5 Creating Audit Policies for Oracle Databases
-
Retrieving and Modifying Audit Settings from an Oracle Database
-
Creating Additional Audit Policy Settings for an Oracle Database
About Audit Policies
Using the Audit Vault Server console, you can retrieve audit policies from Oracle database secured targets. You can then modify the policies or create new ones, and then provision them to the Oracle databases. You can retrieve and modify the following types of Oracle Database audit policies.
-
SQL statements
-
Schema objects
-
Privileges
-
Fine-grained auditing
-
Capture rules (for redo log file activities)
Note:
Although Oracle AVDF can collect data from the v$unified_audit_trail in Oracle Database 12c, Oracle AVDF cannot retrieve or provision unified audit policies.General Steps for Creating Audit Policies for Oracle Databases
In general, to create audit policies for Oracle databases, you perform the following steps as described in this chapter:
-
Retrieve the current audit policy settings from the secured target Oracle database, and specify which of the current settings are needed.
-
If necessary, define more audit policy settings to add to the needed settings.
-
Provision the audit policy to the secured target database. The policy settings you specified as needed, and the new ones you created, then become the policies in use in the database.
Retrieving and Modifying Audit Settings from an Oracle Database
Understanding the Columns on the Audit Settings Page
Each time you retrieve the audit settings from a secured target Oracle database, you see the state of the database audit settings at that point in time. The Audit Settings page in the Audit Vault Server (in the Policy tab) shows an overview of the audit settings in use at secured target Oracle Databases, and shows any differences between those and the settings you have set as needed in your Oracle AVDF audit policies for those databases. You can then specify which of the current settings are needed.
Table 5-1 describes the columns shown in the Audit Settings Page.
Table 5-1 Fields Under Apply Audit Settings in the Audit Settings Page
| Column | Description |
|---|---|
|
Target Name |
Name of the secured target |
|
In Use |
Number of audit settings in use in the secured target |
|
Needed |
Number of audit settings you (the auditor) specified as needed |
|
Problem |
The difference between the audit settings in use at the database and the number specified as needed in your Oracle AVDF audit policy for this database. If this number is greater than zero, new audit settings may have been created at the database since you last provisioned the audit policy from Oracle AVDF. You may also have selected more audit settings as needed or not needed since you last provisioned the audit policy. To resolve the problem, you can specify whether new audit settings are needed and/or provision the policy again. This brings the number in the Problem column back to zero. |
|
Last Retrieved |
The time that the audit information for the selected database was last retrieved |
|
As Provisioned |
The time that the audit settings were last provisioned to the database from Oracle AVDF |
Retrieving Audit Settings from an Oracle Database
To retrieve audit settings from an Oracle Database secured target:
-
Click the Policy tab.
By default, the Audit Settings page appears. A summary of audit settings at this point in time is displayed for that secured target. For each secured target, this page lists the status of the audit policies. See "Understanding the Columns on the Audit Settings Page".
-
From the Target Name column, select the check boxes for the secured target databases you want.
You can only see the Oracle database secured targets to which you have access.
Note: Audit trails and audit policy management are not supported for Oracle Database 9i.
-
Click the Retrieve Audit Settings button.
To check the status of the retrieval, click the Settings tab, then under the System menu, click Jobs. When the audit settings retrieval is complete, the Audit Settings page is refreshed with new data.
Specifying Which Audit Settings Are Needed
After you retrieve the audit settings from the secured target Oracle database, you can view and modify them as needed. Remember that you are modifying audit settings in use at the time you retrieved them. If you think they may have changed, you should retrieve them again. See "Retrieving Audit Settings from an Oracle Database".
-
In the Audit Settings page, click the name of the secured target database you want.
The Audit Settings Overview page for this secured target appears, showing the audit settings in use and marked as needed for these audit types:
-
Statement
-
Object
-
Privilege
-
FGA
-
Capture Rule
-
-
To update settings for any audit type, click its link, for example, Statement.
The Audit Settings page for that audit type appears, listing the current audit settings. The second column displays a problem icon if there is a difference between the setting at the secured target database, and the setting in Oracle AVDF.
