Understanding the PeopleSoft WS-Security for WSRP
Important! The procedures for configuring WSRP consumption and production must be performed in the order set out here.
Complete configuration of WS-Security for WSRP in the following order:
Set up WSRP security options. See Setting Up WSRP Security Options.
Set up Security Assertion Markup Language (SAML). See Setting Up SAML.
Configure WS-Security for PeopleSoft as a WSRP producer. See Configuring WS-Security for PeopleSoft as a WSRP Producer.
Define nodes with WS-Security. See Defining Nodes with WS-Security.
WSRP involves passing SOAP messages between the WSRP consumer and producer. To safely use WSRP, Oracle provides message-level security between the consumer and the producer by incorporating WS-Security.
WS-Security is an extension to the concept of the SOAP envelope header that enables applications to construct secure SOAP message exchanges. It also provides a means for associating security tokens with messages.
WS-Security provides three main mechanisms:
Integration solution between the WSRP consumer and producer: The consumer passes their identification to the producer as part of the SOAP message so that the producer can verify the identity and produce WSRP content without requiring the user to sign in.
Message integrity: Ensures that messages have not been tampered with.
Message confidentiality: Guarantees that messages are protected.
Image: WS-Security SOAP message structure
This diagram shows the SOAP envelope, SOAP header, and SOAP body and how WS-Security embeds the security token in the SOAP messages:
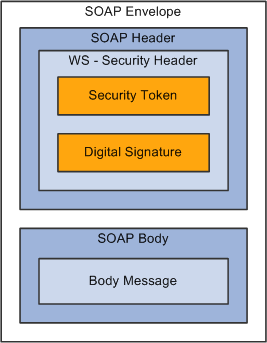
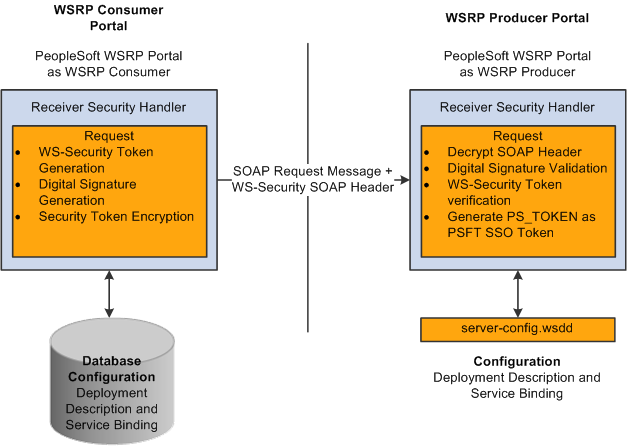
When the PeopleSoft portal is a WSRP consumer, the user ID and password of the user signed in to the portal is placed into a Username or SAML token in the SOAP header, and the WSRP portlet consumes it. It is presented to each portlet during the initial markup request. The security handler performs WS-Security token generation, digital signature generation, and token encryption before the PeopleSoft system sends the SOAP request message and the WS-Security SOAP header.
Important! The PeopleSoft portal authentication information (both the user ID and password) must be the same as the producer's.
When the PeopleSoft system is the producing system, the consuming system sends PeopleSoft the SOAP request message and the WS-Security SOAP header. The portal accepts the Username token in the WS-Security header from the remote portal, assuming that the ID and password are acceptable to the PeopleSoft system. The receiver security handler decrypts the SOAP header, validates the digital signature, verifies the WS-Security token, and generates a PS_TOKEN cookie, the PeopleSoft authentication token.
Image: PeopleSoft Portal as WSRP consumer and producer
This diagram shows the PeopleSoft portal as both WSRP consumer and WSRP producer:
The WS-Security support provided by PeopleSoft applications includes:
Username Token Profile.
Security Assertion Markup Language (SAML) Token Profile.
Note: PeopleSoft applications support SAML 1.1.
UsernameToken Security
With Username Token support, a consumer can supply a UsernameToken as a means of identifying the requestor by user name, and optionally using a password to authenticate that identity to the web service provider.
This is an XML example of a user name token with password:
Note: The password is in clear text.
