| Oracle® Fusion Middleware User's Guide for Oracle Identity Manager 11g Release 1 (11.1.1) Part Number E14316-09 |
|
|
PDF · Mobi · ePub |
| Oracle® Fusion Middleware User's Guide for Oracle Identity Manager 11g Release 1 (11.1.1) Part Number E14316-09 |
|
|
PDF · Mobi · ePub |
Oracle Identity Manager controls access to the application by the users to allow or prevent the users to perform various operations in the application. This is controlled by the authorization engine embedded in Oracle Identity Manager with the help of authorization policies. The purpose of authorization policies is to control user's access to Oracle Identity Manager application, which includes data, UI, and API. The authorization policies determine at runtime whether or not a particular action is allowed. You can define authorization policies that satisfy the authorization requirements within Oracle Identity Manager.
In earlier releases of Oracle Identity Manager, each Oracle Identity Manager feature defines and manages its own authorization policy UI and backend implementation. In Oracle Identity Manager 11g Release 1 (11.1.1), authorization policy management is centralized as an administrative feature. Oracle Identity Manager's authorization policy management and enforcement engine is now based on an embedded version of Oracle Entitlements Server (OES), Oracle's industry-leading fine-grained entitlements administration product. These authorization policies secure access control to the Oracle Identity Manager application, thereby defining "who can do what" inside the application. This centralized definition of authorization policies continues to provide context-sensitive authorizations for each feature as explained in the following sections:
You can define and manage authorization policies in the Authorization Policies section of the Oracle Identity Administration. This section is available to users who have the Manage Authorization Policies privilege.
See Also:
"Adding and Removing Roles" and "Viewing and Administering Roles" for information about assigning roles and privileges
The following are the structural components of an authorization policy:
Identifying details: Each authorization policy must have a name and description.
Oracle Identity Manager feature: Each authorization policy is defined for a specific feature in Oracle Identity Manager. Features are well-defined components in Oracle Identity Manager such as user management and role management. The authorization requirements of multiple features cannot be covered by a single authorization policy.
Assignee: This is the role or roles that a policy grants privileges to. You can grant privileges to one or more roles for each policy. All members of the role (direct or indirect through inheritance) are granted the privileges by the authorization policy. For the user management feature, a rule based on the manager relationship is supported. Here, all the users that are in the management chain of the user being acted on are the assignees of the authorization policy.
Note:
For information about inheritance of role membership, see Chapter 12, "Managing Roles".
To assign policies based on user attributes, you can configure auto-group membership rules and assign policies to that role. See "Viewing, Assigning, and Revoking Membership Rules" for details.
Assignee can include additional conditions that must be fulfilled by the assignee. This is a way of making the authorization policy context aware. For example, for the user management feature, a condition can state that for the assignee to have the privileges, the assignee must be a member of the same organization listed in the data security.
Privileges: These are the privileges that the assignees are granted. The list of privileges is defined by the feature for which this policy is being defined. For example, the user management feature defines privileges such as Search for Users, View User Detail, and Modify User Profile. For a complete list of privileges for the user management feature, see "Privileges".
Some privileges also support fine-grained attribute-level controls that define which specific entity attributes of the feature are further granted to the assignee. For instance, for the View User Detail privilege, the policy can further define which of the attributes on the user entity can be viewed by the assignee at run time. Not all privileges support attribute-level details. For example, the Delete User privilege does not require or support any attribute-level details.
Data security: These are the entities managed by the feature over which a privilege is granted to the assignee. This section is optional based on whether or not the feature for which the authorization policy is being defined supports data security. The data security is expressed in the form of an entity selection criteria or a search criteria that is used to determine the entities over which the privilege is granted. The data security can also be a list of specific entities. The data security capabilities depend on the feature. For instance, the criteria can specify that the assignee is granted privileges over the users belonging to a list of organizations. This criteria can provide additional security settings that apply to the data security. For example, in the user management feature, an instruction can be that the organization condition applies down the hierarchy so that users in the specified organization and all child organizations are in scope for this data security policy.
Using the Administrative and User Console, you can perform the following tasks related to authorization policies:
Note:
Creation, modification, or deletion of authorization policies does not come into effect immediately, but takes approximately 5 to 10 seconds to come into effect.
You can perform simple or quick search and advanced search operations for existing authorization policies. These operations are described in the following sections:
To perform simple search for authorization policies:
Login to the Administration console with credentials that have the Manage Authorization Policies privilege.
In the left pane, click Authorization Policy tab.
Verify that Policy is selected in the lookup.
In the text box, enter a search criteria for authorization policies. For example, you can enter the name of the authorization policy you want to find. You can also use wildcard characters in the search criteria, such as the asterix (*) character to search all authorization policies.
Click the Search icon. You can include wildcard characters (*) in your search criterion. For performance reasons, initial (prefix) wildcards will be removed. However, a trailing (prefix) wildcard will be added to all searches.
Note:
Authorization policy search is case sensitive, so you must ensure proper case while entering search criteria.
