Tools for Verifying Applications
Oracle Developer Studio provides tools to help verify your application's stability. The following tools combine dynamic, static and code coverage analysis to detect application vulnerabilities, including memory leaks and memory access violations.
- discover
-
A command-line utility that helps detect memory access errors in your code.
- uncover
-
A command-line utility that shows you which areas of your application code are not covered by testing.
- Code Analyzer
-
A graphical tool that analyzes and displays static code error data collected by the C or C++ compiler, and data collected by discover and uncover. By integrating static error data with dynamic memory access error data and code coverage data, Code Analyzer lets you find errors in your application that you would not find when using other error detection tools by themselves.
- codean
-
A command-line utility that provides functionality similar to Code Analyzer.
discover Tool for Detecting Memory Errors
The Memory Error Discovery Tool (discover) is an advanced development tool for detecting memory access errors in your programs. Compiling a binary with –g enables discover to display source code and line number information while reporting errors and warnings.
The discover utility is simple to use. After compiling your binary with the –g option, run the discover command on the binary to instrument it. Then, run the instrumented binary to create a discover report. You can request the discover report in HTML format, text format, or both. The report shows memory errors, warnings, and memory leaks, and you can display the source code and stack trace for each error or warning.
The following example from the discover(1) man page shows how to prepare, instrument, and run an executable to generate a discover report for detecting memory access errors. The –w option on the discover command line indicates that the report should be written as text and the –o option indicates that the output should go to the screen.
% cc -g -O2 test.c -o test.prep
% discover -w - -o test.disc test.prep
% ./test.disc
ERROR (UMR): accessing uninitialized data from address 0x5000c (4 bytes) at:
foo() + 0xdc <ui.c:6>
3: int *t;
4: foo() {
5: t = malloc(5*sizeof(int));
6:=> printf("%d0, t[1]);
7: }
8:
9: main()
main() + 0x1c
_start() + 0x108
block at 0x50008 (20 bytes long) was allocated at:
malloc() + 0x260
foo() + 0x24 <ui.c:5>
2:
3: int *t;
4: foo() {
5:=> t = malloc(5*sizeof(int));
6: printf("%d0, t[1]);
7: }
8:
main() + 0x1c
_start() + 0x108
***************** Discover Memory Report *****************
1 block at 1 location left allocated on heap with a total size of 20 bytes
1 block with total size of 20 bytes
malloc() + 0x260
foo() + 0x24 <ui.c:5>
2:
3: int *t;
4: foo() {
5:=> t = malloc(5*sizeof(int));
6: printf("%d0, t[1]);
7: }
8:
main() + 0x1c
_start() + 0x108
For more information, see the discover(1) man page and Oracle Developer Studio 12.6: Discover and Uncover User’s Guide.
uncover Tool for Measuring Code Coverage
The uncover utility is a command-line tool for measuring code coverage. The tool shows you which areas of your application code are exercised when the application is run, and which are not exercised and not covered by testing. Uncover produces a report with statistics and metrics to help you determine which functions should be added to the test suite to ensure that more of the code is covered during testing.
uncover works with any binary that is built with an Oracle Developer Studio compiler, and works best when the binary is built without optimization. Compiling a binary with –g enables uncover to display source code and line-number information while reporting on code coverage.
After compiling the binary, you run the uncover command on the binary. uncover creates a new binary with added instrumentation code and also creates a directory named binary.uc that will contain the code coverage data for your program. Each time you run the instrumented binary, code coverage data is collected and stored in the binary.uc directory.
You can display the experiment data in Performance Analyzer, or generate the uncover report as HTML and display it in your web browser.
The following example shows how to prepare, instrument, and run an executable to generate an uncover report for examining code coverage. The optimized binary is test and is replaced by the instrumented binary also named test.
% cc -g -O2 test.c -o test % uncover test % test
The experiment directory is test.uc and contains the data that is generated when the instrumented test runs. The test.uc directory also contains a copy of the uninstrumented test binary.
To view the experiment in Performance Analyzer:
% uncover test.uc
To view the experiment in an HTML page in a browser:
% uncover -H test.html test.uc
For more information, see the uncover(1) man page and the Oracle Developer Studio 12.6: Discover and Uncover User’s Guide.
Code Analyzer Tool For Integrated Error Checking
-
Static code checking, which is performed when you compile your application with the Oracle Developer Studio C or C++ compiler and specify the –xprevise=yes option.
-
Dynamic memory access checking, which is performed when you instrument your binary with discover using the –a option, and then run the instrumented binary.
-
Code coverage checking, which is performed when you instrument your binary with uncover, run the instrumented binary, and then run Uncover with the –a option on the collected coverage data.
Oracle Developer Studio Code Analyzer is a graphical tool that enables you to perform an integrated analysis of your code. Code Analyzer uses three types of information that you gather using other tools:
You can use Code Analyzer on a binary that has been prepared with any one of these tools or any combination of these tools. However, the integrated view of the three types of data offers the most revealing look into your code and enables you to create a more secure and robust application.
The following example shows how to run Code Analyzer on a binary named a.out that has been prepared previously with discover and uncover.
% code-analyzer a.out
In the following figure, Code Analyzer is displaying the issues found in the a.out binary.
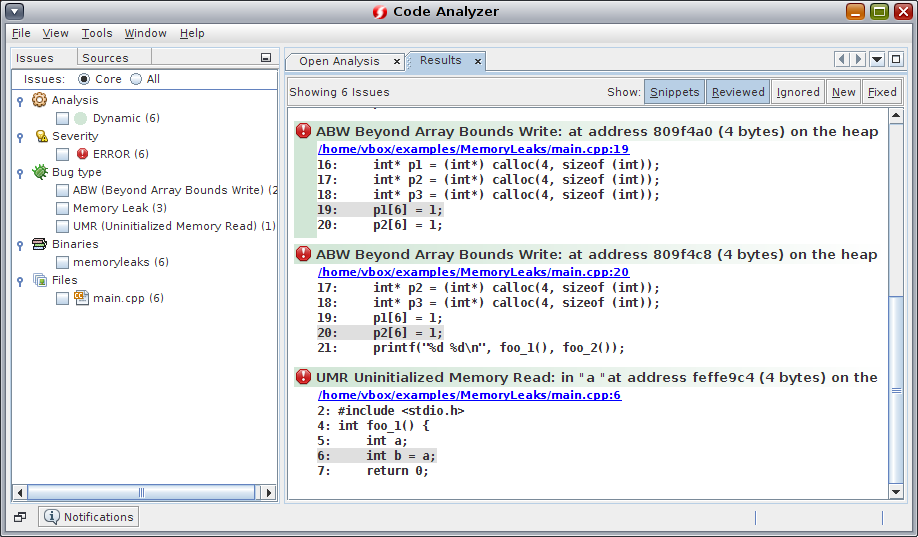
For more information, see the integrated Code Analyzer help, Oracle Developer Studio 12.6: Code Analyzer User’s Guide, and Oracle Developer Studio 12.6: Code Analyzer Tutorial.
codean Tool for Integrated Checking
You can also generate reports from the data collected through the compilers, discover, and uncover using the codean command-line utility. The codean tool provides functionality similar to Code Analyzer, but you can use it on systems where a graphical environment is not available, or if you prefer the command line. The codean tool can also be used in automated scripts and has some features that are not yet available in the Code Analyzer tool.
For more information, see the codean(1) man page, Oracle Developer Studio 12.6: Code Analyzer User’s Guide, and Oracle Developer Studio 12.6: Code Analyzer Tutorial.