Oracle® Database
Security Assessment Tool User Guide
Release 1.0.2
E72220-03
October 2016
1.1 Overview
The Oracle Database Security Assessment Tool (DBSAT) analyzes database configurations and security policies to uncover security risks and improve the security posture of Oracle Databases within your organization.
You can use DBSAT to implement and enforce security best practices in your organization. DBSAT reports on the state of user accounts, role and privilege grants, and policies that control the use of various security features in the database.
You can use report findings to:
-
Fix immediate short-term risks
-
Implement a comprehensive security strategy
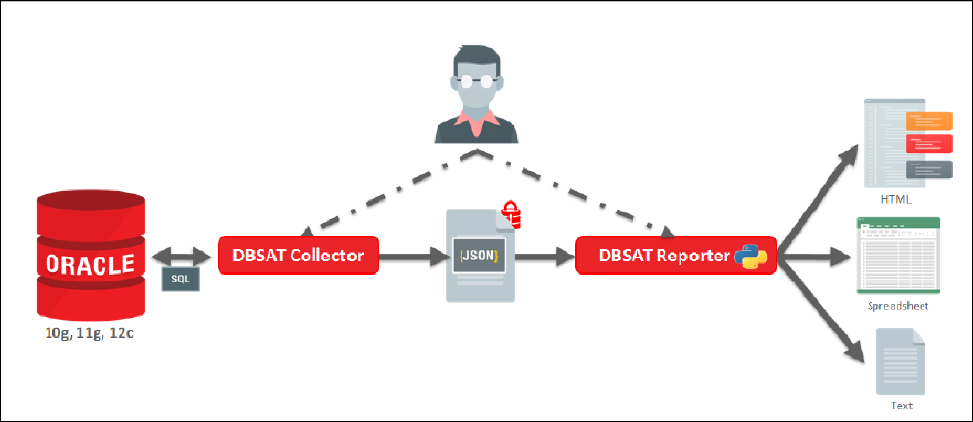
Components of DBSAT
DBSAT consists of two components, the DBSAT Collector and the DBSAT Reporter that correspond to the functions of data collection and data analysis respectively:
-
The DBSAT Collector executes SQL queries and runs operating system commands to collect data from the system to be assessed. It does this primarily by querying database dictionary views. The collected data is written to a file that is used by the DBSAT Reporter in the analysis phase.
-
The DBSAT Reporter analyzes the collected data and reports its findings and recommendations in multiple formats: PDF, Excel, and Text. The Reporter can run on any machine: PC, laptop, or server. You are not limited to running it on the same server as the Collector.
Benefits of Using DBSAT
You can use DBSAT to:
-
Quickly identify security configuration errors in your databases
-
Promote security best practices
-
Improve the security posture of your Oracle Databases
-
Reduce the attack surface and exposure to risk
1.2 Installation Requirements
You must meet certain system and target database platform requirements to install and use DBSAT successfully.
The following sections outline system requirements, supported target database platforms, database versions, and target database requirements.
System Requirements
The DBSAT Reporter is a platform-independent Python program and requires Python 2.6 or later to run.
Both the DBSAT Collector and Reporter use Zip and Unzip utilities already installed on the system to encrypt the generated files. The DBSAT tool expects to find these utilities in the locations shown below. If the utilities are somewhere else on your system, you must update these lines in the appropriate script.
Windows (dbsat.bat script):
SET ZIP_CMD=%ORACLE_HOME%\bin\zip.exe SET UNZIP_CMD=%ORACLE_HOME%\bin\unzip.exe
All other platforms (dbsat script):
ZIP=/usr/bin/zip
UNZIP=/usr/bin/unzip
DBZIP=${ORACLE_HOME}/bin/zip
Supported OS Platforms
The database configuration collection queries run on most supported Oracle Database platforms. However, currently the OS data collection will be skipped on Windows platforms. The list of skipped rules such as OS file permissions can be found at the end of the Text and HTML report.
DBSAT runs on:
-
Solaris x64 and Solaris SPARC
-
Linux x86-64
-
Windows x64
-
HP-UX IA (64-bit)
-
IBM AIX & zSeries Based Linux
Supported Database Versions
You can run the DBSAT tool on Oracle Database 10.2.0.5 and later releases.
Data is collected by running SQL queries and operating system commands. On Windows, the DBSAT Collector collects data only from SQL queries. Since the data from the operating system commands is missing, the DBSAT Reporter runs a subset of rules on this data.
