1 Delegated Administrator Overview
This chapter provides an overview of Oracle Communications Delegated Administrator.
Introduction to Delegated Administrator
The Delegated Administrator utility and console let you provision users, groups, domains, and resources in a LDAP directory used by Communications Suite applications such as Oracle Communications Messaging Server, Oracle Communications Calendar Server, Oracle Communications Instant Messaging Server, and Oracle Communications Contacts Server.
Delegated Administrator provisions the directory to support Messaging Server, Calendar Server, Instant Messaging, and Contacts Server.
With Delegated Administrator, you can distribute provisioning tasks to lower-level administrators who have the authority to manage specified organizations in the LDAP directory. The power to delegate user administration offers the following advantages:
-
Allows you to create organizations in the directory structure that can be managed and provisioned as distinct (or unique) units. These organizations can contain users belonging to customer businesses, corporate departments, or other groups.
-
Distributes among many administrators the potentially time-consuming responsibility for provisioning a large directory. Tens or hundreds of administrators can manage organizations within a directory that may include thousands or millions of users.
Delegated Administrator provides two interfaces for provisioning users and organizations in the directory.
The Delegated Administrator utility is a set of command-line tools for provisioning Messaging Server, Calendar Server, Instant Messaging, and Contacts Server organizations, users, groups, and Calendar resources.
Note:
The Delegated Administrator utility does not offer commands for creating the Service Provider roles and organizations described in this book. To create and manage these roles and organizations, you must use the Delegated Administrator console.You invoke the utility with the commadmin command.
For information about the syntax and options available with the commadmin command, see "Delegated Administrator Reference".
The Delegated Administrator console is a graphical user interface (GUI) for provisioning Messaging Server, Calendar Server, Instant Messaging, and Contacts Server organizations, users, groups, and Calendar resources.
For information on how to use the console, see the Delegated Administrator console online help.
Delegated Administrator LDAP Attributes
Delegated Administrator enables you to provision users by modifying the LDAP directory. You do not need to modify the directory directly. However, it can be useful to understand attributes added to user entries and higher-level nodes in the directory.
For information about the LDAP schema object classes and attributes that support Delegated Administrator, see the discussion about Delegated Administrator LDAP object classes and attributes in Communications Suite Schema Reference.
Communications Suite Schema Reference also defines the object classes and attributes that support the other Communications Suite components: Messaging Server, Calendar Server, Instant Messaging, Contacts Server, Address Book, and Communications Express.
Note:
When using the Delegated Administrator utility or the Delegated Administrator console, you should also run the Referential Integrity plug-in because that plug-in ensures that when entries are removed, all attributes that contain their DN are also removed. See the Maintaining Referential Integrity documentation in Oracle Fusion Middleware Administration Guide for Oracle Directory Server Enterprise Edition 11 for more information.Configuration Choices for LDAP Directory Access, Schema, and Access Manager
This section discusses the configuration choices you have for configuring direct LDAP access, schema, and Access Manager.
Direct LDAP Access to the Directory
By default, Delegated Administrator accesses the directory through direct LDAP calls. By using direct LDAP access, Delegated Administrator allows the following configuration choices:
-
You can provision objects in a Schema 1 or Schema 2 directory.
-
You can use Access Manager (Realm mode) with the Communications Suite products (including Delegated Administrator).
-
You can run Delegated Administrator, and any other Communications Suites product, without installing or using Access Manager.
To take advantage of these choices, you must:
-
Choose whether to use Schema 1 or Schema 2 when you run the Directory Server Preparation Tool, comm_dssetup.pl.
-
Select Direct LDAP access to the directory (DL) when you run the Delegated Administrator configuration program, config-commda.
Directory Access Through Access Manager (Legacy Mode)
You can configure Delegated Administrator to access the directory using Access Manager in Legacy mode.
This access method is intended for users of previous releases of Delegated Administrator who are upgrading to the current release and want to continue to use Access Manager in Legacy mode. Support for Access Manager 7.x and Sun OpenSSO 8.x has been deprecated. Delegated Administrator optionally uses Access Manager or Sun OpenSSO for single sign-on, authentication, and policy options.
You configure this access method by selecting Access Manager LDAP access (AM) when you run the Delegated Administrator configuration program, config-commda.
In the Access Manager (Legacy Mode) access method:
-
Access Manager (Legacy mode) must be installed. If you choose this access method, Delegated Administrator cannot be configured or run without Access Manager.