Figure 15-1 shows the result of the authorization policies simple search:
Figure 15-1 Authorization Policy Simple Search
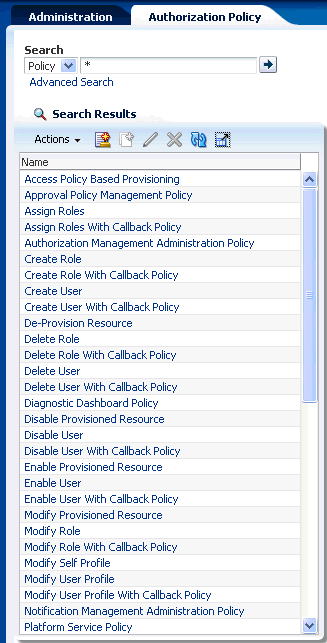
To perform advanced search for authorization policies:
In the Welcome page, under Authorization Policies, click Advanced Search - Authorization Policies. Alternatively, you can click the Authorization Policy tab, and then click Advanced Search link on the left pane. The Advanced Search page is displayed.
Select any one of the following options:
All: On selecting this option, the search is performed with the AND condition. This means that the search operation is successful only when all the search criteria specified are matched.
Any: On selecting this option, the search is performed with the OR condition. This means that the search operation is successful when any search criterion specified is matched.
In the Policy Name field, enter the authorization policy name that you want to search. To do so, select a search comparator in the list adjacent to the Policy Name field. The default search comparator is "Contains". Other comparators are available in the pulldown list as an alternative.
In the Role Name field, enter the name of the role to which the policies are assigned. You can use wildcard characters in your search criteria. Select a search condition in the list adjacent to the Role Name field.
In the Entity Type field, select the entity type for whom the authorization policies are defined.
Click Search. The search results are displayed in the search results table, as shown in Figure 15-2:
Figure 15-2 Authorization Policy Advanced Search
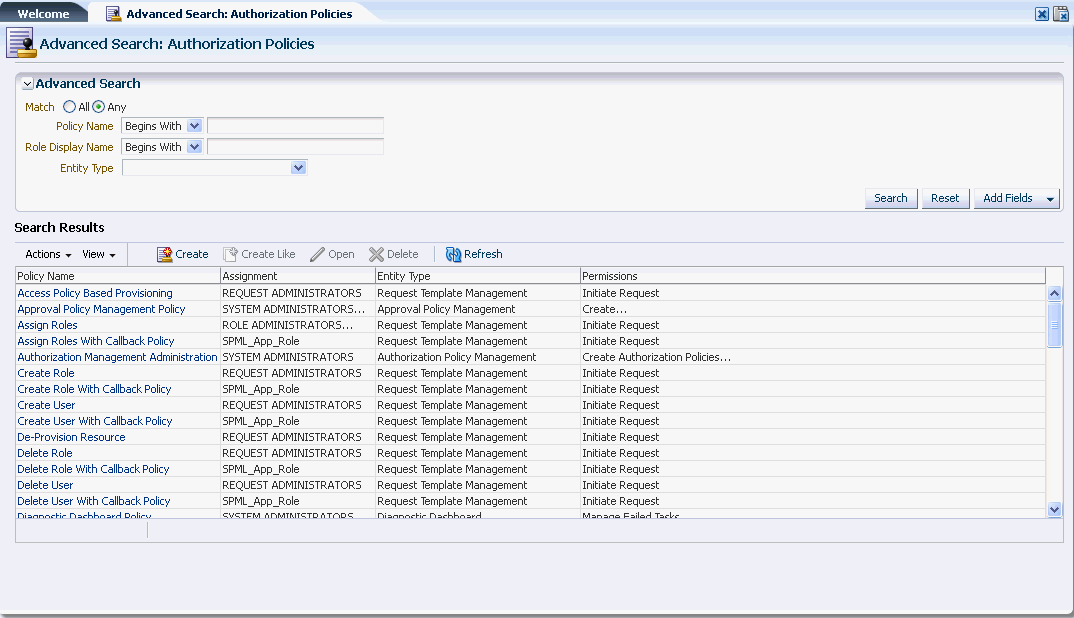
Oracle Identity Manager Administration allows you to create custom authorization policies for the following Oracle Identity Manager components:
User Management
Role Management
Authenticated Self Service User Management
This section describes authorization policy creation in the following topics:
You can create custom authorization policies for user management to control access to user management operations. For example, you can specify that the users belonging to a particular role can search for all users or users belonging to a specific organization, and view a set of selected user attributes.
To create an authorization policy for user management:
Login to the Administrative and User Console, and click Administration.
Note:
You must be a member of the System Administrators role to create, modify, delete, search authorization policies.
On the Welcome page, under Authorization Policies, click Create Authorization Policy. Alternatively, you can click the Authorization Policy tab, and then click the Create Authorization Policy icon on the toolbar, or select Create from the Actions menu. The Basic Policy Information page of the Create Policy wizard is displayed, as shown in Figure 15-3:
Figure 15-3 The Basic Policy Information Page
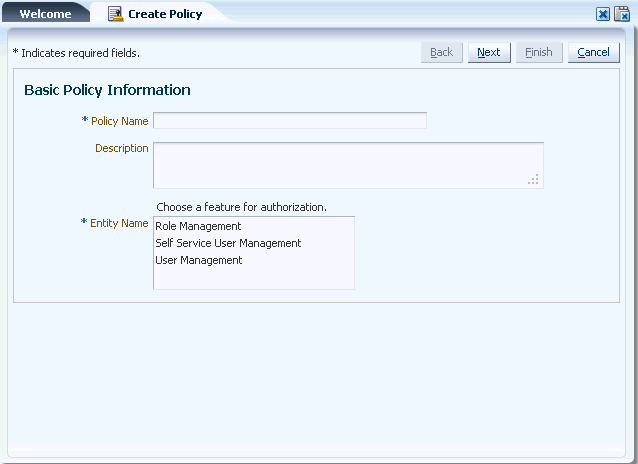
Note:
In the Basic Policy Information page of the Create Policy wizard, only the Basic Policy Information, Policy Settings and Confirmation Nodes are shown at the top of the page. The other Nodes of the wizard are dynamically generated based on your selection in the Entity Name field.
