Installing Digital Certificates
Digital certificates are required to provide client and server authentication in Real-time Event Notification (REN) server using SSL. A digital certificate is an electronic means of establishing your credentials for web or business transactions that are issued by a certification authority (CA). The CA is a trusted third party who signs and issues the certificates for users after verifying their authentication using secure means.
The Installing Digital Certificates for REN SSL topic presents a sample way of installing digital certificates and configuring REN using SSL. PeopleSoft customers may have their own means of obtaining and installing digital certificates for REN server with SSL enabled.
This section outlines the basic steps to install digital certificates. Before installing digital certificates, you must create the application server domain.
Note: The application server domain must have write permissions. All certificates are stored under <PS_HOME>/appserv/<domain name>. The cacerts file has write permissions under <PS_HOME>/JRE/lib/security.
The following overview lists the steps that are required to install digital certificates. The subsequent sections describe each step in detail.
To install digital certificates and configure REN SSL:
Install the CA server certificate.
Install the REN server certificate.
Configure digital certificates.
Import certificates into the Java keystore for any REN Java Clients.
See Importing Certificates in Java Keystore for REN Java Clients.
Configure the REN server.
Configure REN clusters.
Install certificates for local node.
Generate the client certificate.
Install PSMCAPI certificates.
Configure an external keystore.
To install the CA server certificate:
Generate the RSA private key for the certificate authority.
Generate the Certificate Signing Request (CSR) for the certificate authority.
Generate the PEM file.
Note: If a CA certificate already exists in PEM format, the preceding three steps can be omitted.
Import the CA Certificate in PEM format using
The preceding steps are explained in detail in the section Configuring Digital Certificates.
See Configuring Digital Certificates, Implementing Client Authentication.
To install the REN server certificate:
Generate REN server CSR using
Get the CSR signed by a CA.
Note: The certificate must be in PEM format.
Import the certificate into
The preceding steps are explained in detail in the section Configuring Digital Certificates.
Before configuring digital certificates, you must generate the private keys, CSR, and PEM file.
To configure digital certificates:
Select
Click +.
Select ROOTCA from the Type drop-down list box.
Enter an alias name for the CA in Alias, and click Add Root.
The Add Root Certificate dialog box appears.
Open the ca.pem file.
The root CA certificate is generated.
Copy the contents of the ca.pem file, paste them into the Add Root Certificate dialog box, and click OK.
Click +.
Select Cert from the Type drop-down list box.
Enter an alias name in Alias, such as PSFTCA.
Click Add Root.
Select the CA certificate alias of step 4 from the Issuer Alias lookup button.
Click Request.
The Request New Certificate dialog box appears.
Complete the Common Name, Org Unit (organization unit), Organization, Locality, State/Province, Country, Algorithm, Key Size, Email Address, and Challenge Pswdfields.
Note: The common name must be the machine name of the REN server machine, for example, PTA112.peoplesoft.com, where PTA112 is the machine name and .peoplesoft.com is the domain name.
Click OK.
The Certificates Signing Request dialog box appears.
Copy and paste the text from the Certificates Signing Request dialog box, and save the text in a file named ren.csr in <PS_HOME>\appserv\<domain name>\.
Click OK.
The Import link appears.
Submit ren.csr to the CA that issued the selected root certificate.
The CA may send you the signed public key certificate by email or require you to download it from a specified web page.
Open the saved certificate file in a text editor, and then highlight and copy its entire contents.
Select
Click Import.
The Import Certificate page appears.
Paste the copied certificate content into the long edit box, and click OK.
See Implementing Node Authentication, Implementing Nonrepudiation.
In order for REN Java clients, such as a queue server, MCF Log server, or CTI adapter, to communicate with an SSL-enabled REN server, these clients need to have SSL certificates available in a Java keystore. You must import the REN server certificates into the keystore used by each REN Java client. For the Queue servers and MCF Log servers, this will be the keystore used by the JRE in the PeopleSoft domain where the queue server and MCF Log server are running. For CTI adapters, this will be the JRE used by the adapter.