-
Access Manager (Realm mode) cannot be installed. With this access method, Delegated Administrator is not compatible with Access Manager in Realm mode.
-
The Delegated Administrator server must use the same Web container as Access Manager. The Delegated Administrator configuration program asks for Web container information after it asks for the Access Manager base directory.
LDAP Directory Access, Schema, and Access Manager Configuration Summary
Table 1-1 shows the configurations permitted by Delegated Administrator for LDAP directory access, schema choice, and Access Manager.
Table 1-1 LDAP Directory Access, Schema, and Access Manager Configurations
| LDAP Directory Access | Schema | Access Manager Choice |
|---|---|---|
|
Direct LDAP access |
Schema 2 |
Access Manager (Realm mode) |
|
Direct LDAP access |
Schema 2 |
Access Manager not installed |
|
Direct LDAP access |
Schema 1 |
Access Manager (Realm mode) |
|
Direct LDAP access |
Schema 1 |
Access Manager not installed |
|
Access Manager (Legacy mode) |
Schema 2 |
Access Manager (Legacy mode) |
Scenarios for Provisioning Users
Depending on your business needs you can create a simple directory structure managed by a single administrator, or a multi-tier directory hierarchy in which provisioning and management tasks are delegated to lower-level administrators.
This section summarizes three scenarios of increasing complexity. It then describes the administrator roles and directory structures Delegated Administrator provides to support the requirements of these scenarios.
One-Tier Hierarchy
In this scenario, a company or organization might support hundreds or thousands of employees or users. All users are grouped in a single organization. A single administrator role views and manages the entire group. There is no delegation of administrative tasks.
Figure 1-1 shows an example of the administrator role in a single-organization, one-tier hierarchy.
Figure 1-1 Administrator Role in a One-Tier Hierarchy
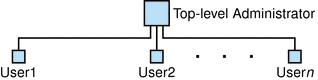
Description of ''Figure 1-1 Administrator Role in a One-Tier Hierarchy''
In this one-tier hierarchy, the administrator is called the Top-Level Administrator (TLA).
In the example shown in Figure 1-1, the TLA directly manages and provisions the users (User1, User2, up to Usern).
If you have one organization in your directory, the TLA is the only administrator you need.
For more information, see:
Two-Tier Hierarchy
In this scenario, a large company such as an Internet Service Provider (ISP) provides services to businesses. Each business has its own unique domain, which may contain thousands or tens of thousands of users.
Instead of relying on a single Top-Level Administrator (TLA) to manage and provision all the domains, this scenario supports the delegation of tasks to lower-level administrators.
In a two-tier hierarchy, the directory contains multiple organizations. A separate organization is created for each hosted domain.
Each organization is assigned to an Organization Administrator (OA). The OA is responsible for the users in that organization. An OA cannot view or modify directory information outside the OA's own organization.
Figure 1-2 shows an example of the administrator roles in a two-tier hierarchy.
Figure 1-2 Administrator Roles in a Two-Tier Hierarchy
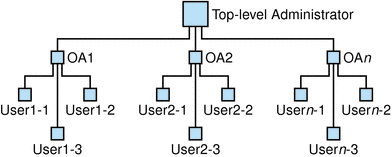
Description of ''Figure 1-2 Administrator Roles in a Two-Tier Hierarchy''
In the example shown in Figure 1-2, the TLA creates and manages OA1, OA2, up to OAn. Each OA manages the users in one organization.
If you need multiple organizations in your directory, you should create the OAs to administer the organizations and their users.
For more information, see:
Three-Tier Hierarchy
In this scenario, a company, such as an ISP, offers services to hundreds or thousands of small businesses, each of which requires its own organization.
The ISP may support millions of end-users requiring mail services. Moreover, the ISP may work with third-party resellers who manage the end-user businesses.
Each day, dozens of organizations might have to be added to the directory.
In a two-tier hierarchy, the TLA would have to create all these organizations.
In a three-tier hierarchy, management tasks are delegated to a second level of administrators. This second level of delegation can ease the management of a large customer base supported by a large LDAP directory.
To support this hierarchy, Delegated Administrator introduces a role, the Service Provider Administrator (SPA).
The SPA's scope of authority lies between that of the Top-Level Administrator (TLA) and the Organization Administrator (OA).
Figure 1-3 shows an example of the administrator roles in a three-tier hierarchy.