Requirements to Run the DBSAT Collector
In order to collect complete data, the DBSAT Collector must be run on a server that contains the database, because it executes some operating system commands to collect process and file system information that cannot be obtained from the database. In addition, the DBSAT Collector must be run as an OS user with read permissions on files and directories under ORACLE_HOME in order to collect and process file system data using OS commands.
The DBSAT Collector collects most of its data by querying database views. It must connect to the database as a user with sufficient privileges to select from these views. You can grant the DBSAT user the individual privileges in the following list, or you can grant this user the DBA role plus the DV_SECANALYST role if needed.
Required privileges and roles:
-
CREATE SESSION -
SELECTonSYS.REGISTRY$HISTORY -
Role
SELECT_CATALOG_ROLE -
Role
DV_SECANALYST(if Database Vault is enabled) -
Role
AUDIT_VIEWER(12c only) -
Role
CAPTURE_ADMIN(12c only) -
SELECTonSYS.DBA_USERS_WITH_DEFPWD(11g and 12c) -
SELECTonAUDSYS.AUD$UNIFIED(12c only)
Note:
In order to successfully collect Database Vault information in a Database Vault environment, you must connect as a non-SYS user with the DV_SECANALYST role.1.3 Security Considerations
Security Guidelines
-
Ensure that the directories holding these files are secured with the appropriate permissions.
-
Delete the files securely after you implement the recommendations they contain.
-
Share them with others in their (by default) encrypted form.
-
Grant user permissions on a short-term basis and revoke these when no longer necessary.
System Impact While Running DBSAT
DBSAT is a light weight utility that will not impair system performance in a measurable way.
Caution
This tool is intended to assist in you in identifying potential vulnerabilities in your system, but you are solely responsible for your system and the effect and results of the execution of this tool (including, without limitation, any damage or data loss). Further, the output generated by this tool may include potentially sensitive system configuration data and information that could be used by a skilled attacker to penetrate your system. You are solely responsible for ensuring that the output of this tool, including any generated reports, is handled in accordance with your company's policies.
1.4 Installing and Running the Oracle Database Security Assessment Tool
To analyze a database using the Oracle Database Security Assessment Tool (DBSAT) you must first install it, then run the Collector and the Reporter in that order.
You can get DBSAT reports in three steps:
1.4.1 Task 1: Install the Database Security Assessment Tool
The Oracle Database Security Assessment Tool (DBSAT) installation is a simple process. Simply extract the file dbsat.zip on the Target Database server.
1.4.2 Task 2: Run the DBSAT Collector
The DBSAT Collector queries the database to collect data for further analysis.
dbsat collect script . You must ensure that the target database and listener are running before executing this step. The DBSAT Collector first connects to the database, then collects the data in a file.1.4.3 Task 3: Run the DBSAT Reporter
The DBSAT Reporter analyses the data collected by the Collector and makes recommendations to improve the security posture of the database.
dbsat report script.1.5 DBSAT Reports
DBSAT produces output in multiple formats for various audiences and purposes.
The HTML report provides detailed results of the assessment in a format that is easy to navigate. The Excel format provides a high-level summary of each finding without the detailed output included in the HTML report. It also allows you to add columns for your tracking and prioritization purposes. A report in text format makes it convenient to copy portions of the output for other usage.
