3 Security Features
Describes the role of security in the product architecture.
Oracle Enterprise Manager Ops Center provides security services for user authentication, custom user authorization, and protection for data in repositories and during network transmissions. Oracle Enterprise Manager Ops Center also provides network authentication between its infrastructure components using standard certificates.
Oracle Enterprise Manager Ops Center uses standard protocols and third-party solutions to secure data and operations, using TLS and X.509v3 certificates, and secure HTTP and PAM (Pluggable Authentication Modules) protocols to provide the following services:
-
Authentication
-
Authorization
-
Access Control
-
Data Protection
Configuring and Using Authentication
Describes authentication.
Authentication allows a system to verify the identity of users and other systems that request access to services or data. In a multi-tier application, the entity or caller can be a human user, a business application, a host, or one entity acting on behalf of another entity.
About Identity Management for Users
Describes how users are authenticated.
Users log in to the browser interface to use the product. The credentials must be valid for the Oracle Enterprise Manager Ops Center installation.
Add users to Oracle Enterprise Manager Ops Center from the local authentication subsystem of the Enterprise Controller's operating system or from a separate directory server.
About Configuring an LDAP Server
Procedure for changing the LDAP server..
You can add directory servers to Oracle Enterprise Manager Ops Center. Users and roles are added to the product from the directory server. The information in this section is also in the Oracle Enterprise Manager Ops Center Administration.
To grant roles to the users in a directory server, you create groups on the directory server that correspond to the roles in Enterprise Manager Ops Center. You grant a role to a user by adding the user to the corresponding group, and remove a role from a user by removing them from the group. You cannot edit the roles of a directory server user through the user interface.
Users that are added from a directory server begin with complete privileges for each of their roles.
You must configure the remote directory server before adding it to Oracle Enterprise Manager Ops Center.
To Configure the Directory Structure
Procedure for adding a new directory server for Oracle Enterprise Manager Ops Center to use.
About PAM Authentication
Procedure for setting the PAM authentication service.
Oracle Enterprise Manager Ops Center uses Pluggable Authentication Modules (PAM) to validate credentials for user accounts of users who log in to the browser interface. The default PAM service allows users to log in to the system in the standard way.
The pam-service-name parameter sets the PAM service for the oem-ec instance of the cacao daemon.
-
Oracle Solaris: The default value is
pam-service-name=other -
Linux: The default value is
pam-service-name=passwd
If you require control of the PAM configuration, create a PAM service with a different service name, which uses different PAM modules.
Verifying PAM Authentication
Procedure for displaying the PAM service.
To see the current value of the pam-service-name parameter, use the following cacaoadm command:
./cacaoadm get-param -i oem-ec pam-service-name
Changing the PAM Authentication
Procedure for changing the the way PAM authentication is used..
To change the authentication service from the operating system's default to a different service name, use the following procedure. If this is a High Availability environment, perform the procedure on both the primary node and on the standby node.
Note:
If you use the SafeNet SafeWord® Agent for PAM software (pam_safeword.so), you can use the SafeWord static password mode or single-use dynamic password mode, but you cannot use the dynamic challenge password mode. To use single-use dynamic passwords, you must modify the pam_safeword.cfg file to ensure that the User ID source is set to SYSTEM and not USER. The SYSTEM setting causes the authentication process to get the User ID from the /etc/passwd file.
Credentials for My Oracle Support
Describes access to My Oracle Support.
In Connected mode, the Oracle Enterprise Manager Ops Center software requires the user to provide one or more sets of My Oracle Support credentials. These credentials are used to authenticate and authorize downloading product updates, creating Service Requests, and retrieving warranty information, in addition to the initial authentication between the Enterprise Controller's system and My Oracle Support.
Credentials for IAAS and Cloud Deployments
Describes the protection of the location of the private key.
Some commands for the IAAS platform require a parameter for the location of the private key file. Because the private key authenticates a cloud user, this file is sensitive and must be managed as a security risk:
-
The file must be owned by the user running the IAAS command-line interface.
-
The file must have the highest restrictive permission: read-only by file owner.
About Authorization
Describes authorization.
