DNS ALG
The Oracle® Enterprise Session Border Controller’s DNS Application Layer Gateway (ALG) feature provides an application layer gateway for DNS transactions on the Oracle® Enterprise Session Border Controller. With DNS ALG service configured, the Oracle® Enterprise Session Border Controller can support the appearance of multiple DNS servers on one side and a single DNS client on the other.
Overview
DNS ALG service provides an application layer gateway for use with DNS clients. DNS ALG service allows a client to access multiple DNS servers in different networks and provides routing to/from those servers. It also supports flexible address translation of the DNS query/response packets. These functions allow the DNS client to query many different domains from a single DNS server instance on the client side of the network.
The Oracle® Enterprise Session Border Controller’s DNS ALG service is commonly used when a DNS client (such as a call agent) needs to authenticate users. In this case, the DNS client that received a message from a certain network would need to authenticate the endpoint in a remote network. Since the DNS client and the sender of the message are on different networks, the Oracle® Enterprise Session Border Controller acts as an intermediary by interoperating with both.
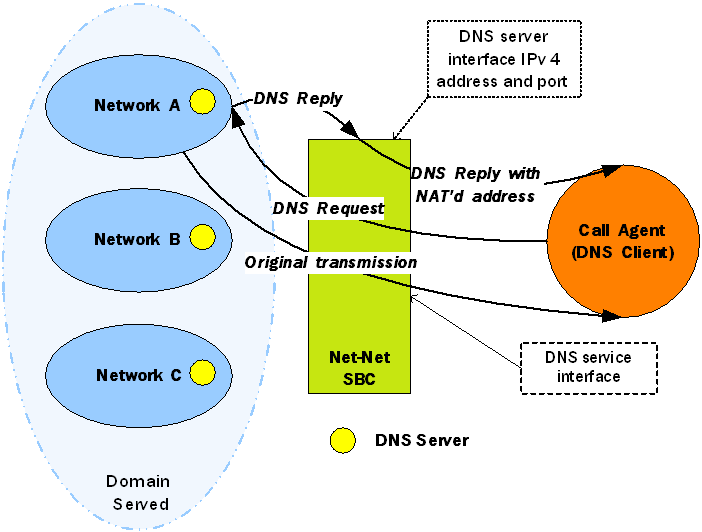
In the following diagram, the DNS client has received a message from an endpoint in Network A. Since the DNS client is in a different realm, however, the DNS client receives the message after the Oracle® Enterprise Session Border Controller has performed address translation. Then the DNS client initiates a DNS query on the translated address. The Oracle® Enterprise Session Border Controller forwards the DNS request to the DNS server in Network A, using the domain suffix to find the appropriate server. Network A’s DNS server returns a response containing its IPv4 address, and then the Oracle® Enterprise Session Border Controller takes that reply and performs a NAT on the private address. The private address is turned into a public one that the DNS client can use to authenticate the endpoint.
Configuring DNS ALG Service
This section tells you how to access and set the values you need depending on the configuration mechanism you choose. It also provides sample configurations for your reference.
Configuring DNS ALG service requires that you carry out two main procedures:
- Setting the name, realm, and DNS service IP interfaces
- Setting the appropriate parameters for DNS servers to use in other realms
Before You Configure
Before you begin to configure DNS ALG service on the Oracle® Enterprise Session Border Controller, complete the following steps.
- Configure the client realm that you are going to use in the main DNS ALG profile and note its name to use in this chapter’s configuration process.
- Configure the server realm that contains the DNS servers and note its name to use in this chapter’s configuration process.
- Determine the domain suffixes for the network where the DNS servers are located so that you can enter them in the domain suffix parameter.
- Devise the NAT scheme that you want to use when the DNS reply transits the Oracle® Enterprise Session Border Controller.
DNS ALG Service Name Configuration
This section explains how to configure the name of the DNS ALG service you are configuring and set its realm.
To add DNS ALG service:
DNS Transaction Timeout
To provide resiliency during DNS server failover, you can now enable a transaction timeout for DNS servers. If you have endpoints that are only capable of being configured with a single DNS server, this can allow DNS queries to be sent to the next configured server—even when contacting the Oracle® Enterprise Session Border Controller’s DNS ALG on a single IP address. So when the first server in the list times out, the request is sent to the next server in the list.
The Oracle® Enterprise Session Border Controller uses the transaction timeout value set in the dns-server-attributes configuration (part of the dns-config).
Dynamic ACL for the HTTP-ALG
The dynamic Access Control List (ACL) option for HTTP-Application Layer Gateway (ALG) provides Distributed Denial of Service (DDoS) attack protection for the HTTP port.
When you enable the dynamic ACL option, the system sets the trust level for static flow for the public listening socket defined in http-alg, public to untrusted. Each listening socket creates and manages its ACL list, which allows the listening socket to keep track of the number of received and invalid messages, the number of connections per endpoint, and so on. You can configure a different setting for each http-alg object.
Dynamic ACL for each endpoint is triggered by Session Initialization Protocol (SIP) registration messages. Upon receiving a SIP registration message, the SIP agent creates a dynamic ACL entry for the endpoint. If the 200 OK response is received, the ACL is promoted, allowing the HTTP message to go through the security domain. If SIP registration is unsuccessful, the ACL entry is removed and HTTP ingress messages are blocked from the endpoint. The ACL entry is removed upon incomplete registration renewal or telephone disconnect.
The following example describes the criteria and associated configuration item that result in a denied or allowed connection for both low and medium control levels.
| Criteria | Associated Configuration Item | Action |
|---|---|---|
| Exceed total number of connections for allowed | http-alg, max-incoming-conns | Connection denied |
| Exceed total connections per peer | http-alg, per-src-ip-mas-incoming-conns | Connection denied |
| ACL not promoted | Dynamically set on SIP registration | Connection denied |
| Exceed maximum number of packets/sec | realm-config, maximum-signal-threshold | Connection denied and peer is promoted |
| Exceed maximum number of error packets | Realm-config, invalid-signal-threshold | Connection denied and peer is promoted |
Oracle recommends setting
realm-config,
access-control-level
to
medium.
If a peer is promoted to trusted, the system performs DDoS checks on max number of packets/sec and max number of error packets allowed.
Demotions depend on the ream-config, access-control-trust-level setting for the realm. For more information on realm-config settings, see the ACLI Configuration Guide.
If you want to configure different ACL settings for SIP traffic and for HTTP-ALG traffic, you must configure a realm for each type of traffic.
Dynamic Access Control List (ACL) Settings for the HTTP Application Layer Gateway (ALG)
- access-control-trust-level
- invalid-signal-threshold
- maximum-signal-threshold
- untrusted-signal-threshold
- deny-period
For more information on realm-config settings, see the ACLI Configuration Guide.
Enable Dynamic Access Control List (ACL) for the HTTP Application Layer Gateway (ALG)
Dynamic ACL option, which provides Distributed Denial of Service (DDoS) attack protection for the HTTP port, is an option that you must enable.
Note:
Enabling dynamic access control for HTTP-ALG traffic reduces the number of available dynamic ACL entries on the session border controller, which may reduce the number of concurrent trusted endpoints that the system can support.