The following example shows how to install the REN server certificates into the JRE trust store for a queue server and MCF log server. You will need to repeat this procedure for every queue server domain being used. You will also need to perform a similar procedure for CTI adapters or any other REN Java client, if you are using them.
Note: If you have configured client authentication, you will need to import client certificates into the JRE keystore.
To import certificates in Java keystore:
Open a command prompt.
Enter the following command:
<PS_HOME>\jre\bin\keytool -import -trustcacerts -alias <alias-name> -file <CA Certificate Pem file> -keystore <full path to keystore used by the REN Java client> -storepass <password>Example:
<PS_HOME>\jre\bin\keytool -import -trustcacerts -alias PSFTCA -file ca.pem -keystore <PS_HOME>\jre\lib\security\cacerts -storepass changeit
Note: You will get an error message, sslv3 alert certificate unknown, if the certificate is not imported correctly.
To configure the REN server for SSL:
Select
The REN Server Definition page appears.
Select the SSL Only check box.
Select your REN Server certificate from the Certificate Alias drop-down list box.
Click Save.
To configure REN clusters:
Select
The REN Server Cluster page appears.
Update the REN server cluster URL using https and the SSL port.
Update the REN server browser URL using https and the SSL port.
Click Save.
Apart from the CA and REN server certificates, client authentication requires local node certificates, a client certificate for the browser, and a PSMCAPI certificate.
To install certificates for the local node:
Select
Click +.
Select Local Node from the Type drop-down list box.
Enter the local node name in Alias, and click Add Root.
Select the alias of the CA certificate from the Issuer Alias lookup button.
Click Request.
Complete the Common Name, Org Unit, Organization, Locality, State/Province, Country, Algorithm, Key Size, Email Address, and Challenge Pswd fields.
Note: The common name must be the machine name of the REN server machine, for example, PTA112.peoplesoft.com, where PTA112 is the machine name and .peoplesoft.com is the domain name.
Click OK.
The Certificates Signing Request dialog box appears.
Copy and paste the text from the Certificates Signing Request dialog box, and save the text in a file.
Click OK.
The Import link appears.
To obtain your local node certificate, submit the certificate request text to the CA that issued the selected root certificate.
The process of obtaining digital certificates varies, depending on the CA. Typically, a CA requires you to paste the content of the PEM-formatted CSR into a form that you submit online. The CA may send you the signed public key certificate by email or require you to download it from a specified web page.
Open the saved certificate file in a text editor, and then highlight and copy its entire contents.
Select
Click the Import link.
The Import Certificate page appears.
Paste the copied certificate content into the long edit box, and click OK.
See Implementing Node Authentication, Implementing Nonrepudiation.
You can generate the client certificate by openssl or keytool in P12 format and import it in the browser. Importing the certificates depends on the browser.
The following steps are an example of generating a client certificate using openssl. Clients can use keytool or Microsoft CA to generate the client certificate.
To generate the client certificate using openssl:
Generate the RSA private key.
openssl genrsa -des3 -out <Private key file>Example:
openssl genrsa des3 out renclient.key passout pass:pass 1024Generate a CSR file.
openssl req -config <filename> -new -M;key <Private key file> -out <CSR file>Example:
openssl req -config ..\apps\openssl.cnf -new -key renclient.key -x509 -days 365 -out renclient.csrGenerate a PEM format file.
openssl x509 -req -days 365 in <CSR file> -CA <CA PEM File> -CAkey<CA Key File> CAcreateserial -out <RenServer PEM file> -outform PEMNote: <CA key file> and <CA PEM file> are Certificate Authority Key file and Certificate Authority in PEM format respectively.
