1 OKM Overview and Installation Planning
OKM provides data security by creating, storing, and managing the encryption keys to encrypt stored data (device-based encryption). OKM supports both open systems and enterprise platforms.
OKM Cluster Overview
A cluster is a set of Key Management Appliances (KMAs) that are aware of each other and fully replicate information to each other. The cluster provides encryption endpoints (agents) a high availability service from which they retrieve keys.
-
Clusters must contain a minimum of twoFoot 1 KMAs and maximum of 20 KMAs.
-
New keys generated at any site replicate to all other KMAs in the cluster.
-
You can define sites to provide a logical grouping of KMAs within the cluster, for example a site representing the KMAs in a particular data center. You can associate encryption agents with a specific site to preference KMAs within that site.
-
All administrative changes propagate to all other KMAs in the cluster.
-
You can cluster multiple KMAs con a dedicated private, local, or wide area network.
-
Any KMA in a cluster can service any agent on the network.
-
You can use any KMA in the cluster for administration functions.
Note:
KMAs in one cluster will be unaware of those in other clusters.Agents are encryption endpoints that use cryptographic keys to encrypt and decrypt data. Agents are devices (for example, tape drives) or applications that are authenticated with OKM and obtain key material over a secure (TLS) session. Agents communicate with KMAs through the agent API (a set of software interfaces incorporated into the agent hardware or software). By default, agents are serviced by local KMAs if available.
Tape drive agents should not be on public networks. Agents must remain connected to the network in the event an encryption key is needed. Connect tape drive agents to KMAs in a private service network. KMAs and agents can be logically grouped to create a site, where agents reference KMAs within the site to which they are assigned.
OKM supports monitoring using Oracle Enterprise Manager with the OKM plug-in, remote syslog, SNMP, or Oracle Hardware Management Pack. The Oracle Service Delivery Platform (SDP2) may be deployed for monitoring tape libraries and their encrypting tape drives on the service network.
Supported OKM Encryption Endpoints
How Encryption Endpoints Retrieve Keys from a KMA
Supported encryption endpoints retrieve keys from the KMA cluster through discovery, load balancing, and failover.
Supported encryption endpoints (agents) send a discover cluster request to a KMA. The KMA that receives the discover cluster request provides the following information for each KMA: IP addresses (IPv4 and IPv6), Site Name, KMA ID, KMA Name, KMA Version, KMA Status. The status can be either responding (indicates if the KMA is responding on the network) or locked (indicates if the KMA is currently locked).
The supported endpoints periodically retrieve this information as part of a key request operation (not when the endpoint is idle) and always request it as part of enrollment and whenever the endpoint is IPLed. Whenever an endpoint discovers a new response state for a KMA, it updates the cluster information with the new status.
During normal operations, the endpoints use their local table of cluster information to select a KMA for key retrieval. The endpoints use an algorithm to select a KMA from the same site as the endpoint. If all KMAs within a site are either locked or not responding, then the endpoint attempts to access a KMA from another site. If KMAs from other sites cannot be reached, the attempt to retrieve keys will time out and force a failover.
The ability for endpoints to failover to remote sites can improve endpoint reliability and availability when local KMAs are down or slow to respond (such as timeout situations because of heavy workloads).
Whenever an endpoint cannot communicate with any of the KMAs in a cluster, the endpoint then uses an algorithm to select a KMA for a failover attempt. When selecting, the endpoint's information about the cluster state is used again. Endpoints attempt a failover up to three times before giving up and returning an error to the host application.
An endpoint may occasionally choose a non-responding KMA during a failover attempt if all other KMAs are not responding. However, because information about the cluster may be stale, the KMA may actually be online and responding
Oracle Database with Transparent Data Encryption (TDE)
You can use OKM with Transparent Data Encryption (TDE) to manage encryption or decryption of sensitive database information. This solution allows you to manage encryption keys for the Oracle database using the same encryption technology used in Oracle StorageTek tape drives.
Transparent Data Encryption, a feature of Oracle Database 11gR2 and higher, provides database encryption and decryption services for:
-
Oracle Database products
-
Oracle Real Application Clusters (Oracle RAC)
-
Oracle Data Guard
-
Oracle Extended Database Machine
-
Oracle Recovery Manager (RMAN)
-
Oracle Data Pump
Refer to "Using OKM with Advanced Security Transparent Data Encryption (TDE)". Additionally, see the white paper Oracle Advanced Security Transparent Data Encryption Best Practices, available at the following URL: http://www.oracle.com/technetwork/database/security/twp-transparent-data-encryption-bes-130696.pdf
Oracle Solaris 11 ZFS Encryption
You can use OKM with Oracle Solaris 11 ZFS to manage encryption and decryption of files in ZFS storage pools. This solution allows you to manage encryption keys for ZFS storage pools using the same encryption technology used in Oracle StorageTek tape drives.
