Within the CMP system you can define the settings that control system behavior.
To define system settings:
- From the System Administration section of the navigation pane, select System Settings.The System Settings page opens in the work area, displaying the current system settings.
- Click Modify.The System Settings page opens.
- In the Configuration section, define the following:
- Idle Timeout (minutes; 0=never)—The interval of time, in minutes, that a user login session is kept alive.The default value is 30 minutes; a value of zero indicates the session remains active indefinitely.
- Account Inactivity Lockout (days; 0=never)—The maximum number of days since the last successful login after which a user is locked out.If the user fails to log in for the defined number of days, the user is locked out and cannot gain access to the system until an administrator resets the account. The default value is 21 days; a value of zero indicates no limit (the user is never locked out for inactivity).
- Maximum Concurrent Sessions Per User Account (0=unlimited)—The maximum number of times a defined user can be logged in simultaneously. A value of zero indicates no limit.If more than the configured number of concurrent users try to log in (for example, a second user if this value is set to 1), they are blocked at the login page with the a message indicating that the maximum number of concurrent sessions has been reached.
- Password Expiration Period (days; 0=never)—The number of days a password can be used before it expires. Enter a value from 7 to 365, or 0 to indicate that the password never expires.
- Password Expiration Warning Period (days; default=3)—The number of days before a password expires to begin displaying a window to users after login warning that their password is expiring.
- Admin User Password Expiration—By default, the password for the admin user never expires.If you select this option, the admin user is subject to the same password expiration policies as other users.
- Block users when password expires—By default, after a password expires, the user must immediately change it at the next login.If you select this option, if their password expires, users cannot log in at all. (If you select Admin User Password Expiration and the admin user’s password expires, the user can still log in but must immediately enter a new password.)
- EMS Shared Secret—Field provided to support third-party single sign-on architectures.
- Minimum Password Length—The minimum allowable length in characters for a password, from 6 to 64 characters.The default is six characters.
- Login Banner Title—The banner that displays on the login page. The default is "Welcome." You can enter up to 30 characters.
- Login Banner Text—The text that displays on the login page. You can enter up to 10,000 characters.
- Top Banner Text—The text that displays in the banner at the top of the GUI page. You can enter up to 50 characters. You can select the font, size, and color of the text.
- Allow policy checkpoint and restore (copies; 0=disallow)—The number of checkpoints allowed in the system. Valid value range is 0 to 10. If set to 0, the Policy Checkpoint/Restore option is turned off and is no longer visible under the Policy Management heading on the navigation panel. The default value is 0.
- Object's "name" attribute validation rule (Debug mode only)—Defines the valid characters in manageable object names in the CMP database; specified as a regular expression. By default, names can only contain the characters A–Z, a–z, 0–9, period (.), hyphen (-), and underline (_). Changing characters could allow users to create names that are not accepted by external systems.
- Idle Timeout (minutes; 0=never)—The interval of time, in minutes, that a user login session is kept alive.
- In the Invalid Login Threshold Settings section, define the following:
- Enable—Enables login threshold control.By default, this feature is enabled; deselect the check box to disable this feature.
- Invalid Login Threshold Value—Defines the maximum number of consecutive failed logins after which action is taken.Enter a value from 1 through 500; the default is 3 attempts.
- Action(s) upon Crossing Threshold—The system action to take if a user reaches the invalid login threshold:
- Lock user account—Prevents users from logging in if they reach the invalid login threshold.
- Send trace log message—If a user account reaches the threshold, an incident is written to the trace log, including the username and the IP address from which the login attempts was made. The default level is Warning; to change the event level, select a different level from the list.
- Enable—Enables login threshold control.
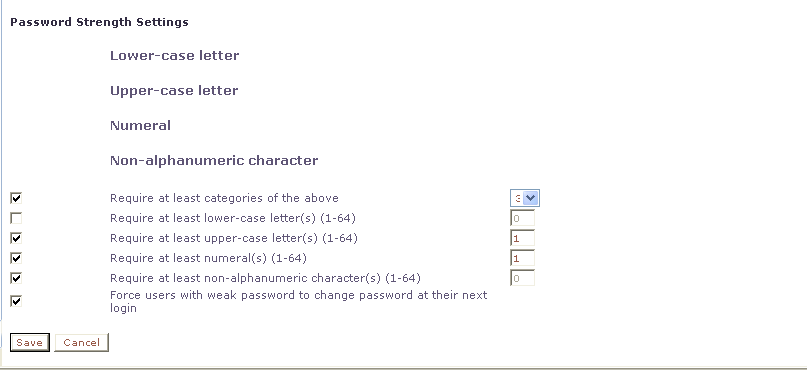
- The Password Strength Settings section lists four character categories: lowercase letters, uppercase letters, numerals, and non-alphabetic characters. You can specify a password strength policy that requires users to create passwords by drawing from these categories:
- Require at least categories below—By default, this setting is 0 (disabled). Select it to require users to include password characters from between one to four of the categories.
- Require at least lower-case letter(s) (1-64)—By default, this setting is 0 (disabled). Select it to require users to include from 1 to 64 lowercase letters in their passwords.
- Require at least upper-case letter(s) (1-64) —By default, this setting is 0 (disabled). Select it to require users to include from 1 to 64 uppercase letters in their passwords.
- Require at least numeral(s) (1-64)—By default, this setting is 0 (disabled). Select it to require users to include from 1 to 64 numerals in their passwords.
- Require at least non-alphanumeric character(s) (1-64)—By default, this setting is 0 (disabled). Select it to require users to include from 1 to 64 non-alphabetic characters in their passwords.
- Force users with weak password to change password at their next login—By default, this setting is disabled. Select it to require users to conform to a new password policy effective the next time they log in.
- Click Save.
- To refresh the CMP system, log out and log back in.
The system settings are configured.
Figure 1 shows an example of settings that establish a password strength policy requiring user passwords to contain at least one uppercase letter, four numerals, and one non-alphabetic character. (A password that would satisfy this policy is P@ssword1357.) Users whose passwords do not meet these requirements will be forced to change their passwords the next time they log in.
Sample Password Strength Policy