5 Migrating the Configuration from Oracle Audit Vault to Oracle Audit Vault and Database Firewall
You can migrate the configuration from Oracle Audit Vault Release 10.3 to Oracle Audit Vault Database Firewall (Oracle AVDF) Release 12.2.
- About Migrating Oracle Audit Vault to Oracle Audit Vault and Database Firewall
Process to migrate from Oracle Audit Vault to Oracle Audit Vault and Database Firewall (Oracle AVDF). - Step 1: Prepare Oracle Audit Vault Release 10.3 for Migration
In Step 1, before you can perform the migration, you must download the migration utility files and set the correct permissions for theAVSYSuser and the migration files. - Step 2: Generate the Oracle Audit Vault Release 10.3 Configuration Data
In Step 2, you run a procedure that generates two files,migration-script.zipandmigration.log. Themigration-script.zipfile contains the Audit Vault 10.3 configuration that you are exporting, and themigration.logfile contains a log of actions and possible errors that took place during this procedure. - Step 3: Prepare Oracle Audit Vault and Database Firewall Release 12.2 for the Migration
In Step 3, put specific settings in place to ensure that Oracle Audit Vault and Database Firewall (Oracle AVDF) is using the same settings as Oracle Audit Vault. - Step 4: Migrate the Oracle Audit Vault Configuration to Oracle Audit Vault and Database Firewall
In Step 4, unzip themigration-script.zipfile to the Oracle Audit Vault and Database Firewall (Oracle AVDF) server and then complete the migration. - Step 5: Perform Post-Migration Procedures
In Step 5, to complete the migration process, you should ensure that the agents, audit trails, alerts, and other components are running, as well as revoke the privileges that you had granted to the Release 10.3AVSYSuser before the migration process.
5.1 About Migrating Oracle Audit Vault to Oracle Audit Vault and Database Firewall
Process to migrate from Oracle Audit Vault to Oracle Audit Vault and Database Firewall (Oracle AVDF).
When you migrate Oracle Audit Vault Release 10.3 to Oracle Audit Vault and Database Firewall Release 12.2, you must perform tasks such as migrating the Audit Vault hosts and alert definitions, setting up the agent, and so on, for Oracle Audit Vault and Database Firewall.
To perform the migration, you use an Oracle-supplied Java migration tool, which is platform independent. You can run it on the Oracle Audit Vault Release 10.3 supported platforms, which are Microsoft Windows and UNIX, and you can run it on the Linux x64 platform for Oracle Audit Vault and Database Firewall Release 12.2.
Figure 5-1 illustrates the migration path from Oracle Audit Vault Release 10.3 to Oracle Audit Vault and Database Firewall 12.2.
Figure 5-1 Migration Path for Oracle Audit Vault to Oracle Audit Vault and Database Firewall
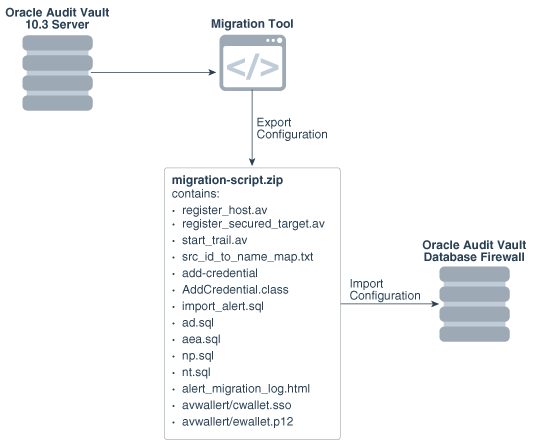
Description of "Figure 5-1 Migration Path for Oracle Audit Vault to Oracle Audit Vault and Database Firewall"
Configurations Migrated
The migration process migrates the following configurations from Oracle Audit Vault 10.3 to Oracle Audit Vault and Database Firewall 12.2:
-
Oracle Audit Vault 10.3 agents to Oracle Audit Vault and Database Firewall 12.2 hosts
-
Oracle Audit Vault 10.3 sources to Oracle Audit Vault and Database Firewall 12.2 secured targets
-
Oracle Audit Vault 10.3 collectors to Oracle Audit Vault and Database Firewall 12.2 audit trails
-
Secured target credentials
-
Wallet for secured target user credentials
-
Alert definitions
-
Alert email actions
-
Alert statuses
-
Notification profiles
-
Notification templates
Migration Overview
The general steps that you will perform are as follows:
-
Prepare Oracle Audit Vault 10.3.
-
Run the migration tool on Audit Vault 10.3 to export the configurations.
-
Check the migration logs for errors.
-
Prepare Oracle Audit Vault and Database Firewall 12.2 to receive the Oracle Audit Vault 10.3 configuration.
-
Run the migration scripts on Oracle Audit Vault and Database Firewall 12.2 to import the Oracle Audit vault 10.3 configuration.
-
Check Oracle Audit Vault and Database Firewall 12.2 status to complete the migration process.
5.2 Step 1: Prepare Oracle Audit Vault Release 10.3 for Migration
In Step 1, before you can perform the migration, you must download the migration utility files and set the correct permissions for the AVSYS user and the migration files.
5.3 Step 2: Generate the Oracle Audit Vault Release 10.3 Configuration Data
In Step 2, you run a procedure that generates two files, migration-script.zip and migration.log. The migration-script.zip file contains the Audit Vault 10.3 configuration that you are exporting, and the migration.log file contains a log of actions and possible errors that took place during this procedure.
5.4 Step 3: Prepare Oracle Audit Vault and Database Firewall Release 12.2 for the Migration
In Step 3, put specific settings in place to ensure that Oracle Audit Vault and Database Firewall (Oracle AVDF) is using the same settings as Oracle Audit Vault.
5.5 Step 4: Migrate the Oracle Audit Vault Configuration to Oracle Audit Vault and Database Firewall
In Step 4, unzip the migration-script.zip file to the Oracle Audit Vault and Database Firewall (Oracle AVDF) server and then complete the migration.