ims-aka-profile
name profile protected-client-port PORT-SDC protected-server-port PORT-SDS encr-alg-list aes-cbc des-ede3-cbc null auth-alg-list hmac-sha-1-96
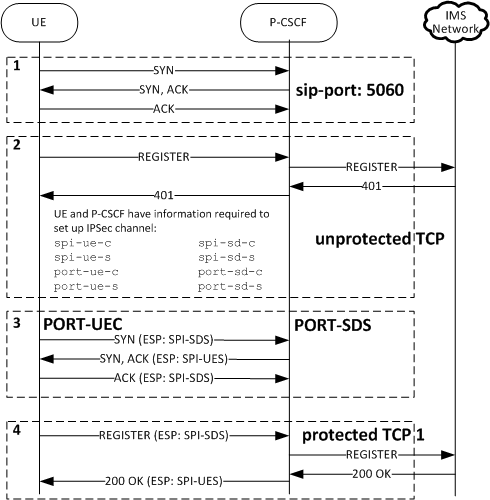
When the UE receives the 401Unauthorized challenge from the Oracle Communications Session Border Controller acting as P-CSCF, both devices have the information to set up security association for two IPSec channels. The UE establishes the second TCP connection via IPSec channel from the UE's PORT-UEC to the P-CSCF's PORT-SDS, and the registration process continues.
Hereafter, the UE uses the IPSec channels from communication.