Overview of Setting Up Data Sources
BI Publisher supports a variety of data sources. The data can come from a database, a HTTP XML feed, a Web Service, an Oracle BI Analysis, an OLAP cube, a LDAP server, or a previously generated XML file or Microsoft Excel file.
About Private Data Source Connections
Private connections for OLAP, JDBC, Web Service, and HTTP data sources are supported in BI Publisher and can be created by users with data model creation privileges.
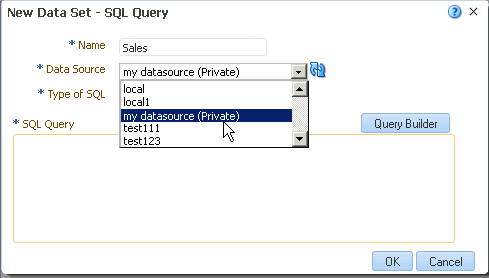
When a user creates a private data source connection, it displays only for that user in the data model editor data source menus. For example, a user creates a private data source connection called "my datasource." When the user creates a data set, the private data source connection displays in the Data Source selection menu as shown in the figure below.
Administrators have access to the private data source connections created by users. All private data source connections are displayed to Administrators when they view the list of OLAP, JDBC, Web Service, and HTTP data sources from the BI Publisher Administration page.
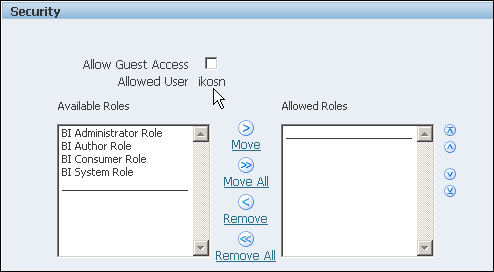
Private data source connections are distinguished by an Allowed User value on the Data Source Administration page as shown in the figure below. Administrators can extend access to other users to a private data source connection by assigning additional user roles to it.
For more information on assigning roles to data sources, see Granting Access to Data Sources Using the Security Region.
For more information about creating private data source connections, see Managing Private Data Sources in Data Modeling Guide for Oracle Business Intelligence Publisher.
Granting Access to Data Sources Using the Security Region
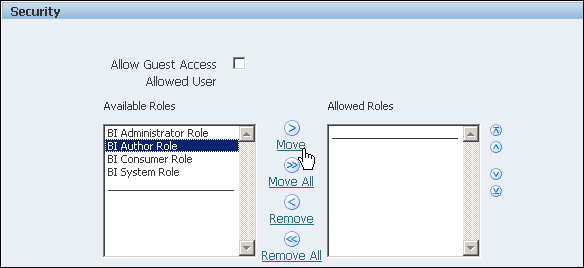
When you set up data sources, you can also define security for the data source by selecting which user roles can access the data source.
You must grant access to users for the following:
-
A report consumer must have access to the data source to view reports that retrieve data from the data source
-
A report designer must have access to the data source to create or edit a data model against the data source
By default, a role with administrator privileges can access all data sources.
The configuration page for the data source includes a Security region that lists all the available roles. You can grant roles access from this page, or you can also assign the data sources to roles from the roles and permissions page.
See Configuring Users, Roles, and Data Access for information.
If this data source must be used in guest reports, then you must also enable guest access here. For more information about guest access see Enabling a Guest User.
The figure below shows the Security region of the data source configuration page.
About Proxy Authentication
BI Publisher supports proxy authentication for connections to various data sources
Supported data sources include:
-
Oracle 10g database
-
Oracle 11g database
-
Oracle BI Server
For direct data source connections through JDBC and connections through a JNDI connection pool, BI Publisher enables you to select "Use Proxy Authentication". When you select Use Proxy Authentication, BI Publisher passes the user name of the individual user (as logged into BI Publisher) to the data source and thus preserves the client identity and privileges when the BI Publisher server connects to the data source.
Note:
Enabling this feature requires additional setup on the database. The database must have Virtual Private Database (VPD) enabled for row-level security.
For more information on Proxy Authentication in Oracle databases, see Oracle Database Security Guide.
For connections to the Oracle BI Server, Proxy Authentication is required. In this case, proxy authentication is handled by the Oracle BI Server, therefore the underlying database can be any database that is supported by the Oracle BI Server.
Choosing JDBC or JNDI Connection Type
In general, a JNDI connection pool is recommended because it provides the most efficient use of your resources.
For example, if a report contains chained parameters, then each time the report is executed, the parameters initiate to open a database session every time.
About Backup Databases
When you configure a JDBC connection to a database, you can also configure a backup database.
A backup database can be used in two ways:
-
As a true backup when the connection to the primary database is unavailable
-
As the reporting database for the primary. To improve performance you can configure your report data models to execute against the backup database only.
To use the backup database in either of these ways, you must also configure the report data model to use it.
See Setting Data Model Properties in Data Modeling Guide for Oracle Business Intelligence Publisher for information on configuring a report data model to use the backup data source.
About Pre Process Functions and Post Process Functions
You can define PL/SQL functions for BI Publisher to execute when a connection to a JDBC data source is created (preprocess function) or closed (postprocess function).
The function must return a boolean value. This feature is supported for Oracle databases only.
These two fields enable the administrator to set a user's context attributes before a connection is made to a database and then to dismiss the attributes after the connection is broken by the extraction engine.
The system variable :xdo_user_name can be used as a bind variable to pass the login username to the PL/SQL function calls. Setting the login user context in this way enables you to secure data at the data source level (rather than at the SQL query level).
For example, assume you have defined the following sample function:
FUNCTION set_per_process_username (username_in IN VARCHAR2)
RETURN BOOLEAN IS
BEGIN
SETUSERCONTEXT(username_in);
return TRUE;
END set_per_process_username
To call this function every time a connection is made to the database, enter the following in the Pre Process Function field: set_per_process_username(:xdo_user_name)
Another sample usage might be to insert a row to the LOGTAB table every time a user connects or disconnects:
CREATE OR REPLACE FUNCTION BIP_LOG (user_name_in IN VARCHAR2, smode IN VARCHAR2) RETURN BOOLEAN AS BEGIN INSERT INTO LOGTAB VALUES(user_name_in, sysdate,smode); RETURN true; END BIP_LOG;
In the Pre Process Function field enter: BIP_LOG(:xdo_user_name)
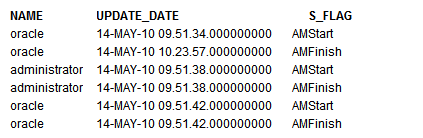
As a new connection is made to the database, it is logged in the LOGTAB table. The SMODE value specifies the activity as an entry or an exit. Calling this function as a Post Process Function as well returns results such as those shown in the table below.