Release 1.2
Part Number E48145-01
Contents
Previous
Next
| Oracle Pedigree and Serialization Manager Security Guide Release 1.2 Part Number E48145-01 | Contents | Previous | Next |
This chapter covers the following topics:
This section outlines the planning process for a secure installation and describes several recommended deployment topologies for the systems.
To better understand your security needs, ask yourself the following questions:
Many resources in the production environment can be protected, including information in databases accessed by WebLogic Server and the availability, performance, applications, and the integrity of the Web site. Consider the resources you want to protect when deciding the level of security you must provide.
For most Web sites, resources must be protected from everyone on the Internet. But should the Web site be protected from the employees on the intranet in your enterprise? Should your employees have access to all resources within the WebLogic Server environment? Should the system administrators have access to all WebLogic resources? Should the system administrators be able to access all data? You might consider giving access to highly confidential data or strategic resources to only a few well trusted system administrators. Perhaps it would be best to allow no system administrators access to the data or resources.
In some cases, a fault in your security scheme is easily detected and considered nothing more than an inconvenience. In other cases, a fault might cause great damage to companies or individual clients that use the Web site. Understanding the security ramifications of each resource will help you protect it properly.
This section describes recommended architectures for deploying Oracle Pedigree and Serialization Manager to secure Internet access.
Single Computer Deployment Architecture
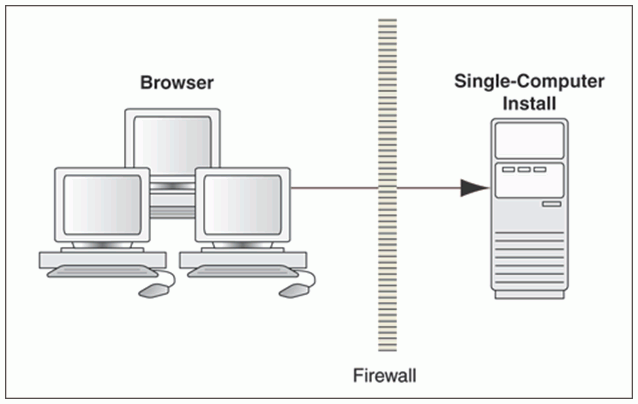
The simplest deployment architecture is shown in the diagram. This single-computer deployment may be cost effective for small organizations; however it cannot provide high availability because all components are stored on the same computer.
Traditional DMZ View
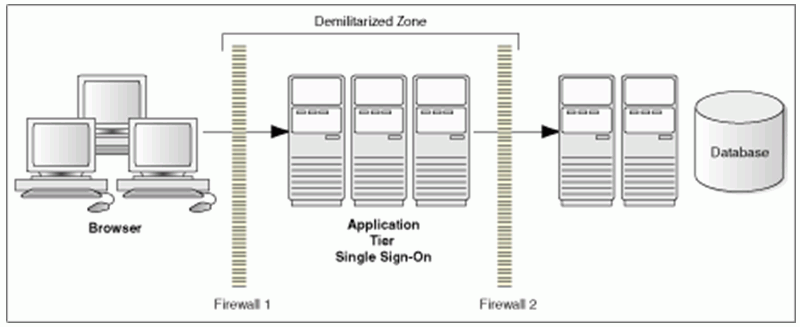
The general architectural recommendation is to use the well-known and generally accepted Internet-Firewall-DMZ-Firewall-Intranet architecture shown in the diagram.
Note: The term demilitarized zone (DMZ) refers to a server that is isolated by firewalls from both the Internet and the intranet, thus forming a buffer between the two.
Firewalls separating DMZ zones provide two essential functions:
Blocking any traffic types that are known to be illegal.
Providing intrusion containment, should successful intrusions take over processes or processors.
The following components can be installed in the same machine or different machines:
Optional Business Intelligence (BI) Publisher server (needed only for printing pedigrees).
A separate web server or the built-in web server in WebLogic Server.
WebLogic Admin server and multiple managed servers. The OPSM application can be deployed on the Admin Server itself and a Service-Oriented Architecture (SOA) server is needed for the SOA components. Or a separate managed server can be used for the OPSM application and the Admin Server can be used for only administrative purposes. Servers can be part of a cluster for failover and reliability reasons. Servers deployed in different machines can be controlled by configuring a node manager.
For more information regarding the WebLogic Server setup, please refer to the WebLogic Server section in the Oracle Fusion Middleware Documentation Library for 11.1.1.7.