Authorization allows a system to determine the privileges which users and other systems have for accessing resources on that system.
Roles grant users the ability to use the different functions of Oracle Enterprise Manager Ops Center. By giving a role to a user, an administrator can control what functions are available to that user and for which groups of assets.
An Enterprise Controller Admin can grant users different roles for the Enterprise Controller, the All Assets group, and any user-defined groups. A user who is assigned a role for a group receives the same role for all subgroups.
Caution:
A user with the Apply Deployment Plans, Exalogic Systems Admin, or SuperCluster Systems Admin role can apply an operational profile to a managed system using root access. Take care when assigning these roles because the role allows the user to use an operational profile to run scripts.
About Credentials for Assets
Describes the types of credentials used to manage assets.
Oracle Enterprise Manager Ops Center uses credentials to discover and manage assets and to establish trust between internal components. Examples of the types of credentials managed by Oracle Enterprise Manager Ops Center include:
-
SSH credentials for Operating System instances and hardware service processors.
-
IPMI credentials for hardware service processors
To see a list of all the types of credentials, select Credentials in the Administration section, then click Create Credentials in the Actions pane. The drop-down list for the Protocols field shows all of the supported protocols.
Oracle Enterprise Manager Ops Center requires remote network access and administrative privileges to discover and manage an asset. This can be done either by using a privileged account or by combining the credentials of a non-privileged user account with the credentials for the administrative account. In this case, Oracle Enterprise Manager Ops Center uses the non-privileged user account to connect to the system and then uses the administrative account to inquire about the characteristics of the system.
To discover an ILOM system, the account must have administrator privileges on the system, and both IPMI and ssh credentials must be provided.
Note:
IPMI communications from the Proxy Controller to the ILOM system are not encrypted. To protect the transmissions, isolate the ILOM system and the Proxy Controller it uses within your private administrative network.
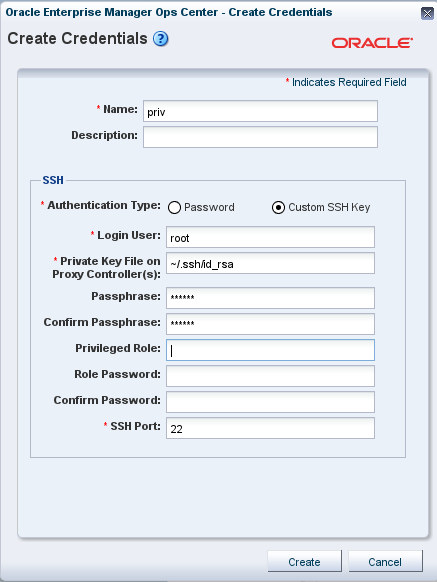
Using SSH Key-Based Authentication
Procedure for using an SSH key for access to assets.
If you prefer not to use password-based SSH credentials, create an SSH key to get access to remote assets, such as operating systems, ILOM service processors, and XSCF service processors. The assets must support the SSH protocol. Oracle Enterprise Manager Ops Center does not protect the SSH keys. If you choose to use this method, you must ensure the following:
-
You must create the SSH key on each Proxy Controller that needs to get access to the asset.
-
For an OS asset, you must add the SSH public key to the
~/.ssh/authorized_keysfile. For a hardware asset, you must use the asset's Web interface to upload the public SSH key.
To create the SSH key, use the Create Credentials action.
Creating Credentials for Access to the Serial Console or SSH Tunnel
Procedure for creating console or SSH credentials.
The information is this section is also in the Oracle Enterprise Manager Ops Center Configure Reference.
To enable a connection to a service processor or virtual machine, define the user account that Enterprise Manager Ops Center uses to open an SSH tunnel on the Enterprise Controller or to create a serial connection.
Note:
If you do not specify this account, Enterprise Manager Ops Center creates an account each time it accesses a serial console and deletes the account when the connection is no longer needed. This activity might not conform to your site's security policy.
The following types of assets use SSH to connect to a serial console. Create an account for each type and define the same password for each account.