Figure 1-3 Administrator Roles in a Three-Tier Hierarchy
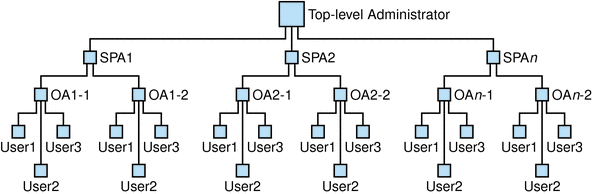
Description of ''Figure 1-3 Administrator Roles in a Three-Tier Hierarchy''
In a three-tier hierarchy, the TLA delegates administrative authority to Service Provider Administrators (SPAs). The SPAs can create subordinate organizations for customers and assign Organization Administrators (OAs) to manage users in those organizations.
If you need multiple organizations that are themselves divided into subgroups or organizations, you can use a three-tier hierarchy that implements the TLA, SPA, and OA roles.
See "Service Provider Administrator and Service Provider Organizations" for information about the SPA role.
Administrator Roles and the Directory Hierarchy
This section shows sample Directory Information Trees that implement one- and two-tier hierarchies. It then describes the tasks that can be performed by the Top-Level Administrator and Organization Administrator.
Directory Structure Supporting a One-Tier Hierarchy
When you configure Delegated Administrator by running the configuration program, config-commda, you create a Top-Level Administrator (TLA) and a default organization.
One-Tier Hierarchy: Default Organization Under the Root Suffix
By default, the configuration program places the default organization under the root suffix.
Figure 1-4 shows a sample Directory Information Tree organized in a one-tier hierarchy (default configuration).
Figure 1-4 One-Tier Hierarchy: Sample Directory Information Tree (default)
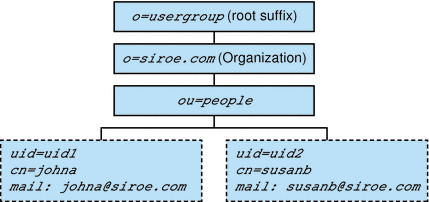
Description of ''Figure 1-4 One-Tier Hierarchy: Sample Directory Information Tree (default)''
One-Tier Hierarchy: Default Organization at the Root Suffix
When you run the configuration program, config-commda, you can choose to create the default organization at the root suffix instead of under it. For configuration details, see Delegated Administrator Installation and Configuration Guide.
In this situation, the Directory Information Tree will look similar to the one shown in Figure 1-5.
However, if you create the default organization at the root suffix, this configuration of the LDAP directory cannot support multiple hosted domains. To support hosted domains, the default organization must be under the root suffix.
Figure 1-5 shows a sample one-tier hierarchy in which the default organization is created at the root suffix.
Figure 1-5 One-Tier Hierarchy: Default Organization at Root Suffix
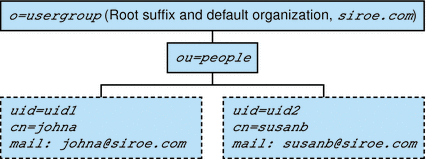
Description of ''Figure 1-5 One-Tier Hierarchy: Default Organization at Root Suffix''
Top-Level Administrator
The TLA has the authority to perform the following tasks:
-
Create, delete, and modify organizations.
In the example shown in Figure 1-6, the TLA can modify or delete siroe.com or sesta.com and can create additional organizations.
In this example, the two organizations are also unique (hosted) domains.
-
Create, delete, and modify users.
-
Create, delete, and modify groups.
-
Create, delete, and modify Calendar resources.
-
Assign OA roles to users. For example, the TLA could assign an OA role to the user johna in the siroe.com organization.
The TLA also can remove the OA role from a user.
-
Assign TLA roles to other users. The TLA also can remove the TLA role from a user.
The TLA can perform the preceding tasks by using the Delegated Administrator console or by executing Delegated Administrator utility (commadmin) commands. For a description of the commadmin commands, see "Delegated Administrator Reference".
-
Assign service packages to organizations.
See "Service Packages" for information on service packages.
The TLA can assign specified types of service packages to an organization and determine the maximum number of each package that can be used in that organization.
For example, the TLA could assign the following service packages:
-
In the siroe.com organization:
1,000 gold packages
500 platinum packages
-
In the sesta.com organization:
2,000 silver packages
1,500 gold packages
100 platinum packages
-
Service Provider Administrator Role
The SPA can perform the following tasks:
-
Create, delete, and modify shared and full organizations in the provider organization in which the SPA has administrative authority.
