| Oracle® Fusion Applications Upgrade Guide 11g Release 7 (11.1.7) Part Number E35833-18 |
|
|
PDF · Mobi · ePub |
| Oracle® Fusion Applications Upgrade Guide 11g Release 7 (11.1.7) Part Number E35833-18 |
|
|
PDF · Mobi · ePub |
This appendix provides additional information about Upgrade Orchestrator.
This appendix includes the following topics:
This section provides additional information about Upgrade Orchestrator commands. The following topics are included:
The following command arguments are available for the orchestration command to retrieve information about the status of the upgrade as well as manage the status.
Use updateStatus to update the status for a specific task to either SUCCESS or FAILURE. For more information, see Section A.1.3, "Options for the Orchestration updateStatus Command."
Use getStatus to retrieve the status of a specific task as well as the summary of the upgrade on a specific POD_NAME and host_type while Upgrade Orchestrator is running. For more information, see Section A.1.4, "Options for the Orchestration getStatus Command" and Section 6.3, "Monitoring Upgrade Orchestration Progress."
Use exitOrchestration to terminate orchestration gracefully on all hosts on a specific pod. For more information, see Section 6.4, "Terminate Upgrade Orchestration."
Use clearExitOrchestration to clear the exit status on all hosts. For more information, see Section 6.4, "Terminate Upgrade Orchestration."
Use getExitOrchestrationStatus to retrieve the status of the exitOrchestration command.
Use validateSetup to validate the shared location status and permissions. This validation is implicitly run when any of the orchestration command options are run. For more information, see Section A.1.5, "The validatesetup Argument."
The following table provides a description of the options available when using the orchestration command to start Upgrade Orchestrator.
Table A-1 Options for the orchestration.sh command
| Name | Mandatory | Description |
|---|---|---|
|
-pod |
Yes |
The value of |
|
-hosttype |
Yes |
The host type. Valid values are PRIMORDIAL, MIDTIER, OHS, and IDM. For more information see Section 1.2.1, "Host Types". |
|
-release |
No |
The release name, for example, REL5-7 or REL7. If this option is not used, all releases defined in the manifest file are executed. |
|
-phase |
No |
Only the |
|
-checkpoint |
No |
Valid values are true or false. If set to false, ignore the checkpoint results and rerun. The default value is true. |
|
-DlogLevel |
No |
The log level. Valid values are SEVERE, WARNING, INFO, CONFIG, FINE, FINER and FINEST. The default value is INFO. Note that error messages are displayed on the console for database component failures if you set the |
|
-v |
No |
Displays the product version and exits. |
|
-h |
No |
Displays help information and exits. |
The following table provides a description of the available options when using the orchestration command to update the status of orchestration tasks.
Table A-2 Options for orchestration.sh updateStatus command
| Name | Mandatory | Description |
|---|---|---|
|
updateStatus |
Do not use with |
Updates the status of the selected task. |
|
-pod |
Yes |
The name of the pod to be searched. |
|
-hosttype |
Yes |
The host type. Valid values are: PRIMORDIAL, MIDTIER, OHS, and IDM. |
|
-hostname |
Yes |
Host name, including domain details. |
|
-release |
Yes |
The release name, for example, REL5-7 or REL7. If this option is not used, all releases defined in the manifest file are executed. |
|
-phase |
Yes |
The phase name. Valid values are: |
|
-taskid |
Yes |
Orchestration |
|
-taskstatus |
Yes |
Orchestration task status. Valid values are |
|
-v |
No |
Displays the product version and exits. |
|
-h |
No |
Displays help information and exits. |
The following table provides a description of the available options when using the orchestration command to get the status of an orchestration session.
Table A-3 Options for orchestration.sh getStatus command
| Name | Mandatory | Description |
|---|---|---|
|
getStatus |
Do not use with |
Retrieves the checkpoint status from the selected orchestration task. |
|
-pod |
Yes |
The name of the pod to be searched. |
|
-hosttype |
Yes |
The host type. Valid values are: PRIMORDIAL, MIDTIER, OHS, and IDM. |
|
-hostname |
Yes |
Host name, including domain details. |
|
-release |
Yes |
The release name, for example, REL5-7 or REL7. If this option is not used, all releases defined in the manifest file are queries. |
|
-phase |
No |
You can specify the following phase names to see the status for the specific phase: |
|
-taskid |
No |
The Orchestration |
|
-taskstatus |
No |
The Orchestration task status. Valid values are |
|
-v |
No |
Displays the product version and exits. |
|
-h |
No |
Displays help information and exits. |
If you run the orchestration.sh command with the validatesetup argument, the following validations occur:
Validating SHARED_UPGRADE_LOCATION
Successfully validated permissions of shared folder.
Validating ORCHESTRATION_CHECKPOINT_LOCATION
Successfully validated permissions of shared folder.
Validating ORCHESTRATION_CHECKPOINT_ARCHIVE_LOCATION
Successfully validated permissions of shared folder.
These options are implicitly run when any of the orchestration commands run.
This section describes the utilities that are run by Upgrade Orchestrator. This is for your information only and no action is needed.The following utilities are included:
During the installation phase, RUP Installer copies all files for 11g Release 7 (11.1.7) to the appropriate locations, such as Oracle Fusion Middleware home and Oracle Fusion Applications Oracle home. After the file copy completes, RUP Installer calls its first installer to update Oracle Fusion Applications Patch Manager and apply Oracle Fusion Middleware patches. When the first installer completes successfully, RUP Installer calls the second installer, which performs the Policy Store Analysis. Upon successful completion of the Policy Store Analysis, RUP Installer calls Configuration Assistants to perform the remaining tasks required to update and deploy artifacts to Oracle Fusion Applications. Depending on the contents of 11g Release 7 (11.1.7), not all configuration assistants may run.
All mandatory configuration assistants must complete successfully before proceeding to the next configuration assistant.
If any tasks fail during the installation phase, refer to Section 6.8, "Troubleshooting Failures During the Installation Phase" for more information.
The following table provides a list of configuration assistants that the first installer runs. The Retry Behavior and Troubleshooting column describes what RUP Installer does after a configuration assistant fails, you resolve the cause of the failure, and then resume orchestration. If available, links are provided to relevant troubleshooting sections.
Table A-4 Configuration Assistants Run by Oracle Fusion Applications 11g Release 7 (11.1.7) RUP Installer Part 1 of 2
| Name | Mandatory | Description | Retry Behavior and Troubleshooting |
|---|---|---|---|
|
Configure Patch Manager |
Yes |
Configures Oracle Fusion Applications Patch Manager. |
Starts from the beginning of the task. |
|
Consolidate Repository And Downloaded Patches |
Yes |
Consolidates patches in the repository and the patches you download in Section 2.3.6.3, "Download and Unzip Mandatory Post-Release 7 Patches". |
Starts from the beginning of the task. |
|
Update Patch Manager |
Yes |
Applies Patch Manager Patches |
Applies failed patches. |
|
Reconfigure Patch Manager |
Yes |
Reconfigures Oracle Fusion Applications Patch Manager. |
Starts from the beginning of the task. |
|
Bootstrap Patch Manager |
Yes |
Updates the data model for Oracle Fusion Applications Patch Manager by running the |
Starts from the beginning of the task. See Section 6.19.5, "Troubleshooting Bootstrapping Patch Manager". |
|
Create Middleware Schemas |
Yes |
Creates Oracle Fusion Middleware schemas |
Starts from the beginning of the task. |
|
Apply Middleware Patch Sets |
Yes |
Applies Oracle Fusion Middleware patch sets, which can include upgrades, schema changes and installers. For more information, see Section A.2.1.1.1, "Middleware Installers Invoked by the Apply Middleware Patch Sets Configuration Assistant". |
Installs failed patch sets. |
|
Apply Pre-PSA Middleware Patches |
Yes |
Applies Pre-PSA Middleware Patches For more information, see Section A.2.1.1.2, "Patches Not Supported by the Apply Pre-PSA and Post-PSA Middleware Patches Configuration Assistants". |
Applies the failed patches. See Section 6.12, "Troubleshooting Applying Middleware Patches". |
|
Verify Middleware PSA Schema Credentials |
Yes |
Verifies users and logins for schemas. |
Starts from the beginning of the task. |
|
Upgrade Middleware Schemas |
Yes |
Runs Oracle Fusion Middleware patch set assistants (PSA). |
Runs failed tasks. See Section 6.12.5, "Troubleshooting Upgrading Middleware Schema". |
|
Apply Post-PSA Middleware Patches |
Yes |
Applies Post-PSA Middleware Patches |
Applies the failed patches. See Section 6.12, "Troubleshooting Applying Middleware Patches". |
|
Restore Default Context in |
Yes |
Restores default context. |
Checks if file is corrupted and replaces the file with a well formed XML file and Re-Try. |
|
Upgrade OPSS |
Yes |
Upgrades the Policy Store. |
Starts from the beginning of the task. |
|
Extend Certificate Validity |
Yes |
Extends certificate validity by three years from the date of the upgrade. |
Starts from the beginning of the task. |
|
Deploy Middleware Policies (jazn-data.xml) |
Yes |
Deploys Middleware policies. |
Starts from the beginning of the task and includes the clean up required. |
|
Apply Offline BI Metadata and Configuration Updates |
Yes |
Performs the deployment of the updated applications policies for Oracle Business Intelligence. |
Retries failed steps. |
|
Apply ESSAPP Code Source Grant Changes |
Yes |
Adds code source grants to support auditing. |
Starts from the beginning of the task. |
|
Apply Domain Configuration |
Yes |
Applies startup parameter changes and configures |
Retries failed steps. |
|
Propagate Domain Configuration |
Yes |
Unzips RUP Lite for Domain Configuration into |
Starts from the beginning of the task. See Section 6.19.6, "Troubleshooting Failures During Propagating Domain Configuration". |
The following table provides a list of configuration assistants that the second installer runs. The Retry Behavior and Troubleshooting column describes what RUP Installer does after a configuration assistant fails, you resolve the failure, and then resume orchestration. If available, links are provided to relevant troubleshooting sections. The second installer supports parallel processing of certain configuration assistants, which run in groups. For more information, see Section A.2.1.2.7, "Parallel Configuration Assistants".