<soapenv:Header>
<wsse:Security soapenv:mustUnderstand="1" xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<wsse:UsernameToken>
<wsse:Username>QEDMO</wsse:Username>
<wsse:Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordText">QEDMO</wsse:Password>
</wsse:UsernameToken>
</wsse:Security>
</soapenv:Header>This is an XML example of a UserName Token with digital signature:
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/">
<soapenv:Header>
<wsse:Security soapenv:mustUnderstand="1" xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd"><ds:Signature xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:SignedInfo>
<ds:CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/>
<ds:SignatureMethod Algorithm="http://www.w3.org/2001/04/xmldsig-more#rsa-sha256"/>
<ds:Reference URI="#id-18871350">
<ds:Transforms>
<ds:Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/>
</ds:Transforms>
<ds:DigestMethod Algorithm="http://www.w3.org/2001/04/xmlenc#sha256"/>
<ds:DigestValue>Do+wViC4mSHBWYmRMWKaRDF8xmU=</ds:DigestValue>
</ds:Reference>
<ds:Reference URI="#id-11549664">
<ds:Transforms>
<ds:Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/>
</ds:Transforms>
<ds:DigestMethod Algorithm="http://www.w3.org/2001/04/xmlenc#sha256"/>
<ds:DigestValue>4NVgNpjX16B4+Wrmw+7bnGfeJSs=</ds:DigestValue>
</ds:Reference>
</ds:SignedInfo>
<ds:SignatureValue>
QFXQuStu8sLAvsDIgNaZHuVWBIes9GpgY6fGb9KLP209hzNi+cPp3NahsF1mVxcXzCjrui2Vc3vq
wLtYA9kaFsM7EMY8TdJC9cmiepr07pR2iXXMmDYYp01dOQkz+3SeBg9F2qPOBAg/jTrWgppys2rS
ES9pV6OIKRk0try8BcU=
</ds:SignatureValue>
<ds:KeyInfo Id="KeyId-1049443">
<wsse:SecurityTokenReference wsu:Id="STRId-14721926" xmlns:wsu="http://docs.
oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">
<ds:X509Data><ds:X509IssuerSerial>
<ds:X509IssuerName>CN=PeopleTools TEST root CA,DC=peoplesoft,DC=com,OU=
PeopleToolsDevelopment,O=PeopleSoft Inc,L=Pleasanton,ST=CA,C=US</ds:X509IssuerName>
<ds:X509SerialNumber>566474176348341487536757</ds:X509SerialNumber>
</ds:X509IssuerSerial>
</ds:X509Data></wsse:SecurityTokenReference>
</ds:KeyInfo>
</ds:Signature>
<wsse:UsernameToken wsu:Id="id-11549664" xmlns:wsu="http://docs.oasis-open.
org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd"><wsse:Username>
QEDMO</wsse:Username><wsse:Password Type="http://docs.oasis-open.org/wss/2004
/01/oasis-200401-wss-username-token-profile-1.0#PasswordText">QEDMO</wsse:
Password></wsse:UsernameToken></wsse:Security></soapenv:Header>
<soapenv:Body wsu:Id="id-18871350" xmlns:wsu="http://docs.oasis-open.org/wss
/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd"><ns1:testMethod xmlns:
ns1="http://axis/service/security/test9/LogTestService9"/></soapenv:Body>
</soapenv:Envelope>SAML Token Security
A SAML token makes statements about a principal. All SAML tokens include the following common information:
Issuer ID
Issuance timestamp
NotBefore or NotOnOfAfter conditions
Subject
Name
Subject confirmation
Conditions under which the assertion is valid
This is an XML example of an SAML token:
<Assertion AssertionID="d9aeaa4c1126df5ee0c6df64fdf961b1" IssueInstant=
"2008-05-14T18:18:47.246Z" Issuer=".example.com" MajorVersion="1"
MinorVersion="1"xmlns="urn:oasis:names:tc:SAML:1.0:assertion" xmlns:saml=
"urn:oasis:names:tc:SAML:1.0:assertion" xmlns:samlp="urn:oasis:names:tc:
SAML:1.0:protocol">
<Conditions NotBefore="2008-05-14T18:18:47.184Z" NotOnOrAfter="2008-05-
14T18:28:47.184Z"/>
<AuthenticationStatement AuthenticationInstant="2008-05-14T18:18:47.