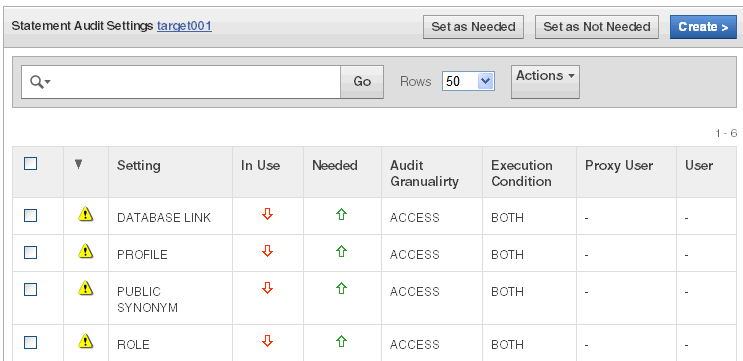
Description of the illustration ''statement_audit_settings.gif''
-
Select the checkboxes for each audit setting you determine is needed, then click Set as Needed.
-
To remove audit settings, select the checkboxes for the ones you want to remove, then click Set as Not Needed.
-
To create new audit settings for this audit type (for example, Statement), click Create. See "Creating Additional Audit Policy Settings for an Oracle Database".
Creating Additional Audit Policy Settings for an Oracle Database
About Creating Audit Policy Settings
Once you have retrieved audit policy settings from the secured target Oracle database, and selected which of the settings in use are needed, you can also create new policy settings for the Oracle database.
Creating Audit Policies for SQL Statements
About SQL Statement Auditing
Statement auditing audits SQL statements by type of statement, not by the specific schema objects on which the statement operates. Statement auditing can be broad or focused (for example, by auditing the activities of all database users or only a select list of users). Typically broad statement auditing audits the use of several types of related actions for each option. These statements are in the following categories:
-
Data definition statements (DDL). For example,
AUDIT TABLEaudits allCREATE TABLEandDROP TABLEstatements.AUDIT TABLEtracks several DDL statements regardless of the table on which they are issued. You can also set statement auditing to audit selected users or every user in the database. -
Data manipulation statements (DML). For example,
AUDIT SELECT TABLEaudits allSELECT ... FROM TABLEorSELECT ... FROM VIEWstatements, regardless of the table or view.
Defining SQL Statement Audit Settings
To define SQL statement audit settings:
-
Log in to the Audit Vault Server console as an auditor.
-
If necessary, retrieve and update the current audit settings.
See "Retrieving and Modifying Audit Settings from an Oracle Database" for more information.
-
Click the Policy tab, and in the Audit Settings page, click an Oracle Database secured target.
The target's Audit Settings Overview page is displayed.
-
Click Statement.
The Statement Audit Settings page appears. See "Understanding the Statement Audit Settings Page".
-
Click the Create button.
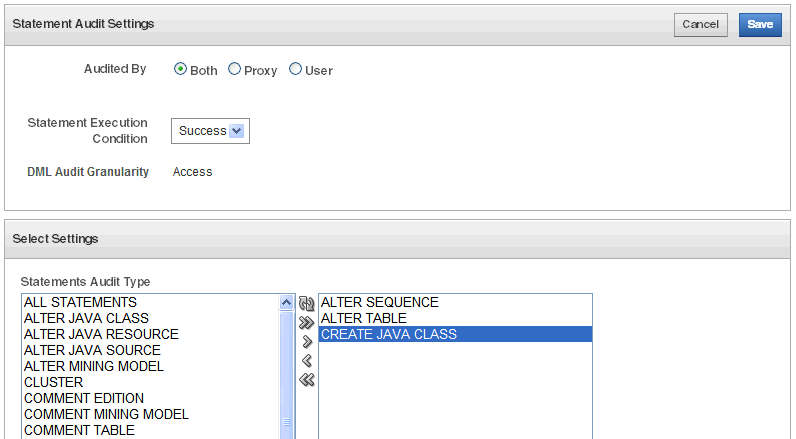
Description of the illustration ''statement_policy_create.gif''
-
In the Create page, define the audit policy as follows:
-
Audited By - Choose the users to audit:
-
Both: Audits all users, including proxy users.
