System Configuration
You can configure the following System objects from the Configuration tab on the Web GUI:
Note:
Click Show Advanced in the navigation pane to display all of the System objects in the following list.| capture-receiver | Enable and configure a capture receiver. |
| fraud-protection | Enable and configure fraud protection. |
| host-route | Add one or more host routes. |
| network-interface | Add one or more network interfaces. |
| network-parameters | Configure TCP and SCTP parameters for the network. |
| ntp-config | Add one or more NTP servers and authentication servers. |
| phy-interface | Add one or more physical interfaces. |
| redundancy-config | Enable redundancy and add one or more peers. |
| snmp-community | Add one or more SNMP communities, including subnet ranges. |
| spl-config | Add an SPL option and one or more plugins. |
| system-access-list | Add one or more system access lists. |
| system-config | Configure the system settings for MIBS, SNMP functions, syslog servers, comm monitor, and more. |
| tdm-config | Enable and configure Time Division Multiplexing (TDM). |
| trap-receiver | Add one or more trap receivers. |
| web-server-config | Enable and configure a web server, including a TLS profile. |
Telephony Fraud Protection
You can configure the Oracle® Enterprise Session Border Controller (E-SBC) to protect against fraudulent calls by using lists of phone numbers to block, allow, redirect, and rate limit calls, according to rules that you configure to manage fraudulent traffic. The lists reside together in a single file that you specify as the source file in the fraud protection configuration. You can enable and manage fraud protection from the Web GUI, but only in Expert mode. You can enable fraud protection from the ACLI, but you cannot manage fraud protection from the ACLI. Telephony Fraud Protection is part of the advanced license. If you owned an Advanced license before the introduction of Telephony Fraud Protection, you must re-enable the license to access this feature.
Fraud Protection List Types and Uses
The E-SBC supports the following types of lists for protecting against fraudulent calls.
Blacklist—Use the blacklist to specify a fraudulent call based on the destination phone number or URI. You can add a known fraudulent destination to the blacklist by prefix or by fixed number. When the E-SBC receives a call to an entry on the blacklist, the system rejects the call according to the SIP response code that you specify.
White List—Use the white list to manage any exception to the blacklist. Suppose you choose to block a prefix such as +49 555 123 by way of the blacklist. This also blocks calls to individual numbers starting with this prefix, such as +49 555 123 666. If you add a prefix or individual number to the white list, the system allows calls to the specified prefix and number. Continuing with the previous example, if you add +49 555 123 6 to the white list, the system allows calls to +49 555 123 666, which was blocked by the blacklist entry of +49 555 123.
Redirect List—Use the redirect list to send a fraudulent call to an Interactive Voice Response (IVR) system, or to a different route. For example, you can intercept and redirect a call to a revenue-share fraud target in a foreign country to an end point that defeats the fraud. For example, you can redirect subscribers dialing a particular number and URI to an announcement to make them aware that an account is compromised and what they should do. You can use an external server to provide such an announcement or you can use the E-SBC media playback function.
Rate Limit List—Use rate limiting to limit the loss of money, performance, and availability that an attack might cause. While local ordinances may not allow you to completely block or suppress communication, as with a blacklist, you may want to reduce the impact with rate limiting until a network engineer can analyze an attack and plan remediation. Note that rate limiting may not function immediately after a High Availability switch over because the newly active system must re-calculate the call rate before it can apply rate limiting.
Configuration
To configure fraud protection, you must specify the source of fraud protection management and specify the file that contains the list of phone numbers to manage. The E-SBC or another device can manage fraud protection. You can create or upload the phone number list file by way of the File Management page on the Web GUI.
Administration
- An Admin with privileges can Refresh, Add, and Upload an unselected file, and Edit, Download, and Delete a selected file.
- An Admin with no privileges can only view the files.
- From the ACLI, use the show commands to view fraud protection statistics.
- From the Web GUI, use the Show Summary, Show Blacklist, Show White List, Show Call Redirect List, and Show Rate Limit Widgets.
Note:
The Telephony Fraud Protection feature does not affect emergency calls.Telephony Fraud Protection Target Matching Rules
- Longest match—The most specific entry takes precedence. For example, when 555-123-4000 is blacklisted and 555-123-* is white listed, the system blocks the call from 555-123-4000 because it is the longest match.
- Destination—When the system detects matches in both the SIP From header and the SIP To header, the match for the To header takes precedence.
- URI—When the system detects matches in both the USER and Host parts of a SIP URI, the match for the USER part takes precedence.
- SIP User-Agent header—Lowest priority. When nothing else matches, and there is a match for the User-Agent field, the E-SBC acts as instructed.
- Multiple instances—When the
system detects multiple instances of the same match length, or when the target
resides in multiple lists, the system uses the following order of precedence:
1. White list—Entries on the white list take precedence with no restrictions. For example, when 555-123-4567 is on both the blacklist and the white list, the system allows this call because the number is on the white list.
2. Blacklist
3. Redirect
4. Rate limiting
Note:
The telephony fraud protection feature does not affect emergency calls.The telephony fraud protection feature uses source or destination IP, source or destination name or phone number, and caller user-agent to identify a caller. The system enforces the following rules for formatting entries on a fraud protection list:
Hostname
Format: Enter the exact IP address or FQDN.
User name
Format: Enter the exact user name. For example: joe.user or joe_user.
