1 Overview
This section gives an overview of the product and explains the general principles of application security.
Oracle Key Manager Overview
The Oracle Key Manager (OKM) creates, stores, and manages encryption keys. It consists of the following components:
-
Key Management Appliance (KMA) – A security-hardened box that delivers policy-based Lifecycle Key Management, authentication, access control, and key provisioning services. As a trusted authority for storage networks, the KMA ensures that all storage devices are registered and authenticated, and that all encryption key creation, provisioning and deletion is in accordance with prescribed policies.
-
Oracle Key Manager GUI – A Graphical User Interface that is executed on a workstation and communicates with the KMA over an IP network to configure and manage the OKM. The Oracle Key Manager GUI must be installed on a customer-provided workstation.
-
Oracle Key Manager CLIs – Two Command Line Interfaces that are executed on a workstation and communicate with the KMA over an IP network to automate commonly issued administrative operations. The Oracle Key Manager CLIs must be installed on a customer-provided workstation.
-
OKM Cluster – The full set of KMAs in the system. All of these KMAs are aware of each other and replicate information to each other.
-
Agent – A device or software that performs encryption, using keys managed by the OKM Cluster. A StorageTek encrypting tape drive is an example of an agent. Agents communicate with KMAs using the KMS Agent Protocol. The Agent API is a set of software interfaces that are incorporated into the agent hardware or software.
The OKM uses TCP/IP networking for the connections between KMAs, Agents, and workstations where you run the Oracle Key Manager GUI and CLIs. To provide flexible network connections, three interfaces are provided for network connections on each KMA:
-
The management connection – Intended for connection to the customer network
-
The service connection – Intended for connection to the agents
-
The ILOM/ELOM connection – Intended for connection to the ILOM or ELOM on the KMA
See the example in the following image:
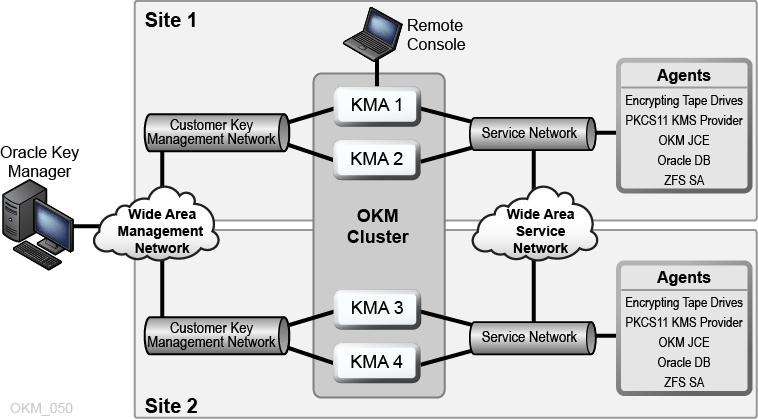
Description of the illustration ''okm_050.png''
General Security Principles
The following principles are fundamental to using any application securely.
One of the principles of good security practice is to keep all software versions and patches up to date. The latest Oracle Key Manager upgrade packages and installers are available on the My Oracle Support website: http://support.oracle.com.
Restrict Network Access to Critical Services
Keep your business applications behind a firewall. The firewall provides assurance that access to these systems is restricted to a known network route, which can be monitored and restricted, if necessary. As an alternative, a firewall router substitutes for multiple, independent firewalls.
Follow the Principle of Least Privilege
The principle of least privilege states that users should be given the least amount of privilege to perform their jobs. Over-ambitious granting of responsibilities, roles, grants, and so on especially earlier on in an organization's life cycle when people are few and work must be done quickly, often leaves a system wide open for abuse. User privileges should be reviewed periodically to determine relevance to current job responsibilities.
System security stands on three legs: good security protocols, proper system configuration, and system monitoring. Auditing and reviewing audit records address this third requirement. Each component within a system has some degree of monitoring capability. Follow audit advice in this document and regularly monitor audit records.
Keep Up To Date on Latest Security Information
Oracle continually improves its software and documentation. Check the My Oracle Support website yearly for revisions.