215Z"AuthenticationMethod="urn:oasis:names:tc:SAML:1.0:am:password">
<Subject>
<NameIdentifier NameQualifier=".example.com">QEDMO</NameIdentifier>
<SubjectConfirmation>
<ConfirmationMethod>urn:oasis:names:tc:SAML:1.0:cm:sender-
vouches</ConfirmationMethod>
</SubjectConfirmation>
</Subject>
</AuthenticationStatement>
</Assertion>
This is an XML example of an SAML token with digital signature
- <soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/">
- <soapenv:Header>
- <wsse:Security soapenv:mustUnderstand="1" xmlns:wsse="http://docs.oasis-open.
org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
- <Assertion AssertionID="ede14876b3389b653824f0456e07676d" IssueInstant="
2008-05-13T22:54:17.417Z" Issuer=".example.com" MajorVersion="1" MinorVersion
="1"xmlns="urn:oasis:names:tc:SAML:1.0:assertion" xmlns:saml="urn:oasis:names:tc:
SAML:1.0:assertion" xmlns:samlp="urn:oasis:names:tc:SAML:1.0:protocol">
<Conditions NotBefore="2008-05-13T22:54:17.386Z" NotOnOrAfter="2008-05-
13T23:04:17.386Z" />
- <AuthenticationStatement AuthenticationInstant="2008-05-13T22:54:17.
401Z" AuthenticationMethod="urn:oasis:names:tc:SAML:1.0:am:password">
- <Subject>
<NameIdentifier NameQualifier=".example.com">QEDMO</NameIdentifier>
- <SubjectConfirmation>
<ConfirmationMethod>urn:oasis:names:tc:SAML:1.0:cm:sender-vouches</
ConfirmationMethod>
</SubjectConfirmation>
</Subject>
</AuthenticationStatement>
</Assertion>
- <wsse:SecurityTokenReference wsu:Id="STRSAMLId-11733267" xmlns:wsu="
http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-
utility-1.0.xsd">
<wsse:Reference URI="#ede14876b3389b653824f0456e07676d" ValueType="http:
//docs.oasis-open.org/wss/2004/XX/oasis-2004XX-wss-saml-token-profile-
1.0#SAMLAssertion-1.1" />
</wsse:SecurityTokenReference>
<wsse:BinarySecurityToken EncodingType="http://docs.oasis-open.org/wss/
2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary"
ValueType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-x509-token-profile-1.0#X509v3"
wsu:Id="CertId-28365241" xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">MIIElzCCBACgAwIBAgIKQrSKyQAAAAAL+DANBgkqhkiG9w0BAQUFADCBvjELMAkGA1UEBhMCVVMxCzAJBgNVBAgTAkNBMRMwEQYDVQQHEwpQbGVhc2FudG9uMRcwFQYDVQQKEw5QZW9wbGVTb2Z0IEluYzEgMB4GA1UECxMXUGVvcGxlVG9vbHMgRGV2ZWxvcG1lbnQxEzARBgoJkiaJk/IsZAEZFgNjb20xGjAYBgoJkiaJk/IsZAEZFgpwZW9wbGVzb2Z0MSEwHwYDVQQDExhQZW9wbGVUb29scyBURVNUIHJvb3QgQ0EwHhcNMDcwODE2MTc1MDIzWhcNMDgwODE2MTgwMDIzWjBxMQswCQYDVQQGEwJVUzETMBEGA1UECBMKQ2FsaWZvcm5pYTETMBEGA1UEBxMKUGxlYXNhbnRvbjEPMA0GA1UEChMGT3JhY2xlMRQwEgYDVQQLEwtQZW9wbGVUb29sczERMA8GA1UEAwwIcWVfaWJ0Z3QwgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGBAMrvvgIBLkotkSm+tnbxjyNQlTi3h3p8h44WhIJ1Ikdvhgtwk890doxdF1HkDaX0Zz7/9IcW4wc5l3z/C/r0kchcq95ToRxKZ5UC50Sx2wbT9/GL6GVUP/EBtGqcaZSeE4G9OHiVmeXxe7opb3InyyAxU/dbuLj/bMpOvABgbmdhAgMBAAGjggHmMIIB4jAdBgNVHQ4EFgQUZ1KpPrdYQY+mEdNk/YWKe4Iqn+wwHwYDVR0jBBgwFoAU/jeXdgwdjCBwIIOg3c+t5n06BswwgawGA1UdHwSBpDCBoTCBnqCBm6CBmIZMaHR0cDovL3B0bnRhczEyLnBlb3BsZXNvZnQuY29tL0NlcnRFbnJvbGwvUGVvcGxlVG9vbHMlMjBURVNUJTIwcm9vdCUyMENBLmNybIZIZmlsZTovL1xccHRudGFzMTIucGVvcGxlc29mdC5jb21cQ2VydEVucm