User-Agent-Header
The User-Agent header text in the INVITE message from the first call leg. This text usually contains the brand and firmware version of the SIP device making the call. For example, sipcli/v1.8, Asterisk PBX 1.6.026-FONCORE-r78.
Format: Enter the exact text.
Phone Number
Format: Enter the exact number or a partial number using the following characters to increase the scope of the matches.
| Asterisk * | Use to indicate prefix matching, but only at the end of the pattern. For example, use 555* not *555. Do not use * in any other patterns, for example, in brackets [ ], parentheses ( ), or with an x. |
| Square Brackets [ ] | Use to enclose ranges in a pattern. Syntax:
[min-max]. For example: 555 [0000-9999].
The system considers 8[1-20]9 and 8[01-20]9 to
contain the same number of characters because the leading 0 is implied. The
system strictly enforces this pattern with respect to the range and the number
of characters, as follows:
|
| Character x | Use as a wildcard a the end of a dial pattern to mean 0-9. For example: 555xxx means match a number starting with 555 followed by 3 digits from 0-9. |
| Parentheses ( ) | Use to enclose optional digits in a pattern. For example: 555xx(xxxx) means match a number starting with 555 plus a minimum of 2 digits, and optionally up to 4 more digits. |
Telephony Fraud Protection File Activation
After you create, edit, or upload the fraud protection file, you must activate the file before the Oracle® Enterprise Session Border Controller (E-SBC) can use it as the source of the fraud protection lists. The system recognizes only one file at a time as the active file.
The first time you configure the E-SBC to manage fraud protection, the system activates the file when you save and activate the configuration. After the initial configuration, the system does not refresh the fraud protection file when you save and activate other configuration changes on the E-SBC. The exception occurs when you specify a new file name in the fraud protection configuration, make changes to other configurations, and save and activate all of the changes at one time.
After the initial configuration, use the following methods to activate the fraud protection file.
- New File—After you create or upload a new file, go to the Fraud Protection configuration page, enter the name of the new file, and click Save. The system prompts for activation upon a successful Save. Note that you can decline the inline activation and manually activate the file later. For example, you might want to edit an uploaded file before activation.
- Overwrite File—When you upload a file with the same name as the specified file, for example a file that you updated outside of the E-SBC, the system prompts for activation upon upload.
- Edit File—When you edit the specified file directly from the Web GUI, the system prompts for activation after you save the edits.
- Refresh File—When you want to use the ACLI to refresh the fraud protection file, send the file to the
E-SBC and use the
notify fped refreshcommand. The name of the file that you refresh must match the name of the file specified in the configuration.
Note:
The system displays an alert on the Notifications menu to remind you that the fraud protection file needs activation.Telephony Fraud Protection File Management
When you want to edit the telephony fraud protection file managed by the Oracle® Enterprise Session Border Controller (E-SBC), use the Web GUI. You cannot manage the fraud protection file from the ACLI. When another device manages the file, you can edit the file on the device and upload the file to the E-SBC or you can upload the file to the E-SBC and perform edits prior to activation.
A user with Admin privileges can work with the fraud protection file, while a user with no Admin privileges can only view the file. The Web GUI supports fraud protection file management only in the Expert mode.
From the System tab, the File Management page displays the File Type drop-down list that includes the Fraud Protection Table item. The Fraud Protection Table displays the list of fraud protection files on the E-SBC, as shown in the following illustration.
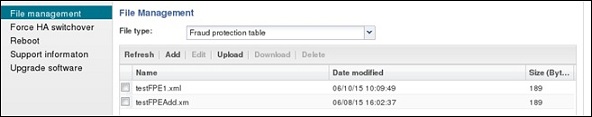
A privileged Admin can Refresh the display, Add a new file, and Upload a file. Upon selecting a file, the Admin can Edit, Download, and Delete a file.
File Upload from an External Source
When you want to use a fraud protection file from another source, you can upload the file to the E-SBC. The system puts the file into the /code/fpe directory. The system supports only the .gz, .gzip, and .xml file extensions for a fraud protection file. The Upload File dialog provides the option to activate the fraud protection file upon upload when the uploaded file name matches the configured file name, as shown in the following illustration.
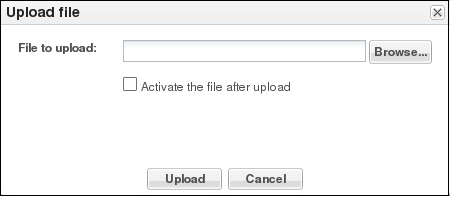
You can activate the file upon upload, or at a later time. For example, you might not activate the file upon upload because you want to edit the entries before activation. If you do not select the option to activate the file now, you must manually activate the file before the system can use the file. When the name of the uploaded file differs from the one specified in the configuration, the Upload dialog does not display the option to activate the file because the system cannot use the file until you specify the file name in the fraud protection configuration and activate the configuration.
File Creation
When you want to create a new fraud protection file on the E-SBC, use the Add button on the File Management page to launch the following dialog.
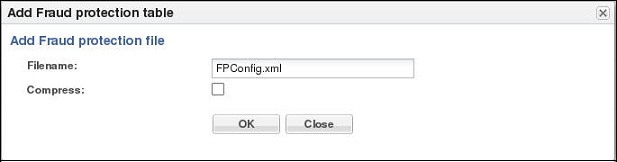
After you enter the file name and click OK, the system adds the new file to the list of Fraud Protection Tables on the File Management page. To make the new file the source file for Fraud Protection, you must specify the file name in the fraud protection configuration and activate the configuration.