ZFS can be configured to use OKM's PKCS#11 provider, pkcs11_kms, to retrieve encryption keys from an OKM cluster. This requires a configured OKM cluster and a Solaris 11 system with established connectivity to KMAs in this OKM cluster.
Once a Solaris 11 administrator installs and configures pkcs11_kms, the administrator can request that pkcs11_kms create a key, and then direct ZFS to use it.
For more information, see "Using OKM with Solaris ZFS Encryption"
ZFS Storage Appliance
The Oracle ZFS Storage Appliance supports encrypted storage using OKM for protection of its encryption keys. It supports KMAs running OKM 2.5.2 and later.
See the ZFSSA product documentation for more details.
Java Applications using Java Cryptographic Extension Provider
The Java Cryptographic Extension Provider for Oracle Key Manager (OKM JCE Provider) implements the KeyGenerator, KeyStore, and Cipher services. It enables Java applications (running Oracle's HotSpot JRE version 7 and version 8) written to the Java Cryptography Architecture (JCA) interface to create, retrieve, utilize, and destroy symmetric encryption keys through an OKM cluster. This Provider implements the subset of JCE's capabilities germaine to OKM.
The OKM JCE Provider version 1.3 is compatible with Oracle Java Runtime Environment version 7 and version 8. It supports only KMAs that are running OKM 3.0.2 and later.
You can download the OKM JCE Provider from the My Oracle Support site where it is published as Patch ID 26915167.
Encryption Capable Tape Drives
The following tape drives support encryption:
-
StorageTek T10000A
-
StorageTek T10000B
-
StorageTek T10000C
-
StorageTek T10000D
-
StorageTek T9840D
-
HP LTO-4 (requires HP Dione card)
-
HP LTO-5 and 6
Table 1-1 FIPS 140-2 Compliant Tape Drives
| Tape Drive | FIPS 140-2 Level |
|---|---|
|
T10000A |
1 |
|
T10000B |
2 |
|
T10000C |
1 |
|
T10000D |
1 |
|
T9840D |
1 |
|
LTO4 (HP and IBM) |
No plans for FIPS |
|
LTO5 (HP and IBM) |
No plans for FIPS |
|
LTO6 (HP and IBM) |
No plans for FIPS |
|
LTO7 (IBM) |
No plans for FIPS |
|
LTO8 (IBM) |
No plans for FIPS |
Note:
LTO drives alone may be FIPS-validated, but not necessarily in specific encryption applications.FIPS 140-2 levels of security for the above tape drives include:
-
Level 1 – The basic level with production-grade requirements.
-
Level 2 – Adds requirements for physical tamper evidence and role-based authentication. Built on a validated operating platform. This selection provides a higher level of security for the KMAs and tape drives.
T-series Tape Drive Encryption Behavior
T10000C and T10000D drives running firmware versions 1.57.30x (T10000C) or 4.06.106 (T10000D) and later do not require encryption enablement keys. For earlier drives and firmware versions, the Oracle support representative must request an encryption license key for each drive.
Table 1-2 T-Series Tape Drive Encryption Behavior
| Tape Drive Type | Non-encrypted Tapes | Encrypted Tapes |
|---|---|---|
|
Not enrolled for encryption |
|
|
|
Enrolled for encryption |
|
|
LTO Tape Drive Encryption Behavior
There are no enablement or drive data requirements for LTO tape drives. The only preparation is to ensure you have the information to assign the IP addresses and agent names for the tape drives in OKM manager.
LTO-8 drives can read and write one generation back. LTO-5, 6, and 7 drives can read two generations back and write one generation back. For best capacity and performance, always use cartridges of the same generation as your drives.
Table 1-3 LTO 5,6,7 and 8 Encryption Behavior
| Drive Behavior | Functionality for Drive Not Enrolled for Encryption | Functionality for Drive Enrolled for Encryption |
|---|---|---|
|
Read same generation non-encryption data |
OK non-encrypted |
OK non-encryption |
|
Read same generation encrypted data |
Error |
OK encrypted if correct key available. |
|
Write same generation from BOT |
OK non-encrypted |
OK encrypted. |
|
Append write same generation encrypted data |
N/A |
OK encrypted if correct key available |
|
Read one generation backwards non-encrypted data |
OK non-encrypted |
OK non-encrypted |
|
Read one generation backwards encrypted data |
Error |
OK encrypted if correct key available |
|
Write one generation backwards from BOT |
OK non-encrypted |
OK encrypted. |
|
Append write one generation backwards encrypted data |
N/A |
OK encrypted if correct key available |
|
Read two generations backwards non-encrypted data (does not apply to LTO-8 drives) |
OK non-encrypted |
OK non-encrypted |
|
Read two generations backwards encrypted data (does not apply to LTO-8 drives) |
Error |
OK encrypted if correct key available |
|
Append write same generation to non-encrypted data (Space EOD, Read to EOD, and write) |
OK non-encrypted |
IBM: Mixing of encrypted and non-encrypted data on a single tape not allowed. HP: OK encrypted if correct key available |
|
Append write same generation to encrypted data (Space EOD, Read to EOD, and write) |
Space EOD = OK non-encrypted Read to EOD = Error |
IBM: OK encrypted if the correct key is available, but with the proper read key. HP: OK encrypted if correct key available |
|
Append write one generation back to non-encrypted Data (Space EOD, Read to EOD, and write) |
OK non-encrypted |
IBM: Mixing of encrypted and non-encrypted data on a single tape not allowed. HP: OK encrypted if correct key available |
|
Append write one generation back to encrypted data (Space EOD, Read to EOD, and write) |
Space EOD = OK non-encrypted Read to EOD = Error |
IBM: OK encrypted if the correct key is available, but with the proper read key. HP: OK encrypted if correct key available |
Updating Tape Drive Firmware
The listed firmware levels are subject to change. To access the latest firmware:
-
Go to My Oracle Support at:
http://support.oracle.comand sign in. -
Click the Patches & Updates tab.
