenter Content installation.
Note:
Replace OAM_HOST, OAM_ADMINSERVER_PORT, WCC_EDG_AGENT, and WCC_EDG_DOMAIN with their respective values in your installation.
After editing, the file should look as follows:
<?xml version="1.0" encoding="UTF-8"?>
<OAM11GRegRequest>
<serverAddress>http://OAM_HOST:OAM_ADMINSERVER_PORT</serverAddress>
<agentName>WCC_EDG_AGENT</agentName>
<applicationDomain>WCC_EDG_DOMAIN</applicationDomain>
<cachePragmaHeader>private</cachePragmaHeader>
<cacheControlHeader>private</cacheControlHeader>
<ipValidation>1</ipValidation>
<ValList ListName="ipValidationExceptions">
<ValListMember Value="10.1.1.1"/>
</ValList>
<logOutUrls>
<url>/oamsso/logout.html</url>
</logOutUrls>
<protectedResourcesList>
<resource>/adfAuthentication</resource>
<resource>/imaging/faces</resource>
<resource>/em</resource>
<resource>/console</resource>
<resource>/DefaultToDoTaskFlow</resource>
<resource>/sdpmessaging/userprefs-ui</resource>
<resource>/integration/worklistapp</resource>
<resource>/workflow/sdpmessagingsca-ui-worklist</resource>
<resource>/soa/composer</resource>
<resource>/soa-infra/deployer</resource>
<resource>/soa-infra/events/edn-db-log</resource>
<resource>/soa-infra/cluster/info</resource>
<resource>/inspection.wsil</resource>
<resource>/soa-infra</resource>
</protectedResourcesList>
<publicResourcesList>
<resource>/cs</resource>
<resource>/_ocsh</resource>
<resource>/imaging</resource>
<resource>/soa-infra/directWSDL</resource>
<resource>/ucs/messaging/webservice</resource>
</publicResourcesList>
<userDefinedParameters>
<userDefinedParam>
<name>filterOAMAuthnCookie</name>
<value>false</value>
</userDefinedParam>
</userDefinedParameters>
</OAM11GRegRequest>
Notes:
The resource_name/.../* resources will be automatically added during the registration.
This guide describes the validation field entry in request files for Oracle Access Manager 11g (11.1.1.2) and later. The validation exception list is defined differently in earlier versions of Oracle Access Manager 11g. For earlier versions, instead of using the <ValList> entry as shown in the preceding text, use this syntax after the </publicResourcesList> entry:
<userDefinedParameters>
<userDefinedParam>
<name>ipValidationExceptions</name>
<value>10.1.1.1</value>
</userDefinedParam>
</userDefinedParameters>
For more information about adding IP validation exceptions, see the Oracle Fusion Middleware Administrator's Guide for Oracle Access Manager with Oracle Security Token Service.
Run the oamreg tool using the following command:
$ ./RREG_Home/bin/oamreg.sh inband input/WCCOAM11gRequest.xml
The run should look as follows:
------------------------------------------------ Welcome to OAM Remote Registration Tool! Parameters passed to the registration tool are: Mode: inband Filename: /u01/app/oracle/product/fmw/iam/oam/server/rreg/client/rreg/input/WCCOAM11GRequest.xml Enter admin username:oamadmin Username: your_oamadmin_user Enter admin password: your_oamadmin_password Do you want to enter a Webgate password?(y/n): y Enter webgate password: your_webgate_password Enter webgate password again: your_webgate_password Password accepted. Proceeding to register.. Apr 18, 2011 12:22:36 PM oracle.security.am.engines.rreg.client.handlers.request.OAM11GRequestHandler getWebgatePassword INFO: Passwords matched and accepted. Do you want to import an URIs file?(y/n): n ---------------------------------------- Request summary: OAM11G Agent Name:WCC_EDG_AGENT URL String:WCC_EDG_AGENT Registering in Mode:inband Your registration request is being sent to the Admin server at: http://oamserver.mycompany.com:7001 ---------------------------------------- Inband registration process completed successfully! Output artifacts are created in the output folder.
By default, the inspection.wsil resource is set to use the form authentication scheme. For the connection between the workflow and Oracle WebCenter Content: Imaging to work, this resource must be updated to use the basic authentication scheme instead:
Log in to the Oracle Access Manager console at http://OAM_HOST:OAM_ADMINSERVER_PORT/oamconsole.
Using the navigation tree on the left, choose Application Domains and then the application domain name to navigate to the application domain created (WCC_EDG_DOMAIN).
Expand your application domain's name.
Expand Authentication Policies.
Double-click Protected Resource Policy.
Select the inspection.wsil and inspection.wsil/.../* resources and click the Delete icon in the Resources pane to remove them.
Click Apply and confirm the action when prompted.
In the navigation tree, click Authentication Policies again, and click the Create button in the tool bar above the navigation tree.
Enter a name for the policy (for example, New Basic Policy).
Select BasicSessionlessScheme as the authentication scheme.
Click Apply.
You will see the newly created policy under Authentication Policies in the navigation tree.
Open the newly created policy.
On the Resources pane, click the Add icon (plus sign) on the right and add the inspection.wsil and inspection.wsil/.../* resources.
Click Apply.
Click the refresh icon on the navigation tree and verify the new authentication policy (click it and make sure the inspection.wsil and inspection.wsil/.../* resources were added).