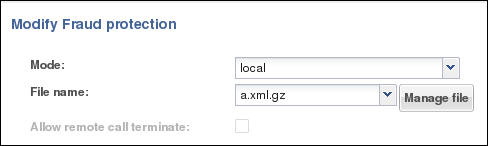
File Activation
The first time you configure the E-SBC to manage fraud protection, the system activates the file when you save and activate the configuration. After the initial configuration, the system does not refresh the fraud protection file when you save and activate configuration changes on the E-SBC, except when you specify a new file name in the fraud protection configuration.
List Maintenance
When you want to edit a fraud protection list, select the file on the File Management page, click Edit, select a list type on the Fraud Protection Table page, and click Edit.
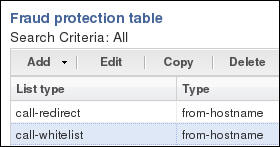
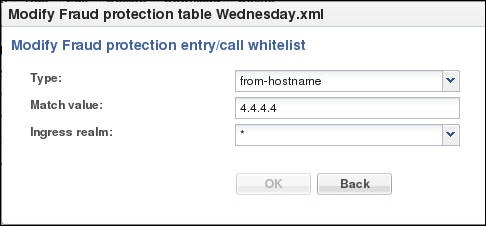
The system displays the corresponding dialog for editing the selected list type. For example, suppose that you selected call-whitelist in the preceding illustration. The system displays the following dialog.
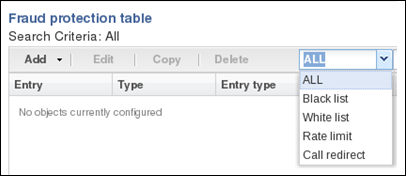
List Viewing Filters
The default view of the Fraud Protection Table displays all of the fraud protection entries in the system for all list types. For easier viewing, you can sort the table by list type. The following illustration shows the sorting selections.
Telephony Fraud Protection Data Types and Formats
Use the information in the following tables when you create or edit a fraud protection list in the Add Fraud Protection Entry and Modify Fraud Protection Entry dialogs.
Data Type Descriptions
The following table describes the data types listed in the Type drop-down list.
| from-hostname | The hostname from the SIP FROM header. |
| from-phone-number | The phone number from the SIP FROM header |
| from-username | The user name from the SIP FROM header. |
| to-hostname | The hostname from the SIP TO header. |
| to-phone-number | The phone number from the SIP TO header. |
| to-username | The user name from the SIP TO header. |
| user-agent-header | The SIP User-Agent header. |
Match Value Formats
The following table describes the formats required for the data types.
| hostname | Enter the exact IP address or FQDN. |
| username | Enter the exact user name. For example: joe.user or joe_user. |
| user-agent-header | Enter the exact text match to the SIP User-Agent header. For example: equipment vendor information. |
| phone-number | You can use the following characters for
phone-number:
|
Create a Telephony Fraud Protection File
When you want to use the Oracle® Enterprise Session Border Controller (E-SBC) to manage telephony fraud protection, the system requires a specified file to use as the source of the fraud protection lists. When you do not want to upload a file from elsewhere, you can create a new file on the system. You can create more files now or anytime after configuring fraud protection, but the system uses only the file named in the configuration as the source file. Note that you cannot create a fraud protection file by way of the ACLI. You must use the Web GUI.
- Confirm that the system displays the Expert mode.
Use the following procedure to create a new fraud protection file on the E-SBC, either before or after enabling fraud protection. See "Telephony Fraud Protection Data Types and Formats" for more information about the selections and formats for Type and Match Value.
- When fraud protection is not configured, see "Configure Telephony Fraud Protection - GUI."
- When fraud protection is configured, see "Activate a New Telephony Fraud Protection File -GUI."
Upload a Telephony Fraud Protection File
When you want to use a telephony fraud protection file from another source, you can upload the file to the Oracle® Enterprise Session Border Controller (E-SBC) by way of the Web GUI. You cannot upload the file by way of the ACLI.
- Confirm that the file to upload uses one of the following file extensions: .gz, .gzip, or .xml.
- Log on to the Web GUI directly to the Expert mode. (The system does not allow this procedure when you log on to Basic mode and switch to Expert mode.)
When you upload a fraud protection file, the system puts the file into the /code/fpe directory. The Upload File dialog provides the option to activate the fraud protection file immediately after the upload, or at a later time. For example, you might defer activation because you want to edit the uploaded file before it becomes the active file.
- When fraud protection is not configured, see "Configure Telephony Fraud Protection - GUI."
- When fraud protection is configured, see "Activate a New Telephony Fraud Protection File - GUI."
Configure Telephony Fraud Protection
The telephony fraud protection feature requires
configuration, which you can perform from the
Oracle® Enterprise Session Border Controller (E-SBC) Web GUI by way of
the
fraud-protection element listed under
System on the Configuration tab.
- Confirm that you own the Advanced license.
- Add or upload at least one telephony fraud protection file to the E-SBC.
- Note the name of the telephony fraud protection file that you want to use.
- Login to Expert mode directly. (The system does not allow this procedure when you login to Basic mode and switch to Expert mode.)