Table A-5 Configuration Assistants Run by Oracle Fusion Applications 11g Release 7 (11.1.7) RUP Installer Part 2 of 2
| Name | Mandatory | Description | Retry Behavior and Troubleshooting |
|---|---|---|---|
|
Configure Patch Manager |
Yes |
Configures Oracle Fusion Applications Patch Manager. |
Starts from the beginning of the task. |
|
Bootstrap Patch Manager |
Yes |
Updates the data model for Oracle Fusion Applications Patch Manager by running the fapmgr |
Starts from the beginning of the task. See Section 6.19.5, "Troubleshooting Bootstrapping Patch Manager". |
|
Offline Preverification Pre Database Content Upload |
Yes |
Performs the following validation checks while all servers are shut down:
|
Runs failed steps. |
|
Grant Privileges to Application Schemas |
Yes |
Grants system privileges to database users and creates base object privileges. |
Runs the failed script. |
|
Load Database Components |
Yes |
Uploads the database content packaged in 11g Release 7 (11.1.7) to the database, such as database objects, seed data, and package headers and bodies. |
Runs failed database commands. See Section 6.13, "Troubleshooting Loading Database Components". |
|
Deploy Applications Policies (jazn-data.xml) |
Yes |
Deploys updated applications policies, based on your selections during the Policy Store Analysis configuration assistant. |
Deploys the failed stripes. See Section 6.14, "Troubleshooting Deployment of Applications Policies". |
|
Deploy BI Publisher Artifacts |
Yes |
Using Catalog Manager, performs the following steps:
|
Starts from the beginning of the task. See Section 6.19.8, "Troubleshooting Deployment of BI Publisher Artifacts". |
|
Import Oracle Data Integrator Repositories |
Yes |
|
Imports failed data. |
|
Create Grants/Synonyms on Application Database Objects |
Yes |
Creates synonyms between database objects and grants object privileges to database users. |
Runs the failed script. |
|
Offline Preverification Post Database Content Upload |
Yes |
Validate Host and Port for New Managed Servers. |
Starts from the beginning of the task. |
|
Deploy Data Security Grants |
Yes |
Performs GUID reconciliation in LDAP. |
Starts from the beginning of the task. |
|
Generate SOA Configuration Plan |
Yes |
Generates the configuration plan to be used for deploying SOA composites. |
Starts from the beginning of the task. |
|
Update Flexfield Configuration |
Yes |
Updates the |
Starts from the beginning of the task. |
|
Configure New Managed Servers |
Yes |
Configures managed servers for new applications to be associated with the first non-admin host by default. |
Reapplies failed managed server templates. |
|
Deploy New Applications |
Yes |
Deploys new applications using domain extension templates. |
Reapplies failed domain extension templates. |
|
Generate ADF Domain Configuration Plan |
Yes |
Generates Oracle ADF domain configuration in Metadata Service (MDS) to be used by Expression Language (EL) expressions in |
Starts from the beginning of the task. |
|
Apply Offline Setting Changes |
Yes |
Applies Oracle Fusion Applications environment configuration setting changes while all servers are shut down. |
Retries failed domains. |
|
Verify Node Manager and OPMN Status |
Yes |
Verifies the following processes:
You must not exit out of RUP Installer during this configuration assistant. |
Runs failed steps. See Section 6.9.3, "Troubleshooting Failure During Verifying Node Manager and OPMN Status". |
|
Start All Admin Servers |
No |
Starts all Administration Servers. |
Restarts failed Administration Servers. See Section 6.15, "Troubleshooting Server Start and Stop Failures". |
|
Configure DB Persistence Store for JMS/TLogs |
Yes |
Configures SOA and UMS to store JMS and TLogs content in the database instead of the file system. |
Retries failed plug-ins. |
|
Configure OPSS Keystore Service |
Yes |
Configures OPSS to be used for remote task flow Keystore Service. |
Starts from the beginning of the task. |
|
Deploying LDAP Data (LDIF) |
No |
Loads new enterprise roles. |
Retries to load the failed LDIF files. |
|
Create Fusion APPIDs |
Yes |
Creates Fusion APPID users and groups in the LDAP server and credentials for those users in the credential store. |
Starts from the beginning of the task. |
|
Apply Admin Server Online Setting Changes |
Yes |
Applies Oracle Fusion Applications environment configuration setting changes that are applicable to the Administration Servers. |
Starts from the beginning of the task. |
|
Start Minimal Servers for Configuration Updates |
Yes |
Starts minimal managed servers required to run the necessary configuration assistants successfully. |
Starts from the beginning of the task. |
|
Apply UCM Configuration |
Yes |
Configures UCM to store content in the database instead of the file system. |
Starts from the beginning of the task. |
|
Apply WebCenter Connection Changes |
Yes |
|
Retries failed plug-ins. |
|
Configure Trust Asserter |
Yes |
Configures trust asserter to be used for remote task flow Keystore Service. |
Starts from the beginning of the task. |
|
Start All Servers |
No |
Starts all servers in all domains, including the BI servers. Also performs the |
Restarts failed servers. See Section 6.15, "Troubleshooting Server Start and Stop Failures". |
|
Online Preverification |
Yes |
Performs steps described in see Section A.2.1.1.3, "Steps Performed During Online Preverification". |
Runs failed steps. See Section 6.15.4, "EditTimedOutException Error During Online Preverification". |
|
Upgrade ADF Metadata |
No |
Upgrades ADF related metadata. |
Retries failed domains. |
|
Generate OHS Reference Configuration File |
No |
Generates OHS configuration files for installed product families in the directory, |
Starts from the beginning of the task. |
|
Apply OWSM Configuration |
Yes |
Upgrades Oracle Web Services Manager (Oracle WSM) policies after backing up the policies. |
Restores the backup of the policies and starts from the beginning of the task. |
|
Deploy SPE Inline Service Artifacts |
No |
Deploys SPE Inline Service Artifacts. |
Retries the deployment. |
|
Deploy Data Role (RGX) Templates |
No |
Deploys RGX Template artifacts to the Common Domain. |
Deploys failed templates. |
|
Apply OAM Configuration |
No |
Applies changes to the Oracle Access Manager (OAM) configuration. |
Starts from the beginning of the task. See Section 6.11.4, "Location of GRC Policies in the OAM Applications Domain". |
|
Deploy Flexfields |
No |
Deploys flexfields to the domain that hosts the |
Starts from the beginning of the task. |
|
Apply Online BI Metadata and Configuration Updates |
Yes |
Applies Oracle Business Intelligence Metadata updates. |
Starts from the beginning of the task. If you made any customizations to the Oracle BI Repository, the Oracle BI Presentation Catalog, or JAZN settings related to Oracle Business Intelligence, you must merge your changes. See Section 5.11, "Resolve Conflicts That Occurred During Oracle BI Metadata Updates". |
|
Import Group Space Templates |
No |
Imports Group Space Templates. |
Deploys failed templates. |
|
SOA Preverification |
Yes |
Performs the steps described in Section A.2.1.1.4, "Steps Performed During SOA Preverification". If you have customizations, you must merge them during this configuration assistant. |
Retries failed steps. See Section 6.16.6, "Merging SOA Composite JDeveloper Customizations During SOA Preverification". |
|
Apply SES Configuration Changes |
No |
Updates additional configuration updates to Oracle Secure Enterprise Search (SES) running on the Common Domain. |
Starts from the beginning of the task. |
|
Remove UCM SES Objects |
No |
||
|
Deploy BPM Templates |
No |
Deploys BPM Templates to the MDS repository. |
Deploys failed templates. |
|
Deploy B2B Metadata |
No |
Deploys B2B Metadata. |
Deploys failed B2B artifacts. |
|
Deploy SOA Shared Repository |
Yes |
Deploys SOA shared repository artifacts to the SOA servers available in the environment. |
Deploys failed SOA shared repository artifacts. |
|
Deploy UpdateSOAMDS Composite |
No |
Deploys the |
Deploys composite on domains that failed. |
|
Deploy SOA Composites |
No |
Deploys SOA composites to the corresponding SOA servers and performs server management steps. |
Deploys failed SOA composites. See Section 6.16, "Troubleshooting SOA Composite Deployment Failures". |