-
Proxy Controllers
-
Global zones that use agents and require access to the consoles of non-global zones
-
Control domains that use agents and require access to the consoles of logical domains
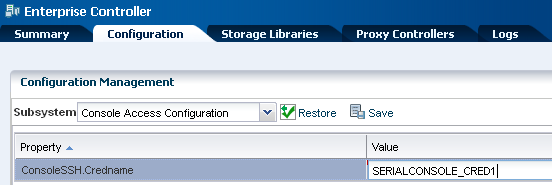
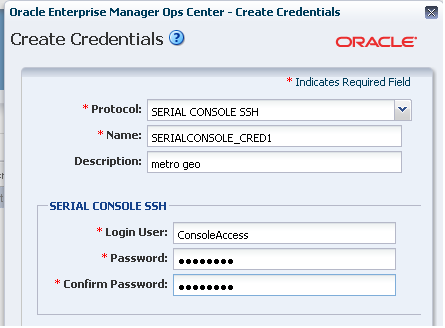
To create the account, define the ConsoleSSHCredname system property using the procedure in Defining the system property for console access and then define a user account for that property using either the procedure in Creating the account using Enterprise Manager Ops Center or the procedure in Creating the account using the useradd command.
Defining the system property for console access
Procedure configuring console access.
When the job is completed, define the account using the following procedure.
Creating the account using Enterprise Manager Ops Center
Procedure for creating a new account.
You must have the Security Admin role to perform this procedure.
After you define the user account, the account is created automatically in /etc/passwd the first time a job for console access is run. However, if your site's security policy requires that the operating system account must be created outside of Enterprise Manager Ops Center's control or if you prefer to create the account manually, use the procedure described in Creating the account using the useradd command.
About Managing Assets Using the agentadm Command
Describes a method of managing assets without storing credentials.
The information in this section is also in the Oracle Enterprise Manager Ops Center Configure Reference.
Although it is possible to discover assets without providing credentials, Oracle Enterprise Manager Ops Center is limited in its ability to manage or monitor these assets. If you prefer not to store credentials for assets in the product software, install the Agent Controller on each asset manually.
Use these procedures to install an Agent Controller and to register the target system.
Before You Install an Agent Controller
Lists prerequisites for installing an agent.
To use the agentadm command, you need the following information:
-
To configure your Agent Controller software using an administrative user account on the Enterprise Controller you need:
-
User name: the user account provides authentication that supports Agent Controller registration. Use the user name of this account as the argument for the
-uoption of the agentadm command. -
Password: use this password to populate the
/var/tmp/OC/mypasswdfile. Then use this file name as the argument for the-poption of the agentadm command.
-
-
The auto-reg-token registration token from the
/var/opt/sun/xvm/persistence/scn-proxy/connection.propertiesfile on the appropriate Proxy Controller – If you decide not to use user credentials to configure your Agent Controller software, use this token to populate the/var/tmp/OC/mytokenfile. Then use this file name as the argument for theagentadm -toption. -
IP address or host name of the Proxy Controller with which you will associate the Agent Controller – Use this IP address or host name as the argument for the
agentadm -xoption. Typically, you would associate the Agent Controller with the Proxy Controller that is connected to the same subnet as the target system. -
The IP address of the network interface that the Agent Controller will use for registration – Use this IP address as the argument for the
agentadm -aoption.
Some example agentadm commands in this procedure use the alternative administrative user name droot. In these examples, the droot user exists on the Enterprise Controller.
When you install an Agent Controller on a global zone, the installation installs, or upgrades to, Oracle Java Runtime Environment (JRE) 1.6.0_91. If a later version of JRE is installed, the installation does not downgrade.
Using User Credentials to Install and Configure an Agent Controller Manually
Procedure for installing an Agent Controller manually.
This procedure creates a file that holds the password of the administrative user for your Enterprise Manager Ops Center installation.
Changing Credentials of Managed Assets
Lists the procedures for managing the credentials for assets.
The information is this section is also in the Oracle Enterprise Manager Ops Center Configure Reference.
Preparing to Use sudo
Procedure to enable escalation of SSH credentials on discovered assets in Oracle Enterprise Manager Ops Center.