-
Proxy: Audits the proxy user for the database. When you select this option, the Proxy User field appears, in which you must specify at least one user. To display a list of proxy users and their secured targets for selection, click the up-arrow icon on the right of the field.
-
User: Audits the user to which this setting applies. If you select this option, you must select a user from the Users drop-down list.
-
-
Statement Execution Condition - Choose one of the following:
-
Both: Audits both successful and failed statements
-
Success: Audits the statement if it is successful
-
Failure: Audits the statement if it fails
-
-
DML Audit Granularity - Choose audit granularity for DML statements:
-
Access: Creates an audit record each time the operation occurs
-
Session: Creates an audit record the first time an operation occurs in the current session
DDL statements are always audited by access.
-
-
Statements Audit Type - Select the SQL statements to audit by double clicking a statement type to move it to the box on the right. You can use the double arrows to move all statements to the right or back to the left.
-
-
Click Save.
The new audit settings are added to the Statement Audit Settings page.
Understanding the Statement Audit Settings Page
Table 5-2 lists the columns used in the Statement page.
Table 5-2 Columns in the Statement Audit Settings Page
| Column | Description |
|---|---|
|
(Leftmost column) |
A checkbox for selecting the audit setting |
|
Problem icon |
An exclamation mark icon indicates one of the following conditions:
|
|
Setting |
The statement that is audited |
|
In Use |
The arrow points upward if the setting is active in the secured target database, and downward if it has not been provisioned or is not active. |
|
Needed |
The arrow points upward if the audit setting is marked as needed in Oracle AVDF, and downward if the audit setting is marked as not needed. If an audit setting that is not in use is set to needed, the In Use arrow points up after provisioning. If an audit setting that is in use is set to not needed, the audit setting is no longer displayed after provisioning. |
|
Audit granularity |
The granularity of auditing: |
|
Execution Condition |
The execution condition audited: |
|
Proxy User |
The proxy user for the database, if any |
|
User |
The user to which this setting applies, if any |
Creating Audit Policies for Schema Objects
About Schema Object Auditing
Schema object auditing is the auditing of specific statements on a particular schema object, such as AUDIT SELECT ON HR.EMPLOYEES. Schema object auditing is very focused, auditing only a specific statement on a specific schema object for all users of the database.
For example, object auditing can audit all SELECT and DML statements permitted by object privileges, such as SELECT or DELETE statements on a given table. The GRANT and REVOKE statements that control those privileges are also audited.
Object auditing lets you audit the use of powerful database commands that enable users to view or delete very sensitive and private data. You can audit statements that reference tables, views, sequences, standalone stored procedures or functions, and packages.
Oracle Database sets schema object audit options for all users of the database. You cannot set these options for a specific list of users.
Defining Schema Object Audit Settings
To define schema object audit settings:
-
Log in to the Audit Vault console as an auditor.
-
If necessary, retrieve and update the current audit settings.
See "Retrieving and Modifying Audit Settings from an Oracle Database" for more information.
-
Click the Policy tab, and in the Audit Settings page, click a secured target Oracle database.
The target's Audit Settings Overview is displayed.
-
Click Object to display the Object Audit Settings page.
See "Understanding the Object Audit Settings Page" for descriptions of the columns used in this page.
-
Click the Create button.
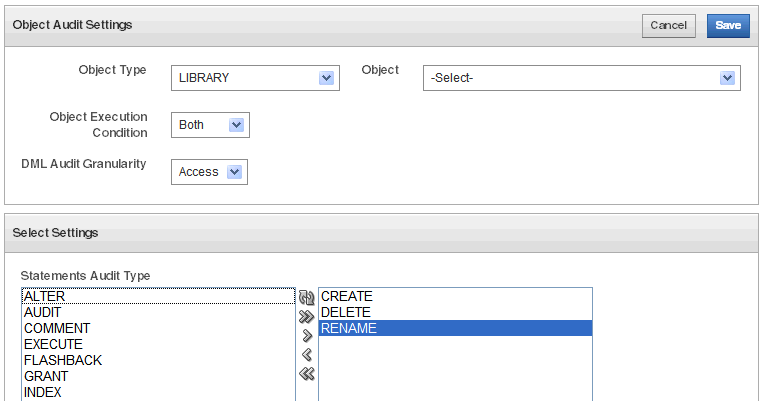
Description of the illustration ''object_policy_create.gif''
-
In the Object Audit Settings page, define the settings as follows:
-
Object Type - Select the type of object to audit from the drop-down list, such as
TABLE,LOB,RULE, orVIEW. -
Object - Select a specific object of the object type you selected.