-
Click Product or Family (Advanced).
-
In the Start Typing... field, type in the product information (for example, "Oracle Key Manager"), and click Search to see the latest firmware for each release.
Table 1-4 Firmware Compatibilities
| Drive | SL8500 | SL4000 | SL3000 | SL500 | SL150 |
|---|---|---|---|---|---|
Legend:
|
|||||
|
T10000D |
L–FRS_8.0.5 (no 3590 drive support) D (FC) –4.06.107 D (FICON) –4.07.xxx |
L -1.0.0.65.27025 D – 4.15.102 |
L–FRS_3.62 (no 3590 drive support) D (FC) –4.06.107 D (FICON) –4.07.xxx |
NA |
NA |
|
T10000C |
L–FRS_7.0.0 D–1.53.316 |
L -1.0.0.65.27025 D – 3.66.101 |
L–FRS_3.0.0 D–1.53.316 |
NA |
NA |
|
T10000B |
L–3.98b D–1.38.x09 |
NA |
L–FRS_2.00 D (FC) –1.38.x07 D (FICON) –1.38.x09 |
NA |
NA |
|
T10000A |
L–3.11c D (FC) –1.37.113 D (FICON) –1.37.114 |
NA |
L–FRS_2.00 D (FC) –1.37.113 D (FICON) –1.37.114 |
NA |
NA |
|
T9840D |
L–3.98 D–1.42.x07 |
NA |
L–FRS_2.00 D–1.42.x07 |
NA |
NA |
|
LTO-8 |
L–8.60 D (IBM) - HB82 |
L–1.0.0.65.27025 D (IBM) - HB82 |
L–4.50 D (IBM) - HB82 |
NA |
L–3.50 (LME) D (IBM) - HB83 |
|
LTO-7 |
L-8.60 D (IBM) - HB82 |
L-1.0.0.68.29240 D (IBM) - HB82 |
L-4.50 D (IBM) - HB82 |
NA |
L-3.50 (LME) D (IBM) - HB83 |
|
LTO-6 |
L–8.01 D (IBM) - CT94 D (HP) - J2AS |
L–1.0.0.65.27025 D (IBM) - G9P2 D (HP) - J5MS |
L–4.0 D (IBM) - CT94 D (HP) - J2AS |
L–1483 D (IBM) - BBNH D (HP) - J2AS NA for SAS |
L -2.50 D (HP) –33ES SAS D (HP) –23DS FC D (IBM) -E6RF FC and SAS without OKM compatibility |
|
LTO-5 |
D(IBM) - BBNH D (HP) - I5BS |
L–1.0.0.65.27025 D (IBM) - G350 D (HP) - I6PS |
D (IBM) - BBNH D (HP) - I5BS |
L–1373 D (IBM) - BBNH D (HP) - I5BS |
IBM - NA L (HP) – 1.80 D (HP) –Z68S SAS D (HP) –Y68S FC |
|
LTO-4 |
L–FRS_4.70 D (IBM) - BBH4 D (HP) - H64S |
NA |
L–FRS_2.30 D (IBM) - BBH4 D (HP) - H64S |
L–1373 D (IBM) - BBH4 D (HP) - H64S |
NA |
Note:
If you use Multi-Drive Virtual Operator Panel (MD-VOP), version 1.1 (minimum) is required. It is recommended that you use the most current version of MD-VOP.Key Management Appliance Overview
The Key Management Appliance (KMA) is a security-hardened server that delivers policy-based lifecycle key management, authentication, access control, and key provisioning services. The KMA ensures that all storage devices are registered and authenticated, and that all encryption key creation, provisioning, and deletion is in accordance with prescribed policies. A KMA is a server node within an OKM cluster.
Refer to the Oracle Key Manager 3 Security Guide for additional information such as secure installation and configuration, security features, encryption end points, and system monitoring.