Use this procedure to enable telephony fraud protection management on the E-SBC. You must also specify the fraud protection file name and activate the configuration. You cannot specify multiple fraud protection files because the system recognizes only one file as the active source file.
Note:
The first time you configure the E-SBC to manage fraud protection, the system activates the file when you save and activate the configuration. After the initial configuration, the system does not refresh the fraud protection file when you save and activate other configuration changes on the E-SBC. The exception occurs when you specify a new file name in the fraud protection configuration, make changes to other configurations, and save and activate all of the changes at one time.Activate a New Telephony Fraud Protection File
When you create or upload a new telephony fraud protection file, you must activate the file before the system can use it as the source of the fraud protection lists. A new file is a file with a different name than one already in the system.
- Create or upload the new file.
- Note the name of the file that you want to activate.
- Confirm that the system displays the Expert mode.
You can activate a fraud protection file from the Web GUI only in Expert mode. In the following procedure, the Local mode establishes the Oracle® Enterprise Session Border Controller (E-SBC) as the source of fraud protection management.
Edit a Telephony Fraud Protection File
When you want to edit a telephony fraud protection file on the Oracle® Enterprise Session Border Controller (E-SBC), use the Web GUI. You cannot edit a telephony fraud protection file from the ACLI.
To edit a fraud protection file, go to the Web GUI and select a file from the list on the File Management page. When you click Edit, the system displays the fraud protection lists in the file. Select a list type and click Edit. The system displays the corresponding dialog for editing the selected type of list. See "Telephony Fraud Protection Data Types and Formats" for more information about the selections and formats for Type and Match Value.
You can use this procedure to edit any fraud protection file, but the system cannot use the file unless it is the file named in the activated configuration. The following procedure assumes editing the configured file.
Configure a Host Route
Use the host-routes element to insert entries into the Oracle® Enterprise Session Border Controller routing table to steer management traffic to the correct network.
- Confirm that the gateway for this host route is defined as a gateway for an existing network interface.
- Confirm that the system displays the Expert mode.
In the following procedure, note that no two host-route elements can use the same "dest network" address.
Configure the Network Interface
You must configure the network interface of the Oracle® Enterprise Session Border Controller (E-SBC) to communicate with the physical interface and the network.
- Confirm that the physical interface is configured. For more information, see "Physical Interface Configuration."
- Confirm that the system displays the Expert mode.
Use the network-interface object to configure the parameters for the network interface, which specifies a logical network interface over which you can configure one or more application SIP interfaces. Note that the E-SBC supports only one network interface.
- For High Availability (HA), configure redundancy. See "Redundancy Configuration" and "Configure Redundancy."
Configure NTP
Use the ntp-config element to associate the Network Time Protocol (NTP) server with theOracle® Enterprise Session Border Controller (E-SBC).
Use the following procedure to configure synchronization of the NTP server with the E-SBC.
Configure the Physical Interface
You must configure the physical interface of the Oracle® Enterprise Session Border Controller to connect to the network.
Use the phy-interface object to configure the physical interface for control, media, and maintenance operations. Perform this procedure for each operation type, which you will select in step 4.
- Configure the Network Interface. See "Configure the Network Interface."
High Availability
High Availability (HA) is a network configuration used to ensure that planned and unplanned outages do not disrupt service. In an HA configuration, Oracle® Enterprise Session Border Controllers (E-SBC) are deployed in a pair to deliver continuous high availability for interactive communication services. Two E-SBCs operating in this way are called an HA node. The HA node design ensures that no stable call is dropped in the event of an outage.
In an HA node, one E-SBC operates in the active mode and the other E-SBCoperates in the standby mode.
- Active. The active member of the HA node is the system actively processing signal and media traffic. The active member continuously monitors itself for internal processes and IP connectivity health. If the active member detects a condition that can interrupt or degrade service, it hands over its role as the active member of the HA node to the standby member.
- Standby. The standby member of the HA node is the backup system. The standby member is fully synchronized with the active member's session status, but it does not actively process signal and media traffic. The standby member monitors the status of the active member and it can assume the active role without the active system having to instruct it to do so. When the standby system assumes the active role, it notifies network management using an SNMP trap.
The E-SBC establishes active and standby roles in the following ways.
- If an E-SBC boots up and is alone in the network, it is automatically the active system. If you pair a second E-SBC with the first one to form an HA node, the second system automatically establishes itself as the standby.
- If both E-SBCs in the HA node boot up at the same time, they negotiate with each other for the active role. If both systems have perfect health, then the E-SBC with the lowest HA rear interface IPv4 address becomes the active E-SBC. The E-SBC with the higher HA rear interface IPv4 address becomes the standby E-SBC.
If the rear physical link between the twoE-SBCs is unresponsive during boot up or operation, both will attempt to become the active E-SBC. In this circumstance, processing does not work properly.
- it does not receive a checkpoint message from the active E-SBC for a certain period of time.
- it determines that the active E-SBC health score declined to an unacceptable level.
- the active E-SBC relinquishes the active role.