Example 3-1 Format of sudoers File for Ops Center
## sudoers file.
##
## This file MUST be edited with the 'visudo' command as root.
## Failure to use 'visudo' may result in syntax or file permission errors
## that prevent sudo from running.
##
## See the sudoers man page for the details on how to write a sudoers file.
##
##
## Host alias specification
##
## Groups of machines. These may include host names (optionally with wildcards),
## IP addresses, network numbers or netgroups.
# Host_Alias WEBSERVERS = www1, www2, www3
##
## User alias specification
##
## Groups of users. These may consist of user names, uids, Unix groups,
## or netgroups.
User_Alias OPSCENTER = <username>
##
## Cmnd alias specification
##
## Groups of commands. Often used to group related commands together.
Cmnd_Alias SOLARIS_DISCOVERY = /sbin/ifconfig -a, \
/usr/sbin/virtinfo -ap, \
/usr/sbin/dladm, \
/opt/SUNWldm/bin/ldm
Cmnd_Alias SOLARIS_PROVISIONING = /usr/bin/sc-console, \
/var/scn/install/uninstall, \
/usr/sbin/zlogin, \
/bin/cat */opt/SUNWxvm/xvm_zone_id, \
/var/tmp/OpsCenterAgent/install, \
/opt/SUNWxvmoc/bin/agentadm, \
/usr/lib/cacao/bin/cacaoadm, \
/usr/bin/unzip -q -o -d /var/tmp/ /var/tmp/OpsCenterAgent*
Cmnd_Alias LINUX_DISCOVERY = /sbin/ifconfig -a, \
/usr/sbin/virtinfo -ap
Cmnd_Alias LINUX_PROVISIONING = /usr/bin/sc-console, \
/var/scn/install/uninstall, \
/tmp/OpsCenterAgent/install, \
/opt/sun/xvmoc/bin/agentadm, \
/opt/sun/cacao2/bin/cacaoadm, \
/usr/bin/unzip -q -o -d /tmp/ /tmp/OpsCenterAgent*
##
## Defaults specification
##
## You may wish to keep some of the following environment variables
## when running commands via sudo.
##
## Locale settings
# Defaults env_keep += "LANG LANGUAGE LINGUAS LC_* _XKB_CHARSET"
##
## Run X applications through sudo; HOME is used to find the
## .Xauthority file. Note that other programs use HOME to find
## configuration files and this may lead to privilege escalation!
# Defaults env_keep += "HOME"
##
## X11 resource path settings
# Defaults env_keep += "XAPPLRESDIR XFILESEARCHPATH XUSERFILESEARCHPATH"
##
## Desktop path settings
# Defaults env_keep += "QTDIR KDEDIR"
##
## Allow sudo-run commands to inherit the callers' ConsoleKit session
# Defaults env_keep += "XDG_SESSION_COOKIE"
##
## Uncomment to enable special input methods. Care should be taken as
## this may allow users to subvert the command being run via sudo.
# Defaults env_keep += "XMODIFIERS GTK_IM_MODULE QT_IM_MODULE QT_IM_SWITCHER"
##
## Uncomment to enable logging of a command's output, except for
## sudoreplay and reboot. Use sudoreplay to play back logged sessions.
# Defaults log_output
# Defaults!/usr/bin/sudoreplay !log_output
# Defaults!/usr/local/bin/sudoreplay !log_output
# Defaults!/sbin/reboot !log_output
Defaults logfile=/var/log/sudo.log
##
## Runas alias specification
##
##
## User privilege specification
##
root ALL=(ALL) ALL
## The password of OPSCENTER must be mandatory.
OPSCENTER ALL=(root) SOLARIS_DISCOVERY,SOLARIS_PROVISIONING
## Uncomment to allow members of group wheel to execute any command
# %wheel ALL=(ALL) ALL
## Same thing without a password
# %wheel ALL=(ALL) NOPASSWD: ALL
## Uncomment to allow members of group sudo to execute any command
# %sudo ALL=(ALL) ALL
## Uncomment to allow any user to run sudo if they know the password
## of the user they are running the command as (root by default).
# Defaults targetpw # Ask for the password of the target user
# ALL ALL=(ALL) ALL # WARNING: only use this together with 'Defaults targetpw'
## Read drop-in files from /etc/sudoers.d
## (the '#' here does not indicate a comment)
#includedir /etc/sudoers.d
Upgrading Management Credentials From a Previous Version
Procedure for use new credentials to manage assets discovered by an earlier version of Oracle Enterprise Manager Ops Center.