Refer to the white paper Monitoring an Oracle Key Management Cluster for more details. The white paper is available at: https://community.oracle.com/community/server_%26_storage_systems/systems-io/oracle-tape-storage/okm
Specifications for OKM Servers
OKM 3.1 (and later) supports Solaris 11.3 on the SPARC T7-1 server. The OKM version of this server includes:
-
4.13 GHz 32-core SPARC M7 Processor
-
128 GB of DRAM
-
600 GB SAS-3 10K RPM 2.5-inch disk drive with Solaris and OKM pre-installed
-
Four 10 Gigabit Ethernet ports
-
Redundant power supplies
-
Six PCIe Gen 3 adapter slots (8 lanes each)
For other server specifications, including environment and power requirements, see: http://docs.oracle.com/cd/E54976_01/index.html
OKM 3.0 supports Solaris 11 on the Netra SPARC T4-1 server. The OKM version of this server includes:
-
2.85 GHz four-core SPARC T4 Processor
-
32 GB of DRAM (four 8 GB DIMMs)
-
600 GB SAS 10K RPM 2.5-inch disk drive with Solaris and OKM pre-installed
-
Four Gigabit Ethernet ports
-
Redundant power supplies
-
Five PCIe Gen 2 adapter slots (8 lanes each)
-
DVD drive (disabled — not used with OKM)
For other server specifications, including environment and power requirements, see: http://docs.oracle.com/cd/E23203_01/index.html
OKM 2.x supports Solaris 10 on the Sun Fire X2100 M2, X2200 M2, and X4170 M2 servers.
-
Sun Fire KMAs cannot be upgraded to OKM 3.x, but can communicate with OKM 3.x KMAs in the same cluster.
-
Sun Fire KMAs can be migrated to OKM 3.0.2. The customer must submit a request to have an Oracle customer service representative perform the migration. The process is described in the Oracle Support Document 1670455.1 published on the My Oracle Support site.
-
Sun Fire X4170 M2 KMAs that have been migrated to OKM 3.0.2 should be upgraded to OKM 3.3 or higher, following a manual procedure. This manual procedure is described in the Oracle Support Document 229422.1 published on the My Oracle Support site.
-
KMAs running an OKM release earlier than OKM 3.1 should not be added to an OKM cluster where there are KMAs running newer OKM releases. Instead, thjey should be initialized into their own temporary cluster, upgraded to OKM 3.3 or later, and then reset to factory default settings. They can then be added to the existing OKM cluster.
-
OKM 3.1 and later releases are not supported on Sun Fire X2x00 M2 KMAs. These KMAs should be replaced with SPARC KMAs.
-
OKM 3.x KMAs can join an existing OKM 2.x cluster using a KMA running KMS 2.2 or later.
Specifications for Installing a KMA into a Rack
The KMAs can be installed in standard, RETMA 19-inch, four post racks or cabinets.
Note:
Two-post racks are not supported.Only 9.5 mm square hole and M6 round mounting holes are supported.
The slide rails are compatible with racks which meet the following standards:
-
Horizontal opening and unit vertical pitch conforming to ANSI/EIA 310-D-1992 or IEC 60927 standards.
-
Distance between front and rear mounting planes between 610 mm and 915 mm (24 in. to 36 in.).
-
Clearance depth to a front cabinet door must be at least 27 mm (1.06 in.).
-
Clearance depth to a rear cabinet door at least 900 mm (35.5 in.) to incorporate cable management or 700 mm (27.5 in.) without cable management.
-
Clearance width between structural supports and cable troughs and between front and rear mounting planes is at least 456 mm (18 in.).
Provide adequate service clearance for rack components:
-
Front service clearance 48.5 in. (1.23 m) minimum
-
Rear service clearance 36 in. (914.4 mm) minimum
Hardware Security Module for KMA
An optional Hardware Security Module (HSM) may be ordered and pre-installed with the KMA, or added to the KMA later. The HSM provides a FIPS 140-2 Level 3 certified cryptographic device. See the Oracle Key Manager 3 Security Guide for how the HSM is used.
For SPARC KMAs running OKM 3.3 or later, the nCipher nShield Solo PCIe card is available as an HSM.
For SPARC KMAs running an earlier OKM 3.x release and for Sun Fire KMAs, the Sun Cryptographic Accelerator (SCA) 6000 card has been available as an HSM. The firmware on the SCA 6000 card had previously undergone FIPS 140-2 Level 3 certification. However, this certification has been revoked as of December 31, 2015, and as such is no longer certified.
OKM Installation Planning Checklist
Review OKM Configurations:
-
Review the KMA server specifications ("Specifications for OKM Servers").
-
Review KMA rack specifications ("Specifications for Installing a KMA into a Rack").
-
Ensure the site meets temperature, humidity, cooling, and power requirements for the server.
-
For the SPARC T7-1 server specifications, see:
-
Verify the circuit breaker locations and ratings.
-
For the redundant power option, ensure there is an additional APC power switch.
-
-
Have the customer consider applying tamper evident security labels to each KMA. Customers are responsible for acquiring these labels.