Example:
openssl x509 req days 365 in RENCLIENT.csr -CA ca.pem -CAkey ca.key -CAcreateserial -out renclient1.pem -outform PEM -passout pass:passGenerate a .p12 certificate for the browser.
openssl pkcs12 -export -in <RenServer PEM file> -out <.p12 file> -inkey <Private key file> -name <alias name>Example:
openssl pkcs12 -export -in renclient.pem -out renclient.p12 -inkey renclient.key -M;name renclient
To install PSMCAPI certificates:
Generate a private key in the keystore using the following command:
<PS_HOME>\jre\bin\keytool genkey dname CN=Company Name, OU=Organization Unit, O=M;Organization, L=Locality, S=State/Provenance, C=Country alias <alias Name> -M;keyalg RSA validity 365 keystore <PS_HOME>\jre\lib\cacerts storepass changeit keypass passwordGenerate the CSR using the following command:
PS_HOME>\jre\bin\keytool certreq alias <alias name> -file <certificate file name> -keystore <full path to the Java keystore used by the CTI adapter> storepass <password> keypass <password>To obtain your certificate, submit the CSR to the CA that issued the selected root certificate.
Import the signed certificates into Java keystore using the following command:
<PS_HOME>\jre\bin\keytool import alias <alias name> -file <certificate file .pem> -keystore <full path to the Java keystore used by the CTI adapter> storepass <password> keypass <password>Note: The clients must import the CA certificate in Java keystore of JRE of PSMCAPI for SSL communication with the REN server using the keytool command.
Certificates that are used to secure a Web server can be reused to secure a REN server. The Java keystore that stores these certificates can be converted to a PKCS #12 keystore. Subsequently, you can configure the REN server to use the newly created external PKCS #12 keystore when you define a REN server the SSL and the UseExternalKeystore options are selected.
To convert a Java keystore to a PKCS #12 keystore, you can use the PSExportToPKCS12.bat file that is delivered by Oracle.
Access PS_HOME/peoplesoft/Piabin and locate the PSExportToPKCS12.bat file.
Note: Ensure that the JAVA_HOME environment variable is set correctly.
Run the PSExportToPKCS12.bat in Windows or PSExportToPKCS12.sh in UNIX.
Note: The PSExportToPKCS12.bat and PSExportToPKCS12.sh scripts must be run using a version of the Sun Java Runtime environment compatible with your PeopleTools installation.
Image: Convert Java keystore to PKCS #12 keystore
This example illustrates the conversion of Java keystore to PKCS #12 keystore using the PSExportToPKCS12.bat file.
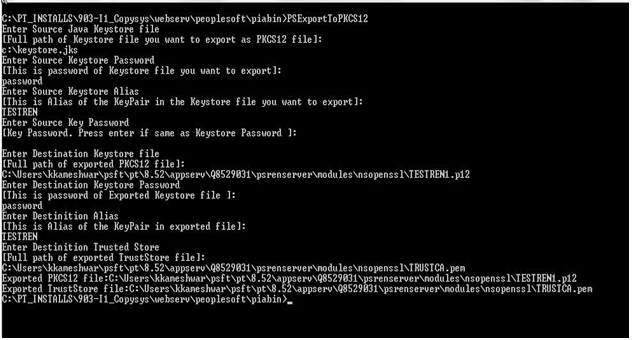
Note: The PSExportToPKCS12.bat file must be run prior to defining a REN server in the REN Server Configuration page. The file must not be run during the boot sequence of the application server.
Enter values for the following:
Source Java Keystore — the full path of Java Keystore.
Source Keystore Password — the password of the Java Keystore
Source Keystore Alias — alias of the KeyPair in the Java Keystore.
Source Key Password — if the password is the same as Source Keystore Password, you can leave it blank.
Destination Keystore — the full path of exported PKCS #12 keystore including the file extension (.p12 is preferred).
Destination Keystore Password — the password of exported keystore.
Destination Alias — alias of the KeyPair in exported keystore.
Destination Trusted Store — the full path of the exported TrustStore file including the file extension (.pem is preferred).
The Java Keystore is converted to PKCS #12 keystore.