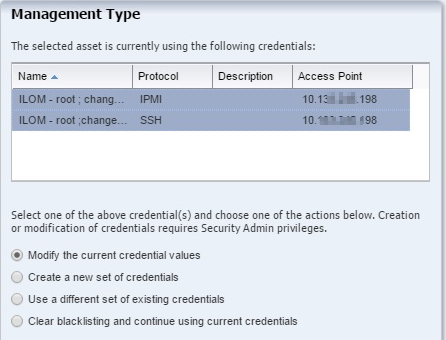
Assets that were discovered and managed in prior versions of Enterprise Manager Ops Center might not have management credentials associated with them. You can associate new or existing sets of credentials with these assets.
If a discovered asset is blacklisted, the same can be removed by updating the management credentials.
To upgrade management credentials, perform the following steps:
Updating Management Credentials
Procedure for updating credentials used to manage an asset.
You can change the set of management credentials used by an asset or group of assets.
To update management credentials, perform the following steps:
Creating Management Credentials
Procedure for creating credentials used to manage an asset.
You can create a new set of management credentials. These credentials can then be used to discover and manage new assets or to manage existing assets.
To create management credentials, perform the following steps:
- On the Navigation pane, under Administration, select Credentials.
- In the Actions pane, click Create Credentials.
- Click on the drop-down list to see the list of available protocols. Accept the default SSH protocol or select a different protocol. Depending on the type of protocol you select, the remaining fields change to collect the required information for the credentials. For specific examples, see Creating SSH Credentials or Creating SNMPV3 Credentials.
- Specify a name and description, such as the purpose of the credentials.
- Select or specify the required information for the type of credential, such as the username and password.
- Click Create to create the management credentials.
Creating SSH Credentials
Create a set of SSH credentials to discover and manage new assets or to manage existing assets.
The default protocol for managing assets is SSH. To create SSH credentials, perform the following steps:
Creating SNMPV3 Credentials
Procedure for creating credentials for accessing assets in Oracle Enterprise Manager Ops Center.
Create a set of management credentials to discover and manage new assets or to manage existing assets.
To create credentials that use the SNMPV3 protocol, perform the following steps:
Editing Management Credentials
Procedure for changing the credentials that manage and asset.
You can edit an existing set of management credentials to reflect changes to the managed assets.
To edit management credentials, perform the following steps:
- On the Navigation pane, under Administration, select Credentials.
- In the center pane, select a set of credentials and click the Edit Credentials icon.
- Edit the description and the information required by the protocol, then click Update to save the changes.
Copying Management Credentials
Procedure for duplicating credentials used to manage an asset.
You can copy an existing set of management credentials to create a new set.
To copy management credentials, perform the following steps:
- On the Navigation pane, under Administration, select Credentials.
- In the center pane, select a set of credentials and click the Copy Credentials icon.
- Edit the name, description, and the information required by the protocol, then click Copy to save the new set of credentials.
Deleting Management Credentials
Procedure for removing credentials used to manage an asset.
You can delete an existing set of management credentials. Discovery profiles that use the credentials might no longer function, and Agentless assets that are managed using the credentials must be given a new set.
To delete management credentials, perform the following steps:
- On the Navigation pane, under Administration, select Credentials.
- In the center pane, select a set of credentials and click the Delete Credentials icon.
- Click OK to delete the credentials.
Creating a Credential Plan
Procedure for creating a deployment plan for credentials.
As an alternative to using the Create Credential and Edit Credential actions, create and apply a plan that updates credentials.
- Expand Plan Management in the Navigation pane.
- Scroll down to the Credentials section and click it.
- Click Create Credentials in the Action pane.
- Click the drop-down list of protocols to select the type of protocol. Enter a name and description of the purpose of these credentials, for example, the type of asset they support.