-
Object Execution Condition - Choose one of the following:
-
Both: Audits both successful and failed statements
-
Success: Audits the statement if it is successful
-
Failure: Audits the statement if it fails
-
-
DML Audit Granularity - Choose audit granularity for DML statements:
-
Access: Creates an audit record each time the operation occurs
-
Session: Creates an audit record the first time an operation occurs in the current session
DDL statements are always audited by access.
-
-
Statements Audit Type - Select the SQL statements to audit by double clicking a statement type to move it to the box on the right. You can use the double arrows to move all statements to the right or back to the left.
-
-
Click Save.
The new object audit settings are added to the Object Audit Settings page.
Understanding the Object Audit Settings Page
Table 5-3 lists the columns used in the Object page.
Table 5-3 Columns in the Object Audit Settings Page
| Column | Description |
|---|---|
|
(Leftmost column) |
A checkbox for selecting the audit setting |
|
Problem icon |
An exclamation mark icon indicates one of the following conditions:
|
|
Setting |
The statement that is audited |
|
In Use |
The arrow points upward if the setting is active in the secured target database, and downward if it has not been provisioned or is not active. |
|
Needed |
The arrow points upward if the audit setting is marked as needed in Oracle AVDF, and downward if the audit setting is marked as not needed. If an audit setting that is not in use is set to needed, the In Use arrow points up after provisioning. If an audit setting that is in use is set to not needed, the audit setting is no longer displayed after provisioning. |
|
Object Type |
The object (such as a database table) to which this setting applies |
|
Object Owner Name |
The database schema to which this setting applies |
|
Object Name |
The name of the object in the specified schema. |
|
Audit granularity |
The granularity of auditing: |
|
Execution Condition |
The execution condition audited: |
Creating Audit Policies for Privileges
About Privilege Auditing
Privilege auditing is the auditing of SQL statements that use a system privilege. You can audit the use of any system privilege. Like statement auditing, privilege auditing can audit the activities of all database users or only a specified list of users.
For example, if you enable AUDIT SELECT ANY TABLE, Oracle Database audits all SELECT tablename statements issued by users who have the SELECT ANY TABLE privilege. This type of auditing is very important for the Sarbanes-Oxley (SOX) Act compliance requirements. Sarbanes-Oxley and other compliance regulations require the privileged user be audited for inappropriate data changes or fraudulent changes to records.
Privilege auditing audits the use of powerful system privileges enabling corresponding actions, such as AUDIT CREATE TABLE. If you set both similar statement and privilege audit options, then only a single audit record is generated. For example, if the statement clause TABLE and the system privilege CREATE TABLE are both audited, then only a single audit record is generated each time a table is created. The statement auditing clause, TABLE, audits CREATE TABLE, ALTER TABLE, and DROP TABLE statements. However, the privilege auditing option, CREATE TABLE, audits only CREATE TABLE statements, because only the CREATE TABLE statement requires the CREATE TABLE privilege.
Privilege auditing does not occur if the action is already permitted by the existing owner and schema object privileges. Privilege auditing is triggered only if these privileges are insufficient, that is, only if what makes the action possible is a system privilege.
Privilege auditing is more focused than statement auditing for the following reasons:
-
It audits only a specific type of SQL statement, not a related list of statements.
-
It audits only the use of the target privilege.
Defining Privilege Audit Settings
To define create privilege audit settings:
-
Log in to the Audit Vault Server console as an auditor.
-
If necessary, retrieve and update the current audit settings.