You should harden the Operating System (OS) as much as possible, according to the OS vendor’s own security guidelines. The application’s needs in terms of ports used, OS users needed and user privileges needed are fairly light, and all should be easily accommodated.
In keeping with the principal of minimizing your attack surface, unnecessary services should not be installed on the machines being used for the application. Services such as DNS, SMTP, non-application web servers, and the like should not be installed unless absolutely necessary. For example, OPSM has an email notification feature that can be disabled in the System Parameters page. In that case, SMTP need not be installed.
Oracle WebLogic Server should be installed and hardened as per the instructions in its own Security Guide. It would not be a good idea from a security perspective to run another application inside of the same WebLogic instance, as a security breach in one application could be exploited into breaches of other applications.
For more information regarding WebLogic Server security, please refer to the WebLogic Security section in the WebLogic Server section in the Oracle Fusion Middleware Documentation Library for 11.1.1.7.
The Oracle Database should be installed and hardened as per its Security Guide.
The Oracle Database installs with many default (preset) database server user accounts. Upon the successful creation of a database server instance, the Database Configuration Assistant automatically locks and expires most default database user accounts.
Note: If you use Oracle Universal Installer or Database Configuration Assistant, then they will prompt for new SYS and SYSTEM passwords, and will not accept the defaults "change_on_install" or "manager", respectively.
Once the database is installed, lock SYS and SYSTEM as well, and use AS SYSDBA for administrator access. Specify administrative passwords individually.
This account (AS SYSDBA) tracks the operating system user name, maintaining accountability. If you only need access for database startup and shutdown, then use AS SYSOPER instead. SYSOPER has fewer administrative privileges than SYS, but enough to perform basic operations such as startup, shutdown, mount, backup, archive, and recover.
Security is most easily broken when a default database server user account still has a default password even after installation. The following steps fix this:
Change the default passwords of administrative users immediately after installing the database server.
In any Oracle environment (production or test), assign strong, secure passwords to the SYS and SYSTEM user accounts immediately upon successful installation of the database server. Under no circumstances should the passwords for SYS and SYSTEM retain their default values. Similarly, for production environments do not use default passwords for any administrative accounts, including SYSMAN and DBSNMP.
Apply basic password management rules, such as password length, history, and complexity, to all user passwords.
Implement data dictionary protection to prevent users who have the ANY system privilege from using it on the data dictionary. Oracle Database sets the O7_DICTIONARY_ACCESSIBILITY to FALSE. This setting prevents using the ANY system privilege on the data dictionary, except for authorized users making DBA-privileged connections (for example CONNECT/AS SYSDBA).
For more information regarding Database security, please refer to the Database Security section in the WebLogic Server section in the Oracle Fusion Middleware Documentation Library for 11.1.1.7.
Oracle Web Services Manager (OWSM) is a comprehensive and easy-to-use solution for policy management and security of service infrastructure. It provides visibility and control of the policies through a centralized administration interface offered by Oracle Enterprise Manager. To secure the service infrastructure (for example, web services, SOA composites, and so on) offered by the Oracle Pedigree and Serialization Manager product, it is highly recommended that you use OWSM.
Installing the BI Publisher server is optional and needed only for printing pedigrees.
For more information regarding security for the BI Publisher, please refer to the Oracle® Fusion Middleware Security Guide for Oracle Business Intelligence Enterprise Edition 11g Release 1 (11.1.1).
For more information regarding Oracle Fusion Middleware security, please refer to the WebLogic Server section in the Oracle Fusion Middleware Documentation Library for 11.1.1.7.
For the installation steps, please refer to the Oracle Pedigree and Serialization Manager Installation Guide. The security aspects during installation are highlighted here:
In the Installing Oracle Pedigree and Serialization Manager chapter, Installation Tasks section, Step 3.
The install script attempts to start the Admin Server. It tests in a loop if the server is up before it continues. If you installed your WebLogic Server in Production Mode, the Admin Server requires a userid and password to start which the script does not set for security reasons. In this case, you must start a new terminal window to start the Admin Server. After the script detects the server has started, it will continue.
After running newInstall_step1_fepasSchema_createUsers.sql during installation, the database schema user/owners will be created locked and password expired. Once the script has run successfully, please be sure to edit the PAS and PASJMS owners to unlock them and set a new password.
You can manage users and groups for Oracle Pedigree and Serialization Manager (OPSM).
