9 Configuring High Availability for Identity Federation Components
This chapter describes Oracle Access Management Identity Federation 11gR2 high availability. See Integration with Access Manager 11gR2 in the Oracle Fusion Middleware Integration Guide for Oracle Identity Management Suite for additional details on Identity Federation.
This section includes the following topics:
-
Section 9.2, "Identity Federation High Availability Concepts"
-
Section 9.3, "Identity Federation High Availability Configuration"
-
Section 9.4, "Identity Federation Failover and Expected Behavior"
-
Section 9.5, "Troubleshooting Identity Federation High Availability"
9.1 Identity Federation Component Architecture
Identity Federation service provides single sign-on capabilities to Oracle Access Management Access Manager in a multiple-domain identity network. It supports the broadest set of federation standards, enabling users to federate in heterogeneous environments and business associations, whether or not they implement other Oracle Identity Management products in their solution set.
Only Identity Federation 11g Release 2 supports the Service Provider (SP) functionality. For Identity Provider (IDP) support, use Identity Federation 11g Release 1.
Acting as an SP, Identity Federation enables you to manage your resources while offloading user authentication to an IDP, without having to synchronize users across security domains out of band. Once authenticated at the IDP, the SP can enable or deny access to users for the SP's applications, depending on local access policies.
If a user no longer has an account with the IDP, the federation is terminated and cross-domain single sign-on for that user is automatically disabled.
Key features of Identity Federation include support for:
-
Multiple leading federation protocols such as SAML 1.x and SAML 2.0
-
Cross-protocol single sign-on and sign-out
-
X.509 certificate validation
-
Native Integration with Access Manager
-
Integration with any LDAP Directory supported by Access Manager
Figure 9-1 Identity Federation Architecture
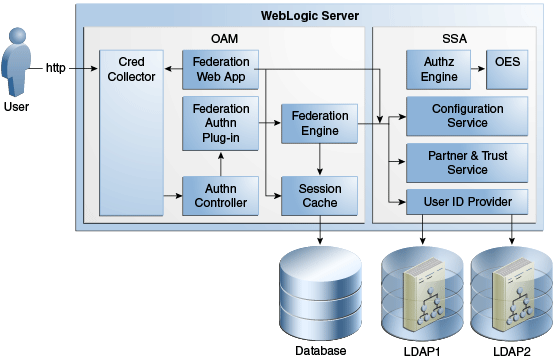
Description of "Figure 9-1 Identity Federation Architecture"
For more details about how Identity Federation integrates with Access Manager, see Integration with Access Manager 11gR2 in Oracle Fusion Middleware Integration Guide for Oracle Identity Management Suite.
9.1.1 Identity Federation Component Characteristics
Identity Federation is an Oracle Access Management component providing SP functionality for Cross Domain Single Sign-On. It enables Oracle Access Management to delegate user authentication to a remote Identity Provider partner. It supports a broad set of federation standards such as SAML 1.x, SAML 2.0.
9.1.1.1 Runtime Processes
Identity Federation is part of the Access Manager J2EE application deployed on the WebLogic Server.
Because Identity Federation runs within the Access Server, it has the same runtime processes as Access Manager.
9.1.1.2 Process Lifecycle
Identity Federation follows the same process lifecycle as Access Manager.
9.1.1.3 Request Flow
See Architecture in Oracle Fusion Middleware Integration Guide for Oracle Identity Management Suite for information on the Identity Federation request flow.
9.1.1.4 Configuration Artifacts
The Identity Federation configuration artifacts include the following files.
-
DOMAIN_HOME/config/fmwconfig/oam-config.xml — configuration file containing instance-specific information.
-
DOMAIN_HOME/config/fmwconfig/oam-policy.xml — present only when OES Micro SM is not being used.
-
DOMAIN_HOME/config/fmwconfig/servers/instanceName/logging.xml — Logging config
-
DOMAIN_HOME/config/fmwconfig/cwallet.sso — stores passwords that are used to connect to identity stores, database, and other entities. This is not for end user passwords.
-
DOMAIN_HOME/config/fmwconfig/.oamkeystore — keystore containing keys and certificates OAM/Identity Federation owns
-
DOMAIN_HOME/config/fmwconfig/amtruststore — keystore containing the trust anchors used for X509 cert validation
-
DOMAIN_HOME/config/fmwconfig/amcrl.jar — zip file containing CRLs used for certificate revocation
-
DOMAIN_HOME/config/fmwconfig/default-keystore.jks — OWSM keystore used to store keys and certificates used by the OWSM Agent, as well as trusted anchors used to validate X.509 certificates for WSS operations
-
DOMAIN_HOME/config/fmwconfig/servers/servername/dms_config.xml — eventing configuration file
-
DOMAIN_HOME/config/fmwconfig/component_events.xml — audit definition
-
DOMAIN_HOME/config/fmwconfig/system-jazn-data.xml — Administration Console permissions
-
DOMAIN_HOME/config/fmwconfig/cacerts.jks — keystore containing Certificate Authority certificates.