Review Network Requirements:
Review Tape Drive Requirements:
Plan User Roles:
-
Ensure authorized personnel are available to handle and accept delivery. The OKM Key Management Appliance (KMA) is considered a secure item.
-
Ensure there is a plan to dispose of or recycle packing material.
Order Components:
Sample OKM Configurations
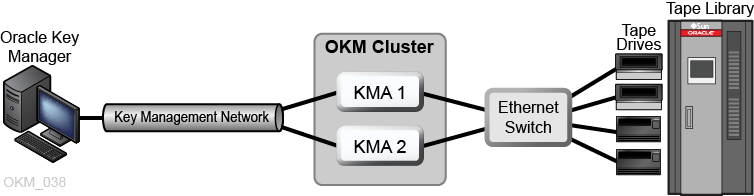
Single Site OKM Configuration
The figure below shows a single site with two KMAs in a cluster. The service network includes multiple tape drives (agents).
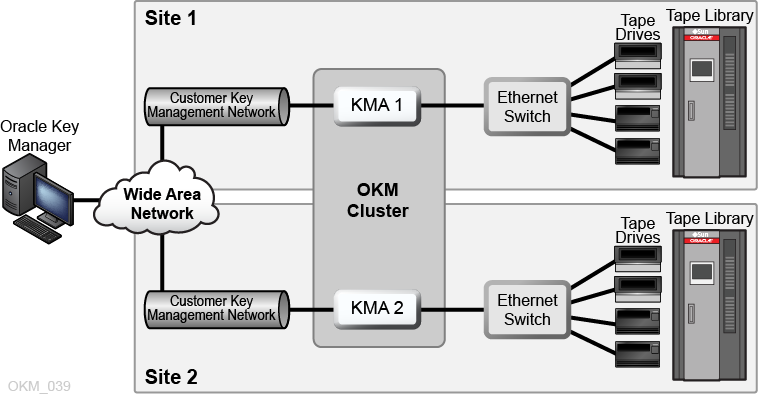
Dual Sites OKM Configuration
In the figure below, each site contains a KMA. The KMAs are managed over a wide area network, and both KMAs belong to the same OKM cluster. In this configuration, Oracle recommends geographically-dispersed sites.
Dual Sites OKM Configuration with Disaster Recovery
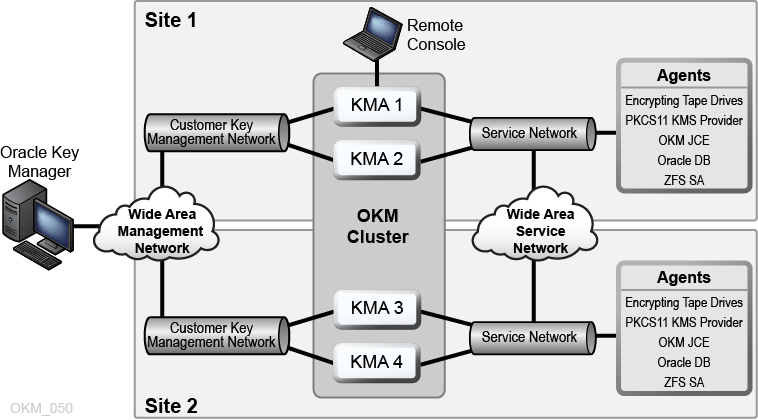
To reduce the risk of a disaster destroying the entire cluster, the cluster should span multiple, geographically-separated sites.
In the figure below, there are two wide area networks — one for key management and one for service. The OKM GUI communicates with both KMAs in the cluster, and the service wide area network allows either KMA to communicate with the agents.
For more information about disaster recovery, refer to "Disaster Recovery".
Figure 1-4 Disaster Recovery Configuration
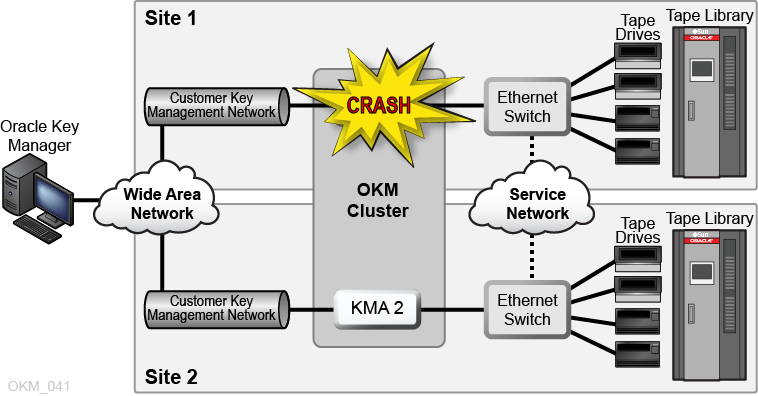
Description of ''Figure 1-4 Disaster Recovery Configuration''
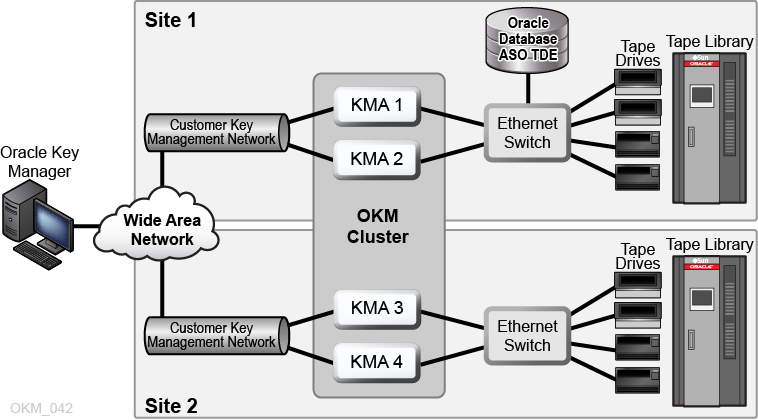
Dual Sites OKM Configuration with Oracle Database
In the figure below, four KMAs in a cluster are supporting two automated tape libraries and an Oracle database with Advanced Security Transparent Data Encryption (TDE) solution. For more information, refer to "Using OKM with Advanced Security Transparent Data Encryption (TDE)".
