| Oracle® Communications Security Edge Protection Proxy (SEPP) Cloud Native User's Guide Release 1.0 F16984-01 |
|
 Previous |
 Next |
| Oracle® Communications Security Edge Protection Proxy (SEPP) Cloud Native User's Guide Release 1.0 F16984-01 |
|
 Previous |
 Next |
N32-C Flow:
The following is performed for N32-C flow:
This is the control plane of the N32 interface, When the SEPPs have mutually authenticated each other and when the negotiated the security mechanism to use over N32 is Transport Layer Security, the SEPPs use the established TLS connection (N32-c connection) to negotiate the N32 specific associated security configuration parameters. Without Security Capability negotiation completed, SEPP can not process any data messages (N32-F) from far end SEPP.
Note:
SEPP implementation supports only TLS security mechanism.For more information on security capability negotiation, see Security Capability Negotiation between SEPPs.
Note:
In the call flow diagram, Error Response is not supported. The server with Responding SEPP will send success response as TLS which is configurable using server's helm chart. For more information on helm chart, see the OCSEPP Cloud Native Installation Guide
N32-F Flow:
Following diagram illustrates a sample N32-F call flow between consumer & provider SEPP:
Figure 2-2 N32-F Flow
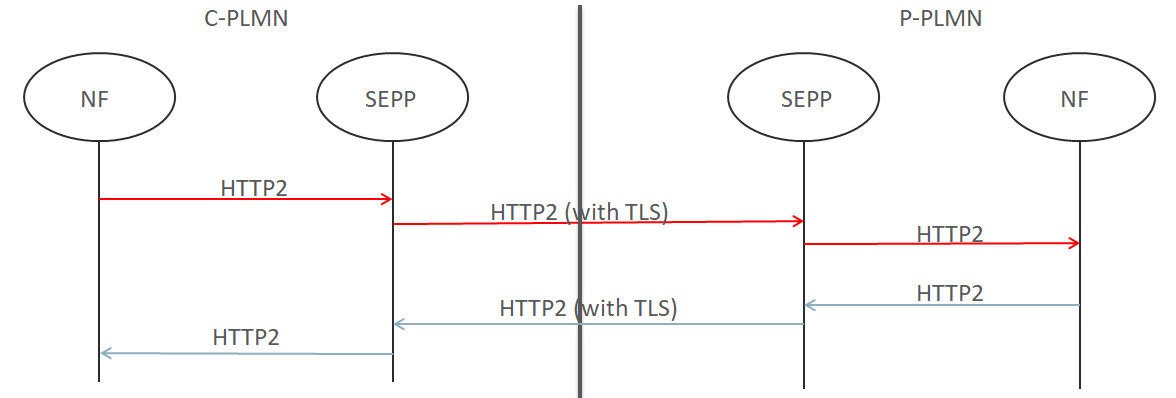
The following is performed for N32-F flow:
This is the data plane of the N32 interface, all data messages are exchanged via this interface over HTTP2. The SEPP receives the HTTP/2 request/response messages from the Network Function (NF). It encrypts the outbound messages based on agreed security capability parameters before they are sent on the N32-f interface to the SEPP in the other PLMN. Then, it decrypts the inbound messages from far-end SEPP before sending it to NF in the PLMN .