Note:
Do not forget to create a new credential for the new user. See Section 11.17, "Configuring BPEL CSF Credentials" for further details. (This book uses the weblogic_ecm user as an example for SSO.)
You must set the NoUniqueSessionsFor10gAgents parameter in the Oracle Access Manager 11g configuration to true. To do this, edit the oam-config.xml file located in the IDM_Home/oam/server/config directory and change the line
<Setting Name="NoUniqueSessionsFor10gAgents" Type="xsd:string">false</Setting>
to
<Setting Name="NoUniqueSessionsFor10gAgents" Type="xsd:string">true</Setting>
Save the file, and restart the Oracle Access Manager server in your identity management system for the change to take effect.
The following two files are generated in RREG_Home/output/WCC_EDG_AGENT:
ObAccessClient.xml
cwallet.sso
Copy these files to the WebGate instance location on the WEBHOST machine:
scp ObAccessClient.xml oracle@WEBHOSTN:ORACLE_BASE/admin/webN/config/OHS/ohsN/ webgate/config/ scp cwallet.sso oracle@WEBHOSTN:ORACLE_BASE/admin/webN/config/OHS/ohsN/ webgate/config/
In the scp command, N is a sequential number for your installation; for example, 1 for WEBHOST1 or 2 for WEBHOST2.
This section assumes that you have already set up the LDAP authenticator by following the steps in Section 15.2.2.1, "Creating the LDAP Authenticator." If you have not already created the LDAP authenticator, do it before continuing with this section.
This section covers the following topics:
To be safe, first back up the relevant configuration files:
ORACLE_BASE/admin/domain_name/aserver/domain_name/config/config.xml ORACLE_BASE/admin/domain_name/aserver/domain_name/config/fmwconfig/jps-config.xml ORACLE_BASE/admin/domain_name/aserver/domain_name/config/fwmconfig/system-jazn-data.xml
In addition, back up the boot.properties file for the Administration Server.
To set up the OAM ID Asserter:
Log in to Weblogic Console, if not already logged in.
Click Lock & Edit.
Navigate to SecurityRealms, then the default realm name, and then Providers.
Click New and select OAMIdentityAsserter from the dropdown menu.
Name the asserter (for example, OAM ID Asserter) and click OK.
Click the newly added asserter to see the configuration screen for OAM Identity Asserter.
Set the control flag to REQUIRED.
Select both the ObSSOCookie and OAM_REMOTE_USER options under Chosen types.
Save the settings.
Finally, log in to the WLST console as an administrator and run the following command:
addOAMSSOProvider(loginuri="/${app.context}/adfAuthentication",logouturi="oamsso/logout.html")
To set the order of the providers:
Log in to Weblogic Console, if not already logged in.
Click Lock & Edit.
Navigate to SecurityRealms, then the default realm name, and then Providers.
Reorder the OAM Identity Asserter, OID/OVD Authenticator, and Default Authenticator by ensuring that the control flag for each authenticator is set as follows:
OAM Identity Asserter: REQUIRED
OID LDAP Authenticator (or OVD LDAP Authenticator): SUFFICIENT
Default Authenticator: SUFFICIENT
Click OK.
Click Activate Changes to propagate the changes.
Restart the Administration Server and all managed servers.
Validate single sign-on through both Oracle HTTP Server instances using the following URLs:
http://WEBHOST1:7777/console
http://WEBHOST1:7777/em
http://WEBHOST1:7777/cs
http://WEBHOST1:7777/imaging
http://WEBHOST2:7777/console
http://WEBHOST2:7777/em
http://WEBHOST2:7777/cs
http://WEBHOST2:7777/imaging
Then validate single sign-on through the front-end (using the SSO user name and password):
http://admin.mycompany.com/console
http://admin.mycompany.com/em
http://wcc.mycompany.com/cs
http://wcc.mycompany.com/imaging
After you have verified that the extended domain is working, back up the installation. This is a quick backup for the express purpose of immediate restore in case of problems in the further steps. The backup destination is the local disk. This backup can be discarded once the enterprise deployment setup is complete. At that point, the regular deployment-specific backup and recovery process can be initiated. The Oracle Fusion Middleware Administrator's Guide provides further details. For information on describing the Oracle HTTP Server data that must be backed up and restored, refer to the "Backup and Recovery Recommendations for Oracle HTTP Server" section in this guide. For information on how to recover components, see "Recovery of Components" and "Recovery After Loss of Component" sections in the guide. For recommendations specific to recovering from the loss of a host, see the "Recovering Oracle HTTP Server to a Different Host" in the guide. Also refer to the Oracle Database Backup and Recovery User's Guide for information on database backup.
To back up the installation at this point:
Back up the web tier:
Shut down the instance using opmnctl.
ORACLE_BASE/admin/instance_name/bin/opmnctl stopall
Back up the Middleware Home on the web tier using the following command (as root):
tar -cvpf BACKUP_LOCATION/web.tar $MW_HOME
Back up the Instance Home on the web tier using the following command (as root):
tar -cvpf BACKUP_LOCATION/web_instance.tar $ORACLE_INSTANCE
Start the instance using opmnctl:
ORACLE_BASE/admin/instance_name/bin/opmnctl startall
Back up the AdminServer domain directory on SOAHOST1. Perform a backup to save your domain configuration. The configuration files all exist under the ORACLE_BASE/ admin/domain_name directory.
tar -cvpf edgdomainback.tar ORACLE_BASE/admin/domain_name