See "Retrieving and Modifying Audit Settings from an Oracle Database" for more information.
-
Click the Policy tab, and in the Audit Settings page, click a secured target Oracle database.
The target's Audit Settings Overview is displayed.
-
Click Privilege to display the Privilege Audit Settings page.
See "Understanding the Privilege Audit Settings Page" for descriptions of the fields used in this page.
-
Click the Create button, and in the Create Privilege Audit page, define the privilege audit policy as follows:
-
Audited By - Choose the users to audit:
-
Both: Audits all users, including proxy users.
-
Proxy: Audits the proxy user for the database. When you select this option, the Proxy User field appears, in which you must specify at least one user. To display a list of proxy users and their secured targets for selection, click up-arrow icon on the right of the field.
-
User: Audits the user to which this setting applies. When you select this option, the Users field appears, and you must specify a user from the drop-down list.
-
-
Statement Execution Condition - Choose one of the following:
-
Both: Audits both successful and failed statements
-
Success: Audits the statement if it is successful
-
Failure: Audits the statement if it fails
-
-
DML Audit Granularity - Choose audit granularity for DML statements:
-
Access: Creates an audit record each time the operation occurs
-
Session: Creates an audit record the first time an operation occurs in the current session
DDL statements are always audited by access.
-
-
Statements Audit Type - Select the privileges to audit by double clicking a statement type to move it to the box on the right.
You can use the double arrows to move all statements to the right or back to the left.
-
-
Click Save.
The new privilege audit settings are added to those listed in the Privilege Audit Settings page.
Understanding the Privilege Audit Settings Page
Table 5-4 lists the columns used in the Privilege Audit Settings page.
Table 5-4 Columns in the Privilege Audit Settings Page
| Column | Description |
|---|---|
|
(Leftmost column) |
A checkbox for selecting the audit setting |
|
Problem icon |
An exclamation mark icon indicates one of the following conditions:
|
|
Setting |
The statement that is audited |
|
In Use |
The arrow points upward if the setting is active in the secured target database, and downward if it has not been provisioned or is not active. |
|
Needed |
The arrow points upward if the audit setting is marked as needed in Oracle AVDF, and downward if the audit setting is marked as not needed. If an audit setting that is not in use is set to needed, the In Use arrow points up after provisioning. If an audit setting that is in use is set to not needed, the audit setting is no longer displayed after provisioning. |
|
Audit granularity |
The granularity of auditing: |
|
Execution Condition |
The execution condition audited: |
|
User |
The user to which this setting applies, if any |
|
Proxy User |
The proxy user for the database, if any |
Creating Audit Policies for Fine-Grained Auditing (FGA)
About Fine-Grained Auditing
Fine-grained auditing (FGA) enables you to create a policy that defines specific conditions that must exist for the audit to occur. For example, fine-grained auditing lets you audit the following types of activities:
-
Accessing a table between 9 p.m. and 6 a.m. or on Saturday and Sunday
-
Using an IP address from outside the corporate network
-
Selecting or updating a table column
-
Modifying a value in a table column
A fine-grained audit policy provides granular auditing of select, insert, update, and delete operations. Furthermore, you reduce the amount of audit information generated by restricting auditing to only the conditions that you want to audit. This creates a more meaningful audit trail that supports compliance requirements. For example, a central tax authority can use fine-grained auditing to track access to tax returns to guard against employee snooping, with enough detail to determine what data was accessed. It is not enough to know that a specific user used the SELECT privilege on a particular table. Fine-grained auditing provides a deeper audit, such as when the user queried the table or the computer IP address of the user who performed the action.
Auditing Specific Columns and Rows
When you define the fine-grained audit policy, you can target one or more specific columns, called a relevant column, to be audited if a condition is met. This feature enables you to focus on particularly important, sensitive, or privacy-related data to audit, such as the data in columns that hold credit card numbers, patient diagnoses, Social Security numbers, and so on. A relevant-column audit helps reduce the instances of false or unnecessary audit records, because the audit is triggered only when a particular column is referenced in the query.
