Controlling Network Access
Computers are often part of a network of computers that allows connected computers to exchange information. Networked computers can access data and other resources from other computers on the network. Although computer networks create a powerful and sophisticated computing environment, networks also complicate computer security.
For example, within a network of computers, individual systems allow the sharing of information. Unauthorized access is a security risk. Because many people have access to a network, unauthorized access is more likely, especially through user error. A poor use of passwords can also allow unauthorized access.
Network Security Mechanisms
Network security is usually based on limiting or blocking operations from remote systems. The following figure describes the security restrictions that you can impose on remote operations.
Figure 1 Security Restrictions for Remote Operations
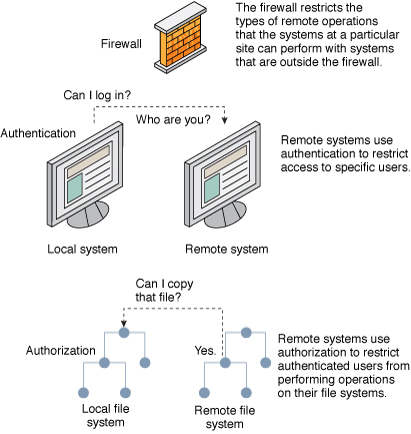
Authentication and Authorization for Remote Access
Authentication is a way to control access when users try to access a remote system. Authentication can be set up at both the system level and the network level. After a user has gained access to a remote system, authorization is a way to restrict operations that the user can perform. The following table lists the services that provide authentication and authorization.
|
A possible substitute for Secure RPC is the Oracle Solaris privileged port mechanism. A privileged port is assigned a port number less than 1024. After a client system has authenticated the client's credential, the client builds a connection to the server by using the privileged port. The server then verifies the client credential by examining the connection's port number.
Clients that are not running Oracle Solaris software might be unable to communicate by using the privileged port. If the clients cannot communicate over the port, you see an error message that appears similar to the following:
"Weak Authentication NFS request from unprivileged port"
Firewall Systems
You can set up a firewall system to protect the resources in your network from outside access. A firewall system is a secure host that acts as a barrier between your internal network and outside networks. The internal network treats every other network as untrusted. You should consider this setup as mandatory between your internal network and any external networks, such as the Internet, with which you communicate.
A firewall acts as a gateway and as a barrier. As a gateway, it passes data between the networks. As a barrier, it blocks the free passage of data to and from the network. A user on the internal network must log in to the firewall system to access host systems on remote networks. Similarly, a user on an outside network must first log in to the firewall system before being granted access to a host system on the internal network.
A firewall can also be useful between some internal networks. For example, you can set up a firewall or a secure gateway computer to restrict the transfer of packets by address or by protocol. You could then allow packets for transferring mail but not allow packets for the ftp command.
In addition, all electronic mail that is sent from the internal network is first sent to the firewall system. The firewall then transfers the mail to a system on an external network. The firewall system also receives all incoming electronic mail, and distributes the mail to the systems on the internal network.
 | Caution - Even if you maintain strict and rigidly enforced security on the firewall, if you relax security on other systems on the network, an intruder who can break into your firewall system can then gain access to all the other systems on the internal network. |
A firewall system should not have any trusted hosts. A trusted host is a host system from which a user can log in without being required to supply a password. A firewall system should not share any of its file systems, or mount any file systems from other servers.
IPsec and the Packet Filter feature of Oracle Solaris can provide firewall protection. For more information about protecting network traffic, see Securing the Network in Oracle Solaris 11.3.
Encryption and Firewall Systems
Unauthorized users from outside a network can corrupt or destroy the data in packets by capturing the packets before they reach their destination and injecting arbitrary data into the contents before sending the packets back on their original course. This procedure is called packet smashing.
On a local area network, packet smashing is impossible because packets reach all systems, including the server, at the same time. Packet smashing is possible on a gateway, however, so make sure that all gateways on the network are protected.
The most dangerous attacks affect the integrity of the data. Such attacks involve changing the contents of the packets or impersonating a user.
Other attacks might involve eavesdropping but do not compromise data integrity or impersonate a user. An eavesdropper records conversations for later replay. Although eavesdropping attacks do not attack data integrity, the attacks do affect privacy. You can protect the privacy of sensitive information by encrypting data that goes over the network.
-
To encrypt remote operations over an insecure network, see Chapter 1, Using Secure Shell in Managing Secure Shell Access in Oracle Solaris 11.3.
-
To encrypt and authenticate data across a network, see Chapter 2, Kerberos on Oracle Solaris in Managing Kerberos and Other Authentication Services in Oracle Solaris 11.3.
-
To encrypt IP datagrams, see Chapter 8, About IP Security Architecture in Securing the Network in Oracle Solaris 11.3.