8 Configuring High Availability
About High Availability Configurations in Oracle AVDF
You can configure pairs of Database Firewalls or pairs of Audit Vault Servers, or both, to provide a high-availability system architecture. These are known as resilient pairs. For the Database Firewall, the resilient pair configuration described in this chapter applies to Database Activity Monitoring (DAM) mode only. See "The Database Firewall" for more information on DAM and DPE (Database Policy Enforcement) modes.
In a resilient pair of Audit Vault Servers, the primary Audit Vault Server performs all server functions. Audit and configuration data are copied from the primary to the secondary Audit Vault Server. The UI is not available on the secondary Audit Vault Server, so if you attempt to access the UI on the secondary server, you will be redirected to the UI on the primary server.
In a resilient pair of Database Firewalls, both primary and secondary Database Firewalls:
-
Receive the same span traffic
-
Have the same configuration (which the Audit Vault Server synchronizes). This is the configuration of secured targets, enforcement points, policies, and other monitoring settings, not the Database Firewall's system configuration (which is set on the system page of the Database Firewall console, and is not synchronized).
-
Create log files according to the policy applied
-
Send out alerts to the Audit Vault Server. The Audit Vault Server then sends only the alerts from the primary Database Firewall.
The Audit Vault Server collects traffic logs from the primary Database Firewall. If there is a time gap in the audit data from the primary Database Firewall, possibly due to a reboot of this Database Firewall, then the Audit Vault Server collects traffic log files from the secondary Database Firewall. The Audit Vault Server then deletes all the traffic log files from both Database Firewalls.
The Audit Vault Server controls the state of the resilient pair of Database Firewalls. There is no communication between Database Firewalls in a resilient pair. If the Audit Vault Server is unable to contact the primary Database Firewall for an extended period of time, the Audit Vault Server collects the log files from the secondary Database Firewall and promotes the secondary Database Firewall to be the primary (so the new primary firewall starts sending out real-time alerts).
Figure 8-1 shows a pair of Database Firewalls being used to protect a single database.
Figure 8-1 A High Availability Pair of Database Firewalls Protecting a Single Secured Target
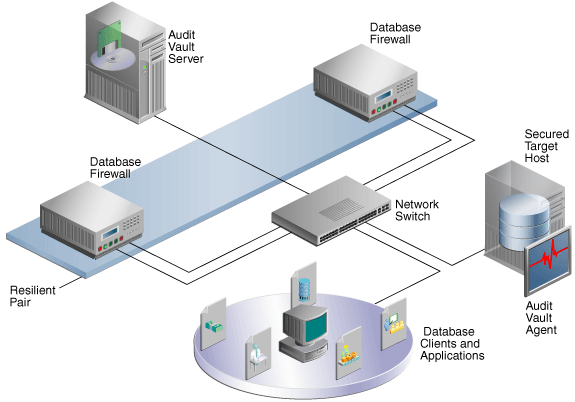
Description of ''Figure 8-1 A High Availability Pair of Database Firewalls Protecting a Single Secured Target''
Figure 8-2 shows a pair of Audit Vault Servers and a pair of Database Firewalls in high availability mode.
Figure 8-2 Pairs of Audit Vault Servers and Database Firewalls in High Availability Mode
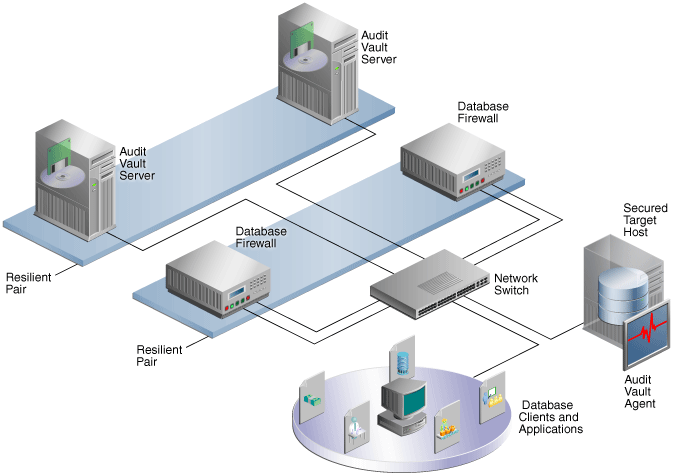
Description of ''Figure 8-2 Pairs of Audit Vault Servers and Database Firewalls in High Availability Mode''
Configuring a Resilient Pair of Audit Vault Servers
-
Prerequisites for Configuring a Resilient Pair of Audit Vault Servers
-
Step 3: Start High Availability Pairing of the Audit Vault Servers
-
Checking the High Availability Status of an Audit Vault Server
-
Updating Audit Vault Agents After Pairing Audit Vault Servers
About Pairing Audit Vault Servers
When you pair two Audit Vault Servers, designating one as the primary and the other as the secondary server, all data and configuration in the primary server (with the exception of network settings) is automatically copied to, and thereafter synchronized with, the secondary server.