9.1.1.5 External Dependencies
The following external components are required for Identity Federation server to function:
-
WebLogic Server
-
Administration Server
-
Managed Server
-
-
LDAP based Identity Store
-
User Identity Repository
-
LDAP access abstracted by User/Role API.
Note:
Access Manager always connects to one Identity store, which can be a physical server or a load balancer IP. If the primary is down, Access Manager reconnects and expects the load balancer to connect it to the secondary.
-
-
OCSP Responder Service
-
Real-time X.509 Certification Validation
-
-
RDBMS Policy Store/Coherence Store
-
Policy (Authentication and Authorization) Repository
-
RDBMS access abstracted by the Access Manager policy engine
-
-
Oracle Entitlements Server (though OAM)
-
Federation Data Cache
-
For session and runtime information. You can configure Identity Federation to use the memory store or RDBMS store for this. However, in a high availability environment you must use a RDBMS store.
-
The session information related to federation, partners where the user is signed in, and protocol data is stored in the session and cache. You can configure Identify Federation to use either a memory store or an RDBMS store for this data. For high availability environments, you must use a RDBMS store.
9.1.1.6 Identity Federation Log File Location
The default location of the WebLogic Server log file is:
WEBLOGIC_SERVER_HOME/user_projects/domains/domainName/servers/serverName/logs/ serverName-diagnostic.log
Use the Oracle Enterprise Manager Fusion Middleware Control to view the log files.
9.2 Identity Federation High Availability Concepts
This section provides conceptual information about using Identity Federation in a high availability two-node cluster.
This section includes the following topics:
9.2.1 Identity Federation High Availability Architecture
Figure 9-2 shows the Identity Federation high availability architecture in an active-active configuration.
Figure 9-2 Identity Federation in a High Availability Architecture
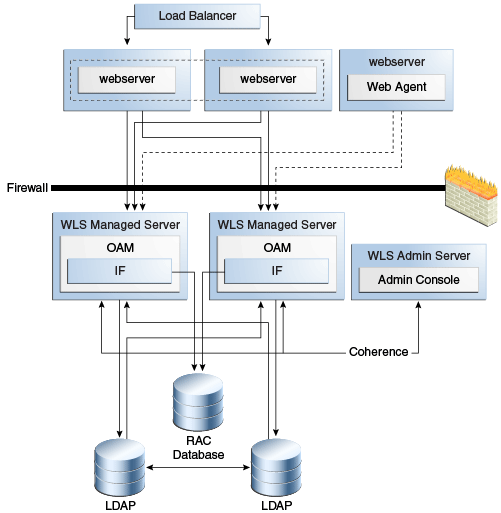
Description of "Figure 9-2 Identity Federation in a High Availability Architecture"
In Figure 9-2, the hardware load balancer receives incoming authentication requests and routes them a web server in the web tier. These hosts have Oracle HTTP Server installed. The Oracle HTTP Server forwards requests to the WebLogic managed servers using WebLogic plugin mod_wl_ohs.conf.
The load balancing router should use session stickiness for HTTP traffic only.
The two managed servers that host the Oracle Access Server application are configured in a cluster which enables the Access Servers to work in active-active mode.
If a federation scheme protects the resource being accessed, OAM uses the Federation Engine to authenticate the user.
The LDAP directories that the Federation Engine uses are deployed in a cluster.
An Oracle RAC database provides high availability in the data tier.
The WebLogic Administration Server runs on the same host as one of the managed servers and deploys the Administration Console, Oracle Enterprise Manager Fusion Middleware Control, and the Oracle Access Management Console.
9.2.1.1 Starting and Stopping the Cluster
Identity Federation clusters start and stop in the same manner as OAM clusters. For more information, see Section 9.2.1.1, "Starting and Stopping the Cluster."
9.2.1.2 Cluster-Wide Configuration Changes
Configuration changes made through one cluster member propagate automatically to all others because the configuration is stored in the shared database. See Section 9.2.1.2, "Cluster-Wide Configuration Changes" for additional information.
9.2.2 Identity Federation Prerequisites
Because Identity Federation is part of OAM, it has the same prerequisites as OAM. See Section 9.2.1.2, "Cluster-Wide Configuration Changes" for more information.
Note:
Oracle requires that you synchronize the system clocks on the cluster nodes when you are using Identity Federation in a high availability deployment.9.3 Identity Federation High Availability Configuration
As a feature that runs on OAM servers, you configure Identity Federation high availability as part of OAM high availability. To configure OAM high availability, see Section 6.4, "Access Manager High Availability Configuration Steps". Note the following special considerations as you configure Identity Federation for high availability.
9.3.1 Setting the Hostname and Port
Oracle recommends that you set the host name and port in the OAM/Identity Federation configuration to the load balancer host and port. If you do not, errors occur during Single Sign-On/Logout operation. Oracle also recommends that you use virtualized hostnames in OAM configuration so that, after a restore on a different host, the corresponding agent configuration does not require updates.
9.3.2 Changing the ProviderID Value
The ProviderId is a string that uniquely identifies the SP. The ProviderId for all servers in a cluster must be identical. The ProviderId defaults to http://host:port/oam/fed/ at installation. If necessary, change or set this value after installation; do not change it during operation.
