B Programming Standards
This appendix contains these topics:
B.1 Error Handling
JD Edwards World includes an efficient means of handling errors using arrays. The following illustrate the error handling arrays within the Single Record Maintenance Program.
-
The EMK array contains the four byte data dictionary name of every error that can occur in this program.
-
The @MK array maintains an indicator for each error in EMK. If one of the errors occurs, the system activates the indicator.
-
The @ER array loads the error messages when you choose Display Error Message (F7) to view the errors.
The code to launch the error message handling program follows.
Figure B-1 Error Message Handling Program Code screen
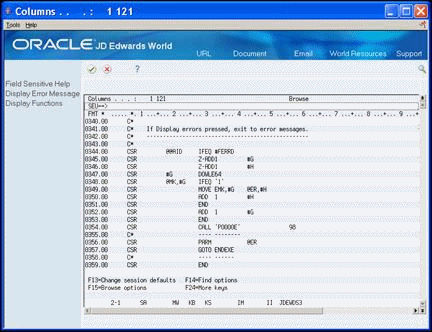
Description of "Figure B-1 Error Message Handling Program Code screen"
If an error indicator is set to one, the program moves the corresponding data item from the array of all possible errors (EMK) into the array of the errors (@ER).
The system loads the array which contains every possible error for this program only once (in S999).
B.2 Indicator Usage
There are 99 indicators available for use. JD Edwards World groups them by purpose and includes standards for the use of the indicators that are in the following table. JD Edwards World does not include standards for indicators that are not in the following table.
| INDICATOR | DESCRIPTION |
|---|---|
| 01 | Causes the Invalid Function Key Pressed message to display |
| 02 | Dictates the color palette to use |
| 04 | Controls subfile keywords SFLDROP and SFLFOLD for fold areas |
| 20 | Controls the clear screen action code |
| 21 | Controls the add action code |
| 22 | Controls the change action code |
| 23 | Controls the delete action code |
| 24 | Controls the inquire action code |
| 31 | The system uses this in conjunction with subfile processing to initiate the INVITE or SFLCLR keyword |
| 32 | The system uses this in conjunction with subfile processing initiating the keyword SFLNXTCHG |
| 37 | The system uses this in conjunction with subfile processing to highlight the last record in the display (used only with inquiry subfiles) |
| 38 | The system uses this in conjunction with subfile processing to control the display keyword SFLDSP |
| 42-79 | The system uses this for error processing to indicate which fields are in error |
| 40 | The system reserves this for errors in the Action Code field |
| 41 | The system reserves this for errors in the key fields |
| 80-89 | Indicates a general reusable one-time indicators |
| 93 | Indicates global error indicator that highlights line 24 |
| 98 | Indicates a chain or read failure |
| 99 | Indicates a record is in use |
| OF | Indicates overflow for report processing |
| LR | Indicates that the last record has been read and the program should end normally |
| RT | Indicates that a temporary or final halt in the program should take place and returns to the calling program leaving files open |
B.3 Naming Conventions
Use the following characters in the first place of the naming convention to distinguish different item names:
@ - Array names
$ - Field names the program creates for flags and work fields
# - Fields you define in common subroutines
B.4 Key List (KLIST)
Define key lists in the housekeeping subroutine.
Begin the key list name with the data file prefix. For example, the Address Book Master file prefix is AB, so the key list would be ABKY01.
The program generator creates key lists using the following naming conventions:
-
XXKY01 for physical files where XX = the file prefix. For example: ABKY01
-
When a physical file needs to have more than one key list in a program, you denote the successive files by the last character. For example, for three key lists for the physical F0101, the key lists are: ABKY01, ABKY02, and ABKY03.
-
XXKY0x for logical files where XX is equal to the file prefix and X is equal to the last letter of the logical file name. For example: ABKY0A for F0101LA, ABKY0B for F0101LB
-
When a logical file needs to have more than one key list in a program, you denote the successive files by the penultimate character. For example, the three key lists for the logical F0101LA are: ABKY0A, ABKY1A, and ABKY2A.
B.5 Work Fields
Define work fields only once within a program. JD Edwards World recommends that you use the LIKE DEFN command to define work fields when their attributes directly tie to those of database fields.
For example, if the work field needs to have the same attributes as a field that exists in a file:
MOVE ABANS $ANS,
You then define $ANS as follows:
*LIKE DEFN ABANS $ANS
The advantage of this method is that the work field and database field retain the same attributes even if the database field changes.
When using work fields as an indicator, you should assign the prefix $ and enter descriptive text for the remainder of the name. For example, a work field name such as $GLOBL is more descriptive than a field name such as $G.
For numeric indices, use the fields in the data structure I00DSINX.
B.6 Current Date and Time
When retrieving the current date and time, use the TIME operation code instead of UDATE. UDATE obtains the date format of the system on which you compiled the program. You cannot change the date format without recompiling the program. TIME uses the system's date format when it executes the operations code.
|
Note: The TIME operation requires significant system resources. If possible, use it only once for a program. Typically, this would occur in the Housekeeping Subroutine (S999). |
Always use program X0028 to edit dates and format them for output.