After configuring the resilient pair of Audit Vault Servers, do all configuration tasks on the primary server only. This includes tasks such as deploying the Audit Vault Agent, setting up secured targets and hosts, and adding Database Firewalls and enforcement points.
Remember that if you are deploying Database Firewalls, and you configure a resilient pair of Audit Vault Servers, you must provide the server certificate and IP address of both the primary and secondary Audit Vault Server to each Database Firewall. See "Specifying the Audit Vault Server Certificate and IP Address" for instructions.
If you have deployed Audit Vault Agents before pairing Audit Vault Servers, you should manually update those agents after pairing. See "Updating Audit Vault Agents After Pairing Audit Vault Servers".
See also: "Handling a Failover of the Audit Vault Server Pair".
Prerequisites for Configuring a Resilient Pair of Audit Vault Servers
The following are prerequisites for configuring a pair of Audit Vault Servers:
-
Ensure that both the primary and secondary Audit Vault Servers have the same amount of disk space.
-
Do the initial system configuration tasks for both primary and secondary Audit Vault Servers. See "Specifying Initial System Settings and Options (Required)".
Step 1: Configure the Secondary Audit Vault Server
In this procedure, the secondary or standby server is called Server2, and the primary server is called Server1.
To configure Server2, the secondary server:
-
Copy the server certificate from Server1 (the primary):
-
Log in to Server1 as an administrator.
-
In the Settings tab of Server1, from the Security menu, click Certificate.
-
Copy the certificate.
-
-
In another browser window, log in to Server2 as a super administrator.
-
In the Server2 console, click the Settings tab.
-
From the System menu, select High Availability.
-
In the Peer System IP Address field, enter the IP address of Server1.
-
In the Peer System Certificate field, paste the certificate of Server1.
-
Click Save.
Step 2: Configure the Primary Audit Vault Server
In this procedure, the primary server is called Server1, and the secondary or standby server is called Server2.
To configure Server1, the primary server:
-
Copy the server certificate from Server2 (the secondary):
-
Log in to Server2 as an administrator.
-
In the Settings tab of Server1, from the Security menu, click Certificate.
-
Copy the certificate.
-
-
In another browser window, log in to Server1 as a super administrator.
-
In the Server1 console, click the Settings tab.
-
From the System menu, select High Availability.
-
Select the checkbox Configure this system as the Primary server.
-
In the Peer System IP Address field, enter the IP address of Server2.
-
In the Peer System Certificate field, paste the certificate of Server2.
-
Click Save.
When you are ready to start the pairing of Server1 and Server2, go to "Step 3: Start High Availability Pairing of the Audit Vault Servers".
Step 3: Start High Availability Pairing of the Audit Vault Servers
You initiate high availability pairing at the primary server (Server1). This will take a few minutes, and once it is complete, the secondary server will no longer have a console UI.
Note: After completing this procedure, do all configuration tasks on the primary server only. This includes tasks such as deploying the Audit Vault Agent, setting up secured targets and hosts, and adding Database Firewalls and enforcement points. The console UI of Server2 (the standby) will be unavailable and you will be redirected to Server1.
To initiate high availability pairing at the primary server (Server1):
-
Log in to Server1 as a super administrator.
-
In the Server1 console, click the Settings tab.
-
From the System menu, click High Availability.
-
Be sure the checkbox Configure this system as the Primary server is selected.
-
Click Save.
-
Click Make Primary.
The embedded Oracle Database is restarted and the console UI is temporarily unavailable. After this process is complete, this Audit Vault Server becomes the primary server.
-
If you deployed Audit Vault Agents before doing this procedure, manually update those agents. See "Updating Audit Vault Agents After Pairing Audit Vault Servers".
This step is necessary in order for those Audit Vault Agents to be recognized in the event of a failover.
Checking the High Availability Status of an Audit Vault Server
To check the high availability status of an Audit Vault Server:
-
In the Audit Vault Server console, click the Settings tab.