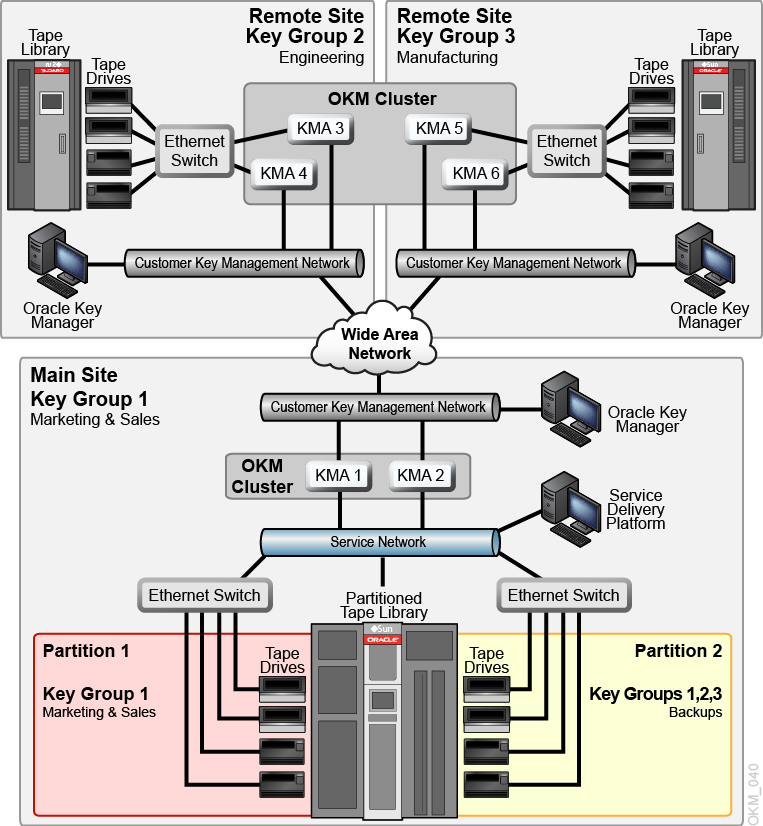
Multiple Sites OKM Configuration with Partitioned Library
When using encryption-capable tape drives, partitions can add a layer of data security. Partitions can:
-
Limit access to tape drives and data cartridges.
-
Separate different encryption key groups.
-
Isolate clients as service centers.
-
Be dedicated for specific tasks.
-
Give multiple departments, organizations, and companies access to appropriate sized library resources.
The figure below shows two remote sites and a local (main) site, all within one OKM cluster. The main site contains a partitioned library with specific key groups that provide backup facilities for all the KMAs (1–6) and media within the cluster.
For more information about partitioning, see your library documentation.
OKM Networking Overview
OKM uses TCP/IP networking (dual stack IPv4 and IPv6Foot 2 ) for the connections between KMAs, agents, and workstations. Each KMA has network connections for the:
Management Network
The management network connects the KMA to other KMAs in the cluster for peer-to-peer replication. The OKM Manager GUI, CLI, and other admin tools (such as Remote Console, Oracle Enterprise Manager, and SNMP) use the management network. Customers are expected to provide the management network. Use a gigabit Ethernet, or faster, connection for optimal replication and performance.
Encryption endpoints may also connect to the management network if the service network is inappropriate due to its isolation properties.
For additional security and to isolate LAN traffic, you may want to use Virtual Local Area Networks (VLANs) to connect to the management network.
Service Network
The service network connects the OKM cluster to the agents. It isolates key retrievals from other network traffic.
Note:
Agents may connect to the OKM cluster by the management network, if desired.The KMA's service network interfaces can optionally be aggregated (see "KMA Service Port Aggregation").