In the Policy Name field, enter the name of the authorization policy.
In the Description field, enter a description of the authorization policy.
To create an authorization policy for user management, in the Entity name field, select User Management.
Click Next. The Permissions page is displayed, as shown in Figure 15-4:
In this page, you can select permissions that you want to enable in the authorization policy.
In the Permissions table, select the check boxes in the Enable column. If you want to enable all permissions for the authorization policy, then select Enable All Permissions at the top of the table.
To allow permission to be used only on a specific set of attributes, you can click Edit Attribute.
Click Next. The Data Constraints page of the Authorization Policy wizard is displayed, as shown in Figure 15-5:
In this page, options for the feature selected on the Entity Name field in step 1 are displayed.
Select one of the following:
All Users: Select this option to specify all the users in Oracle Identity Manager for which the authorization policy is created.
Users that are members of selected Organizations: Select this option to specify organizations for whose members you want to create the authorization policy.
If you select the Users that are members of selected Organizations option, then you must specify one or more organizations. To do so:
Click Add Organization. The Add Organization dialog box is displayed.
Click the Search icon to display the list of organizations in the Available Organizations list.
From the Available Organizations list, select one or more organizations, and then click the Move or Move All buttons to move the selected organizations to the Organizations to Add list.
Click Save. The selected organizations are added in the table in the Data Constraints page.
Under Organization Security Setting, select Hierarchy Aware (include all child organizations) to specify that the authorization policy is applicable to users who are members of all the child organizations of the selected organizations.
Click Next. The Policy Assignment page of the Authorization Policy wizard is displayed, as shown in Figure 15-6:
Under Assign by Rule, select Management Chain of User to assign the direct and indirect managers of the user to the authorization policy.
To assign roles to the authorization policy:
Click Add. The Assign Roles dialog box is displayed.
Click the Search icon to display the list of roles in the Available Roles list.
From the Available Roles list, select one or more roles, and then click the Move or Move All buttons to move the selected roles to the Organizations to Add list.
Click Save. The selected roles are added to the table in the Assignment page.
Note:
To remove a role from the table in the Assignment page, click Remove.
Under Assignment Security Setting, select Assignee must be a member of the User's Organization to specify that the authorization policy is to be applied only for the users that are members of the same organization in which the policy is applied.
Click Next. The Confirmation page of the Authorization Policy wizard is displayed with details specified in the steps of the wizard.
Click Finish. The authorization policy is created.
You can create custom authorization policies for role management to control the access to role management operations. For example, you can specify that users belonging to a particular role can search for roles and role categories and view role details and role category details for all roles or for some selected roles. But the users belonging to that particular role will not be allowed to perform other role management operations.
To create an authorization policy for Oracle Identity Manager role management feature:
On the Welcome page of Oracle Identity Administration, under Authorization Policies, click Create New Policy. Alternatively, you can:
Click the Authorization Policy tab, and then click the Authorization Policy icon on the toolbar.
From the Actions menu, select Create.
The Basic Policy Information page of the Authorization Policy wizard is displayed.
Note:
The pages in the Create Policy wizard are dynamically generated based on the Entity Name selection in the Basic Policy Information page.
In the Policy Name field, enter the name of the authorization policy.
In the Description field, enter a description of the authorization policy.
In the Entity Name field, select an entity name based on the authorization feature you want the assignee to have. To create an authorization policy for role management, select Role Management.
Click Next. The Permissions page is displayed.
Select the permissions that you want to enable for the authorization policy. To select all permissions, select Enable All Permissions at the top of the table.
Click Next. The Data Constraints page is displayed.
Select any one of the following options::
All Roles: To specify that the authorization policy is applicable to all roles in Oracle Identity Manager including all the child roles.
Selected Roles: To specify that the authorization policy is applicable to selected roles only.
The roles selected in the Data constraint page are roles on which action is to be performed.
If you select the Selected Roles option, then you must select the roles for which the authorization policy is been created. To do so:
Click Add Role. The Assign Roles dialog box is displayed.
Click the Search icon to display all roles in the Available Roles list.
Select the roles for which you want to apply the authorization policy.
Click the Move or Move All buttons to move the roles to the Roles to Assign list.
Click Save. The selected roles are added to the Data Constraints page of the Authorization Policy wizard.
To remove a selected role from the Data Constraints page:
Select the role, and then click Remove. A message box is displayed asking for confirmation.
Click OK to confirm.
In the Data Constraints page, under Role Security Setting, select Hierarchy Aware (Include all Parent Roles) to specify that the authorization policy is applicable to Roles, which are added as parent Roles.