You further can fine-tune the audit to specific columns and rows by adding a condition to the audit policy. For example, suppose you enter the following fields in the Create Fine Grained Audit page:
-
Condition:
department_id = 50 -
Columns:
salary, commission_pct
This setting audits anyone who tries to select data from the salary and commission_pct columns of employees in Department 50.
If you do not specify a relevant column, then Oracle Database applies the audit to all the columns in the table; that is, auditing occurs whenever any specified statement type affects any column, whether or not any rows are returned.
Using Event Handlers in Fine-Grained Auditing
In a fine-grained audit policy, you can specify an event handler to process an audit event. The event handler provides flexibility in determining how to handle a triggering audit event. For example, it could write the audit event to a special audit table for further analysis, or it could send a pager or an email alert to a security administrator. This feature enables you to fine-tune audit responses to appropriate levels of escalation.
For additional flexibility in implementation, you can employ a user-defined function to determine the policy condition, and identify a relevant column for auditing (audit column). For example, the function could allow unaudited access to any salary as long as the user is accessing data within the company, but specify audited access to executive-level salaries when they are accessed from outside the company.
Defining Fine-Grained Audit Settings
To define fine-grained audit settings:
-
Log in to the Audit Vault Server console as an auditor.
-
If necessary, retrieve and update the current audit settings.
See "Retrieving and Modifying Audit Settings from an Oracle Database" for more information.
-
Click the Policy tab, and in the Audit Settings page, click a secured target Oracle database.
The database's Audit Settings Overview is displayed.
-
Click FGA to display the Fine Grained Audit Settings page.
See "Understanding the Fine-Grained Audit Settings Page" for descriptions of the fields used in this page.
-
Click the Create button.
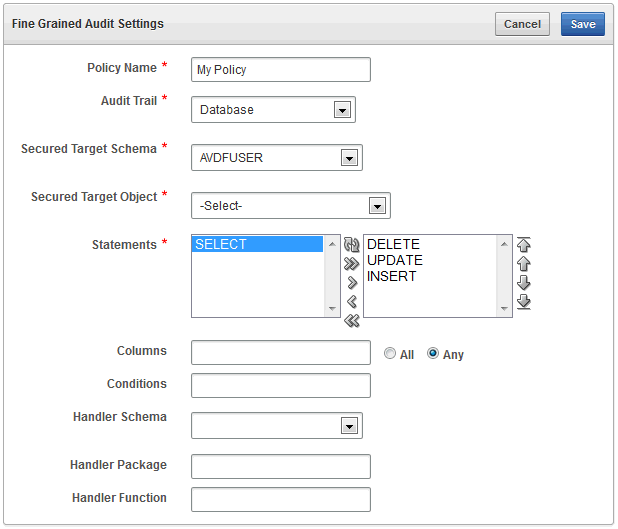
Description of the illustration ''fga_policy_create.gif''
-
Define the audit policy as follows:
-
Policy Name - Enter a name for this fine-grained audit policy.
-
Audit Trail - Select from one of the following audit trail types:
-
Database: Writes the policy records to the database audit trail
SYS.FGA_LOG$system table. -
Database with SQL Text: Performs the same function as the Database option, but also populates the SQL bind and SQL text CLOB-type columns of the
SYS.FGA_LOG$table. -
XML: Writes the policy records to an operating system XML file. To find the location of this file, a database administrator can run the following command in SQL*Plus:
SQL> SHOW PARAMETER AUDIT_FILE_DEST
-
XML with SQL Text: Performs the same function as the XML option, but also includes all columns of the audit trail, including
SQLTEXTandSQLBINDvalues.
WARNING:
Be aware that sensitive data, such as credit card numbers, appear in the audit trail if you collect SQL text.
-
-
Secured Target Schema - Select a schema to audit.
-
Secured Target Object - Select an object to audit.
-
Statements - Select one or more SQL statements to audit by double clicking each statement to move it to the box on the right. You can select:
DELETE,INSERT,MERGE,SELECT, orUPDATE. -
Columns - (Optional) Enter the names of the database columns (relevant columns) to audit. Separate each column name with a comma. If you enter more than one column, select All or Any as the condition that triggers this policy.