|
Deploy SOA Resource Bundles |
Yes |
Deploys SOA Resource Bundles to the corresponding SOA servers. |
Deploys failed SOA resource bundles. |
|
Import Image Routing (IPM) Artifacts |
No |
Deploys IPM artifacts to the IPM server. |
Retries failed IPM artifacts. See Section 6.19.10, "Failure During IPM Import". |
|
Restart All SOA Servers |
Yes |
Restarts all SOA servers in the environment. |
Starts at the beginning of the task. |
|
Apply Online Setting Changes |
No |
Applies Oracle Fusion Applications environment configuration setting changes during the online phase. |
Starts from the failed task. |
|
Generate RUP Lite for OHS |
No |
Generates the zip file that contains all files needed by RUP Lite for OHS to upgrade OHS. |
Starts at the beginning of the task. |
|
Apply Downloaded Oracle Fusion Applications Patches |
Yes |
Applies the Oracle Fusion Applications patches that you downloaded in Section 2.3.6.3, "Download and Unzip Mandatory Post-Release 7 Patches". |
Applies failed patches. |
|
Post Configuration |
No |
|
Retries failed domains. |
The following installers are invoked by the Apply Middleware Patch Sets configuration assistant:
Oracle Business Intelligence
Oracle Common
Oracle Data Integrator (ODI)
Oracle Database Client
Oracle Enterprise Content Management
Oracle HTTP Server (OHS) - OHS may be installed either beside the rest of the Oracle Fusion Middleware in the Oracle Fusion Applications middle tier or on a separate DMZ machine. For either case, patching OHS requires running RUP Lite for OHS.
Oracle Fusion Middleware Extensions for Applications
Oracle Global Order Promising
Oracle Identity Management (IDMUTIL)
Oracle Secure Enterprise Search (SES)
Oracle SOA Suite
Oracle Social Networking (OSN)
Oracle WebCenter Suite
Oracle WebLogic Server
Oracle Web Tier
The following patches are not supported by these configuration assistants:
Integrated Development Environment (IDE)
OHS installed in the DMZ: Installed by RUP Lite for OHS.
Database Server: You patch your Database Server using RUP Lite for RDBMS. For more information, see Chapter 3, "Updating the Oracle Fusion Applications and Oracle Identity Management Databases".
Oracle Identity Management Server: You patch your IDM server by following the steps in Section 4.4.4, "Upgrade Oracle Identity Management Domain to 11g Release 6 (11.1.6)" and Section 4.4.5, "Upgrade Oracle Identity Management Domain to 11g Release 7 (11.1.7)".
The following validation steps are performed during the Online Preverification configuration assistant, if Release 7 (11.1.7) contains artifacts related to the validation:
Taxonomy URL
Database validation
Flexfield: Checks for the HelpPortal Managed Server in the Common Domain and for the successful deployment of the FndSetup application.
OAM Configuration
SES Admin Server URL
SPE Inline Service: Checks if the Oracle CRM Performance application is deployed. If it is, the OracleRTD application must be deployed and at least one BI server must be running where the OracleRTD application is deployed.
Data Role (RGX) Template: Checks if the Administration Server for the Common Domain is up.
Group Space Template: Checks if the following Managed Servers are up: WC_Spaces, WC_Collaboration, ucm_server1.
Oracle WSM validation
The following validation steps are performed during the SOA Preverification configuration assistant:
Business Process Management (BPM) Template
B2B Metadata: Checks if the Common Domain, SOA Managed Server, and the LDAP Server are up.
SOA Shared Repository: Verifies the taxonomy, checks if the Administration Server is up, and checks for SOA_SERVER and SOA_PLATFORM readiness.
UpdateSOAMDS SOA Composite: Verifies the taxonomy, checks if the Administration Server is up, and if the SOA platform is ready.
SOA Resource Bundle: Verifies the taxonomy, checks if the Administration Server is up, and if the SOA platform is ready.
SOA Composites: Performs the following validation steps:
Verifies the taxonomy.
Checks if the Administration Server is up.
Checks if the SOA platform is ready.
Checks if the base composite is deployed.
Checks if the default revision is deployed.
Checks if the new revision is not deployed.
Checks whether the SOA composites that will be affected by the upgrade contain JDeveloper customizations. For more information, see Section 6.16.6, "Merging SOA Composite JDeveloper Customizations During SOA Preverification".
Image Routing (IPM): Checks if the IPM server is up.
RUP Installer and Language Pack Installer provide a graphical user interface which allows you to control the behavior of the installer by the use of buttons, in cases where it encounters a failure. Note that the behavior of these buttons may vary, depending on whether it is a configuration assistant, or a step within a configuration assistant, that fails. The behavior also depends on whether a configuration assistant is mandatory. All mandatory configuration assistants must complete successfully before proceeding to the next configuration assistant. For information about which configuration assistants are mandatory, see Section A.2.1.1, "RUP Installer Configuration Assistants".
You can exit out of the installer in the event of a failure and restart from the point of failure. If a non-mandatory configuration assistant fails, and you continue to the next configuration assistant, you must restart the installer after it finishes the last configuration assistant. When you restart, the installer retries all failed configuration assistants and steps.
An explanation of the usage of each button follows. Note that the buttons are available only in GUI mode, not in silent mode. For information about how to use the buttons during parallel processing of certain configuration assistants, see Section A.2.1.2.7, "Parallel Configuration Assistants".
The Abort button allows you to skip a failed configuration assistant or step within a configuration assistant, and records the failure so it can be rerun when you restart the installation. For mandatory configuration assistants, after you abort the configuration assistant, the installer does not proceed and only the Cancel button is enabled. You must then resolve the cause of the failure and start the installer from this failure point. For non-mandatory configuration assistants, the installer proceeds to the next configuration assistant after you abort the configuration assistant. This button is enabled only after a failure.
The Cancel button allows you to stop an installer session after the failure of a mandatory action. This button is enabled only after a failure.
The Windows Close button allows you to stop an installer session after a failure. This is enabled only after a failure.
The Continue button allows you to skip a failed non-mandatory step within any configuration assistant The installer records the failure and then proceeds with the next step within the configuration assistant. When you rerun this installer session, the failed steps within the configuration assistant are attempted again.
Note that this button is enabled only for non-mandatory steps within a configuration assistant.
The Next button allows you to proceed to the next screen. This button is enabled only when all configuration assistants complete successfully in the current screen.
The Retry button allows you to attempt to rerun a failed configuration assistant, or a step within a configuration assistant. Use Retry when you know the cause of the failure and can resolve the issue during the current RUP Installer session.
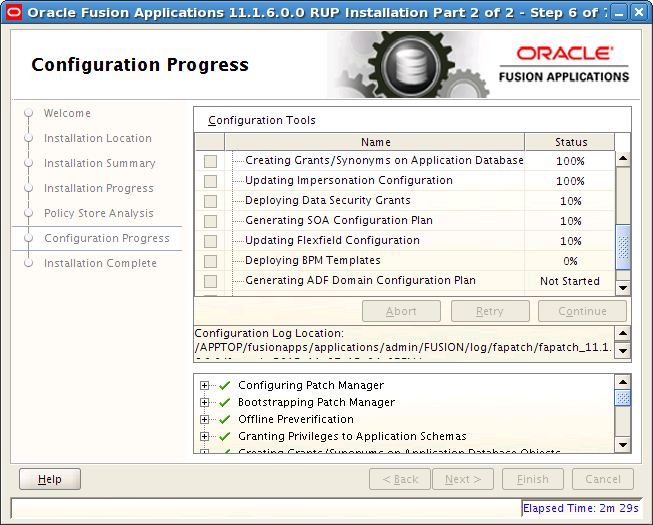
RUP Installer and Language Pack Installer support parallel processing of certain configuration assistants to improve performance. Parallel configuration assistants are organized by groups and all configuration assistants in a group start running at the same time. The installer proceeds to the next configuration assistant outside of the group, only after all parallel tasks in a group complete successfully. The following example depicts a group of configuration tasks that are running in parallel. As depicted in the following graphic, a group of configuration tasks, Deploying Security Grants, Generating SOA Configuration Plan, and Updating Flexfield Configuration, are running in parallel and have all reached 10% completion.