Click Next. The Policy Assignment page is displayed. In this page, you can add and remove roles as described in steps 10 and 11.
Roles selected in the Policy Assignment page are roles whose direct and indirect members will perform the action based on the policy.
Click Next. The Confirmation page is displayed with Basic Policy Information and details about permissions, data constraints, and assignments.
Click Finish. The authorization policy is created.
You can create custom authorization policies for authenticated user self service to control the access of user self service operations. For example, if you want to make a few self profile attributes available for modification by a user or a group of users but do not want the users to modify some other self profile attributes, then create a custom authorization policy for user self service with permission to modify a set of user profile attributes, and assign roles to the policy. The users who belong to the assigned roles will have permission to modify the self profile attributes as specified in the authorization policy.
To create an authorization policy for authenticated user self service:
On the Welcome page of Oracle Identity Administration, under Authorization Policies, click Create New Policy. Alternatively, you can:
Click the Authorization Policy tab, and then click the Authorization Policy icon on the toolbar.
From the Actions menu, select Create.
The Basic Policy Information page of the Authorization Policy wizard is displayed.
Note:
The pages in the Create Policy wizard are dynamically generated based on the Entity Name selection in the Basic Policy Information page.
In the Policy Name field, enter the name of the authorization policy.
In the Description field, enter a description of the authorization policy.
In the Entity Name field, select an entity name based on the authorization feature you want the assignee to have. To create an authorization policy for role management, select Self Service User Management.
Click Next. The Permissions page is displayed.
Select the permissions that you want to enable for the authorization policy. For example, if you want to allow the user to modify self profile, then select Modify User Profile.
To select all permissions, select Enable All Permissions at the top of the table.
You can modify some permissions that have attribute-level settings. To do so:
Select the permission, for example, Modify User Profile, and click Edit Attributes on the toolbar. The Attribute Settings window is displayed with a list of all user attributes.
Select the attributes that you want to allow the user to modify, and click Save.
Click Next. The Policy Assignment page is displayed with a table that contains the roles that are assigned to this policy.
To add a role to the policy, click Add. Alternatively, from the Actions menu, select Add.
The Assign Roles window is displayed.
Search for role in the Assign Roles window, select the role or roles that you want to assign to the policy, and click Add. The role is added to the policy assignment table.
The authorization Policy will be enabled for all the members of the assigned roles.
To remove a role from the policy, select the role in the policy assignment table, and click Remove.
Click Next. The Confirmation page is displayed with Basic Policy Information and details about permissions, data constraints, and assignments.
Click Finish. The authorization policy is created.
You can create an authorization policy by using the general, permissions, data constraints, and assignment information from another authorization policy already existing in Oracle Identity Manager. To do so:
Search for the authorization policy from which you want to use information to create another policy.
Select the policy. From the Actions menu, select Create Like. The Authorization Policy wizard is displayed.
In the Basic Policy Information page, edit the Policy Name, Description, and Entity Name fields to specify new values.
Perform the steps to complete the wizard as described in "Creating Custom Authorization Policies".
You can view and modify authorization policies, and change the general information, permissions, data constraints, and assignments of the authorization policies. To do so:
Note:
The options for authorization policy modification changes dynamically based on the entity type selected for the policy. In this procedure, the example of an authorization policy for role management is used.
In the Authorization Policy tab of the Administration Console, in the left pane, search for authorization policies. The policies matching the search criteria are displayed in the search results table.
Click an authorization policy. Alternatively, you can select an authorization policy, and from the Actions menu, select Open. The page that allows you to view and modify authorization policy details is displayed. The General tab of the page is displayed by default, with details about the policy name, description, entity name, permissions, data constraints, and assignment.
Edit the Policy Name and Description fields to update the authorization policy name and description.
Note:
You cannot change the entity name of an authorization policy after the policy is created.
Click the Permissions tab. In this tab, you can check the permissions that you want to enable in this policy. To do so, select the permissions from the table, or select Enable All Permissions to enable all permissions.
Some permissions have attribute-level settings. To modify the attribute-level settings, click Edit Attributes.
Click the Data Constraints tab. In this tab, you can modify the roles that the user must be a member of for this authorization policy.
Select any one of the following options:
All Roles: To specify that the authorization policy is applicable to all roles in Oracle Identity Manager including all the child roles.
Selected Roles: To specify that the authorization policy is applicable to selected roles only.
If you select the Selected Roles option, then you must select the roles for which the authorization policy is been created. This tab also allows you to remove selected roles. To add or remove roles, perform the steps described in steps 10 or 11 respectively of "Creating an Authorization Policy for Role Management".
Select Hierarchy Aware (include all Parent Roles) to specify that all the parent roles of the selected roles must be selected for the authorization.
Note:
Steps 6 through 8 are applicable for authorizations policies for roles.
Click the Assignment tab. This tab displays the roles that are assigned to this policy.
You can add or remove the assignment by performing steps 10 or 11 respectively of "Creating Custom Authorization Policies" and "Creating an Authorization Policy for Role Management".
Click Apply to save changes.
Alternatively, click Revert to refresh the page with old values.
See Also:
"Disabling Access to Features Through the Authorization Policies" in the Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager for information about disabling or hiding features by using authorization policies
To delete an authorization policy:
In the Authorization Policy tab of the Administration Console, search for the authorization policy that you want to delete.
