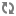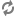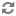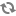In release 11.2 of Platform Services, the cryptographic protocols TLSv1.1 and TLSv1.2 are enabled by default. These protocols provide protection against serious security threats that have emerged recently. The protocols SSL 3.0 and TLS 1.0 do not provide similar protection and are disabled by default. Note that if you enable SSL 3.0 and TLS 1.0 -- for compatibility or any other reason -- you thereby make your application vulnerable to the serious threats against which TLSv1.1 and TLSv1.2 provide protection.
In
ENDECA_CONF/server.xml, make sure that any non-SSL
connector is commented and uncomment the following SSL connector:
<<Connector port="8443" maxHttpHeaderSize="8192" SSLEnabled="true"
maxThreads="150" minSpareThreads="25" maxSpareThreads="75"
enableLookups="false" disableUploadTimeout="true"
acceptCount="100" scheme="https" secure="true"
clientAuth="true" sslEnabledProtocols="TLSv1.1,TLSv1.2"
keystoreFile="C:/Endeca/ToolsAndFrameworks/11.1.0/deployment_template~
/ssl_certs_utility/bin/ssl/hostname.ks" keystorePass="eacpass"
truststoreFile="C:/Endeca/ToolsAndFrameworks/11.1.0/deployment_template~
/ssl_certs_utility/bin/ssl/TS-hostname.ks" truststorePass="eacpass"
URIEncoding="UTF-8"/>