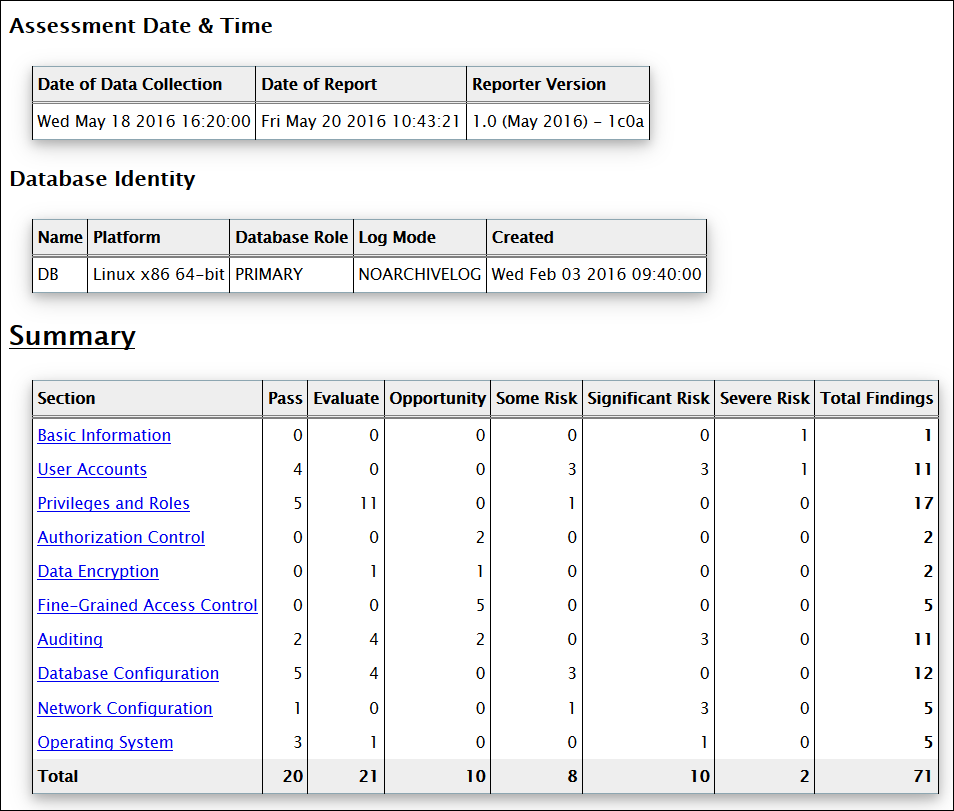
The following figure displays the first three tables of a DBSAT summary.
The resulting analysis is reported in units called Findings. An example follows:
Figure - DBSAT Finding — Users with Default Password
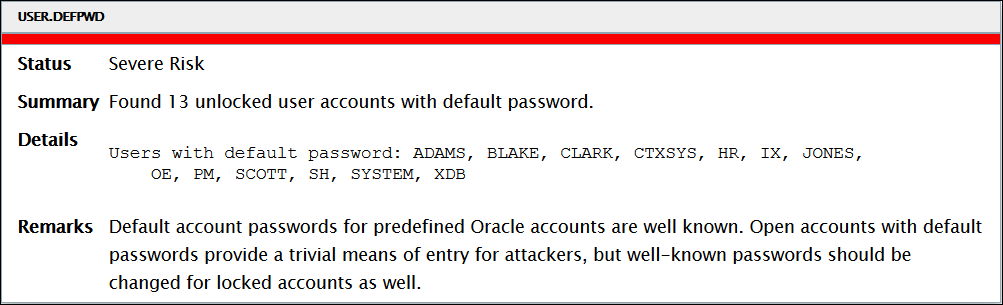
Description of "Figure - DBSAT Finding — Users with Default Password"
Each Finding consists of the following components:
-
Title and Unique ID for the Rule
The ID has two parts: the prefix identifies the report section, and the suffix identifies the specific rule.
-
Status
You can use the status values as guidelines to implementing DBSAT recommendations. They can be used to prioritize and schedule changes based on the level of risk, and what it might mean to your organization. Severe risk might require immediate remedial action, whereas other risks might be fixed during a scheduled downtime, or bundled together with other maintenance activities.-
Pass: no error found
-
Evaluate: needs manual analysis
-
Some Risk: low
-
Significant Risk: medium
-
Severe Risk: high
-
Opportunity: improve security posture by enabling additional security features and technology
-
-
Summary
This is a one-line summary of the finding. When the finding is informational, the summary typically reports only the number of data elements that were examined.
-
Details
This provides detailed information to explain the finding summary, typically results from the assessed database, followed by any recommendations for changes.
-
Remarks
This explains the standard used to assess the results found. It may also explain the recommended actions for remediation if a risk is reported.
1.6 Sample Script to Create a User with Minimum Privileges
You can create a user with required minimum privileges to run the Database Security Assessment Tool Collector with a script.
Purpose
Create a DBSAT user to run the DBSAT Collector script with required privileges.