Follow this procedure to create new users and Enterprise groups in Embedded LDAP:
To Create Users and Enterprise Groups in Embedded LDAP
Navigate to the WebLogic Server Administration Console:
http://<HostName>:<portno>/console or https://<HostName>:<sslportno>/console, if SSL is enabled
Click the Security Realms link.
The Summary of Security Realm is displayed.
Click the myrealm link in the Summary of Security Realms region.
The Myrealm Settings page is displayed.
Click the Users and Groups tab.
A list of existing users is displayed.
Click the New button.
The User Creation page is displayed.
Enter a name, description, and password for the user.
Note: The name is what the user will enter when they login, and the description is how the user is displayed in the lists of values.
Tip: Use an LDAP browser (such as JExplorer LDAP) to add an e-mail address to the user definition. This is the e-mail address that is used when sending notifications.
Click OK.
Click the username that you just created.
Click the Groups tab.
Assign one or more job roles to the user.
Click Save.
Enterprise groups map to job, abstract, and data roles. To create an enterprise group, navigate back to the Users and Groups tab and click the Groups tab.
A page appears displaying all existing groups.
Click the New button.
The Enterprise Group Creation page is displayed.
Enter the group details and leave everything else as the default.
Note: You must suffix Enterprise group names with "_Job".
Click OK when finished.
Oracle Web Services Manager (OWSM) is a comprehensive and easy-to-use solution for policy management and security of service infrastructure. It provides visibility and control of the policies through a centralized administration interface offered by Oracle Enterprise Manager. To secure the service infrastructure (for example, web services, SOA composites, and so on) offered by the Oracle Pedigree and Serialization Manager product, it is highly recommended that you use OWSM.
Important: The policies mentioned below are “access control” service policies. As a result, they only enforce who is authorized to invoke the service. The connection between the client and the WebLogic Service is not secure, and the SOAP message is in plain text. Where appropriate, it is highly recommended that services are further hardened to utilize more secure "transport-level" or "message-level" policies as described in the Security and Administrator's Guide for Web Services documentation.
The following steps provide instructions on how to set up a credential store used to store credentials used by the identity switching policies described below.
Follow this procedure to create a credential store and related key for use when securing Oracle Pedigree and Serialization Manager services:
Navigate to the Oracle Enterprise Manager URL:
http://<HostName>:<portno>/em
On the Enterprise Manager Control page, expand the WebLogic Domain node under the navigation tree and select your domain (for example, base_domain).
Select WebLogic Domain, Security, and Credentials to navigate to the credential store setup page.
Using the Create Map button, create the following new map name:
oracle.wsm.security
Select the newly created map, and use the Create Key button to create a new key. Provide the following values:
Key: <any user chosen value> (for example, basic.credentials, opsm.credentials, and so on)
Type: Password
User Name: <valid user name>
Password: <valid password>
Confirm Password: <re-enter valid password)
Important: It may be necessary to create multiple credential store keys to store different users. Please refer to Security Model for more details.
Important: In addition to providing functional security for the application, the system also provides equivalent functional security for web services. As such, it may be necessary to create multiple credential store keys to store different users. For example, you may want to create a credential store key of "opsm.lotsynch.credentials" to store the user that is authorized to invoke services related to management of lots. In addition, you may want to create an additional credential store key of "opsm.transactions.credentials" to store the user that is authorized to invoke services related to creation of shipment and/or return transactions. Similarly, you may want to create an additional credential store key of "opsm.captureepcis.credentials" to store the user that is authorized to invoke services related to capture of EPCIS documents. These credential store keys can then be referenced on the security policies as described in the Setting Up Policies With Different Credentials section.
The following steps provide instructions on how to set up global policy attachments that apply to the Oracle Pedigree and Serialization Manager services.
Important: The policies mentioned below are “access control” service policies. As a result, they only enforce who is authorized to invoke the service. The connection between the client and the WebLogic Service is not secure, and the SOAP message is in plain text. Where appropriate, it is highly recommended that services are further hardened to utilize more secure "transport-level" or "message-level" policies as described in the Security and Administrator's Guide for Web Services documentation.
To Create Global Policy Attachments
Follow this procedure to create global policy attachments (for example, policy sets) for use when securing Oracle Pedigree and Serialization Manager services:
Navigate to the Oracle Enterprise Manager URL:
http://<HostName>:<portno>/em or https://<HostName>:<sslportno>/em, if SSL is enabled
On the Enterprise Manager Control page, expand the WebLogic Domain node under the navigation tree and select your domain (for example, base_domain).