-
Modify or delete the DEF, HIJ, and SESTA organizations.
-
Create additional organizations under the VIS provider organization.
-
-
Create, delete, and modify users in any organization under the provider organization.
-
Create, delete, and modify groups in any organization under the provider organization.
-
Create, delete, and modify Calendar resources in any organization under the provider organization.
-
Assign OA roles to users.
The SPA also can remove the OA role from a user.
-
Assign the SPA role to other legitimate users under the provider organization (and remove the SPA role).
-
Allocate service packages to organizations.
See "Service Packages" for information about service packages.
The SPA can assign specified types of service packages to an organization and determine the maximum number of each package that can be used in that organization.
For example, the SPA could assign the following service packages:
-
In the DEF organization:
1,000 gold packages
500 platinum packages
-
In the HIJ organization:
2,500 topaz packages
500 platinum packages
500 emerald packages
1,000 ruby packages
-
In the SESTA organization:
2,000 silver packages
1,500 gold packages
100 platinum packages
-
The SPA can use the Delegated Administrator console to perform these tasks. In this release, the Delegated Administrator utility does not include command options to perform these tasks.
Note:
The TLA can modify or delete any existing shared organization or full organization. The TLA also can manage users in those organizations.The TLA can remove the SPA role from a user but cannot assign the SPA role through the console.
See "Administrator Roles and the Directory Hierarchy" for a complete description of the administrative tasks performed by the TLA.
Organization Administrator Role
The OA has the authority to perform the following tasks within the OA's organization:
-
Create, delete, and modify users
In the example shown in Figure 1-6, if the user johna is assigned the OA role in the siroe.com organization, johna can manage users in siroe.com
-
Create, delete, and modify groups
-
Create, delete, and modify Calendar resources
-
Assign the OA role to other users
-
Assign and remove service packages for users
The OA cannot perform any of these tasks for users, groups, or resources outside the OA's organization.
For example, if johna is the OA for siroe.com in Figure 1-6, johna cannot manage users, groups, or resources in sesta.com.
The OA can perform the preceding tasks by using the Delegated Administrator console or by executing Delegated Administrator utility (commadmin) commands.
For a list of the commadmin commands available to the OA, see "Delegated Administrator Reference".
Directory Structure Supporting a Two-Tier Hierarchy
After Delegated Administrator has been configured with the config-commda program, the TLA can create additional organizations, as shown in Figure 1-6.
Figure 1-6 shows a sample Directory Information Tree organized in a two-tier hierarchy.
Figure 1-6 Two-Tier Hierarchy: Sample Directory Information Tree
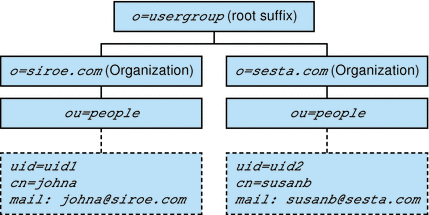
Description of ''Figure 1-6 Two-Tier Hierarchy: Sample Directory Information Tree''
For Former Users of iPlanet Delegated Administrator
Communications Suite Delegated Administrator is designed for provisioning users in an LDAP Schema 2 directory.
Users of previous versions of Messaging Server who have an LDAP Schema 1 directory may have used iPlanet Delegated Administrator, a deprecated tool. If you still have a Schema 1 directory, you should use iPlanet Delegated Administrator to provision users.
iPlanet Delegated Administrator uses different terms for the administrator roles than those currently used by Oracle Communications Delegated Administrator.
Table 1-2 lists and defines the administrator roles in each version of Delegated Administrator.
Note:
In this release of Delegated Administrator, the TLA cannot create provider organizations or business organizations under a provider organization.Table 1-2 Administrator Roles in iPlanet Delegated Administrator and Communications Suite Delegated Administrator
| iPlanet Delegated Administrator | Communications Suite Delegated Administrator Utility | Communications Suite Delegated Administrator Console | Definition |
|---|---|---|---|
|
Site Administrator |
Top-Level Administrator (TLA) |
Top-Level Administrator (TLA) |
Manages the entire directory supported by Delegated Administrator, including the organizations and users. |
|
None |
None in this release |
Service Provider Administrator (SPA) |
Manages a provider organization, the shared and full business organizations under the provider organization, and users in those business organizations. |
|
Domain Administrator |
Organization Administrator (OA) |
Organization Administrator (OA) |
Manages one organization and the users in that organization. |