Health Checker is a command line utility that performs a set of validation checks against an Oracle Fusion Applications environment. The validation checks are organized into groups, based on the purpose of the checks and when the checks are performed. When Health Checker runs, it uses a specific manifest file which performs the appropriate checks. Several health checks are called by Upgrade Orchestrator and all health checks can also be run manually. Health Checker provides a list of corrective actions for the checks that fail validation. The suggested corrective actions must be run manually to fix the issue before proceeding with the related activity, such as upgrading or patching activities.
Note that you should not run the Health Checker manifests that are located in the FA_ORACLE_HOME/lcm/hc/config/SaaS directory. If manifests in this directory are run, unexpected failures in the environment may occur.
The following topics describe the usage of Health Checker:
When you run Health Checker manually, you specify a manifest file which corresponds to the group, as described in Table A-6. The manifest files are located in the following directories:
Before upgrading your environment, the manifest files in the following location are from the previous release. Do not use these manifest files until after you upgrade:
FA_ORACLE_HOME/lcm/hc/config:
The manifest files in the following location are from the current release and must be used when running Health Checker before the upgrade:
REPOSITORY_LOCATION/installers/farup/Disk1/upgrade/config
Table A-6 Health Checker Manifest Files
| Manifest File | Host Requirements | Typical Usage of the Manifest |
|---|---|---|
|
GeneralSystemHealthChecks.xml |
Primordial, OHS, Midtier, DB |
Run this manifest any time. See Section A.2.2.5.1, "General System Health Checks." |
|
PreDowntimeUpgradeReadinessHealthChecks.xml |
Primordial, OHS, Midtier, DB |
Upgrade Orchestrator runs this manifest before the upgrade downtime. You can run this at any time. See Section A.2.2.5.2, "Pre-Down Time Upgrade Tasks." |
|
Release5to7PreUpgradeReadinessChecks.xml |
Primordial, OHS, Midtier, DB |
Upgrade Orchestrator runs this manifest during down time and before the upgrade starts, when performing the chained upgrade from Release 5 to Release 6 to Release 7. See Section A.2.2.5.3, "Pre-Upgrade Tasks Performed by Health Checker During Down Time." This manifest must be run only on the Release 5 environment and the |
|
DuringDowntimeUpgradeReadinessHealthChecks.xml |
Primordial, OHS, Midtier |
Upgrade Orchestrator runs this manifest during down time and before the upgrade starts. See Section A.2.2.5.3, "Pre-Upgrade Tasks Performed by Health Checker During Down Time." |
|
VitalSignsChecks.xml |
Upgrade Orchestrator runs this manifest during the upgrade. See Section A.2.2.5.10, "Vital Signs Check." |
|
|
PostUpgradeHealthChecks.xml |
Primordial, OHS, Midtier |
Upgrade Orchestrator runs this manifest after the upgrade. See Section A.2.2.5.4, "Post-Upgrade Tasks Performed by Health Checker." |
|
LanguagePackReadinessHealthChecks.xml |
Run this manifest before installing a language pack. See Section A.2.2.5.5, "Language Pack Readiness Health Checks." |
|
|
PostLanguagePackHealthChecks.xml |
Run this manifest after installing a language pack. See Section A.2.2.5.6, "Post Language Pack Health Checks." |
|
|
PatchingReadinessHealthChecks.xml |
Run this manifest before applying a patch. See Section A.2.2.5.7, "Patching Readiness Health Checks." |
|
|
PostPatchingHealthChecks.xml |
Run this manifest after applying a patch. See Section A.2.2.5.8, "Post Patching Health Checks." |
|
|
DataQualityChecks.xml |
Run this manifest to check the quality of data such as JAZN and seed data. Note that these checks may require significant processing time. See Section A.2.2.5.9, "Data Quality Check." |
Perform the following one-time setup steps on the database host and the OHS host for Health Checker.
Create a ZIP archive of the Health Checker framework that exists on the primordial host in REPOSITORY_LOCATION.
setenv APPLICATIONS_BASE APPLICATIONS_BASE
cd REPOSITORY_LOCATION/installers/farup/Disk1/upgrade
bin/hczip.py /any_scratch_directory/hc.zip --repoLoc $REPOSITORY_LOCATION
Use FTP or another method to transfer the hc.zip file to the DB or OHS host.
Create a directory where you want the Health Checker framework contents to reside. You must choose a separate directory that does not overlap with any provisioned components. This directory is referred to as HC_TOP in this section.
mkdir /u01/hcframework cd /u01/hcframework cp hc.zip /u01/hcframework unzip hc.zip
Refer to the appropriate section for the steps to run Health Checker, which is delivered in the REPOSITORY_LOCATION/installers/farup/Disk1/upgrade/bin directory as hcplug.sh (UNIX) and hcplug.cmd (Windows).
Note:
If you are running the PreDowntimeUpgradeReadinessHealthChecks.xml or PostUpgradeHealthChecks.xml manifests, you must also run the GeneralSystemHealthChecks.xml manifest.
Perform the following steps to run Health Checker on the primordial host.
Set the following environment variables:
APPLICATIONS_BASE: The directory that contains Oracle Fusion Applications. For example, if Oracle Fusion Applications is installed in /server01/APPTOP/fusionapps, then set the APPLICATIONS_BASE environment variable to /server01/APPTOP.
REPOSITORY_LOCATION: The directory where the repository is staged, SHARED_LOCATION/11.1.7.0.0/Repository.
FA_SCRIPTS_DOWNLOAD_DIR: The location of the PatchConflictManager.py utility, which you downloaded in Section 2.3.4, "Download and Unzip the Patch Conflict Manager Utility".
DOWNLOAD_PATCH_DIR: The location where you downloaded post-release patches in Section 2.3.6.3, "Download and Unzip Mandatory Post-Release 7 Patches".
Note that the following environment variables are set in the primordial host but the values come from the OHS host. For example, /u1/mw_home/Oracle_WT1/instances/CommonDomain_webtier does not exist on the primordial host and this path is a path on the OHS host. However, Health Checker requires this environment variable on the primordial host.
OHS_INSTANCE_ID: The OHS instance id being upgraded, such as ohs1.
WT_CONFIG_HOME: The Webtier instance configuration home, such as /u1/mw_home/Oracle_WT1/instances/CommonDomain_webtier.
OHS_HOST_NAME: The OHS host name, such as ohs_host.my.company.com.
Run Health Checker.
(UNIX) $REPOSITORY_LOCATION/installers/farup/Disk1/upgrade/bin/hcplug.sh -manifest REPOSITORY_LOCATION/installers/farup/Disk1/upgrade/config/manifest_name.xml -DlogLevel=FINEST (Windows) %REPOSITORY_LOCATION%\installers\farup\Disk1\upgrade\bin\hcplug.cmd -manifest REPOSITORY_LOCATION\installers\farup\Disk1\upgrade\config\manifest_name.xml -DlogLevel=FINEST
If Health Checker fails, follow the steps in Section A.2.2.4, "Troubleshoot Health Checker Failures."
Perform the following steps to run Health Checker on the MidTier host.
Set the following environment variables:
APPLICATIONS_BASE: The directory that contains Oracle Fusion Applications. For example, if Oracle Fusion Applications is installed in /server01/APPTOP/fusionapps, then set the APPLICATIONS_BASE environment variable to /server01/APPTOP.
REPOSITORY_LOCATION: The directory where the repository is staged.
IS_SECONDARY_NODE: A value of yes or no, to indicate whether the midtier node is secondary.
Run Health Checker.
(UNIX) $REPOSITORY_LOCATION/installers/farup/Disk1/upgrade/bin/hcplug.sh -hostType MIDTIER -manifest REPOSITORY_LOCATION/installers/farup/Disk1/upgrade/config/manifest_name.xml -DlogLevel=FINEST (Windows) %REPOSITORY_LOCATION%\installers\farup\Disk1\upgrade\bin\hcplug.cmd -hostType MIDTIER -manifest REPOSITORY_LOCATION\installers\farup\Disk1\upgrade\config\manifest_name.xml -DlogLevel=FINEST
If Health Checker fails, follow the steps in Section A.2.2.4, "Troubleshoot Health Checker Failures."
