Security in a Virtualized Environment
To effectively secure your Oracle VM Server for SPARC virtualized environment, secure the operating system and each service that runs in each domain. To reduce the effects of a successful breach, separate services by deploying them to different domains.
The Oracle VM Server for SPARC environment uses a hypervisor to virtualize CPU, memory, and I/O resources for logical domains. Each domain is a discrete virtualized server that you must secure against potential attacks.
A virtualized environment enables you to consolidate several servers into one server by means of hardware resource sharing. In Oracle VM Server for SPARC, CPU and memory resources are allocated exclusively to each domain, which prevents abuse through excessive CPU usage or memory allocation. Disk and network resources are typically provided by service domains to many guest domains.
When evaluating security, always assume that your environment has a flaw that an attacker can exploit. For example, an attacker might exploit a weakness in the hypervisor to hijack the entire system, including its guest domains. So, always deploy systems to minimize the risk of damage in the case of a breach.
Execution Environment
Hypervisor – Platform-specific firmware that virtualizes hardware and relies heavily on the hardware support that is built into the CPU.
Control domain – A specialized domain that configures the hypervisor and runs the Logical Domains Manager, which manages the logical domains.
I/O domain or root domain – A domain that owns some or all of the platform's available I/O devices and shares them with other domains.
Service domain – A domain that offers services to other domains. A service domain might provide console access to other domains or provide virtual disks. A service domain that provides virtual disk access to other domains is also an I/O domain.
The execution environment includes the following components:
For more information about these components, see Figure 1 and the more detailed component descriptions.
You can improve serviceability for redundant I/O configurations by configuring a second I/O domain. You can also use a second I/O domain to isolate the hardware from security breaches. For information about configuration options, see Oracle VM Server for SPARC 3.3 Administration Guide .
Securing the Execution Environment
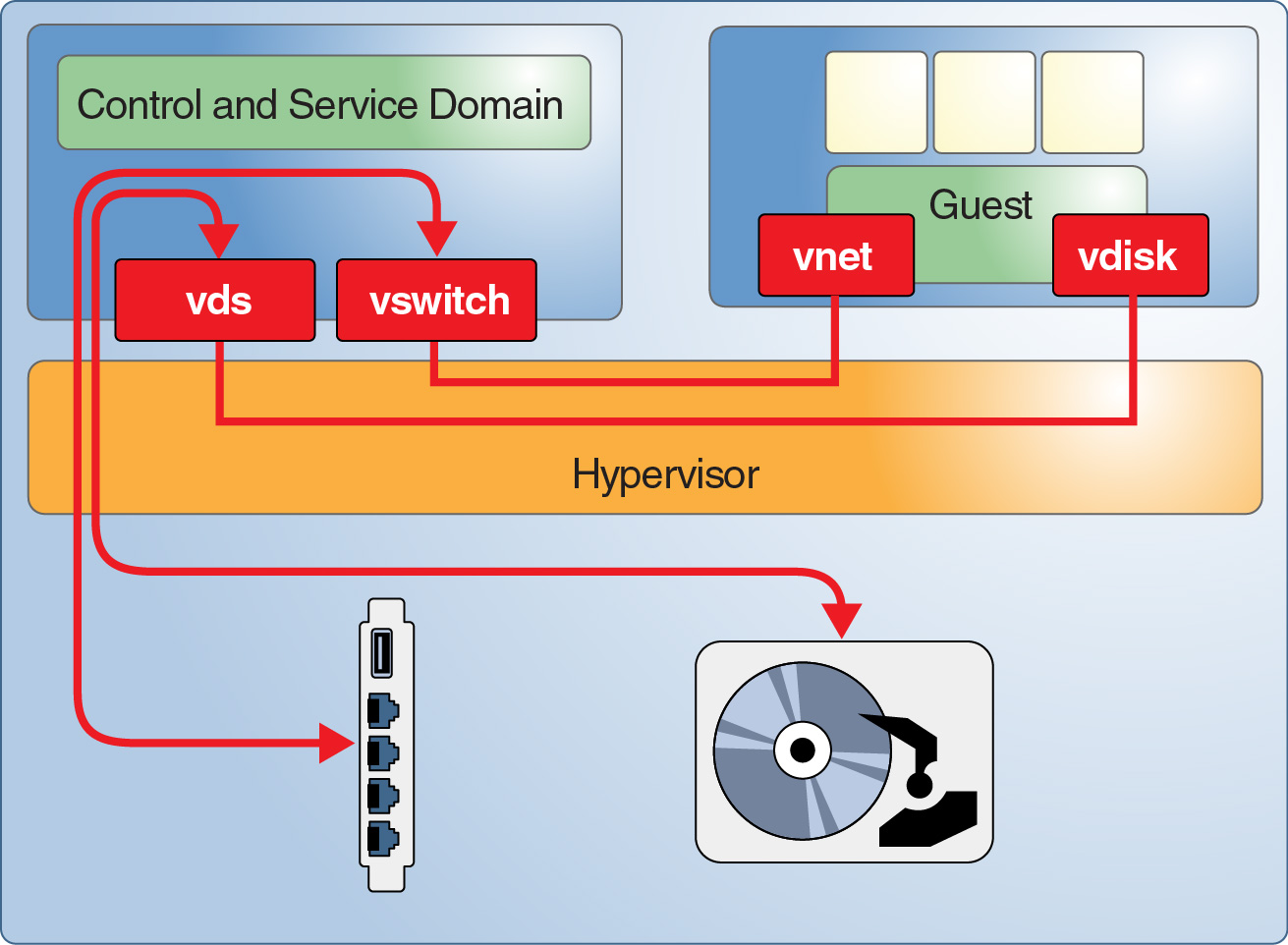
Oracle VM Server for SPARC has several attack targets in the execution environment. Figure 2 shows a simple Oracle VM Server for SPARC configuration where the control domain provides network and disk services to a guest domain. These services are implemented by means of daemons and kernel modules that run in the control domain. The Logical Domains Manager assigns Logical Domain Channels (LDCs) for each service and a client to facilitate a point-to-point communication between them. An attacker might exploit an error in any of the components to break the isolation of the guest domains. For example, an attacker might execute arbitrary code in the service domain or might disrupt normal operations on the platform.
Figure 2 Sample of Oracle VM Server for SPARC Environment