9.3.3 Tuning Identity Federation Parameters
You can tune the connection to the RAC database that stores session data.
If you use the artifact profile, use WLST to tune SOAP connection details.
Identity Federation parameters that you can set include the following:
Outgoing SOAP connection parameters that you can tune include:
-
Max connections total
-
Max connections per host
RDBMS Transient Store Asynchronous Settings
Table 9-0 describes RDBMS transient store asynchronous settings.
Table 9-1 RDBMS Transient Store Asynchronous Settings
| Setting | Description |
|---|---|
|
rdbmsasynchronousmanagerinterval |
Execution interval for the asynchronous thread manager |
|
rdbmsasynchronousmanagersleep |
Sleep interval for the asynchronous thread manager, to check if execution should occur |
|
rdbmsasynchronousqueuesize |
Size of the queue containing RDBMS operations of the same type (create session, create artifact) |
|
rdbmsasynchronousqueuesleep |
Sleep time before the calling thread can retry adding an operation to a queue if the queue is full |
|
rdbmsasynchronousqueueretries |
Number of retries when attempting to add an operation to the queue if the queue is full |
|
rdbmsasynchronousthreadcore |
Number of default threads in the RDBMS thread executor module for RDBMS asynchronous operations |
|
rdbmsasynchronousthreadkeepalive |
Maximum amount of time to keep the extra threads in the RDBMS thread executor module for RDBMS asynchronous operation |
|
rdbmsasynchronousthreadmax |
Maximum number of threads in the RDBMS thread executor module for RDBMS asynchronous operation |
|
rdbmsasynchronousthreadpolicy |
Thread policy of the RDBMS thread executor module for RDBMS asynchronous operation |
|
rdbmsasynchronousthreadqueuesize |
Thread queue size of the of the RDBMS thread executor module for RDBMS asynchronous operation |
RDBMS Artifact memory cache settings
Table 9-0 describes RDBMS Artifact memory cache settings, used in conjunction with the RDBMS asynchronous module.
Table 9-2 RDBMS Artifact memory cache settings
| Setting | Description |
|---|---|
|
artifactrdbmscachetimeout |
Time to live in the memory cache |
|
artifactrdbmsretries |
Maximum number of time to retry to locate an entry in RDBMS before returning a failure |
|
artifactrdbmssleep |
Sleeping time between retrying lookup operations |
Table 9-3 describes RDBMS Memory cache setting, with the exception of artifact settings (see Table 9-2).
Table 9-3 RDBMS Memory Cache Settings
| Setting | Description |
|---|---|
|
transientrdbmscachesize |
Cache size |
|
transientrdbmscachetimeout |
Time to live for cache objects before becoming invalid and forcing an RDBMS lookup operation when an object is searched |
Interval for the RDBMS cleanup thread
The setting for the RDBMS cleanup thread interval is rdbmscleanupinterval, which indicates the sleep interval of the thread that removes expired entries from Identity Federation database tables.
9.4 Identity Federation Failover and Expected Behavior
This section describes steps for performing failover operations on Identity Federation instances deployed in a high availability environment and their expected behavior.
To perform a test of a failover of an Identity Federation instance and to check the status of Identity Federation:
-
Log in to the Administration Server console. Go to Home, Summary of Security Realms, myrealm, Users and Groups, Realm Roles, then Edit Global Role. Add the group
OAMAdminstrators. -
Log in to the OAM Administration Console. Go to System Configuration, Common Settings, Available Services then enable Identity Federation.
-
Set up Identity Federation between an IDP instance (which can be an Oracle Identity Federation 11g Release 1 instance) and this Identity Federation 11gRelease 2 instance that is functioning as an SP.
-
Integrate with OAM 11gR2 and protect a resource with OIFScheme. Follow the steps in Integration with Access Manager 11gR2 in Oracle Fusion Middleware Integration Guide for Oracle Identity Management Suite.
-
Shut down one of the two managed servers and try to access the protected resource.
-
When the IDP login page appears, restart the managed server that you stopped in the previous step, shut down the managed server that was running, and try to complete the operation.
9.5 Troubleshooting Identity Federation High Availability
Use the following tips to troubleshoot Identity Federation issues:
-
Identity Federation logs its messages in the Managed Server log files, for example:
WEBLOGIC_SERVER_HOME/user_projects/domains/domainName/servers/serverName/logs/ serverName-diagnostic.log
-
Verify that the hostname and port in the Identity Federation server configuration are set to the load balancer host and port, otherwise errors occur during Single Sign-On operation.
-
If system clocks on the computers which IDP and SP run on have different times, errors occur during Single Sign-On. Fix this by setting the system clocks to have the same time or by adjusting the server drift using the Server Properties page in Oracle Enterprise Manager Fusion Middleware Control.
-
The
ProviderIdstring uniquely identifies the IDP/SP and must be identical for all servers in a cluster. TheProviderIdstring defaults to:http://host:port/oam/fedat installation. If you must changeProviderId, change it after installation, not during an operation.