ILOM/ELOM
Your Oracle support representative accesses the ILOM or ELOM for initial KMA setup. The NET MGT port of the KMA is for access to the Integrated Lights Out Manager (ILOM) on SPARC T7-1, Netra SPARC T4-1, or Sun Fire x4170 M2 servers or the Embedded Lights Out Manager (ELOM) on the Sun Fire x2100 M2 and Sun Fire x2200 M2 servers.
The service processor network (ELOM or ILOM) should have spanning tree turned off or disabled.
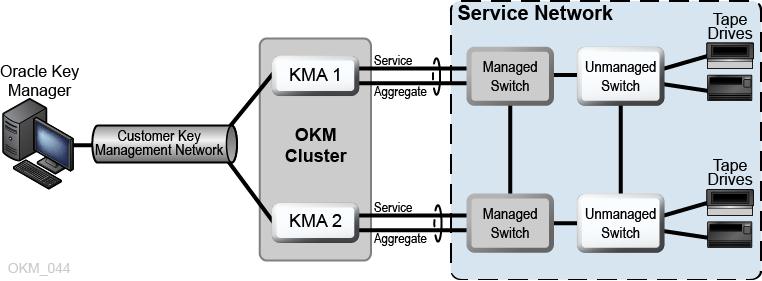
Managed Switches
Oracle recommends a managed switch for connecting KMAs to encryption agents on private service networks. A managed switch supplies connectivity to unmanaged switches and to routers for the wide area service network.
Managed switches improve serviceability through better switch diagnostics and service network troubleshooting, and can minimize single points of failure on the service network through use of redundant connections and the spanning tree protocol.
Supported Managed Switch Models
Oracle tests, recommends, and provides configuration guidance for Brocade ICX 6430, 3COM Switch 4500G 24-Port (3CR17761-91), and Extreme Networks Summit X150-24t.
The Brocade switch is included in the Switch Accessory Kit (see "Switch Accessory Kit Order Numbers").
You can aggregate the physical Ethernet interfaces into a single virtual interface. Aggregating these ports provides additional availability — if a failure occurs with either port, the other port maintains connectivity.
Ensure the Ethernet switch ports have the correct configuration. The switch ports should be set to auto-negotiate for full duplex and gigabit speed.
For service port aggregation configuration instructions, your Oracle support representative can consult the Oracle Key Manager 3 Installation and Service Manual (internal only).
You can mirror ports to use a network analyzer in the service network. Ports can be mirrored on Brocade ICX 6430 switches. For configuration instructions, your Oracle support representative can consult the Oracle Key Manager 3 Installation and Service Manual (internal only).
Managed Switch Configuration Example
In Figure 1-7, if either a KMA or managed switch should fail, the drives still have a communication path to the other KMA.The managed switches are connected to unmanaged switches containing redundant paths requiring a spanning tree configuration. (Managed switches must be enabled for spanning tree whenever the cabling includes redundancy.) The service network interfaces are aggregated into a single virtual interface (see "KMA Service Port Aggregation").
Network Routing Configuration
The routing configuration of a KMA effects responses to tape drive discovery requests. Mistakes in the routing configuration can lead to erroneous cluster information being provided to encryption agents. This could cause agents to attempt communication with KMAs that they cannot reach over the network.
When planning the OKM network, observe the following:
-
Use the KMA console network menu option to configure a route between sites. Do not configure a default route.
Note:
Oracle does not recommend starting with a multi-site service network topology. -
When planning for a multi-site service network, determine a subnet addressing scheme for the KMA service ports and drives. You must avoid duplicate network addresses and use of 172.18.18.x networks (a common convention).
-
Use of default gateway settings can affect failover performance. Consult a network engineer to plan for failover capability.
Part Numbers for OKM Components
Table 1-6 KMA Server Order Numbers
| Order Number | Description |
|---|---|
|
7115065 |
Oracle Key Manager 3 |
|
7114954 |
140-2 PCIe Card with FIPS support and level 3 security (for factory installation) |
|
7115395 |
140-2 PCIe Card with FIPS support and level 3 security This hardware security module is for use in SPARC KMAs only. |
Table 1-7 Switch Accessory Kit Order Numbers
| Order Number | Description |
|---|---|
|
7104584 |
Switch Accessory Kit (SAK). Includes 24-port managed switch and a rack power cord, two Ethernet cables, and switch mounting hardware. |
The switch can support a maximum of 22 tape drive agents. Additional switch accessory kits might be needed depending on the number of encrypting tape drives supported by the library.
Order Ethernet cables to connect the switch to encrypting tape drives.
