13 Set Up User Defined Codes Security
This chapter contains the topic:
13.1 Setting Up User Defined Codes Security
From Master Directory (G), choose Hidden Selection 27
From Advanced & Technical Operations (G9), choose Security & System Admin
From Security & System Administration (G94), choose Security Officer
From Security Officer (G9401), choose User Defined Codes
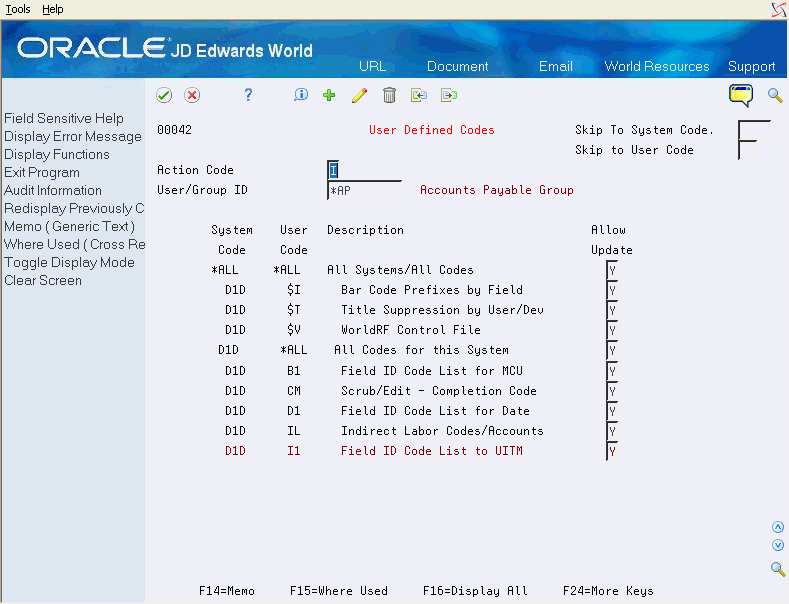
User Defined Code Security allows you to secure users, groups, or *PUBLIC from adding, changing, or deleting User Defined Code files. You may secure all User Defined Code files, all User Defined Code files within a system code, or individual User Defined Code files. When you define User Defined Security by system code, you can allow or deny access to all User Defined Codes files in a system code, without affecting authorization in other system codes.
|
Important!: The default setting for the User Defined Codes Security program is No Access if you have not set up records with the Allow Update field set to 'Y'. To allow users to update user-defined code files, you must set up records for individual users, groups, or *PUBLIC with the appropriate authorization to allow update access to User Defined Code files.Users can always inquire on UDC files and the values in the tables. |
To set up User Defined Codes security
-
On User Defined Codes, enter a user ID or group ID in the User ID field.
-
In the Allow Update field, enter 'Y' to allow update access, or 'N' to restrict update access.
| Field | Explanation |
|---|---|
| User ID | The User/Group field is used to enter user defined code security records for a particular user, group, or *PUBLIC. |
| Allow Update | Enter 'Y' to allow updating or 'N' to restrict updating. |
In the top half of the screen, you enter a user ID, group ID, or *PUBLIC in the User ID field. The subfile displays all User Defined Code security that is set up for the profile that you entered. When you enter a value in the User/Group ID field, that profile must exist in the User Information file (F0092).
The following function keys are available on the screen. Place your cursor on a subfile record to use these options:
-
F14 - Memo: Use this option to enter free-form text with any notes, comments or explanations about the security record. If a memo exists for a record, the subfile values in the System Code and User Code columns are highlighted and See Memo displays above the System Code column.
-
F8 - Audit Information: Use this option to retrieve audit information for a security record.
-
F9 - Use this option to display an inquiry again after an update.
13.1.1 General Guidelines
To set up security for a profile for the first time, inquire on the profile name. The subfile is then loaded with all User Defined Code files. Set the appropriate actions for the desired codes, change the Action Code field to 'C' and press enter. If the user profile does not exist in the User Information file (F0092), the User Defined Code files are not displayed. You cannot set up security information for a profile that does not exist.
To add new lines to an existing user record, inquire on the record. Press F16 to display all User Defined Code files, make your security selections, then change the action code to 'C', and press Enter.
To copy one user's setup to another, inquire on the record, change action code to an 'A', type the new user profile name and press Enter. Ensure that all the users' security records are loaded into the subfile before copying. Only records loaded in the subfile are copied to the new profile.
Use the 'D' action code with caution. If you enter 'D' in the Action Code field after you have inquired on a profile, all records in the subfile are deleted. To delete just one record in the subfile, place a 'C' in the Action Code field, clear the Allow Update field in the line to be deleted and press Enter.
13.1.2 User Defined Codes Security - Helpful Hints
When working with User Defined Code Security, the following considerations apply:
If you do not use roles or groups, the system checks user- defined code security in the following order:
-
User Profile ID and User Defined Code Table
-
User Profile ID and System Code, User Code=*ALL
-
User Profile ID and System Code=*ALL
-
*PUBLIC and User Defined Code Table
-
*PUBLIC and System Code, User Code=*ALL
-
*PUBLIC and System Code=*ALL
If the user logs on without selecting a role and belongs to a group (specified on the JDE User Profile record in the F0092 file), the system checks the security file in the following order:
-
User Profile ID and User Defined Code Table
-
User Profile ID and System Code, User Code=*ALL
-
User Profile ID and System Code=*ALL
-
Group Profile ID (if any) and User Defined Code Table
-
Group Profile ID (if any) and System Code, User Code=*ALL
-
Group Profile ID (if any) and System Code=*ALL
-
*PUBLIC and User Defined Code Table
-
*PUBLIC and System Code, User Code=*ALL
-
*PUBLIC and System Code=*ALL
In either of the scenarios described, the application stops checking when it encounters an appropriate record and uses the authority on the record it has found.
If you do not use role-based security, the system uses the group profile from the JD Edwards user profile, if a user profile exists.
If you use role-based security, a user who signed on using a role may have access to the authority for multiple groups. In this case, the system checks the profiles of all active groups for the role. If any group has authority, the role is granted authority. When a user is signed on using a role, the system does not check the user profile's group.