Perform the following steps to run Health Checker on the OHS or DB host.
For pre-down time checks, note the location where the PatchConflictManager.py utility was downloaded in Section 2.3.4, "Download and Unzip the Patch Conflict Manager Utility", because you must set the FA_SCRIPTS_DOWNLOAD_DIR environment variable as a pointer to this location in Step 2.
Set the following environment variables:
Required environment variables for the OHS host:
APPLICATIONS_BASE: HC_TOP, which was created in Step 3
REPOSITORY_LOCATION: The directory where the repository is staged
JAVA_HOME: The Java home.
WT_MW_HOME: The Webtier Middleware home directory that contains the oracle_common, webtier, and webgate homes.
WT_ORACLE_HOME: The Webtier Oracle home which is usually under the Webtier Middleware Home directory.
WT_CONFIG_HOME: The Webtier Config Home that contains the webtier instance, for example, /u01/oracle/mw_home/Oracle_WT1/instances/CommonDomain_webtier.
OHS_INSTANCE_ID: The OHS instance id being upgraded, such as ohs1.
UPGRADEOHS_PROP_FILE: Location for upgradeOHS.properties file. For example: /tmp/upgradeohs.properties.
RUPLITE_FOR_OHS_DIR: Directory for RUPLite for OHS webgate installer. For example: /u01/webgate/webgate_installer_REL7.
CURRENT_FA_RELEASE_VERSION: The current release, 11.1.7.0.0.
FA_SCRIPTS_DOWNLOAD_DIR: The location of the PatchConflictManager.py utility, which you downloaded in Section 2.3.4, "Download and Unzip the Patch Conflict Manager Utility".
DOWNLOAD_PATCH_DIR: The location where you downloaded post-release patches in Section 2.3.6.3, "Download and Unzip Mandatory Post-Release 7 Patches".
Required environment variables for the database host:
APPLICATIONS_BASE: HC_TOP, which was created in Step 3
REPOSITORY_LOCATION: The directory where the repository is staged
JAVA_HOME: The Java home.
ORACLE_HOME: The Oracle Database home directory.
PATH: The path to Oracle_home/bin.
LISTENER_NAME: The Oracle database listener name
ORACLE_SID: The Oracle database SID
TNS_ADMIN: The Oracle home admin directory, such as ORACLE_HOME/network/admin
LD_LIBRARY_PATH: $ORACLE_HOME/lib
GRID_HOME: On RAC configurations, set this to GRID_HOME. Otherwise set to ORACLE_HOME.
FA_SCRIPTS_DOWNLOAD_DIR: The location of the PatchConflictManager.py utility, which you downloaded in Section 2.3.4, "Download and Unzip the Patch Conflict Manager Utility".
DOWNLOAD_PATCH_DIR: The location where you downloaded post-release patches in Section 2.3.6.3, "Download and Unzip Mandatory Post-Release 7 Patches".
Run Health Checker and specify -hostType and the -jreLoc on this host. Note that -jreLoc is the same as the JAVA_HOME location for this host.
(UNIX) $REPOSITORY_LOCATION/installers/farup/Disk1/upgrade/bin/hcplug.sh -hostType [DB|OHS] -jreLoc location_of_Java -manifest REPOSITORY_LOCATION/installers/farup/Disk1/upgrade/config/manifest_name.xml -DlogLevel=FINEST [-logDir logfile_directory] (Windows) %REPOSITORY_LOCATION%\installers\farup\Disk1\upgrade\bin\hcplug.cmd -hostType [DB|OHS] -jreLoc location_of_Java -manifest REPOSITORY_LOCATION\installers\farup\Disk1\upgrade\config\manifest_name.xml -DlogLevel=FINEST [-logDir logfile_directory]
If Health Checker fails, follow the steps in Section A.2.2.4, "Troubleshoot Health Checker Failures."
If Health Checker finds an issue that must be corrected, the description of the required corrective action displays on the console, in the Health Checker log file, and in an HTML summary report. The log file and the HTML summary are located in APPLICATIONS_CONFIG/fapatch/logs/11.1.7.0.0/healthchecker
Health Checker generates a report named healthcheckplugin_actionsummary_timestamp.html, that displays the validation checks performed and their statuses. Review this report to determine whether any checks failed to validate and then manually perform the corrective actions for the failed checks.
After you resolve the issue that caused the error, start Health Checker again to run the failed tasks. You must rerun Health Checker until there are no more failed tasks.
There may be situations in which you want to run health checks manually, outside of orchestration. For example, you may want to run the pre-down time checks several weeks before you upgrade, so that you have time to fix any issues found by PreDowntimeUpgradeReadinessHealthChecks.xml.
Health Checker calls plug-ins to perform its tasks. This section describes which plug-ins run during the following phases of the installer process:
The following checks occur when you run Health Checker using the GeneralSystemHealthChecks.xml manifest.
Administration Servers and Managed Servers are Up
Confirms that all relevant Administration Servers and Managed Servers have a RUNNING status.
Certificate Expiry in Trust Keystore
Checks the expiration date for the certificates in the Trust key store and reports an error if the expiration date has passed or is within the next 90 days.
Credential Store Connectivity
Checks if a connection can be established to the credential store.
Credentials in Oracle Directory Services Manager (ODSM)
Verifies that a specific user, usually the PolicyRWUser user, is part of the cn=DirectoryAdminGroup.
Database Instance Connectivity
Checks if the database instance is up. For RAC databases, checks if all nodes are up.
DBMS_STATS Collection for MDS Schema in Oracle Fusion Applications Database
Confirms that DBMS_STATS has recently been run on the MDS schema in the Oracle Fusion Applications database. You must run DBMS_STATS on any schemas that are reported by Health Checker.
Deployed Applications are Up
Verifies that all deployed applications are up and running.
FAPatchManager Configuration
Checks if Oracle Fusion Applications Patch Manager is correctly configured, including the following validations:
Checks to see if FUSION_env.properties and ATGPF_env.properties are correct.
Checks for existence of the fapmgr.ini file in the environment.
Verifies registered products against the database.
Flexfields Metadata in the Flex Repository
Checks if there is a Flexfields metadata violation that indicates that the Extensible Flexfields has a UI Page defined that references a Flexfield Context which has not been associated with the corresponding Category or any of its parent Categories.
Fusion Applications Certification Matrix
Confirms the correct versions of installed components, according to the certification matrix.
Fusion Schema Connectivity
Validates the database connectivity to all Fusion schemas.
Hosts Name
Confirms that host names are correctly formatted in the /etc/hosts file. The /etc/hosts file is a network configuration file that associates IP addresses with host names and host alias names, if used. The following checks are performed by this plug-in:
The /etc/hosts file contains an entry for the IP address 127.0.0.1, followed by the name localhost.
The format of each host entry in /etc/hosts is IP_address canonical_hostname [aliases]. If the machine name is a logical host name and is different from the physical host name that is specified in /etc/sysconfig/network, the logical host name must be listed before the physical host. Ensure that the first entry in /etc/hosts, machine name (host name), and the value used in pod.properties, are identical.
If the machine name is the same as the physical host name, there is no need to check the order of the host names.
Identity and Policy Store LDAP
Verifies the connectivity to the identity store and policy store LDAP using identity store credentials.
Identity Store Connectivity using jps-config-jse.xml
Verifies that the idstore.ldap.provider in jps-config-jse.xml can be used to connect to the identity store.
IIR Configuration
Verifies that Fusion Informatica IR is set up properly.
INBOUND_CONNECT_TIMEOUT parameter in sqlnet.ora and listener.ora
Checks for recommended values in the INBOUND_CONNECT_TIMEOUT parameter in sqlnet.ora and listener.ora files on the database host.
Index Validity in Fusion Schema of Oracle Fusion Applications Database
Checks for unusable indexes in the Fusion Schema of the Oracle Fusion Applications database.
init.ora parameters
Verifies that the init.ora parameters are correct.
Invalid Objects
Checks for and reports any invalid objects.
JAZN Version in Oracle_Home Matches LDAP
Verifies that the JAZN version in system-jazn-data.xml is the same as the version in the policy store.
JVM Architecture, JDK platform Type, JAVA Version, and JDK Vendor
Verifies that the JDK version is valid. It also validates the JVM architecture, JDK platform type, and JDK vendor.
Listener Configuration
Verifies that the database listener configuration runs from the grid home on the DB host and also that no duplicate processes for the listener are running.
Local Port Range Value
Checks the local port range value in /proc/sys/net/ipv4/ip_local_port_range. The recommended value is 32768 61000. If the range is set to any value below 32768, a system process could potentially use a port that was assigned to one of the Managed Servers. Since RUP Installer requires all domains to be down, those ports are available for the system to use.