See "Auditing Specific Columns and Rows" for more information about relevant columns.
-
Conditions - (Optional) Enter a Boolean condition to filter row data. For example,
department_id = 50.If this field is blank or null, auditing occurs regardless of condition.
-
Handler Schema - (Required if you specify an event handler function) Enter the name of the schema account in which the event handler was created. For example:
SEC_MGR -
Handler Package - (Required if you specify an event handler function) Enter the name of the package in which the event handler was created. For example:
OE_FGA_POLICIES -
Handler Function - (Optional) Enter the name of the event handler. For example:
CHECK_OE_VIOLATIONS
-
-
Click Save.
The fine-grained audit policy is created.
Understanding the Fine-Grained Audit Settings Page
Table 5-5 lists the columns used in the Fine-Grained Audit Settings page.
Table 5-5 Columns in the Fine-Grained Audit Settings Page
| Field | Description |
|---|---|
|
(Leftmost column) |
A checkbox for selecting the audit setting |
|
Problem icon |
An exclamation mark icon indicates one of the following conditions:
|
|
Policy Name |
The name of this fine-grained audit policy |
|
In Use |
The arrow points upward if the setting is active in the secured target and downward if it has not been provisioned or is not active. |
|
Needed |
The arrow points upward if the audit setting is marked as needed in Oracle AVDF, and downward if the audit setting is marked as not needed. If an audit setting that is not in use is set to needed, the In Use arrow points up after provisioning. If an audit settings that is in use is set to not needed, the audit setting is no longer displayed after provisioning. |
|
Object Owner |
The schema to which this audit setting applies |
|
Object |
The object, in the specified schema, to which this audit setting applies |
|
Statement Types |
The SQL statement to which this audit setting applies. Values are:
|
|
Columns |
The database columns being audited, also referred to as the relevant columns. If this field is empty, all columns are audited. |
Creating Capture Rules for Redo Log File Auditing
About Capture Rules Redo Log File Auditing
You can create a capture rule to track before and after value changes in the database redo log files. The capture rule specifies DML and DDL changes that should be checked when Oracle Database scans the database redo log. You can apply the capture rule to an individual table, a schema, or globally to the entire database. Unlike statement, object, privilege, and fine-grained audit policies, you do not retrieve and activate capture rule settings from a secured target, because you cannot create them there. You only can create the capture rule in the Audit Vault Server console.
Note:
In the secured target database, ensure that the table that you plan to use for the redo log file audit is not listed in theDBA_STREAMS_UNSUPPORTED data dictionary view.Defining a Capture Rule for Redo Log File Auditing
-
Log in to the console as an auditor.
-
If necessary, retrieve and update the current statement audit policies.
See "Retrieving and Modifying Audit Settings from an Oracle Database" for more information.
-
Click the Policy tab, and in the Audit Settings page, click a secured target Oracle database.
The target's Audit Settings Overview is displayed.
-
Click Capture Rule to display the Capture Rule Settings page.
See "Understanding the Capture Rule Settings Page" for descriptions of the fields used in this page.
-
Click the Create button.
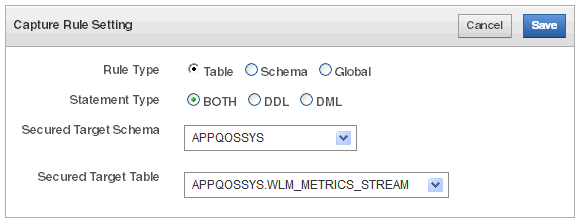
Description of the illustration ''capture_rule_create.gif''
-
Define the capture rule as follows:
-
Rule Type - Select one of the following:
-
Table: Captures either row changes resulting from DML changes or DDL changes to a particular table.
-
Schema: Captures either row changes resulting from DML changes or DDL changes to the database objects in a particular schema.
-
Global: Captures either all row changes resulting from DML changes or all DDL changes in the database.
-
-
Statement Type - Select DDL, DML, or Both.
-
Secured Target Schema - If you selected Table or Schema as the Rule Type, select the name of the schema to which the capture rule applies from the drop-down list.