9sbFxQZW9wbGVUb29scyBURVNUIHJvb3QgQ0EuY3JsMIHwBggrBgEFBQcBAQSB4zCB4DBwBggrBgEFBQcwAoZkaHR0cDovL3B0bnRhczEyLnBlb3BsZXNvZnQuY29tL0NlcnRFbnJvbGwvcHRudGFzMTIucGVvcGxlc29mdC5jb21fUGVvcGxlVG9vbHMlMjBURVNUJTIwcm9vdCUyMENBLmNydDBsBggrBgEFBQcwAoZgZmlsZTovL1xccHRudGFzMTIucGVvcGxlc29mdC5jb21cQ2VydEVucm9sbFxwdG50YXMxMi5wZW9wbGVzb2Z0LmNvbV9QZW9wbGVUb29scyBURVNUIHJvb3QgQ0EuY3J0MA0GCSqGSIb3DQEBBQUAA4GBABaZwo6xhKZFRbESi3ICewrBTKFjtDbmJvVqBaB0pConBMRGDJ0bQf9Rwo6/Ucm/BoUEEP/dzBkLYM0NEuEqoQvF4ZHRD73qwNV9CCUHU3nlwfnL5K54qrda4V2CoBvgpHEU7EVdt47YV2E8HUAUfyDaXZ0prRMB6I2KtKaaYBNI</wsse:BinarySecurityToken>
- <ds:Signature Id="Signature-22949069" xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
- <ds:SignedInfo>
<ds:CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#" />
<ds:SignatureMethod Algorithm="http://www.w3.org/2001/04/xmldsig-more#rsa-sha256" />
- <ds:Reference URI="#STRSAMLId-11733267">
- <ds:Transforms>
- <ds:Transform Algorithm="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#STR-Transform">
- <wsse:TransformationParameters>
<ds:CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#" />
</wsse:TransformationParameters>
</ds:Transform>
</ds:Transforms>
<ds:DigestMethod Algorithm="http://www.w3.org/2001/04/xmlenc#sha256" />
<ds:DigestValue>TK2a7xf+ldF9MkI1XYut8g5RG+A=</ds:DigestValue>
</ds:Reference>
- <ds:Reference URI="#id-78219">
- <ds:Transforms>
<ds:Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#" />
</ds:Transforms>
<ds:DigestMethod Algorithm="http://www.w3.org/2001/04/xmlenc#sha256" />
<ds:DigestValue>wTVh0pHi6NrTKDWnyXbX/WNCw68=</ds:DigestValue>
</ds:Reference>
</ds:SignedInfo>
<ds:SignatureValue>LGWmXxak++duS8IfY+/4BphfPJW+Ka6a8DxUfYmUGUZ57d1HOmTs0fLR0RoqdIOKJtSD33qRyU6p 7lufZXsRoiJD5iEUJr+El7KgBEmFPFV5hDx2a+dnHN8Zd9A1DRh7qzr1ewKcRpdBDdoS2mJnqjcz mlLOU6aPQqKAjgRtZtg=</ds:SignatureValue>
- <ds:KeyInfo Id="KeyId-15595312">
- <wsse:SecurityTokenReference wsu:Id="STRId-24840600" xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">
<wsse:Reference URI="#CertId-28365241" ValueType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-x509-token-profile-1.0#X509v3" />
</wsse:SecurityTokenReference>
</ds:KeyInfo>
</ds:Signature>
</wsse:Security>
</soapenv:Header>
- <soapenv:Body wsu:Id="id-78219" xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">
<ns1:testMethod xmlns:ns1="http://axis/service/security/test9/LogTestService9" />
</soapenv:Body>
</soapenv:Envelope>Note these points about PeopleSoft SAML assertions:
The PeopleSoft SAML token is concerned with the authentication statement only.
The PeopleSoft SAML token supports SAML with digital signature and encryption. SAML tokens without digital signatures are not supported.
The PeopleSoft SAML profile of WSS: SOAP Message Security requires that systems support sender-voucher methods of subject confirmation.
The SAML Assertion validity or condition by default is set to 10 minutes. However, you can override the default time by adding
org.apache.ws.security.saml.AssertValidMins=15in the wssSAML.properties file, which is located in the \\WEB-INF\classes\wssSAML.properties directory.