Firewalld Configuration Overview
The firewalld service provides a strong line of defense in securing ISR Servers and Services. The firewall is, by default, enabled and configured to provide a secure operating environment for ISR. There are three default zones utilized by ISR services:
- Public—The default firewall
zone interfacing to the most networks; This zone is utilized by the ‘Admin’
Ethernet interface. Services utilizing this zone include:
- SSH
- ISR Dashboard (HTTPS)
- Trusted—An internal firewall
zone used by Data services such as:
- MySQL (for non-VM RSS hosts)
- ISR Web Services (HTTPS)
- ISR Web Services (HTTP)
- VoIP traffic (SIPREC/RTP)
- Internal—An internal
firewall zone used by ISR VMs for communication. Services include:
- MySQL
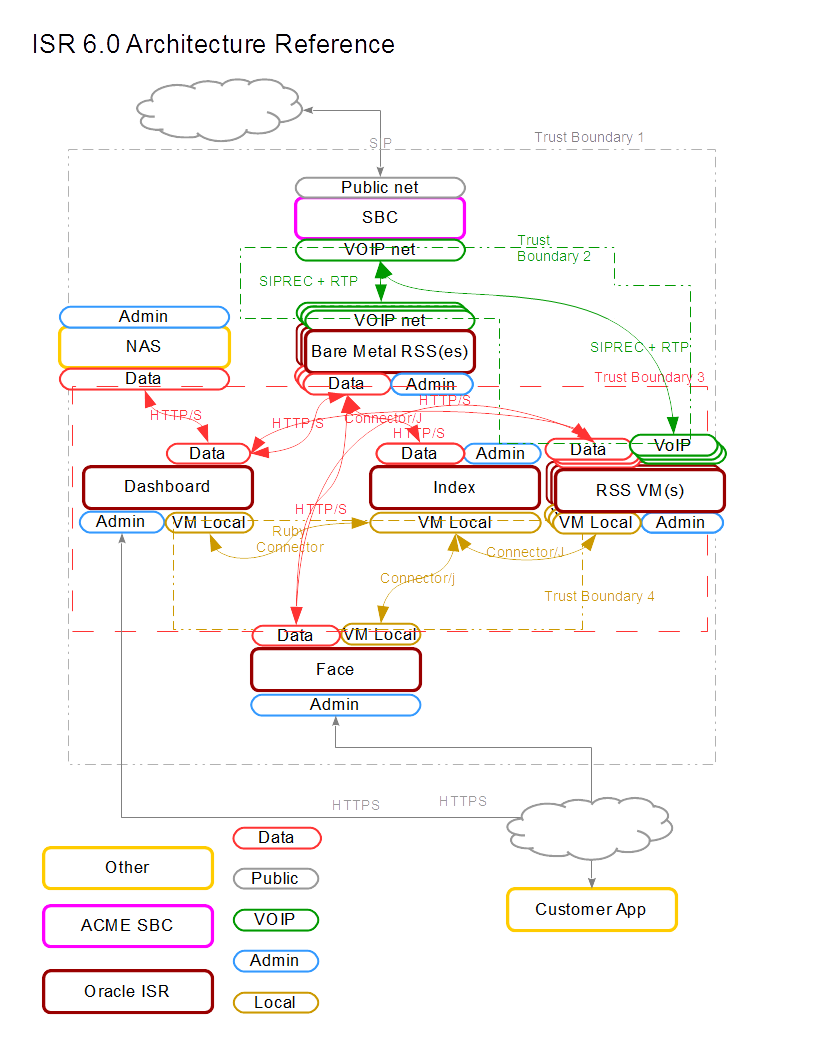
ISR Firewalld Configuration
By default, ISR provides a secure default firewall configuration which should not require end user changes. However, it may be necessary to modify these settings to disable unnecessary ISR services, or to allow communication with third party services. To help ensure the security of your systems, it is recommended that you do not disable the firewall.
- Service Configuration Files—ISR provides firewall zone configuration files, found in the
/opt/isr/security/firewalld/services/directory. These files outline the services and ports utilized by the particular ISR service and configure the firewalld service to allow these communications. - Interface/Zone Settings—ISR configures the firewall based on the “ISR Network Interface Mapping” performed during initial configuration.
- Service/Zone Settings—ISR comes preconfigured to allow the ISR Services to be run only on specified zones.
Modifying ISR Firewalld Configuration
By default, the firewall is configured upon installation to allow all services to communicate on specified interfaces within the firewalld zones. However, you may need to move a service to an additional zone, or remove an extraneous firewall service from a particular zone.
Common changes include:
- Adding the ISR Dashboard service to the public zone if it must be reachable from external addresses. This can be done by entering the following commands on the ISR Dashboard host:
$ sudo firewall-cmd --zone=public --add-service dashboard $ sudo firewall-cmd --zone=public --add-service dashboard -–permanent
Similarly, it can be removed from the internal zone:$ sudo firewall-cmd --zone=internal --remove-service dashboard $ sudo firewall-cmd --zone=internal --remove-service dashboard -–permanent
- Disabling unused components such as the ISR converter service.
$ sudo firewall-cmd --zone=data --remove-service converter $ sudo firewall-cmd --zone=data --remove-service converter –-permanent