Table 1-8 Ethernet Cable Order Numbers
| Order Number | Description |
|---|---|
|
CABLE10187033-Z-A |
8 feet CAT5e Ethernet cable (for factory installation) |
|
CABLE10187033-Z-N |
8 feet CAT5e Ethernet cable |
|
CABLE10187034-Z-A |
35 feet CAT5e Ethernet cable (for factory installation) |
|
CABLE10187034-Z-N |
35 feet CAT5e Ethernet cable |
|
CABLE10187037-Z-A |
55 feet CAT5e Ethernet cable (for factory installation) |
|
CABLE10187037-Z-N |
55 feet CAT5e Ethernet cable |
Table 1-9 Power Cable Part Numbers
| ATO Power Cord | PTO Equivalent | Description | Amps | Voltage | Cable |
|---|---|---|---|---|---|
|
333A-25-10-AR |
X312F-N |
Pwrcord, Argentina, 2.5m, IRAM2073, 10A,C13 |
10 |
250 |
180-1999-02 |
|
333A-25-10-AU |
X386L-N |
Pwrcord, Australian, 2.5m, SA3112, 10A,C13 |
10 |
250 |
180-1998-02 |
|
333A-25-10-BR |
X333A-25-10-BR-N |
Pwrcord, Brazil,2.5m,NBR14136, 10A, C13 |
10 |
250 |
180-2296-01 |
|
333A-25-10-CH |
X314L-N |
Pwrcord, Swiss,2.5m,SEV1011, 10A, C13 |
10 |
250 |
180-1994-02 |
|
333A-25-10-CN |
X328L |
Pwrcord, China,2.5m,GB2099, 10A, C13 |
10 |
250 |
180-1982-02 |
|
333A-25-10-DK |
X383L-N |
Pwrcord, Denmark,2.5m, DEMKO107, 10A,C13 |
10 |
250 |
180-1995-02 |
|
333A-25-10-EURO |
X312L-N |
Pwrcord, Euro,2.5m,CEE7/VII,10A, C13 |
10 |
250 |
180-1993-02 |
|
333A-25-10-IL |
X333A-25-10-IL-N |
Pwrcord, Israel,2.5m,SI-32, 10A,C13 |
10 |
250 |
180-2130-02 |
|
333A-25-10-IN |
X333A-25-10-IN-N |
Pwrcord, India,2.5m,IS1293,10A,C13 |
10 |
250 |
180-2449-01 |
|
333A-25-10-IT |
X384L-N |
Pwrcord, Italian,2.5m,CEI23, 10A,C13 |
10 |
250 |
180-1996-02 |
|
333A-25-10-KR |
X312G-N |
Pwrcord, Korea,2.5m,KSC8305,10A, C13 |
10 |
250 |
180-1662-03 |
|
333A-25-10-TW |
X332A-N |
Pwrcord, Taiwan,2.5m, CNS10917, 10A, C13 |
10 |
125 |
180-2121-02 |
|
333A-25-10-UK |
X317L-N |
Pwrcord, UK,2.5m,BS1363A, 10A,C13 |
10 |
250 |
180-1997-02 |
|
333A-25-10-ZA |
X333A-25-10-ZA-N |
Pwrcord, South Africa,2.5m,SANS164, 10A,C13 |
10 |
250 |
180-2298-01 |
|
333A-25-15-JP |
X333A-25-15-JP-N |
Pwrcord, Japan,2.5m,PSE5-15, 15A, C13 |
15 |
125 |
180-2243-01 |
|
333A-25-15-NEMA |
X311L |
Pwrcord, N.A./Asia,2.5m, 5-15P,15A, C13 |
15 |
125 |
180-1097-02 |
|
333A-25-15-TW |
X333A-25-15-TW-N |
Pwrcord, Taiwan,2.5M, CNS10917, 15A,C13 |
15 |
125 |
180-2333-01 |
|
333F-20-10-NEMA |
X320A-N |
Pwrcord, N.A./Asia,2.0m, 6-15P,10A, C13 |
10 |
250 |
180-2164-01 |
|
333F-25-15-JP |
X333F-25-15-JP-N |
Pwrcord, Japan,2.5m,PSE6-15, 15A, C13 |
15 |
250 |
180-2244-01 |
|
333J-40-15-NEMA |
X336L |
Pwrcord, N.A./Asia,4.0m, L6-20P,15A, C13 |
15 |
250 |
180-2070-01 |
|
333R-40-10-309 |
X332T |
Pwrcord, INTL,4.0m, IEC309-IP44, 10A,C13 |
10 |
250 |
180-2071-01 |
Table 1-10 Oracle Rack II (Redwood) Power Cord Part Numbers
| ATO Power Cord | PTO Equivalent | Description | Amps | Voltage | Cable |
|---|---|---|---|---|---|
|
SR-JUMP-1MC13 |
XSR-JUMP-1MC13-N |
Pwrcord, Jmpr,SR2,1.0m,C14RA,13A, C13 |
13 |
250 |
180-2379-01 |
|
SR-JUMP-2MC13 |
XSR-JUMP-2MC13-N |
Pwrcord, Jmpr,SR2,2.0m,C14RA,13A, C13 |
13 |
250 |
180-2380-01 |
Footnote Legend
Footnote 1: An exception can be made with the approval of Engineering, Professional Services, and Support Services.Footnote 2: Not all applications use IPv6 (for example, DNS). Therefore, IPv4 is still required.