Select the policy. From the Actions menu, select Delete. A message box is displayed asking for confirmation.
Click OK to confirm deletion.
This section describes the authorization policy components for the following Oracle Identity Management features:
The components of the authorization policies defined for the user management feature and the default authorization policy are described in the following sections:
See Also:
Chapter 11, "Managing Users" for information about the user management feature
The assignee of the policy can be a set of roles. The policy is assigned to each role in the set of policies. In addition, a rule for selecting the management chain of the user being managed as an assignee is supported. There is no ability to restrict this to just the direct manager of the user being managed.
The Assignee must be a member of security setting restricts the grant to the users who are also members of the organizations or roles being granted privileges over. If assignee belongs to multiple organization hierarchies, then a match to at least one organization hierarchy must provide the grant.
Multiple privileges are defined for the user management feature such as Search for Users and View User Detail.
Note:
Any user management policy that provides the Search User permission must also provide the View User Details permission.
For a complete list of privileges for the user management feature, see "Privileges".
The following privileges support the fine-grained attribute-level controls, in which the user is able to select the specific attributes applicable to that operation:
View User Detail
Modify User Profile
The list of attributes are based on the list of attributes defined for the user entity.
For the user management feature, data security is defined as the list of organizations whose members the assignee has privileges over. The set of users being managed by the authorization policy cannot be specified by attribute filtering.
If the Hierarchy Aware option is selected, then the organization and role hierarchies are taken into account when determining the data security.
There are two default authorization policies for the user management feature. Users are not allowed to modify or delete these policies. Any User Management policy that provides the "Search User" permission should also provide the "View User Details" permission. The "View User Details" permission should include the User Login, Account Status, Identity Status, Full Name, and Display Name attributes. If these attributes are not provided, the user might not be fully viewable or editable.
The following table lists the default authorization policy details for user management:
| Policy Name | Assignee | Functional Security | Data Security | Description |
|---|---|---|---|---|
|
User Management Administration Policy: |
System Administrators and Identity User Administrators roles |
The permissions include: Change User Password Create User Delete User Evaluate Access Policies Modify OIM Account Status Modify User Profile Modify User Proxy Profile Modify User Status Provision Resource to User Search User View User Details View User Requests Note: The Modify User Profile and View User Details have associated attribute settings. For both the permissions, the attribute setting is All Attributes. |
All Users organization Assignee must be a member of the User's Organization: No Hierarchy Aware: Yes |
Allows users with the SYSTEM ADMINISTRATORS or IDENTITY USER ADMINISTRATORS role to access all User Management actions |
|
User Management Search Policy |
Request Template Administrators, Request Administrators, Approval Policy Administrators, and Reconciliation Administrators roles |
The permissions are: Search Users View User Details: This has associated attribute settings. They are: Display Name, First Name, Full Name, GUID, Last Name, Organization, and User Login |
All Organizations Assignee must be member of the User's Organization: No Hierarchy Aware: Yes |
Allows users with the REQUEST ADMINISTRATORS, RECONCILIATION ADMINISTRATORS, REQUEST TEMPLATE ADMINISTRATORS, or APPROVAL POLICY ADMINISTRATORS roles to search based on GUID and User Login |
|
User Management All Users Policy |
ALL Users role |
The permission is: View User Details: This has associated attribute settings. They are: Display Name, First Name, Full Name, GUID, Last Name, Organization, and User Login |
All Organizations Assignee must be member of the User's Organization: No Hierarchy Aware: Yes |
Allows users with the ALL USERS role to access all User Management actions |
|
User Management policies for Managers |
ALL Users role |
The permissions are: Search User View User Details |
All Organizations Assignee must be member of the User's Organization: No Hierarchy Aware: Yes |
Allows managers to search and view their reportees |
Authorization policies are used to control the following areas of authenticated self service:
See Also:
Chapter 8, "Managing Profile", Chapter 9, "Managing Tasks", and Chapter 10, "Managing Requests" for information about the authenticated user self service feature
The attributes displayed on the My Profile page of Oracle Identity Manager Self Service are controlled by using the VIEW_USER_DETAILS and MODIFY_USER_DETAILS privileges from the Self Service User Management OES authorization policies. If multiple policies are applicable, then the list of attributes on which the user has permissions is a union of the attributes determined by individual policies.
By default, the All Users and System Administrators roles have permissions to view and modify a set of attributes. The All users and System Administrators roles have permissions to view the following attributes:
Email, Display Name, First Name, Last Name, Locale, Middle Name, Telephone Number, Time Zone, User Login, Manager, Identity Status, and Account Status
The All users and System Administrators roles have permissions to modify the following attributes:
Email, Display Name, First Name, Last Name, Locale, Middle Name, Telephone Number, Time Zone, and User Login
If the user has view and modify privileges for an attribute, then the attribute is displayed as editable on the My Profile page. If the attribute has view permission only, then it is displayed as read-only. The request to modify self profile is submitted by using the Modify Self Profile request template. The request dataset for this request template is the same as that for the Modify User request template.
See Also:
"Configuring Requests" in the Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager for detailed information about requests models, request templates, and request datasets
To display additional attributes on the user's profile:
Create a custom self service authorization policy with view and/or modify user profile permission having default or custom additional attributes. See "Creating Custom Authorization Policies" for information about creating custom authorization policies.
