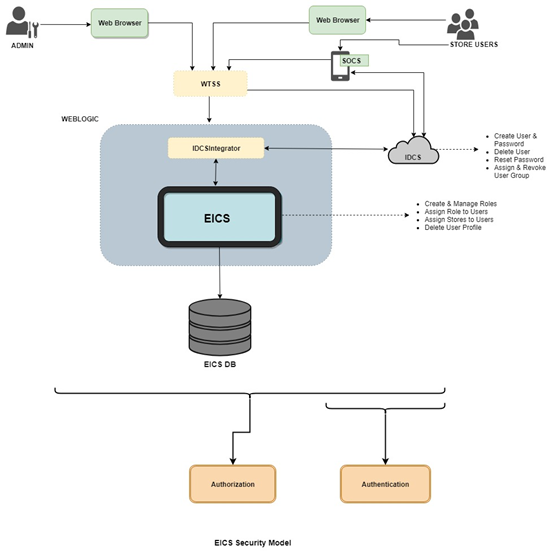
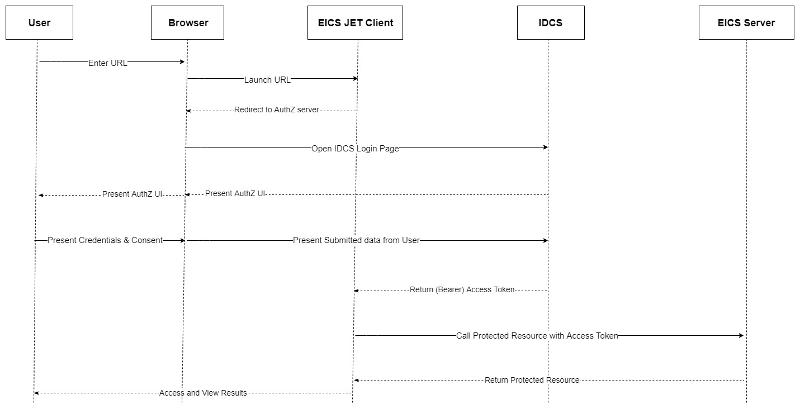
2 Security Model
Terminology
This section defines Security Terms used.
| Term | Definition |
|---|---|
|
Application Administrator |
A customer application admin user who can perform application configurations via EICS admin screen. |
|
Application Implementer |
System implementer is user who implements the application. |
|
Application Role |
An application role is a collection of users and other application roles. Application roles are defined in applications and they are not necessarily known to a Java Container. |
|
Customer Cloud Administrator |
A delegated customer cloud user for customer cloud management tasks, for example create customer security admin user, and other users. |
|
Customer Security Admin |
A customer security admin user who can create customer users and assign application roles. Please note that sometimes this may not be setup as a separate user than application administrator. |
|
Retail Home User |
A user who can access EICS tile reports on Retail Home and navigate to related operational views in EICS from there. |
|
Security Group |
A collection of users and groups. These groups are defined in security store, and are known to java EE server container. |
|
Store Manager |
A user who performs store manager role. |
|
Store User |
A user who performs store operations with assigned role permissions. |
|
System Operator |
Will be used by Oracle cloud team for debug. |
|
User |
A user is an end-user accessing a service or application. |
In addition to application users, integration users need to be setup based on integrated applications.
User Access to Functionality
Users of SIOCS have roles through which they gain access to functions and data.
Security implementation involves the management of:
-
User creations
-
Assigning security groups to corporate operational users
-
Assigning application roles to store users
Security Groups
EICS comes with 9 groups used for special purpose access, which are managed through IDCS.
The group sim_admin_users is required for access to administration tasks, such as managing configuration settings or translations.
This group should only be assigned to system operators and administrators.
This group should only be assigned to system operators and batch administrators.
The group sim_batch_users is required for access to batch related tasks, such as job management or scheduling.
The group sim_global_store_users grants the user access to all store locations.
This group should only be assigned to system operators, and administrators or special users requiring access to all store locations.
The group sim_integration_users is required for accessing integration resources, such as web services.
This group should only be assigned to users designated for application integration, not those requiring access to the application UI.
Users that are only integrating with EICS are considered integration users, for example, the RIB injection user is a typical case of an integration user.
These users do not require access to the EICS client applications, and therefore do not require store assignments or role assignments (permissions).
The group sim_mps_users is required for access to MPS (message processing service) related tasks, such as staged message maintenance or work type management.
This group should only be assigned to system operators and MPS administrators.
The group sim_security_users is required for access to security management tasks, such as role maintenance and user role/store assignments.
This group should only be assigned to system operators and security administrators.
Users accessing application UI features that are restricted by group access must also be granted the relevant permissions through role and store assignments.