Select WebLogic Domain, Web Services, and Policy Sets to set up global policy attachments.
Using the Create button, add new policy sets for each of the following resources:
SOA Reference
SOA Service
Web Service Client
Web Service Connection
Web Service Endpoint
Asynchronous Callback Client
When it is necessary to select the service policy, please utilize the "oracle/wss_saml_or_username_token_service_policy" policy.
When it is necessary to select the client policy, please utilize the "oracle/wss10_saml_token_client_policy" policy.
Note: Be sure to provide the appropriate resource scope (for example, domain name, server instance name, application name, soa composite name, and so on) to control the scope of resources for the policy set.
For more information, see the Oracle Fusion Middleware Security and Administrator's Guide for Web Services, "Creating and Managing Policy Sets".
Important: Remember to enable the policy set for the security policies to be applied when running the Oracle Pedigree and Serialization Manager services.
For EPCIS Capture and Query web services, directly attach the policies as described below:
To Set Up Direct Policy Attachments
Navigate to the Oracle Enterprise Manager URL:
http://<HostName>:<portno>/em or https://<HostName>:<sslportno>/em, if SSL is enabled
On the Enterprise Manager Control page, expand the WebLogic Domain node under the navigation tree and select your domain (for example, base_domain).
Select WebLogic Domain, Web Services, and Policies.
Select oracle/wss_saml_or_username_token_service_policy and click the Create Like button.
In the Create Policy page, add an assertion with "oracle/binding_permission_authorization_template".
In the Settings tab, enter:
Action Pattern as *
Permission Check Class as oracle.wsm.security.WSFunctionPermission
Resource Pattern as urn:epcglobal:epcis:wsdl:1/EPCglobalEPCISService
Click the Save button.
Click PasEpcServices under Application Deployments and then select Application Deployments, Web Services.
Click EPCglobalEPCISServicePort
Directly attach the policy created above and click OK.
EPCIS Capture Web Service
For Capture follow the steps similar to above with the exception of:
In step 6, enter Resource Pattern as http://xmlns.oracle.com/epcis/CaptureService and continue
In step 8, click on capturePort and continue
In the Setting Up Global Policy Attachments For Composites section below, you will be using policies that utilize identity switching. By default, these security polices utilize the "basic.credentials" credential store key when looking for the appropriate user credentials. If you did not utilize "basic.credentials" as your credential store key, or you set up multiple credential store keys due to functional security requirements, you will need to copy the existing default web service policy to modify the value being used as the credential store key. The following steps provide instructions on how to set up basic security policies that use different credential store keys:
To Create Policies Using Different Credentials
Important: The following steps are only required if you are not using "basic.credentials" as your credential store key.
Follow this procedure to create a copy of the existing Oracle Web Service Manager policies for use when securing Oracle Pedigree and Serialization Manager services:
Navigate to the Oracle Enterprise Manager URL:
http://<HostName>:<portno>/em or https://<HostName>:<sslportno>/em, if SSL is enabled
On the Enterprise Manager Control page, expand the WebLogic Domain node under the navigation tree and select your domain (for example, base_domain).
Select WebLogic Domain, Web Services, and Policies to navigate to the available web service policies.
Select the following web service policy then click the Create Like button:
oracle/wss_username_token_client_policy
Note: The filters on the web service policies page may need to be modified to be able to view the client policies.
On the Configurations tab, edit the property set for the csf-key and enter the value of the key you specified in step 5 of the Setting Up a Credential Store and Key section.
Repeat steps 4 and 5 for each credential store key you set up in step 5 of the Setting Up a Credential Store and Key section.
The following steps provide instructions on how to set up global policy attachments that apply specifically to the Oracle Pedigree and Serialization Manager SOA composites used by integrations:
To Create Global Policy Attachments for Composites
Separate global policies are required for the SOA composites that are used by integrations. Specifically, they are used to override the default global policy attachment that uses identity propagation, to instead use a policy that uses identity switching.
Follow this procedure to create global policy attachments for web service references used within the PasCreateTransactionsComposite, PasLotSynchronizationComposite, and PasCaptureEpcisDocComposite SOA composites:
Navigate to the Oracle Enterprise Manager URL:
http://<HostName>:<portno>/em
On the Enterprise Manager Control page, expand the WebLogic Domain node under the navigation tree and select your domain (for example, base_domain).