To produce a seamless switch over from one E-SBC to the other, the HA node members share their virtual MAC and virtual IP addresses for the media interfaces in a way that is similar to Virtual Router Redundancy Protocol (VRRP). Sharing these addresses eliminates the possibility that the MAC address and the IPv4 address set on one E-SBC in an HA node will be a single point of failure. Within the HA node, the E-SBCs advertise their current state and health to one another in checkpointing messages to apprise each one of the other one's status. Using the Oracle HA protocol, the E-SBCs communicate with UDP messages sent out and received on the rear interfaces. During a switch over, the standby E-SBC sends out an ARP request using the virtual MAC address to establish that MAC address on another physical port within the Ethernet switch. To the upstream router, the MAC address and IP address are still alive. Existing sessions continue uninterrupted.
Configure the Acme Packet 1100 for HA
The details in the procedures for configuring High Availability (HA) on the Acme Packet 1100 differ from configuring HA for other models of the Oracle® Enterprise Session Border Controller because the Acme Packet 1100 has a single management interface and it shares the wancom0 port for HA operations.
Use the following Expert mode procedures to configure the Acme Packet 1100 for HA operations. You must perform the physical interface configuration twice. One configuration sets the Management operations the other configuration sets the Media operations.
- Configure the physical interface for management. See "Configure the Physical Interface."
- Configure the physical interface for media. See "Configure the Physical Interface."
- Configure the network interface with addresses for the Primary and Secondary devices. See "Configure the Network Interface."
- Configure the peers for redundancy. See "Configure Redundancy."
Configure Redundancy
Use the redundancy-config element to configure the parameters to support redundancy for a High Availability (HA) pair of Oracle® Enterprise Session Border Controller (E-SBC) devices.
- Confirm that the physical interface for Control, the physical interface for Media, and the Network interface on the primaryE-SBC are configured for HA pairing.
Perform this procedure to configure redundancy for High Availability (HA) pairing of the primary E-SBC and the secondary E-SBC.
SNMP Trap Receiver
A trap receiver is an application used to receive, log, and view SNMP traps for monitoring the Oracle® Enterprise Session Border Controller (E-SBC).
An SNMP trap is the notification sent from a network device, such as an E-SBC, that declares a change in service. You can define one or more trap receivers on an E-SBC for redundancy or to segregate alarms with different severity levels to individual trap receivers. Each server on which an NMS is installed should be configured as a trap receiver on each E-SBC managed by an NMS.
You can select a filter level threshold that indicates the severity level at which a trap is sent to the trap receiver. The following table maps Syslog and SNMP alarms to trap receiver filter levels.
| Filter Level | Syslog Severity Level | (SNMP) Alarm Severity Level |
|---|---|---|
| All | Emergency (1)
Critical (2) Major (3) Minor (4) Warning (5) Notice (6) Info (7) Trace (8) Debug (9) |
Emergency
Critical Major Minor Warning |
| Critical | Emergency (1)
Critical (2) |
Emergency
Critical |
| Major | Emergency (1)
Critical (2) Major (3) |
Emergency
Critical Major |
| Minor | Emergency (1)
Critical (2) Major (3) Minor (4) |
Emergency
Critical Major Minor |
When configuring the trap-receiver element for use with Network Management Systems, Oracle recommends setting the filter-level parameter to All.
Configure an SNMP Trap Receiver
You can define one or more SNMP trap receivers on an Oracle® Enterprise Session Border Controller (E-SBC) for redundancy or to segregate alarms with different severity levels to individual trap receivers.
- Confirm that SNMP is configured.
- Note the names of users who are allowed to receive secure traps.
Oracle recommends that you configure each server with an NMS installed as a trap receiver on each E-SBC managed by an NMS. When configuring the trap-receiver element for use with Network Management Systems, Oracle recommends setting the filter-level parameter to All.
SNMP Community
A Simple Network Management Protocol (SNMP) community is a grouping of network devices and management stations used to define where information is sent and accepted. An SNMP device or agent might belong to more than one SNMP community. SNMP communities provide a type of password protection for viewing and setting management information within a community.
An SNMP community is a string used as a password by the SNMP manager to communicate with the SNMP agent. The SNMP community string allows access to statistics of other devices. The access is used to support the monitoring of devices attached to the network for conditions that warrant administrative attention. When an SNMP community is configured, the Oracle® Enterprise Session Border Controller (E-SBC) sends the community string along with all SNMP requests.
A community name value can also be used as a password to provide authentication, thereby limiting the NMS that has access to an E-SBC. With this field, the SNMP agent provides trivial authentication based on the community name that is exchanged in plain text SNMP messages. For example, public.
- Read-only. Allows GET requests. (Default)
- Read/Write. Allows both GET and SET requests.
IPv4 addresses that are valid within this SNMP community correspond with the IPv4 address of NMS applications that monitor or configure this E-SBC. Include the IPv4 addresses of each server on which an NMS is installed.
Only devices that support SNMPv1 and SNMPv2c protocol can use SNMP community strings. SNMPv3 uses username and password authentication, along with an encryption key.
Configure SNMP Community
Configure a Simple Network Management Protocol (SNMP) community to support the monitoring of devices, such as the Oracle® Enterprise Session Border Controller (E-SBC), attached to the network for conditions that warrant administrative attention.
- Confirm that SNMP is configured.
- Note the IP addresses that you want for this community.
Use this procedure to group network devices and management stations, and to set the access rights for the community. If you want to narrow the scope of the this community, use the Network Addresses option to specify one or more subnets. See "Subnet Ranges for SNMP Community" for more information.