- Enter the credentials.
- Click the Create button.
About Certificates
Describes self-signed certificates.
By default, Oracle Enterprise Manager Ops Center uses self-signed certificates for authentication between the web container and the browser client. Oracle Enterprise Manager Ops Center does not provide certificates signed by a Certificate Authority such as Verisign because an Authority requires the name of the domain where the certificate will be used. The Oracle Enterprise Manager Ops Center software cannot be delivered with a generated signed certificate because the domain where the Web server of the Enterprise Controller runs is unknown until the customer installs the software. However, after installation, use the procedure in Substituting Certificates for the Glassfish Web Container to replace the self-signed certificate with a certificate from a Certificate Authority.
Configuring and Using Access Control
Lists the procedures for configuring an asset so that it can be managed.
Access control allows a system to grant access to resources only in ways that are consistent with security policies defined for those resources:
Verifying Security of Session Cookies
Procedure for displaying information about a certificate.
Oracle Enterprise Manager Ops Center uses cookies to store session data for individual users. The cookies are encrypted using JSESSIONID and use the http-only flag to deny access to scripting languages.
The HTTP protocol includes the TRACE method to echo input. Because it is possible to use TRACE requests to view session cookies, Oracle Enterprise Manager Ops Center redirects HTTP transactions to HTTPS where the TRACE method is disabled.
To confirm that TRACE is disabled, use the following command on the Enterprise Controller's system or a Proxy Controller's system:
# curl -v --insecure -X TRACE https://<hostname>:9443
(output omitted)
HTTP/1.1 405 TRACE method is not allowed
Setting the Expiration Time for Sessions
Procedure for setting the activity timer for a session.
The browser controls a session's inactivity timer with a default time of 30 minutes. Consider changing the expiration time to a shorter duration, using the following procedure:
Configuring and Using Data Protection
Lists the procedures for backing up information about the assets.
Using an NFS Server
Procedure for setting up an NFS server for Oracle Enterprise Manager Ops Center.
NFS protocol requires agreement on the Domain Name System (DNS) that the NFS server and NFS clients use. The server and a client must agree on the identity of the authorized users accessing the share.
The Oracle Enterprise Manager Ops Center software prepares an NFS client to mount the share. Use the following procedure to prepare the NFS server on an Oracle Solaris 10. The same procedure is also supported in Oracle Solaris 11 system, or you can use a new procedure, described in Oracle Solaris Administration: ZFS File Systems.
About Backing Up and Restoring the Enterprise Controller
Oracle Enterprise Manager Ops Center has several tools that can be used for disaster recovery. These tools let you preserve Oracle Enterprise Manager Ops Center data and functionality if the Enterprise Controller or Proxy Controller systems fail.
The information is this section is also in the Oracle Enterprise Manager Ops Center Administration.
The ecadm backup and ecadm restore commands back up and restore the Enterprise Controller. They also back up and restore the co-located Proxy Controller unless otherwise specified. The proxyadm backup and proxyadm restore commands back up and restore remote Proxy Controllers.
The ecadm backup command creates a tar file that contains all of the Oracle Enterprise Manager Ops Center information stored by the Enterprise Controller, including asset data, administration data, job history, and the database password, but not including software and storage library contents. The proxyadm backup command creates a tar file that contains all of the Oracle Enterprise Manager Ops Center information stored by the Proxy Controller, including asset data. You can specify the name and location of the backup file and the log file for each command.
Run the ecadm backup and proxyadm backup commands regularly and save the backup files on a separate system.
If the Enterprise Controller system fails, you can use the ecadm restore command and the backup file to restore the Enterprise Controller to its previous state on the original system or on a new system. The ecadm restore command accepts the name of the backup file as input, and restores the Enterprise Controller to the state it had at the time of the backup.
If you are restoring the Enterprise Controller on a new system, you must verify that the new system is compatible.
-
The new system must have the same architecture and operating system as the old system. It is recommended that the operating system versions be identical, including updates and SRUs.
-
The host name of the new system should be the same as the old system. You can change the host name of the new system, provided the old host name is added as an alias host name in the new system.