Mandatory Patches Have Been Applied
Verifies that mandatory patches have been applied.
MDS Schema Connectivity
Checks database connectivity for schemas that contain FUSION_MDS in their name.
Middleware Schema Connectivity
Checks database connectivity for all schemas except for FUSION_MDS schemas.
Multi-Tenant set-up in Fusion Schema of Oracle Fusion Applications Database
Ensures that only one enterprise is enabled in the database.
Node Manager Crash Recovery Is Set To True
Verifies the CrashRecoveryEnabled entry in nodemanager.properties is set for each host.
Node Managers are up and accessible
Checks if node managers for all hosts are running and are accessible.
OAM Configuration
Verifies the following information in Fusion_env.properties:
OAM_ADMIN_SERVER_HOST
OAM_ADMIN_SERVER_PORT
OAM_WEB_DOMAIN
OAM admin user credential from the credential store
ODI Repository URLs
Finds all jdbc connection URLs in the ODI repository and validates that they point to the same database as the database that is referenced in the DB_CONNECT_STRING parameter in Fusion_env.properties.
ODI supervisor credentials
Confirms the correct connection URLs exist in the ODI Repository.
OHS Instance Registration
Verifies that the OHS instance is registered in topology.xml.
OHS Process Status on OHS Using OPMN
Check if the OHS process is up on the OHS host.
OPatch Version in FA_ORACLE_HOME
Verifies that the version of OPatch is compatible with Oracle Fusion Applications. If an incompatible version of OPatch exists in FA_ORACLE_HOME, errors can occur while applying patches and running RUP Installer.
Open File Limit
Verifies the open file limit. RUP Installer uses multiple workers for uploading database content. The number of workers used dictates the open file limit setting for the machine where you run the RUP Installer. To understand how the number of workers are calculated and the requirement for the open file limit setting for the workers, see "Patching Database Artifacts" in the Oracle Fusion Applications Patching Guide. For more information, see "Increase the Open Files Limit" in the Oracle Fusion Applications Installation Guide.
Oracle Homes are Registered in the Central Inventory
Verifies that the Oracle Business Intelligence, Global Order Processing, Web Tier, and Web Tier Common Oracle home directories are registered for use by Oracle Fusion Applications.
ORACLE_COMMON Inventory Location on OHS
Verifies that the OH home and the Oracle Common home are pointing to the correct inventory location on OHS in WT_MIDDLEWARE_HOME/oracle_common/oraInst.loc.
OS Attributes
Validates the operating system name, architecture and versions.
Password Expiry For Critical Bind Users in LDAP
Verifies that the passwords for critical bind users are not locked and will not expire within the next three days.
Read Write Access to APPLICATIONS_BASE
Verifies that directory the APPLICATIONS_BASE directory has read-write access.
Remote OPMN Access
Verifies that the remote OPMN process is accessible.
Size and Contents of default-keystore.jks File in All Domains
Verifies that the size of the default-keystore.jks file for all domains is same as that of CommonDomain.
Taxonomy URL
Verifies the TAXONOMY_URL value, which is obtained from FUSION_env.properties.
User Administrator or Super User Role
Verifies that the owner of APPLICATIONS_BASE is the same as the user who is running Health Checker.
Virtual Hosts Wiring
Verifies that the host and port wirings in the APPLICATIONS_CONFIG/CommonDomain_webtier/config/OHS/ohs1/moduleconf/FusionVirtualHost_app.conf files are correct.
WSM-PM Application is Active
Verifies that the WSM-PM application is running on all SOA domains.
The following checks occur when Health Checker runs using the PreDowntimeUpgradeReadinessHealthChecks.xml manifest.
Base SOA Composites Exist
Verifies that all base SOA composites exist for the versions that are going to be upgraded by a patch.
Data Guard State
Checks if Data Recovery is enabled in the environment and that it is stopped before the upgrade.
Environment Properties on OHS
This plug-in verifies the properties used by the RUP Lite for OHS utility.
Free and Total Memory
Verifies that the primordial host has enough free memory for the upgrade. The required memory is calculated based on which domains and servers are configured to run on the host where the Health Checker is run.
Free Disk Space
Checks for free and usable disk space on the primordial and non-primordial Oracle Fusion Applications hosts.
HCM Workforce Reputation Offerings Shared Mount
If the environment is provisioned with HCM Workforce offerings, verifies if the environments have the mandatory shared directory and mount point configured.
Middleware Installer exists in Release Repository
Verifies that all Middleware installers exist in the repository.
No Locked ODI Objects or SES Objects Exist
Verifies that there are no locked objects in the FUSION_ODI and SES schemas.
No Patch Conflicts Exist
Runs the PatchConflictManager utility to remove conflicting patches.
WLS Edit Sessions and Unactivated Changes Exist
Verifies that no WLS edit sessions or unactivated changes exist.
OHS Process Status on OHS Using OPMN
Verifies that the OHS process is up and running on the OHS host.
Oracle Fusion Applications Release Version:
To install Release 7, the installed Oracle Fusion Applications version must be Release 6. This plug-in ensures that the installed version of Oracle Fusion Applications is 11g Release 6, (11.1.6.0.0).
Permissions For Temp Directory
Verifies that files in the temporary directory that match the pattern, /tmp/*pki*, are owned by the same user that starts servers.
Availability of ports for new Managed Servers
Verifies the availability of ports for managed servers that were added. This plug-in is available only in Release 7.
Properties for DB Host Upgrade
Verifies that the environment properties to be used for DB Host upgrade are valid.
Repository Integrity
Checks whether all required files are present in the repository and reports any missing files.
Seed Data For Potential Conflicts
Performs a set of validations to prevent potential seed data failures.
SES Schedules and Index Optimizer are Stopped/Disabled
Verifies that SES schedules and the index optimizer are stopped.
SOA Platform is Ready
Verifies whether the SOA platform is ready for each domain that is impacted by the contents of the upgrade.
Sessions holding 'library cache load lock' in Fusion Schema of Oracle Fusion Applications Database
Checks whether there are any database sessions that are holding a "library cache load lock" in the Fusion schema of the Oracle Fusion Applications database.
Total Memory and Swap
Verifies there is sufficient memory for upgrading. The memory requirement calculation is based on the domains and servers that are configured to run where Health Checker runs.
The following checks occur when Health Checker runs the DuringDowntimeUpgradeReadinessHealthChecks.xml manifest.
AD Admin Sessions, AutoPatch and Patch Manager Processes are Complete
Checks whether any AD Administration, AutoPatch or Patch Manager processes are running.
Credential Store Connectivity
Checks if a connection can be established to the credential store.
Data Guard State
Checks if Data Recovery is enabled in the environment and that it is stopped before the upgrade.
Database Instance Connectivity
Checks if the database instance is up. For RAC databases, checks if all nodes are up.
Database version
Checks if Oracle Database version is above the minimum required for Oracle Fusion Applications 11g Release 7 (11.1.7).
Database is Running and in Idle State
Verifies that no SQL sessions, jobs, or processes are running or are scheduled to be running against the database.
Free Memory and Swap
Identity and Policy Store LDAP
Verifies the connectivity to the identity store and policy store LDAP using identity store credentials.
Identity Store Connectivity using jps-config-jse.xml
Verifies that the idstore.ldap.provider in jps-config-jse.xml can be used to connect to the identity store.
Invalid Objects
Checks for and reports any invalid objects.
JAZN Version in Oracle_Home Matches LDAP
Verifies that the JAZN version in system-jazn-data.xml is the same as the version in the policy store.
Mandatory Patches Have Been Applied
Verifies that mandatory patches have been applied.
MDS Schema Connectivity in RUP1 Env
Checks database connectivity for schemas that contain FUSION_MDS in their name.
Middleware Schema Connectivity in RUP1 Env
Checks database connectivity for all schemas except for FUSION_MDS schemas.
Node Managers are down
Verifies Node Managers are down.
Administration Servers and Managed Servers are Down
Confirms that all relevant Administration Servers and Managed Servers are down.
The following checks occur when Health Checker runs the PostUpgradeHealthChecks.xml manifest.
AD Admin Sessions, AutoPatch and Patch Manager Processes are Complete
Checks whether any AD Administration, AutoPatch or Patch Manager processes are running.
Data Guard State
Checks if Data Recovery is enabled in the environment and that it is stopped before the upgrade.
Database version
Checks if Oracle Database version is above the minimum required for Oracle Fusion Applications 11g Release 7 (11.1.7).
Installed Languages are Upgraded to Release
Checks if a language pack has been upgraded to the current release or needs to be upgraded to the current release.