Assign the custom authorization policy to the All Users and System Administrators roles because the administrator user does not have All Users role by default.
If the additional attribute is set to modify user profile permission in the policy, then update the request dataset for the Modify Self Profile, that is, ModifyUserDataset.xml to include the attribute. The entry in dataset is made for the attribute to be rendered on the Modify Self Profile page.
Note:
Ensure that the additional attribute has the visible property set.
There is no permission defined for requesting and viewing roles as self service operations. However, while requesting for roles, only those request templates are displayed that the user is authorized to access. The request management feature controls this. While searching for roles during the request operation, the user is allowed to select from only those roles that the user is authorized to search and view. This is controlled by role management policies.
The roles available for the user in the list of roles on the Request Roles page are the result of intersection of the roles provided in the request template and roles that the user has search permission for. For example, if the request template has roles Role1, Role2, and Role3 and the user has search permission on Role2 and Role3, then Role2 and Role3 are displayed in the list of roles. Similarly, if the user has search permission over Role1, Role2, and Role3 and the request template has roles Role2 and Role3, then Role2 and Role3 are displayed in the list of roles.
The user can request for all the roles for which the user has search permission. This is controlled by general authorization policy defined by role management. While creating a request for a role, the user must search and select the roles.
There is no permission defined for requesting and viewing resources as self service operations. However, for requesting and viewing resources, the resource must be configured so that self requesting for that resource is allowed. This is done by selecting the Self Request Allowed option in the Resource Objects form in Oracle Identity Manager Design Console.
See Also:
Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager for information about the Resource Objects form in Oracle Identity Manager Design Console
To add, modify, and remove proxy operations, authorization checks are required in the authenticated self service APIs along with a new MODIFY_SELF_USER_PROXY_PROFILE privilege in the default authorization policy for self service user management. The authenticated self service API first checks for this privilege. If the user is authorized to perform the proxy operation, then the authenticated self service API calls the corresponding APIs for user management.
See Also:
Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager for information about Oracle Identity Manager APIs
The Modify Self User Proxy Profile permission is required to allow adding, modifying, and removing proxies.
The following table lists the default authorization policy details for authenticated self service:
| Policy Name | Assignee | Functional Security | Data Security | Description |
|---|---|---|---|---|
|
Self Assign Roles |
ALL USERS role |
The permission is: Initiate Request |
None |
Allows users with ALL USERS role to access the Self Assign Roles request template |
|
Self De-Provision Resource |
ALL USERS role |
The permission is: Initiate Request |
None |
Allows users with ALL USERS role to access Self Modify Provisioned Resource request template |
|
Self Modify Provisioned Resource |
ALL USERS role |
The permission is: Initiate Request |
None |
Allows users with ALL USERS role to access Self Remove Roles request template |
|
Self Remove Roles |
ALL USERS role |
The permission is: Initiate Request |
None |
Allows users with ALL USERS role to access Self Assign Roles request template |
|
Self Service User Management All Users Policy |
ALL USERS and SYSTEM ADMINISTRATORS roles |
The permissions are: Modify Self User Proxy Profile Modify User Profile: This has associated attribute settings. They are Display Name, Email, First Name, Last Name, Locale, Middle Name, Telephone Number, Time Zone, and User Name Preferred Language. View User Details: The associated attribute settings are Account Status, Display Name, Email, First Name, Identity Status, Last Name, Locale, Manager, Middle Name, Password Expire Date, Password Expired, Password Warn Date, Password Warned, Telephone Number, Time Zone, User Login, and User Name Preferred Language. |
None |
Allows all users to access certain Self Service User Management actions |
|
Self Request Resource |
ALL USERS role |
The permission is: Initiate Request |
None |
Allows users with ALL USERS role to access Self-Request Resource request template |
The components of the authorization policies defined for the role management feature and the default authorization policy for this feature are described in the following sections:
See Also:
Chapter 12, "Managing Roles" for information about the role management feature
The assignee of the policy can be a role or a set of roles.
Multiple privileges are defined for the role management feature. The privileges do not support fine-grained attribute-level controls.
For the role management feature, data security is defined as the list of roles the assignee will have privileges over.
The Assignee Must Be Member of condition restricts the grant to assignees that are also members of the role being granted privileges over.
The Hierarchy Aware setting takes the role hierarchies into account when determining the data security.