Note:
Only devices that support SNMPv1 and SNMPv2c protocol can use SNMP community strings. SNMPv3 uses username and password authentication, along with an encryption key.Configure Subnet Ranges in SNMP Community
The SNMP system can dynamically originate SNMP GET requests from any host among a wide range of IP addresses. Due to the distributed nature of a typical network, the SNMP GET request may come from any IP address on an /8 netblock. It is not feasible to add all 16,777,216 possible IP addresses, one-by-one, to the snmp-community configuration. The solution for the Oracle® Enterprise Session Border Controller (E-SBC) is to allow subnet ranges in the snmp-community configuration. Such configuration allows the (E-SBC) to accept SNMP GET requests from any host in the specified subnet.
You can configure the subnet range from the ACLI and the Web GUI by way of the
IP-addresses parameter in the snmp-community object.
The IP-addresses parameter accepts subnet addresses in address prefix format (<Net_addr>/<Net_mask>), for example, 10.0.0.0/24. For an exact match, omit the number of bits, for example, 10.196.0.0. For multiple entries, use the parenthesis separated by comma format, for example, (172.16.0.0/16,192.168.4.0/24).
Configure system-config
The system-config object contains attributes and sub-objects that you use to configure system-level operations for the Oracle® Enterprise Session Border Controller (E-SBC).
Time Division Multiplexing
Oracle® designed the Time Division Multiplexing (TDM) functionality for companies planning to migrate from TDM to SIP trunks by using a hybrid TDM-SIP infrastructure, rather than adopting VoIP-SIP as their sole means of voice communications. The TDM interface on the Oracle® Enterprise Session Border Controller (E-SBC) provides switchover for egress audio calls, when the primary SIP trunk becomes unavailable. You can use TDM with legacy PBXs and other TDM devices.
- Only the Acme Packet 1100 and the Acme Packet 3900 platforms support TDM, which requires the optional TDM card.
- TDM supports bidirectional calls as well as unidirectional calls.
- TDM operations require the configuration of tdm-config and tdm-profile, as well as local policies for inbound and outbound traffic.
- The software upgrade procedure supports the TDM configuration.
- Options for the Acme Packet 1100 and the Acme Packet 3900 platforms include Calling-Line Identification Presentation (CLIP) and Connected-Line Identification Presentation (COLP).
- Options for the Acme Packet 1100 platform include the four-port Primary Rate Interface (PRI), the Euro ISDN Basic Rate Interface (BRI), and the Foreign Exchange Office-Foreign Subscriber Office (FXO-FXS) card.
Interface Requirements
PRI—Digium1TE133F single-port or Digium 1TE435BF four-port card.
BRI—Digium 1B433LF four-port card
FXS—Digium 1A8B04F eight-port card, green module (ports 1-4)
FXO—Diguim 1A8B04F eight-port card, red module (ports 5-8)
Notes
When you deploy either the Acme Packet 1100 or the Acme Packet 3900 in a High Availability (HA) pair, the active system cannot replicate calls between SIP and TDM to the standby system.
The Acme Packet 1100 does not support HA for the PRI, BRI, and FXO-FXS interfaces.
Time Division Multiplexing Configuration
To perform Time Division Multiplexing (TDM) operations on the Oracle® Enterprise Session Border Controller (E-SBC), you must enable TDM, specify the parameters for the interface in use, run the TDM configuration wizard, and create local policies for routing TDM traffic.
- Configure the
tdm-config element and its corresponding sub-elements. The
tdm-config element, located under
system, contains the parameters that are common to all TDM configurations. The sub-elements contain the particular parameters for the interface that the system detects in use on the
E-SBC. The system displays the sub-elements, as follows:
- When the E-SBC detects either the Primary Rate Interface (PRI) or the Basic Rate Interface (BRI) interface, tdm-config displays the tdm-profile sub-element with the parameters that correspond to the interface. See "Primary Rate Interface Support" and "Basic Rate Interface Support."
- When the E-SBC detects the Analog interface, tdm-config displays both the fxo-profile and the fxs-profile sub-elements with the parameters that correspond to the interface. See "Foreign Exchange Office-Foreign Exchange Subscriber Support."
- Run the TDM configuration wizard to complete the configuration. The wizard creates the realm, SIP interface, steering pools, and other necessary configuration elements including the network interface and the phy-interface for SIP call routing. With SRTP enabled (default), the wizard also creates the
media-sec-policy object, enables the
secured-network attribute for the
sip-interface
object, and configures the
media-sec-policy attribute for
realm-config. You can run the wizard from either the Web GUI (Set TDM Configuration) or the ACLI (setup tdm).
The Oracle® Enterprise Session Border Controller (E-SBC) requires running the TDM configuration wizard only after the initial TDM configuration. The system does not require you to run the wizard after you make changes to the existing configuration.
Note:
When the Oracle Session Delivery Manager (SDM) manages the E-SBC, you configure TDM from the SDM and you do not need to run the TDM configuration wizard. See "Time Division Multiplexing (TDM) Settings on the Session Delivery Manager (SDM)" for the required settings. - Configure the local policy for routing traffic through the TDM interface. For unidirectional TDM call routing, the system requires a local policy only for the call direction that you want. For example, inbound-only or outbound-only. For bi-directional TDM call routing, create both inbound and outbound local policies. See "Local Policy Configuration for Time Division Multiplexing."
- ACLI—Use the tdm-config, tdm-profile, fxo-profile, and fxs-profile elements located under system.