JAZN Conflicts
Validates the results of the JAZN analysis reports for each stripe to find any potential conflicts or deletions that were not patched automatically by the installer.
Locked ODI Objects or SES Objects
Verifies that there are no locked objects in the FUSION_ODI and SES schema.
Permissions For Temp Directory
Verifies that files in the temporary directory that match the pattern, /tmp/*pki*, are owned by the same user that starts servers.
SOA Composites in the Repository are Deployed
Verifies that the SOA composites in the repository were deployed by the upgrade.
SOA Platform is Ready
Verifies whether the SOA platform is ready for each domain that is impacted by the contents of the upgrade.
WLS Edit Sessions and Unactivated Changes
Verifies that no WLS edit sessions or unactivated changes exist.
The following checks occur when Health Checker runs the LanguagePackReadinessHealthChecks.xml manifest. You typically run this manifest before you install a language pack. For more information, see "Installing and Maintaining Oracle Fusion Applications Languages" in Oracle Fusion Applications Administrator's Guide.
AD Admin Sessions, AutoPatch and Patch Manager Processes are complete
Checks whether any AD Administration, AutoPatch or Patch Manager processes are running.
All Installed Languages are Upgraded to Release
Checks if a language pack has been upgraded to the current release or needs to be upgraded to the current release.
Database is Running and in Idle State
Verifies that no SQL sessions, jobs, or processes are running or are scheduled to be running against the database.
Repository Integrity
Checks whether all required files are present in the repository and reports any missing files.
SOA Platform is Ready
Verifies whether the SOA platform is ready for each domain that is impacted by the contents of the upgrade.
The following checks occur when Health Checker runs the PostLanguagePackHealthChecks.xml manifest. You typically run this manifest after you install a language pack. For more information, see "Installing and Maintaining Oracle Fusion Applications Languages" in the Oracle Fusion Applications Administrator's Guide.
JAZN Conflicts
Validates the results of the JAZN analysis reports for each stripe to find any potential conflicts or deletions that were not patched automatically by the installer.
The following checks occur when Health Checker runs the PatchingReadinessHealthChecks.xml manifest. You typically run this manifest before applying a patch. For more information, see "Step 7 Prepare the System" in the Oracle Fusion Applications Patching Guide.
AD Admin Sessions, AutoPatch and Patch Manager Processes are complete
Checks whether any AD Administration, AutoPatch or Patch Manager processes are running.
Base SOA Composites Exist
Verifies that all base SOA composites exist for the versions that are going to be upgraded by a patch.
Database version
Checks if Oracle Database version is above the minimum required for Oracle Fusion Applications 11g Release 7 (11.1.7).
Database is Running and in Idle State
Verifies that no SQL sessions, jobs, or processes are running or are scheduled to be running against the database.
IPM server status
No Locked ODI Objects or SES Objects Exist
Verifies that there are no locked objects in the FUSION_ODI or SES schema.
WLS Edit Sessions and Unactivated Changes Exist
Verifies that no WLS edit sessions or unactivated changes exist.
SOA Platform is Ready
Verifies whether the SOA platform is ready for each domain that is impacted by the contents of the upgrade.
The following checks occur when Health Checker runs the PostPatchingHealthChecks.xml manifest. You typically run this manifest after applying a patch. For more information, see "Step 11 Run Health Checker for Post Patching Health Checks" in the Oracle Fusion Applications Patching Guide
AD Admin Sessions, AutoPatch and Patch Manager Processes are complete
Checks whether any AD Administration, AutoPatch or Patch Manager processes are running.
JAZN Conflicts
Validates the results of the JAZN analysis reports for each stripe to find any potential conflicts or deletions that were not patched automatically by the installer.
No Locked ODI Objects or SES Objects Exist
Verifies that there are no locked objects in the FUSION_ODI schema.
WLS Edit Sessions and Unactivated Changes Exist
Verifies that no WLS edit sessions or unactivated changes exist.
The Validating JAZN Policy Data check occurs when Health Checker runs the DataQualityChecks.xml manifest.
The following checks occur when Health Checker runs the VitalSignsChecks.xml manifest.
Database Instance Connectivity
Checks if the database instance is up. For RAC databases, checks if all nodes are up.
Fusion Schema Connectivity
Validates the database connectivity to all Fusion schemas.
Identity and Policy Store LDAP
Verifies the connectivity to the identity store and policy store LDAP using identity store credentials.
Identity Store Connectivity using jps-config-jse.xml
Verifies that the idstore.ldap.provider in jps-config-jse.xml can be used to connect to the identity store.
MDS Schema Connectivity
Checks database connectivity for schemas that contain FUSION_MDS in their name.
Middleware Schema Connectivity
Checks database connectivity for all schemas except for FUSION_MDS schemas.
Verify All Admin Servers and Managed Servers are Up
Verifies that all Administration and Managed Servers are up.
The Health Checker utility offers a method for you to manage which health checks run on your environment. For example, you may want to exclude a health check that is related to a known issue in an environment. You can also add a new check to an existing Health Checker plug-in, if needed. The configuration parameters for Health Checker are stored in the REPOSITORY_LOCATION/installers/farup/Disk1/upgrade/config/healthchecks.xml file. You are not allowed to edit this file. If you want to override any configuration parameters or exclude certain plug-ins from running, you can create configuration override files. Health Checker first loads the configuration parameters that are stored in healthchecks.xml and then it considers the configuration override files.
This section describes the following topics related to managing Health Checker sessions:
The first step in overriding the standard checks run by Health Checker is to create one or more override files. To create an override file, copy the appropriate override template to the override directory, which defaults to location SHARED_UPGRADE_LOCATION/healthchecker/POD_NAME, and rename this file to eliminate the .template extension. The following templates are located in the ORCH_LOCATION/fusionapps/applications/lcm/hc/config directory. ORCH_LOCATION is where orchestration.zip is unzipped, as described in Section 2.3.7, "Unzip Orchestration.zip".
ALL_overrides.xml.template
DB_overrides.xml.template
MIDTIER_overrides.xml.template
OHS_overrides.xml.template
PRIMORDIAL_overrides.xml.template
Select the template that corresponds to the host type for which you want to create the overrides. For example, if you want to create overrides for the primordial host, use PRIMORDIAL_overrides.xml. If the override applies to all hosts, use ALL_overrides.xml.
The default location for override files is SHARED_UPGRADE_LOCATION/healthchecker/POD_NAME.
To override configuration parameters within an override file, uncomment the XML portion of the override file, and customize the override file to meet your requirements. Remove all values from the override file except for the values that you want to exclude. To disable a check, add disabled=true to the check. To add a check, add the value to the override file.
This example shows how to customize the list of URIs that are verified by Health Checker. The following steps describe this customization:
Copy the template for the override file.
cp REPOSITORY_LOCATION/installers/farup/Disk1/upgrade/config/ALL_overrides.xml.template SHARED_UPGRADE_LOCATION/healthchecker/POD_NAME/ALL_overrides.xml
Uncomment the XML portion of the override file.
The original override file looks as follows:
<!-- <checks category="context_root_locations"> <check value="/console"/> <check value="/soa-infra"/> <check value="/wsm-pm"/> <check value="/apm"/> <check value="/setup"/> <check value="/helpPortal"/> <check value="/fndSetup"/> <check value="/homePage"/> </checks> -->
After removing the XML comment lines, <!--, the -->, the override file now looks as follows:
<checks category="context_root_locations"> <check value="/console"/> <check value="/soa-infra"/> <check value="/wsm-pm"/> <check value="/apm"/> <check value="/setup"/> <check value="/helpPortal"/> <check value="/fndSetup"/> <check value="/homePage"/> </checks>
Remove all rows except those that you want to exclude. In this example, you do not want Health Checker to validate the URI for soa-infra and you want to add a validation for myuri. To disable a check, add disabled="true" to the check. To add a URI to be checked, add the URI to the override file. The override file now looks as follows:
<checks category="context_root_locations"> <check value="/soa-infra" disabled="true"/> <check value="/myuri"/> </checks>
To disable a plug-in, you must first find its display name (from the HTML report), its class name (from the log file), or its ID (from the manifest). The following example displays how a plug-in is defined in a Health Checker manifest file:
<plugin id="TotalMemoryCheck" description="Verifying Total Memory and Swap" invoke="" plugin.class="oracle.check.sys.TotalMemCheckPlugin"
The following example depicts how you can override the plug-in the override file. This example shows the display name, class name, and ID for the plug-in, but only one of these is required. Note that excluded plug-ins must be listed under the "exclude" category.