Select WebLogic Domain, Web Services, and Policy Sets to set up global policy attachments.
Using the Create button, add a new policy set for the following resource:
SOA Reference
Enter a name and optionally a description for this policy set, then click the Next button to continue.
Tip: Use either the name or the description, to identify that this policy set is used specifically for SOA references within the PasCreateTransactionsComposite.
Provide appropriate resource scope values for Domain Name and Server Instance Name. In addition, enter PasCreateTransactionsComposite for the SOA Composite Name. Click the Next button to continue.
Attach the following web service policy then click the Next button to continue:
oracle/wss_username_token_client_policy
Important: If you created a copy of the above policy as described in the Setting Up Policies With Different Credentials section, be sure to attach that policy instead.
Validate the policy set, then click the Save button.
Using the Create button, add a new policy set for the following resource:
SOA Reference
Enter a name and optionally a description for this policy set, then click the Next button to continue.
Tip: Use either the name, or the description, to identify that this policy set is used specifically for SOA references within the PasLotSynchronizationComposite.
Provide appropriate resource scope values for Domain Name and Server Instance Name. In addition, enter PasLotSynchronizationComposite for the SOA Composite Name. Click the Next button to continue.
Attach the following web service policy then click the Next button to continue:
oracle/wss_username_token_client_policy
Important: If you created a copy of the above policy as described in the Setting Up Policies With Different Credentials section, be sure to attach that policy instead.
Validate the policy set, then click the Save button.
Using the Create button, add a new policy set for the following resource:
SOA Reference
Enter a name and optionally a description for this policy set, then click the Next button to continue.
Tip: Use either the name, or the description, to identify that this policy set is used specifically for SOA references within the PasCaptureEpcisDocComposite.
Provide appropriate resource scope values for Domain Name and Server Instance Name. In addition, enter PasCaptureEpcisDocComposite for the SOA Composite Name. Click the Next button to continue.
Attach the following web service policy then click the Next button to continue:
oracle/wss_username_token_client_policy
Important: If you created a copy of the above policy as described in the Setting Up Policies With Different Credentials section, be sure to attach that policy instead.
Validate the policy set, then click the Save button.
The following steps provide instructions on how to verify policy attachments to ensure the appropriate Oracle Pedigree and Serialization Manager (OPSM) web services are secured.
Use this procedure to verify policy attachments for all services and clients used by the OPSM product:
Start a WLST session to run custom web services WLST commands.
Note: Review the “Accessing the Web Services Custom WLST Commands” section in the Security and Administrator’s Guide for Web Services for instructions.
Verify service policies are attached and the endpoint is secure by running the following WLST command:
listWebServices(None,None,true)
Note: Use this table to verify the services used within the OPSM product.
| Service/Composite | Reference | Service Policy |
|---|---|---|
| PasTransmitSerialsViaFileComposite | transmitserialsviafile_client_ep | oracle/wss_saml_or_username_token_service_policy |
| PasTransmitSerialsViaWebComposite | transmitserialsviaweb_client_ep | oracle/wss_saml_or_username_token_service_policy |
| PasSerialsService_SerialsService | LotsServiceAMService | oracle/wss_saml_or_username_token_service_policy |
| PasSerialsService_SerialsService | PackagingServiceAMService | oracle/wss_saml_or_username_token_service_policy |
| PasTransactionsService_TransactionsService | SerialsServiceAMService | oracle/wss_saml_or_username_token_service_policy |
| PasTransactionsService_TransactionsService | SerialGenerationRequestProcessServiceAMService | oracle/wss_saml_or_username_token_service_policy |
| PasTransactionsService_TransactionsService | JobInstanceServiceAMService | oracle/wss_saml_or_username_token_service_policy |
| PasTransactionsService_TransactionsService | TransactionsProcessingServiceAMService | oracle/wss_saml_or_username_token_service_policy |
| PasTransactionsService_TransactionsService | SerialGenRequestServiceAMService | oracle/wss_saml_or_username_token_service_policy |
| PasTransactionsService_TransactionsService | TransactionsServiceAMService | oracle/wss_saml_or_username_token_service_policy |
| PasSetupService_SetupService | ProductServiceAMService | oracle/wss_saml_or_username_token_service_policy |
| PasEpcService | CaptureService | oracle/wss_saml_or_username_token_service_policy |
| PasEpcService | QueryService | oracle/wss_saml_or_username_token_service_policy |
Verify client policies are attached and the endpoint is secure by running the following WLST command:
listWebServiceClients(None,None,true)
Note: Use this table to verify the clients used within the OPSM product.