- Web GUI—Basic mode. Double-click the TDM icon in the network diagram to display the TDM configuration dialog.
- Web GUI—Expert mode. Use the tdm-config, tdm-profile, fxo-profile, and fxs-profile elements located under system.
- Session Delivery Manager (SDM)—Launch the Web GUI from SDM and use the tdm-config, tdm-profile, fxo-profile, and fxs-profile elements located under system.
Incoming Call Pattern Guidelines
When you configure either the Primary Rate Interface (PRI) or Basic Rate Interface (BRI) interface for Time Division Multiplexing (TDM), you can set a list of extension numbers and match patterns for routing incoming calls. You can specify exact matches as well as patterns that route to a range of destinations.
For example, suppose that a company with 300 employees deploys the Oracle® Enterprise Session Border Controller (E-SBC) and connects to the PSTN network by way of an ISDN interface. The company allocates 300 extension numbers: numbers 7100 - 7399 for employee desk phones, and number 70 for the reception desk so that it is easy to remember.
The service provider assigns the prefix 49331200 to the company, so the reception desk PSTN number becomes 4933120070 and the employee numbers become 493312007100 , 493312007101-493312007399.
The incoming pattern in this example will match either the reception desk number or one of the other extensions. When the match is successful, the received number is complete and the call setup can proceed. You can configure TDM to match the reception desk number as a whole: "4933120070," and to match any of the other extensions through a single pattern: "_493312007[1-3]XX". To put these rules together, set the incoming-pattern parameter to the following value: "4933120070|_493312007[1-3]XX".
In match patterns, separate single extension numbers with the vertical bar (|) character. Start a match pattern with the underscore (_) character preceding the first number of the pattern. Do not use the underscore with an exact match. Type the exact match, starting with the first number. An exact match does not use In an extension pattern, note the meaning of the following characters:
X matches any digit from 0-9
Z matches any digit from 1-9
N matches any digit from 2-9
[1237-9] matches any digit in the brackets (in this example, 1,2,3,7,8,9).
. wildcard, matches one or more characters
! wildcard, matches zero or more characters immediately
Configure the Single-Port Primary Rate Interface
The Acme Packet 1100 Supports the single-port ISDN Primary Rate Interface (PRI). To configure the PRI interface, you must set the parameters in tdm-config and tdm-profile under system. After you create the configuration, you must run either the Set TDM Configuration wizard from the Web GUI or the setup tdm command from the ACLI to complete the configuration.
- Confirm the presence of the single-port PRI interface on the Acme Packet 1100.
Note that because the single-port interface supports only one profile, you can set either pri_cpe (Customer Premises Equipment) or pri_net (Network) for signaling. The setting you choose depends on the setting at the other end of the connection. Set this configuration to the opposite of the other end. For example, when the setting at the other end is pri_net, set pri_cpe in this configuration.
Note:
The system requires the four-port interface to support profiles for both pri_cpe and pri_net.- Run the TDM configuration wizard.
- Configure the inbound and outbound TDM local policies.
Configure the Four-Port Primary Rate Interface
The Acme Packet 1100 and the Acme Packet 3900 support the four-port ISDN Primary Rate Interface (PRI) for carrying multiple Digital Signal 0 (DS0) voice and data transmissions between the network and an endpoint. To configure the PRI interface, you must set the parameters in tdm-config and tdm-profile under system. After you create the configuration, you must run either the Set TDM Configuration wizard from the Web GUI or the setup tdm command from the ACLI to complete the configuration.
- Confirm the presence of the four-port PRI.
- Plan the number of TDM profiles that you want. (You can add or delete profiles later.)
When the Oracle® Enterprise Session Border Controller (E-SBC) detects the PRI interface interface, it displays the corresponding configuration parameters. In the PRI configuration, the line mode that you specify dictates certain corresponding settings. You can set either t1 or e1 for line-mode, but note that each one requires certain uniquely compatible settings. For example, when you specify the t1 line mode you must specify esf for the framing-value. Do not specify an e1 value for the t1 line mode or a t1 value for the e1 line mode. The following procedure shows the specific t1 and e1 settings, where required.
- Run the TDM configuration wizard.
- Configure the inbound and outbound TDM local policies.
Configure the Basic Rate Interface
To configure the Basic Rate Interface (BRI) card, you must set the parameters in tdm-config and tdm-profile under system. Note that the system supports coexisting profiles for both bri_cpe (Customer Premises Equipment) and bri_net (Network). After you create the configuration, you must run either the Set TDM Configuration wizard from the Web GUI or the setup tdm command from the ACLI to complete the configuration.
- Confirm the presence of the BRI interface on the Acme Packet 1100.
- Plan the number of TDM profiles that you want. (You can add or delete profiles later, if your needs change.)
When the Oracle® Enterprise Session Border Controller (E-SBC) detects the BRI interface, it displays the corresponding parameters and inserts certain values that you cannot change.
- Run the TDM configuration wizard.
- Configure the inbound and outbound TDM local policies.
Configure Inbound TDM Policy
Time Division Multiplexing (TDM) operations require policies for directing traffic to and from the TDM realm. In the following procedure, you specify the attributes for inbound TDM traffic.
- Configure TDM.
For the Policy priority parameter, the priority hierarchy from lowest to highest is none, normal, non-urgent, urgent, emergency. None means no priority. Each higher priority handles sessions at its level plus the sessions in the priorities above it. For example, non-urgent also handles sessions for urgent and emergency.
