Typical customer configurations include Replication Engines with redundant HBAs connected to the ports on the Oracle FS System Controller through redundant SAN switches. All ports of one HBA in the Replication Engine connect to the same SAN switch fabric, while all ports of the redundant HBA connect to an alternate SAN switch fabric.
Figure 1: Typical cabling connections of Oracle MaxRep Replication Engines
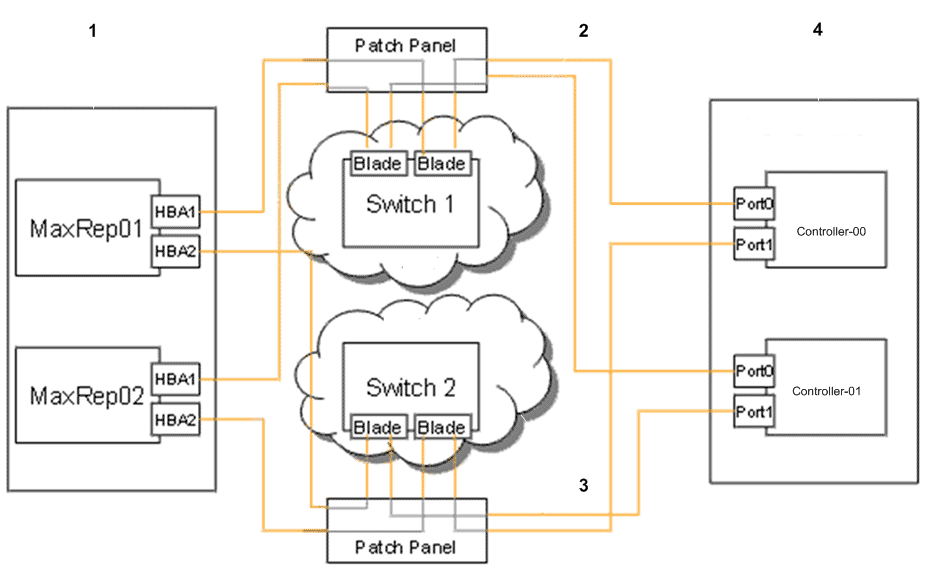
- Legend
1 MaxRep high availability cluster with two redundant Replication Engines 3 SAN fabric switch 2 2 SAN fabric switch 1 4 Oracle FS System Controllers
Following cables are required to connect the Replication Engine in the rack.
Type |
Description |
Cable length |
|---|---|---|
Fibre Channel (FC) patch cables |
Connect the FC ports at the back of the Replication Engine to the SAN Switch or SAN fabric to which the Oracle FS System is connected. These cables provide connectivity to the Oracle FS System for replication. |
50/125 optical FC have a distance limit of 164.04 feet (50 meters) for 8 Gb/s fabric speed. |
Ethernet cables |
Connect the Ethernet ports on the Replication Engine to management network switches for management and to create NIC bonding for port virtualization. |
1Gb/s Twisted Pair 10 Gb/s Twisted Pair 1 Gb/s Optical 10 Gb/s Optical |
|
Purpose |
Replication Engine |
Primary LUN |
Secondary LUN |
|---|---|---|---|
| User Interface | Inbound HTTP |   |   |
| Default: TCP Port 80 | N/A | N/A | N/A |
| Configuration | Inbound HTTP |   |   |
| Configuration Management: Port 3306 | N/A | N/A | N/A |
| Default: TCP Port 80 | N/A | N/A | N/A |
| Or TCP (21 + con- figured passive port range) | N/A | N/A | N/A |
| Or TCP (20 + 21) | Outbound FTP or (>1024) | Outbound FTP or (>1024) | N/A |
| Data resync | Inbound TCP Port 873 | N/A | N/A |
| FX data (Push ) | N/A | N/A | N/A |
| FX data (Pull) | N/A | N/A | N/A |
Purpose |
Firewall configuration |
|---|---|
| Linux | VNC server with VNC viewer (Port: 5500) Secure shell (SSH) (Port: 22) |
| Windows | Remote desktop connection or terminal client (3389) PC Anywhere (TCP 5631, UDP 5632) |