| Service/Composite | Reference | Client Policy |
|---|---|---|
| PasTransmitSerialsViaWebComposite | ExampleWebService | oracle/wss10_saml_token_client_policy |
| PasTransactionsComposite | TransmitViaWeb | oracle/wss10_saml_token_client_policy |
| PasTransactionsComposite | TransmitViaFile | oracle/wss10_saml_token_client_policy |
| PasLotSynchronizationComposite | MergeLotWebService | Client policy you attached in step 12 of the Setting Up Global Policy Attachments for Composites section. |
| PasLotSynchronizationComposite | JobInstanceServiceAMService | Client policy you attached in step 12 of the Setting Up Global Policy Attachments for Composites section. |
| PasSerialGenRequestComposite | SerialGenRequestWebService | oracle/wss10_saml_token_client_policy |
| PasCreateTransactionsComposite | CreateTransactionWebService | Client policy you attached in step 7 of the Setting Up Global Policy Attachments for Composites section. |
| PasCreateTransactionsComposite | CreateJobInstanceWebService | Client policy you attached in step 7 of the Setting Up Global Policy Attachments for Composites section. |
| PasTransactionsComposite | TransactionWebServices | oracle/wss10_saml_token_client_policy |
| PasSerialsService_SerialsService | LotsServiceAMServiceImpl/_oracleAsyncResponseClient | oracle/wss10_saml_token_client_policy |
| PasSerialsService_SerialsService | PackagingServiceAMServiceImpl/_oracleAsyncResponseClient | oracle/wss10_saml_token_client_policy |
| PasTransactionsService_TransactionsService | SerialsServiceAMServiceImpl/_oracleAsyncResponseClient | oracle/wss10_saml_token_client_policy |
| PasTransactionsService_TransactionsService | TransactionsProcessingServiceAMServiceImpl/_oracleAsyncResponseClient | oracle/wss10_saml_token_client_policy |
| PasTransactionsService_TransactionsService | JobInstanceServiceAMServiceImpl/_oracleAsyncResponseClient | oracle/wss10_saml_token_client_policy |
| PasTransactionsService_TransactionsService | SerialGenerationRequestProcessServiceAMServiceImpl/_oracleAsyncResponseClient | oracle/wss10_saml_token_client_policy |
| PasTransactionsService_TransactionsService | TransactionsServiceAMServiceImpl/_oracleAsyncResponseClient | oracle/wss10_saml_token_client_policy |
| PasTransactionsService_TransactionsService | SerialGenRequestServiceAMServiceImpl/_oracleAsyncResponseClient | oracle/wss10_saml_token_client_policy |
| PasCaptureEpcisDocComposite | CaptureService | Client policy you attached in step 17 of the Setting Up Global Policy Attachments for Composites section. |
| PasSetupService_SetupService | ProductServiceAMServiceImpl/_oracleAsyncResponseClient | oracle/wss10_saml_token_client_policy |
| PasEpcService | EPCISServicePortTypeImpl/_oracleAsyncResponseClient | oracle/wss10_saml_token_client_policy |
| PasEpcService | CapturePortImpl/_oracleAsyncResponseClient | oracle/wss10_saml_token_client_policy |
The following steps are only needed if you want to digitally sign a Pedigree:
Set up keystore and keys.
Create a file-based keystore containing keys having aliases the same as Oracle Pedigree and Serialization Manager (OPSM) user names of users who would be using those respective keys. OPSM has been certified with JKS and PKCS12 keystores, however other keystore types may also work.
Set up keystore and key passwords in OPSM.
Keystore and key passwords should be stored in the table PAS_S_KEYSTORE_CONFIG so that the same can be retrieved and used for digitally signing a Pedigree.
Note: The definition for the PAS_S_KEYSTORE_CONFIG table includes AFTER INSERT and AFTER UPDATE triggers that are used to encrypt the password stored in the USER_CERTIFICATE_PASSWORD column. Because these triggers are used, the password should always be set in the column in plain text.
Note: The OPSM Release 1.2 application does not provide a page to enable you to maintain the keystore password configuration table. Any changes to this table must be made directly in the database.
![]()
Copyright © 2013, Oracle and/or its affiliates. All rights reserved.