<checks category="exclude"> <check name="TotalMemoryCheck"/> <check name="Verifying Total Memory and Swap"/> <check name="oracle.check.sys.TotalMemCheckPlugin"/> <check name="TotalMemCheckPlugin"/>
To prevent a plug-in timeout while Health Checker runs, you can create an override file to specify a longer timeout. You must know the plug-in class name, and the timeout value in seconds to modify the value. You can find the plug-in class name in the Health Checker manifest. In the following example, the plug-in class name for the Verify DataSource connectivity check is oracle.check.apps.VerifyDSConnectivity.
GeneralSystemHealthChecks.xml- plugin id="DSStatusPlugin" GeneralSystemHealthChecks.xml- description="Verify DataSource connectivity" GeneralSystemHealthChecks.xml- invoke="" GeneralSystemHealthChecks.xml: plugin.class="oracle.check.apps.VerifyDSConnectivity" GeneralSystemHealthChecks.xml- class.path="$HC_LOCATION/lib/precheckplugin.jar; GeneralSystemHealthChecks.xml- $HC_LOCATION/lib/hccommon.jar" GeneralSystemHealthChecks.xml- stoponerror="false"/>
To find the current timeout value, open the healthchecker log file and find the portion of the log that was produced by the plug-in. The log includes the current timeout value, as shown in the following examples:
[2013-08-08T22:35:42.791+00:00] [healthcheckplug] [NOTIFICATION] [] [oracle.healthcheckplug] [tid: 10] [ecid: 0000K1W4R2R3v1G5IzXBif1I11oQ000000,0] Using default timeout of 120 seconds [2013-08-08T22:35:17.877+00:00] [healthcheckplug] [NOTIFICATION] [] [oracle.healthcheckplug] [tid: 10] [ecid: 0000K1W4R2R3v1G5IzXBif1I11oQ000000,0] [SRC_CLASS: oracle.check.common.util.Utils] [SRC_METHOD: getTimeout] Timeout for VerifyDSConnectivity is 901 seconds
Perform the following steps to modify the timeout value.
Create the override file as described in Section A.2.2.6.1, "Create Override Files".
Go to the timeout_seconds section as shown in the following example.
<!-- Timeout, used by plugins for running external commands or wlst scripts or ... -->
<checks category="timeout_seconds">
<check name="VerifyDSConnectivity" value="600"/>
<check name="LdapDataQualityCheckPlugin" value="1800"/>
<check name="ContextRootCheckPlugin" value="1800"/>
</checks>
If the plug-in is already listed in this section, set the new timeout value in seconds. If the plug-in is not listed, add it.
In the following example, the time out for Verify DataSource connectivity (oracle.check.apps.VerifyDSConnectivity) is set to 45 minutes (2700 seconds).
<checks category="timeout_seconds">
<check name="VerifyDSConnectivity" value="600"/>
<check name="LdapDataQualityCheckPlugin" value="1800"/>
<check name="ContextRootCheckPlugin" value="1800"/>
<!-- Either of the two lines below changes the timeout to 2700 -->
<check name="VerifyDSConnectivity" value="2700"/>
<check name="oracle.check.apps.VerifyDSConnectivity" value="2700"/>
</checks>
The RUP Lite for OVM utility addresses the differences between a newly provisioned Oracle VM environment on the latest release and an Oracle VM environment provisioned in a previous release. You run RUP Lite for OVM only if you are running Oracle Fusion Applications in an Oracle VM environment that was created from the official releases of Oracle VM templates for Oracle Fusion Applications Release 2 (11.1.2) and higher. This utility is not applicable for any Oracle VM environments that are created using other methods.
The following steps provide an overview of how Upgrade Orchestrator supports RUP Lite for OVM when upgrading from Release 5 to Release 6 to Release 7. Plug-ins for both Release 6 and Release 7 are included and shared plug-ins run only once.
Note that log files for RUP Lite for OVM are located under the location from where you are running RUP Lite for OVM. An example location for running RUP Lite for OVM in offline mode follows:
/u01/lcm/rupliteovm/output/logs/11.1.7.0.0/mycompany.com/rupliteoffline.log
Table A-7 Orchestration of RUP Lite for OVM - Release 5 to Release 7 Upgrade
| Description | Step Support | For More Information |
|---|---|---|
|
Copy the Release 6 |
Pre-Upgrade Step |
Step 1, Section 2.4.2.2.1, "Prepare RUP Lite for OVM for Release 6" |
|
Copy the Release 7 |
Pre-Upgrade Step |
Step 1, Section 2.4.2.2.2, "Prepare RUP Lite for OVM for Release 7" |
|
Configure the properties for each release Run RUP Lite for OVM in wallet mode for each release |
Pre-Upgrade Step |
|
|
Run RUP Lite for OVM Release 6 in validate mode Install Release 6 Run RUP Lite for OVM in offline mode Run RUP Installer for Release 6 Run RUP Lite for OVM in online mode |
Upgrade Orchestrator |
|
|
Run RUP Lite for OVM in post-root mode for Release 6 |
Pause Point |
Section 4.4.7, "Run RUP Lite for OVM in Post-Root Mode for Release 6" |
|
Run RUP Lite for OVM Release 7 in validate mode Install and upgrade Release 7 |
Upgrade Orchestrator |
|
|
Run RUP Lite for OVM in pre-root mode |
Pause Point |
Section 4.4.6, "Run RUP Lite for OVM in Pre-Root Mode for Release 7" |
|
Run RUP Lite for OVM in offline mode Run RUP Installer for Release 7 Run RUP Lite for OVM in online mode |
Upgrade Orchestrator |
|
|
Run RUP Lite for OVM in post-root mode |
Pause Point |
Section 4.4.8, "Run RUP Lite for OVM in Post-Root Mode for Release 7" |
RUP Lite for OVM implements several plug-ins that are designed specifically for Oracle VM environments. Each plug-in determines which nodes it needs to run on and in which mode it must run. Table A-8 describes the plug-ins that are included in RUP Lite for OVM in offline mode.
Table A-8 Offline Plug-ins for RUP Lite for OVM
| Plug-in Name | Mandatory | Description |
|---|---|---|
|
ValidateEnvironment |
Yes |
Checks if the node is a valid Oracle VM node. This plug-in always runs and has no properties. |
|
SetupCredentials |
Yes |
Prompts for credentials and stores the results in a secure manner for other plug-ins to use. This plug-in always runs and only prompts for secure properties that are needed by other plug-ins that will run. If a plug-in does not run on the current node or is disabled, then its properties are not requested. |
|
UpdateResolvConf |
No |
Adds DNS name servers, search domains, and other options by updating |
|
ApplyMemorySettings |
No |
This plug-in runs only on the Note that values that are higher in the environment compared to the reference values are not changed. Only lower values are increased. |
|
GenerateOptimizedQueryPlans |
Yes |
Generates optimized query plans for Oracle MDS queries. |
|
DisableSearchUI |
Yes |
Disables the global search UI for Oracle Fusion Applications. |
|
UpdateFusionIIRDiag |
Yes |
Updates the |
|
DisableWebchat |
Yes |
Performs the steps to disable Webchat. |
Table A-9 describes the plug-ins that are included in RUP Lite for OVM in online mode.
Table A-9 Online Plug-ins for RUP Lite for OVM
| Plug-in Name | Mandatory | Description |
|---|---|---|
|
ValidateEnvironment |
Yes |
Checks if the node is a valid Oracle VM node. This plug-in always runs and does not have any properties. |
|
SetupOnlineCredentials |
Yes |
Prompts for credentials for online plug-ins and stores the results in a secure manner for other plug-ins to use. This plug-in always runs and only prompts for secure properties that are needed by other plug-ins that will run. If a plug-in does not run on the current node or is disabled, then its properties are not requested. You are prompted for the password twice. |
|
DeployECSF |
Yes |
Deploys ECSF artifacts that are not yet deployed, such as search objects, search categories, and index schedules. |
|
DisableWebchatConnections |
Yes |
Disables Webchat WebCenter connections. |
|
ConfigureBIEmailDelivery |
Yes |
Enables outbound email communication of BI Delivery reports |
The RUP Lite for OHS utility manages the steps required to update WebGate, OHS, and ORACLE_COMMON. The following steps are performed by RUP Lite for OHS to accomplish this upgrade:
Stop Oracle Process Manager and Notification Server (OPMN) processes and start the OPMN server.
Apply OPatches from the repository to WebGate, OHS, and ORACLE_COMMON.
Apply manually downloaded OPatches to WebGate, OHS, and ORACLE_COMMON.
Update the OHS configuration files.
Apply OHS settings changes.
Start the OPMN server process.
Reassociate OHS to the Common Domain.
Start the OHS instance.
The RUP Lite for BI utility automates changes to BIInstance configurations files required for Oracle Business Intelligence after upgrading.