The default authorization policy defined for this feature cannot be modified or deleted by users. The policies are describes in the following table:
| Policy Name | Assignee | Functional Security | Data Security | Description |
|---|---|---|---|---|
|
Role Management Administration Policy |
System Administrators and ROLE ADMINISTRATORS roles |
The permissions are: Create Role Create Role Category Delete Role Delete Role Category Modify Role Modify Role Category Modify Role Hierarchy Modify Role Membership Search for Role Search for Role Categories View Role Category Detail View Role Detail View Role Membership |
All Roles |
This is the predefined authorization policy associated with the ROLE ADMINISTRATORS and SYSTEM ADMINISTRATORS roles. |
|
Role Management All Users Policy |
ALL USERS role |
The permissions are: Search for Role Search for Role Categories View Role Detail View Role Category Detail |
All Roles, in which the authorization is applied to users belonging to roles Selected Roles, in which you can select the roles that the user must be a member of for this authorization |
This is the predefined authorization policy associated with the ALL USERS role. |
|
Role Management Role Owner Policy |
ALL USERS role |
The permissions are: Delete Role Modify Role Modify Role Hierarchy Modify Role Membership Search for Role Search for Role Categories View Role Category Detail View Role Detail View Role Membership |
All Roles that the assignee is the owner of.When a user creates a role, the person with the role created will become the role owner. |
This is the predefined authorization policy to enable role owners to have control of their roles. |
|
Role Management Approval and Request Policy |
APPROVAL POLICY ADMINISTRATORS, REQUEST TEMPLATE ADMINISTRATORS roles, and REQUEST ADMINISTRATORS roles |
The permissions are: Search for Role Search for Role Categories View Role Category Detail View Role Detail |
All Roles |
This is the predefined authorization policy associated with the APPROVAL POLICY ADMINISTRATORS, REQUEST ADMINISTRATORS, and REQUEST TEMPLATE ADMINISTRATORS roles. |
|
Role Management Delegated Administration Policy |
ROLE ADMINISTRATORS role |
The permissions are: Modify Role Membership Search for Role Search for Role Categories View Role Category Detail View Role Detail View Role Membership |
All Roles |
This policy can be used as an example for the Delegated Role Administrator persona. You can change the assignee and the data constraint, if required. |
|
Role Management Hierarchy Administration Policy |
ROLE ADMINISTRATORS role |
The permissions are: Modify Role Modify Role Hierarchy Search for Role Search for Role Categories View Role Category Detail View Role Detail View Role Membership |
All Roles |
This policy can be used as an example for the Role Hierarchy Administrator persona. You can change the assignee and the data constraint, if required. |
Access to the authorization policy management feature is controlled by a default authorization policy. This policy grants the users who belong to the System Administrators role to perform authorization policy operations, such as searching authorization policies, and creating, modifying, and deleting custom authorization policies.
Note:
The delete or disable action is controlled by feature-specific UI code, which calls AuthorizationService API to find out whether the user is allowed to perform that action. If the user has the permission, then under Action list on the left pane of the UI, the user can see Delete or Disable options enabled.
The details of the default authorization policy for this feature is the following:
Policy Name: Authorization Management Administration Policy
Assignee: System Administrators role
Functional security: The supported permissions are:
Create Authorization Policies
Delete Authorization Policies
Modify Authorization Policies
Search Authorization Policies
These privileges do not support fine-grained attribute-level controls.
Data security: This authorization policy does not support any data security. Anybody with the privileges to manage authorization policies can manage any and all authorization policies.
The default authorization policy for the user management configuration feature allows users with the System Administrators and USER CONFIGURATION ADMINISTRATORS roles to access all user management configuration operations. This policy has the following details:
See Also:
"Configuring User Attributes" in the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Manager for information about the user management configuration feature
Policy name: User Management Configuration Administration Policy
Assignee: System Administrators and USER CONFIGURATION ADMINISTRATORS roles
Functional security: The permissions are:
Add Category
Add Derived Attributes
Create Attribute
Delete Attribute
Delete Category
Set Search Attributes
Set Search Attributes
Update Attribute
Update Category
These permissions do not support fine-grained attribute-level controls.
Data security: None
Description: This policy allows users with the SYSTEM ADMINISTRATORS or USER CONFIGURATION ADMINISTRATORS roles to access all user management configuration actions.
Note:
When the user is authorized to view all attributes on the pages to create and modify users, if an UDF is created through User Management Configuration, then the UDF is displayed in the pages to create and modify users.
The components of the authorization policies defined for the reconciliation management feature and the default authorization policy for this feature are described in the following sections:
See Also:
"Managing Reconciliation Events" in the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Manager and Chapter 4, "Deployment Configurations" for information about the reconciliation feature
The assignee of the policy can be a role or a set of roles.
The reconciliation management feature defines multiple privileges from the authorization policy management area. These privileges do not support fine-grained attribute-level controls.
This authorization policy does not support any data security. A user with the privileges to manage reconciliation events can manage all reconciliation events.
The following table lists the default authorization policies for the reconciliation management feature:
| Policy Name | Assignee | Functional Security | Data Security | Description |
|---|---|---|---|---|
|
Reconciliation Management Administration Policy |
SYSTEM ADMINISTRATORS and RECONCILIATION ADMINISTRATORS roles |
The permissions include: Assign Bulk Action Create Act Create User Link Act Link User Search View Event Details These permissions do not support fine-grained attribute-level controls. |
None |
Allows users with the RECONCILIATION ADMINISTRATORS or SYSTEM ADMINISTRATORS role to access all reconciliation management actions |
|
Reconciliation API Policy |
SYSTEM ADMINISTRATORS and RECONCILIATION ADMINISTRATORS roles |
The permissions are: Create Reconciliation Event Delete detected Accounts Get Missing Accounts Ignore Event Link Event to Resource for user Link Event to User Process Reconciliation Event These permissions do not support fine-grained attribute-level controls. |
None |
Allows users with the RECONCILIATION ADMINISTRATORS or SYSTEM ADMINISTRATORS role to access all reconciliation management actions |
The default authorization policy for the scheduler feature allows users with the System Administrators and SCHEDULER ADMINISTRATOR roles to access all scheduler operations. This policy has the following details:
See Also:
"Managing Scheduled Tasks" in the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Manager for information about the Scheduler feature
Policy Name: Scheduler Administration Policy
Assignee: System Administrators and SCHEDULER ADMINISTRATOR roles
Functional security: The permissions are:
Job Create
Job Delete
Job Disable
Job Enable
Job Filter
Job Modify
Job pause
Job Resume
Job run now
Job Search
Job stop
Reset Status
Scheduler Search
Scheduler Start
Scheduler Stop
Trigger Create
Trigger Delete
Trigger Modify
These permissions do not support fine-grained attribute-level controls.