-
The IP address of the new system can be different. If the new system has a different IP address, the restore process includes a step to configure any remote Proxy Controllers to use the new Enterprise Controller IP address. The MAC address of the new system can be different.
-
The new system's Enterprise Controller software version must also match those of the backed up system.
For a regular back up and restore procedure, the IP address and the host name of the new system should match that of the old system. For a disaster recovery procedure, the IP address and the host name of the new system can be different than that of the old system.
If a remote Proxy Controller system fails, you can use the proxyadm restore command and the backup file to restore the Proxy Controller. The proxyadm restore command accepts the name of the backup file as input, and restores the Proxy Controller to the state it had at the time of the backup.
Some of the procedures described in this section use the ecadm and proxyadm commands. See the Oracle Enterprise Manager Ops Center Administration for more information about these commands.
-
On Oracle Solaris systems, these commands are in the
/opt/SUNWxvmoc/bin/directory. -
On Linux systems, these commands are in the
/opt/sun/xvmoc/bin/directory.
The following features and topics are covered in this chapter:
Backing Up an Enterprise Controller
You can create a backup for the Enterprise Controller using the ecadm command with the backup subcommand.
You can create a backup for the Enterprise Controller using the ecadm command with the backup subcommand.
Note:
The ecadm backup command does not back up the /var/opt/sun/xvm/images/os directory because the size of some of the OS image files in this directory can be prohibitively large.
In addition to running the ecadm backup command, back up the /var/opt/sun/xvm/images/os directory and archive the files to another server, file-share facility, or a location outside of the /var/opt/sun directory.
By default, the server data is saved in a backup file in the /var/tmp directory with a file name that includes a date and time stamp. You can define the file name and location during the backup, as shown in the example below.
If you are using an embedded database, the backup file includes the product schema from the embedded database. If you are using a customer-managed database, you can back up the database schema using the --remotedb option, or you can use the existing backup and recover processes implemented by your database administrator.
Restoring an Enterprise Controller
You can use a backup file to restore the state of the Enterprise Controller to the state it had at the time of the backup.
This procedure restores the data from the backup file, which is the archive created by the backup operation. It also defines the procedure to change the IP address of an Enterprise Controller.
If you are using an embedded database, the restore process restores the product schema from the embedded database. If you are using a customer-managed database, you can use the --remotedb option to restore the product schema on the customer-managed database, or do not use this option to restore the Enterprise Controller without restoring the database.
Note:
Before you restore on a system, you must uninstall any previously existing Enterprise Controllers, Proxy Controllers, and Agent Controllers from the system.
Note:
After restoring the Enterprise Controller, the asset details might take several minutes to display completely in the user interface.
Note:
During the database schema restore, an import log is created. The name of the import log appears in the Enterprise Controller restore log file with the OC_import<timestamp>.log format. You can check the progress of the database import status using this import log.
Example: Restoring an Enterprise Controller With an Embedded Database
Sample command for restoring an Enterprise Controller.
In this example, the ecadm restore command includes options to set the restore in verbose mode (-v), and to create a restore log (-l) for debugging purposes. The input (-i) option specifies the backup file location.
# /opt/SUNWxvmoc/bin/ecadm restore -v -i /var/tmp/OC/server1/EC-17December.tar -l logfile-restore-15January.log
Example: Restoring an Enterprise Controller With a Customer-Managed Database
Sample command for restoring an Enterprise Controller.
In this example, the ecadm restore command includes the (-r) option to restore the database schema on a customer-managed database. The input (-i) option specifies the backup file location.
# /opt/SUNWxvmoc/bin/ecadm restore -i /var/tmp/OC/server1/EC-17December.tar -r
Example: Restoring an Enterprise Controller With a Customer-Managed Database Without Restoring the Database Schema
Sample command for restoring an Enterprise Controller.
In this example, the ecadm restore command includes options to set the restore in verbose mode (-v), and to create a restore log (-l) for debugging purposes. The input (-i) option specifies the backup file location. The (-r) option is not included.
# /opt/SUNWxvmoc/bin/ecadm restore -v -i /var/tmp/OC/server1/EC-17December.tar -l logfile-restore-15January.log