Sample Script
create user dbsat_user identified by dbsat_user; // If Database Vault is enabled, connect as DV_ACCTMGR to run this command grant create session to dbsat_user; grant select_catalog_role to dbsat_user; grant select on sys.registry$history to dbsat_user; grant select on sys.dba_users_with_defpwd to dbsat_user; // 11g and 12c grant select on audsys.aud$unified to dbsat_user; // 12c only grant audit_viewer to dbsat_user; // 12c grant capture_admin to dbsat_user;// 12c covers sys.dba_priv_captures, sys.priv_capture$, sys.capture_run_log$ // if Database Vault is enabled, connect as DV_OWNER to run this command grant DV_SECANALYST to dbsat_user;
1.7 Known Issues
-
Some versions of Microsoft Excel may display text on the screen using a font that is too large to fit in the spreadsheet cells, even though it is sized correctly in printed output. If this happens, you can resize columns to be slightly wider in order to make the text visible.
1.8 Attribution for Third-Party Licenses
Third-party licenses used in the Database Security Assessment Tool Release 1.0.
About Third-Party Licenses
For third party technology that you receive from Oracle in binary form which is licensed under an open source license that gives you the right to receive the source code for that binary, you can obtain a copy of the applicable source code from this page. If the source code for the technology was not provided to you with the binary, you can also receive a copy of the source code on physical media by submitting a written request to:
Oracle America, Inc. Attn: Associate General Counsel Development and Engineering Legal 500 Oracle Parkway, 10th Floor Redwood Shores, CA 94065
Or, you may send an email to Oracle using this form. Your request should include:
The name of the component or binary file(s) for which you are requesting the source code The name and version number of the Oracle product The date you received the Oracle product Your name Your company name (if applicable) Your return mailing address and email A telephone number in the event we need to reach you
We may charge you a fee to cover the cost of physical media and processing. Your request must be sent (i) within three (3) years of the date you received the Oracle product that included the component or binary file(s) that are the subject of your request, or (ii) in the case of code licensed under the GPL v3, for as long as Oracle offers spare parts or customer support for that product model
XlsxWriter, Version: 0.7.7
Copyright (c) 2013, John McNamara <jmcnamara@cpan.org>
All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met: 1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer. 2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
The views and conclusions contained in the software and documentation are those of the authors and should not be interpreted as representing official policies, either expressed or implied, of the FreeBSD Project.
1.9 Documentation Accessibility
For information about Oracle's commitment to accessibility, visit the Oracle Accessibility Program website at http://www.oracle.com/pls/topic/lookup?ctx=acc&id=docacc.
Access to Oracle Support
Oracle customers that have purchased support have access to electronic support through My Oracle Support. For information, visit http://www.oracle.com/pls/topic/lookup?ctx=acc&id=info or visit http://www.oracle.com/pls/topic/lookup?ctx=acc&id=trs if you are hearing impaired.
Oracle® Database Security Assessment Tool User Guide, Release 1.0.2
E72220-03
Copyright © 2016, Oracle and/or its affiliates. All rights reserved.
This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited.
The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing.
If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notice is applicable:
U.S. GOVERNMENT END USERS: Oracle programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, delivered to U.S. Government end users are "commercial computer software" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, use, duplication, disclosure, modification, and adaptation of the programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, shall be subject to license terms and license restrictions applicable to the programs. No other rights are granted to the U.S. Government.
This software or hardware is developed for general use in a variety of information management applications. It is not developed or intended for use in any inherently dangerous applications, including applications that may create a risk of personal injury. If you use this software or hardware in dangerous applications, then you shall be responsible to take all appropriate fail-safe, backup, redundancy, and other measures to ensure its safe use. Oracle Corporation and its affiliates disclaim any liability for any damages caused by use of this software or hardware in dangerous applications.
Oracle and Java are registered trademarks of Oracle and/or its affiliates. Other names may be trademarks of their respective owners.
Intel and Intel Xeon are trademarks or registered trademarks of Intel Corporation. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International, Inc. AMD, Opteron, the AMD logo, and the AMD Opteron logo are trademarks or registered trademarks of Advanced Micro Devices. UNIX is a registered trademark of The Open Group.
This software or hardware and documentation may provide access to or information about content, products, and services from third parties. Oracle Corporation and its affiliates are not responsible for and expressly disclaim all warranties of any kind with respect to third-party content, products, and services unless otherwise set forth in an applicable agreement between you and Oracle. Oracle Corporation and its affiliates will not be responsible for any loss, costs, or damages incurred due to your access to or use of third-party content, products, or services, except as set forth in an applicable agreement between you and Oracle.