Data security: None
Description: Allows users with the SYSTEM ADMINISTRATORS or SCHEDULER ADMINISTRATORS role to access all scheduler actions.
Any user with the REQUEST TEMPLATE ADMINISTRATORS role has access to all management operations related to request templates, such as creating, deleting, modifying, and searching request templates. For information about the default authorization policy, see "Request Creation By Using Request Templates".
Each request template can be associated with a set of roles. Only the users with any of these roles are able to create a request by using this template. When a new request template is created with a list of associated roles, a new authorization policy is created internally. In addition, if the role association with any of the existing request templates is modified (adding new roles or removing existing roles), then the existing authorization policy for this template is modified.
See Also:
Chapter 17, "Managing Request Templates" for information about creating and managing request templates for request creation
The default authorization policy for creating requests by using request template allows users with the REQUEST TEMPLATES ADMINISTRATORS role to access all operations related to request templates. The policy has the following details:
Policy name: Request Template Administration Policy
Assignee: REQUEST TEMPLATE ADMINISTRATORS role
Functional security: The permissions are:
Create
Delete
Modify
Search
These permissions do not support fine-grained attribute-level controls.
Data security: None
Description: Allows users with the REQUEST TEMPLATE ADMINISTRATORS or SYSTEM ADMINISTRATORS role to access all request template actions.
The default authorization policy for the approval policy management feature allows users with the APPROVAL POLICY ADMINISTRATORS role to access all approval policy management operations. This policy has the following details:
See Also:
Chapter 18, "Managing Approval Policies" for information about the approval policy management feature
Policy name: Approval Policy Management Policy
Assignee: APPROVAL POLICY ADMINISTRATORS role
Functional security: The permissions are:
Create
Delete
Modify
Search
These permissions do not support fine-grained attribute-level controls.
Data security: None
Description: Allows users with the APPROVAL POLICY ADMINISTRATORS or SYSTEM ADMINISTRATORS role to access all approval policy management actions.
The default authorization policy for the notification management feature allows users with the NOTIFICATION TEMPLATE ADMINISTRATORS role to access all notification management operations. This policy has the following details:
See Also:
"Managing Notification Templates" in the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Manager for information about the notification management feature
Policy Name: Notification Management Administration Policy
Assignee: System Administrators and NOTIFICATION TEMPLATE ADMINISTRATORS roles
Functional security: The permissions are:
Add Locale
Create
Delete
Filter
Lookup
Modify
Remove Locale
Search
These permissions do not support fine-grained attribute-level controls.
Data security: None
Description: Allows users with SYSTEM ADMINISTRATORS or NOTIFICATION TEMPLATE ADMINISTRATORS role to access all notification template management actions.
The default authorization policy for the system properties feature allows users with the System Administrators and SYSTEM CONFIGURATION ADMINISTRATORS roles to access all operations related to system properties. This policy has the following details:
See Also:
"Administering System Properties" in the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Manager for information about the system properties
Policy name: System Properties Administration Policy
Assignee: System Administrators and SYSTEM CONFIGURATION ADMINISTRATORS roles
Functional security: The permissions include:
Create
Delete
Filter
Lookup
Modify
Search
These permissions do not support fine-grained attribute-level controls.
Data Constraints: None
Description: Allows users with the SYSTEM ADMINISTRATORS or SYSTEM CONFIGURATION ADMINISTRATORS role to access all system properties actions
The default authorization policy for the Diagnostic Dashboard feature allows users with the System Administrators role to access the diagnostic dashboard. This policy has the following details:
See Also:
"Working With the Diagnostic Dashboard" in the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Manager for information about the Diagnostic Dashboard
Policy name: Diagnostic Dashboard Policy
Assignee: System Administrators role
Functional security: The Manage Failed Tasks permission without any fine-grained attribute-level controls
Data constraints: None
Description: Allows users with the SYSTEM ADMINISTRATORS role to access the Diagnostic Dashboard
The default authorization policy for the Plug In feature allows users with the PLUGIN ADMINISTRATOR role to register unregistered policies. This policy has the following details:
See Also:
"Developing Plug-ins" in the Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager for information about plug-ins
Policy name: Plugin Administrator Policy
Assignee: PLUGIN ADMINISTRATOR and SYSTEM ADMINISTRATOR role
Functional security: The permissions are:
Register Plug In
Unregister Plug In
These permissions do not support fine-grained attribute-level controls.
Data constraints: None
Description: Allows users with the PLUGIN ADMINISTRATORS or SYSTEM ADMINISTRATORS role to register and unregister plugins