A regular store user should not require any security group assignments for accessing the application UI.
The group sim_sysop_users is required for access to restricted areas of the application, such as certain system configuration settings.
This group should only be assigned to system operators, which are typically the cloud operator.
The group sim_full_permission_users allows the user to gain access to all available permissions without any database role assignment.
This group should only be assigned to system operator and initial customer admin user.
Note:
This full permissions group does not provide full data permission access. For performing administration operations on EICS, user should be assigned administer role in EICS application.The group sim_retail_home_users is required for retail home application to successfully call EICS APIs to fetch tile report data.
This group should only be assigned to retail home users.
For pre-production deployment, EICS provides the set of nine security groups as mentioned above but with PREPROD appended to the group names for easy differentiation.
Security Group assignments are typically used for special purpose access such as integration or various administration tasks. Enterprise Groups are assigned to users through IDCS.
This table identifies predefined application security groups:
Table 2-2 Predefined Application Security Groups
| Cloud Service or Options | Predefined Group |
|---|---|
|
Admin Service |
sim_admin_users |
|
Security Service |
sim security_users |
|
Message Processing Service |
sim_mps_users |
|
Batch Service |
sim_batch_users |
|
All store locations |
sim_global_store_users |
|
Perform application system configurations (both non-restricted and restricted) |
sim_sysop_users |
|
Initial user setup to login to EICS application |
sim_full_permission_users |
|
Retail Home Service |
sim_retail_home_users |
Application Roles
Application roles are a collection of permissions that are assigned to users for specific or all of their assigned stores. These permissions are used to control access to application functionality and data. Roles are created, managed, and assigned to users through the EICS security admin UI.
EICS has the following predefined application roles.
Table 2-3 Predefined Application Roles
| Operations | Role |
|---|---|
|
Admin permission role |
ADMINISTRATOR |
|
Store Manager permission role |
MANAGER |
|
Retail Home permission role |
RETAIL HOME |
Role Permissions Configuration
There are 350+ configuration settings that decide how users access functionality. For details, see the Oracle Retail Enterprise Inventory Cloud Service Administration Guide - Configuration chapter.
User Types with Security Groups and Application Roles
Table 2-4 User Types with Security Groups and Application Roles
| Application User Type | Job Duties | Application Roles Assigned (User Role Assignment is via EICS Security Admin Console) | Security Enterprise Group Assigned (User Security Group Assignment is via Oracle IDCS) |
|---|---|---|---|
|
Initial Application Admin User |
To access EICS application and create other application admin and store users. |
N/A |
sim_admin_users sim_security_users sim_mps_users sim_batch_users sim_global_store_users sim_full_permission_users |
|
Application Admin User |
Perform all administration activities, setup other customer application store users and perform application configuration. |
ADMINISTRATOR |
sim_admin_users sim_security_users sim_mps_users sim_batch_users sim_global_store_users |
|
Store Users |
Perform store operations in store using Mobile client. |
Custom Defined Role with selected role permissions. |
N/A |
|
Integration Users |
External system invokes EICS provided Integration Services. See Integration Implementation sections for additional details. |
N/A |
sim_integration_users |
|
Retail Home User |
Access EICS tiles on retail home and navigate to related operational views in EICS. |
RETAIL HOME |
sim_retail_home_users |
User Provisioning
Before users can access the Oracle Retail Enterprise Inventory Cloud Service applications it is necessary to provision each user access to the system, and assign groups, stores, and roles to each user to control what functionality will be available to them. The access provisioning is done using Oracle Identity Cloud Service (IDCS) for initial customer admin user. This user can create or manage other user provisioning via IDCS and the EICS security admin UI.
Group assignments are typically used for special purpose access such as integration or various administration tasks. Groups are assigned to users through IDCS.
The application client uses store based sessions for performing business operations. Store assignments control the stores available for a user to login to. Users can be assigned access to specific stores through the EICS security admin UI.
Application roles are a collection of permissions that are assigned to users for specific or all of their assigned stores. These permissions are used to control access to application functionality and data. Roles are created, managed, and assigned to users through the EICS security admin UI.
User Access
It is recommended that users are granted the least level of access they require to perform their duties.
Users should not be reused or shared by multiple people or for multiple purposes.
For example, users created for integration purposes should not be granted access required for application UI usage.
Oracle Identity Cloud Service User and Group Management
Oracle Identity Cloud Service (IDCS) provides a fully integrated service that delivers all the core identity and access management capabilities through a multi-tenant Cloud platform.
For instructions on managing users and groups in IDCS, follow the Manage Users and Groups IDCS document at the following URL:
https://docs.oracle.com/en/cloud/paas/identity-cloud/index.html