-
From the System menu, click Status.
Check the High Availability Status. The values are:
-
Standalone - This server has no partner server.
-
Primary - This server is currently the primary server.
-
Role Conflict - This primary server has failed over and can no longer be used to collect data.
To see the IP address and certificate of the other (peer) server in a paired system, in the System menu, click High Availability.
-
Updating Audit Vault Agents After Pairing Audit Vault Servers
In a high availability pair of Audit Vault Servers, the secondary server becomes the primary in the event of a failover. If you deployed Audit Vault Agents before you did the high availability pairing of the Audit Vault Servers, after a failover, the agent status in the new primary server is UNREACHABLE. To avoid this scenario, manually update previously deployed Audit Vault Agents after pairing Audit Vault Servers.
To manually update an Audit Vault Agent after pairing Audit Vault Servers:
-
On the host machine, kill the agent process:
kill -9agent_process_id -
Remove the file
agent.lckin the directoryAgent_Home/av/conf. -
Download the new
agent.jarfrom the new primary Audit Vault Server, and copy it to theAgent_Homedirectory on the host machine. -
In the
Agent_Homedirectory run:java-jar agent.jar -
Restart your audit trails.
Handling a Failover of the Audit Vault Server Pair
During normal operation, the system periodically checks the availability of the primary Audit Vault Server in the resilient pair. If the primary Audit Vault Server becomes unavailable, the system automatically fails over to the secondary Audit Vault Server after a 10 minute delay. The delay prevents a failover due to a reboot of the primary server.
In the event of a failover, the secondary server becomes a standalone Audit Vault Server. You must do the following to configure this standalone serve, and repeat the high availability pairing:
-
On the standalone server, configure the network and services settings (for example DNS settings). See "Specifying the Audit Vault Server System Settings".
-
On the standalone server, manually mount any remote filesystems (NFS shares) defined as archive locations, using this AVCLI command:
ALTER REMOTE FILESYSTEMfilesystem_nameMOUNTSee "ALTER REMOTE FILESYSTEM" for details.
-
Disconnect the failed server and replace it. The replacement server can now be configured as the new secondary server.
-
Follow the configuration steps again to pair the two Audit Vault Servers. See "Configuring a Resilient Pair of Audit Vault Servers".
Configuring a Resilient Pair of Database Firewalls
About Configuring a Resilient Pair of Database Firewalls
The procedure described here applies to a Database Firewall in DAM mode only.
-
Before you designate two Database Firewalls as a resilient pair, do the initial configuration tasks for each of them. See "Configuring the Database Firewall".
-
There must be no enforcement points configured on either of the Database Firewalls that you plan to pair. Be sure to delete all enforcement points on both Database Firewalls before creating a resilient pair.
If You Configure a Resilient Pair of Audit Vault Servers
If you have also configured a resilient pair of Audit Vault Servers, remember you must provide each Audit Vault Server's IP address and certificate to each Database Firewall in your system. See "Specifying the Audit Vault Server Certificate and IP Address".
Configuring a Resilient Pair of Database Firewalls
To configure a resilient pair of Database Firewalls:
-
Log in to the Audit Vault Server console as an administrator.
If you have defined a resilient pair of Audit Vault Servers, use the primary server's console.
-
Select the Firewalls tab.
-
In the Firewalls menu, select Resilient Pair.
-
In the Primary and Secondary fields, select the primary and secondary firewalls you want to use in this pair.
Swapping Roles in a Resilient Pair of Database Firewalls
Follow this procedure if you need to switch the roles of the primary and secondary Database Firewalls in a resilient pair.
To swap the roles of a resilient pair of Database Firewalls:
-
Log in to the Audit Vault Server console as an administrator.
If you have defined a resilient pair of Audit Vault Servers, use the primary server's console.
-
Select the Firewalls tab.
-
In the Firewalls menu, select Resilient Pair.
-
Select the resilient pair you want, and then click Swap.
Breaking (Un-pairing) a Resilient Pair of Database Firewalls
Use this procedure if you need to break (or un-pair) a resilient pair of Database Firewalls.
To break a resilient pair of Database Firewalls:
-
Log in to the Audit Vault Server console as an administrator.
If you have defined a resilient pair of Audit Vault Servers, use the primary server's console.
-
Select the Firewalls tab.
-
In the Firewalls menu, select Resilient Pair.
-
Select the resilient pair you want, and then click Break.