In the following procedure, the to-address and from-address can match the caller and called phone number or you can use any of the valid values noted. Note that you must use tdmRealm, which is case sensitive, for source-realm.
- If your deployment requires an outbound TDM local policy, see "Configure the Outbound TDM Policy."
Configure the Outbound TDM Policy
Time Division Multiplexing (TDM) operations require policies for directing traffic to and from the TDM realm. In the following procedure, you specify the attributes for outbound TDM traffic.
For the Policy priority parameter, the priority hierarchy from lowest to highest is none, normal, non-urgent, urgent, emergency. None means no priority. Each higher priority handles sessions at its level plus the sessions in the priorities above it. For example, non-urgent also handles sessions for urgent and emergency.
For the next-hop parameter in policy-attributes, use the name of the tdm-profile that you want associate with this policy.
- If your deployment requires an inbound TDM local policy, see "Configure the Inbound TDM Policy."
Configure Outbound Local Policy with TDM Backup
To complete the Time Division Multiplexing (TDM) configuration for redundancy, you must configure the TDM local routing policy.
- Confirm that a TDM configuration exists.
- Confirm that a policy exists for the realm.
To configure TDM for backup, add the tdm profile as a second attribute to the local policy.
Add an FXO-FXS Profile
When your deployment requires Foreign Exchange Office-Foreign Exchange Subscriber (FXO-FXS) profiles, you can add up to four profiles each to support different attributes at different endpoints. For example, you might create profiles based on user name, department, location, and so on. You can create FXO profiles only, FSO profiles only, or both. To configure the FXO-FXS profiles, go to tdm-config under system, and create the profiles that you need.
- Requires the FXO-FXS interface
The configuration process includes configuring tdm-config and a corresponding fxo-profile or fxo-profile.
- Run the TDM configuration wizard.
- Configure the inbound and outbound TDM local policies.
Perform FXO Port Tuning
Tuning the Foreign Exchange Office (FXO) ports can help the echo canceller to work more efficiently. The setup fxotune run command creates the fxotune configuration file, which contains the script that fine tunes the Digium Asterisk Hardware Device Interface (DAHDI) FXO channels, and restarts the system. The tuning takes place during the restart. After FXO tuning, the system saves the result in a configuration file that is automatically applied after each subsequent restart. No additional user action is necessary.
- Configure one or more FXO profiles and activate the configuration.
Note that the following procedure requires a system restart, which can take longer than usual due to the tuning process.
- From the command line, type setup fxotune run.
- Restart the E-SBC.
Reset the FXO Port Tuning Defaults
If you ever want to reset the setup fxotune run boot parameter, use the setup fxotune reset command. The command resets the boot parameter for setup fxotune run to the default tuning values and removes the fxotune configuration file.
Note that the following procedure requires a system restart.
- From the command line, type setup fxotune reset.
- Restart the E-SBC.
Configure Fax Transcoding for the Acme Packet 1100
The system requires two codec policies, two local policies, and two realms to support fax transcoding.
- Before you begin, configure one realm that points to the Internet and one realm that points to the Time Division Multiplexing (TDM) interface.
For example, suppose you name the internet-facing codec policy "Remote" and you name the TDM-facing codec policy "TDM." Use the following guidelines for configuration:
- In the "Remote" codec-policy, set allow-codecs to T.38 PCMU PCMA and set add-codecs-on-egress to T.38OFD.
- In the "TDM" codec-policy, set allow-codecs to PCMU PCMA and set add-codecs-on-egress to G711FB.
- In the "Remote" local-policy, set source-realm to remote.
- In the "TDM" local-policy, set source-realm to tdmRealm.
- In the "Remote" realm-config, set identifier to remote, set the codec-policy type, and set codec-manip-in-realm to enabled.
- In the "TDM" realm-config, set identifier to tdmRealm, set the codec-policy type, and set codec-manip-in-realm to enabled.
Configure Overlap Dialing for Call Routing
When you enable overlap dialing and set the incoming match pattern, the Oracle® Enterprise Session Border Controller (E-SBC) can work with the information in the SETUP message to successfully route calls through the Primary Rate Interface (PRI) and Basic Rate Interface (BRI) in a Time Division Multiplexing (TDM ) deployment.
- Plan the match patterns that you want for incoming calls. See "Incoming Call Patterns Guidelines" for rules and syntax.
- Confirm that the tdm-profile that you want to enable for overlap dialing exists.
Note:
If the tdm-profile that you want does not exist, you can set the overlap dial and incoming-pattern parameters when you create the profile. The following procedure assumes the profile already exists.Access tdm-confg and use the tdm-profile sub-element to set the overlap dial and incoming-pattern parameters.
Web Server Configuration
The Web server is a software application that helps to deliver Web content that you can access through the Internet. The Web server runs the Enterprise application called the Web GUI.
Every Web server has an IP address and sometimes a domain name. For example, if you enter the URL http://www.acmepacket.com/index.html in your browser, the browser sends a request to the Web server with domain name is acmepacket.com. The server fetches the page named index.html and sends it to the browser.
If you enter http://132.45.6.5, and this address has been configured by your Administrator to access the Web GUI, the server fetches the page and displays the Web GUI logon page to your browser.
This section provides a procedure for configuring the Web server in your network.