-
Secured Target Table - If you selected Table as the Rule Type, select the name of the table to which the capture rule applies from the drop-down list.
-
-
Click Save.
The capture rule is created and added to the list in the Capture Rule Settings page.
Understanding the Capture Rule Settings Page
Table 5-6 lists the columns used in the Capture Rule page.
Table 5-6 Columns in the Capture Rule Page
| Column | Description |
|---|---|
|
(Leftmost column) |
A checkbox for selecting the audit setting |
|
Problem icon |
An exclamation mark icon indicates one of the following conditions:
|
|
Rule Type |
The types of capture rules are as follows:
|
|
In Use |
The arrow points upward if the setting is active in the secured target and downward if it has not been provisioned or is not active. |
|
Needed |
The arrow points upward if the audit setting is marked as needed in Oracle AVDF, and downward if the audit setting is marked as not needed. If an audit setting that is not in use is set to needed, the In Use arrow points up after provisioning. If an audit setting that is in use is set to not needed, the audit setting is no longer displayed after provisioning. |
|
Schema |
Indicates the schema to which this rule applies |
|
Table |
For table capture rules, this fields indicates the table to which this rule applies. |
|
Statement Type |
Indicates the type of statements that are audited: |
Provisioning Audit Policies to an Oracle Database
After you have updated and/or created the audit policies for a secured target Oracle Database, you can provision the audit policy changes to that database.
You can provision the audit policy settings in the following ways:
Caution:
Any audit setting that is not indicated as Needed in the Audit Vault Server console will be turned off on the secured target. See "Specifying Which Audit Settings Are Needed".Exporting Audit Settings to a SQL Script
You can export audit policy settings for a secured target to a SQL script from Oracle AVDF. Then you can give the script to a database administrator for the secured target Oracle Database to use to update the audit settings on that database.
To export the audit settings to a SQL script for a secured target database:
-
Log in to the Audit Vault console as an auditor, and click the Policy tab.
The Audit Settings page is displayed, showing the Oracle database secured targets to which you have access.
-
Click the name of a secured target database.
The Audit Settings Overview for that database appears.
-
Select from the audit types you want to export: Statement, Object, Privilege, FGA, or Capture Rule.
-
Click Export/Provision.
The Export/Provision Audit Settings page appears, displaying the exportable audit commands.
-
Click Export, and then click OK to confirm.
-
Save the SQL file to a location on your system.
-
Give the saved script to the database administrator for that secured target. The database administrator can then apply the policies to the secured target. To verify that the settings have been updated, you can retrieve the audit settings as described in "Retrieving Audit Settings from an Oracle Database".
Provisioning the Audit Settings from the Audit Vault Server
You can provision the audit policy settings directly from the Audit Vault Server to the secured target Oracle database. This updates the audit settings in the secured target without the intervention of a database administrator. However, a database administrator can modify or delete these audit settings, as well as add new ones. For this reason, you should periodically retrieve the settings to ensure that you have the latest audit settings. See "Retrieving Audit Settings from an Oracle Database".
To provision the audit settings to the secured target:
-
Log in to the Audit Vault Server console as an auditor, and click the Policy tab.
The Audit Settings page is displayed, showing the Oracle database secured targets to which you have access.
-
Click the name of a secured target database.
The Audit Settings Overview for that database appears.
-
Select from the audit types you want to provision: Statement, Object, Privilege, FGA, or Capture Rule.
-
Click Export/Provision.
The Export/Provision Audit Settings page appears, displaying the exportable audit commands, and allowing you to verify them before provisioning.
-
In the Username field, enter the user name of a user who has been granted the
EXECUTEprivilege for theAUDITSQL statement, theNOAUDITSQL statement, and theDBMS_FGAPL/SQL package.If the secured target database is protected with Oracle Database Vault, ensure that the user has been granted the
AUDIT SYSTEMandAUDIT ANYprivileges. If there is an audit command rule in place, ensure the command is enabled and the user whose name you enter is able to execute the command. -
In the Password field, enter the password of this user.
-
Click Provision, and then click OK to confirm.