21 Troubleshooting VNFM
21.1 Debug VNFM
- VNFM logs are located in " /var/vnfm/logs/vnfm.log "
- VNFM boot logs are located in "/var/log/messages".
- Tomcat logs are located in " /usr/share/vnfm/apache-tomcat-9.0.16/logs/catalina.out ".
- SNMP notifier logs are located in "/var/vnfm/logs/snmp_notifier.log"
- Alert Manager logs are located in "/var/vnfm/logs/alertmanager.log"
- Prometheus server logs are located in "/var/vnfm/logs/prometheus.log"
- Node Exporter logs are located in "/var/vnfm/logs/node_exporter.log"
- RSync logs are location in "/var/log/rsync.log"
- Reboot logs are location in "/var/vnfm/logs/reboot.log"
- Cloud-init logs of the DSR/SDS VNFs are located in "/var/TKLC/log/cloud-init/cloud-init.log"
21.2 Adding Route for a New VIM
root
user mode:
- Open
route-network.sh, and append the new VIM route address to the DataList.For example:
DataList=10.75.167.0/24,10.75.185.0/24 - Execute the
/route-network.sh, and then executeifdown eth1andifup eth1.
21.3 Reboot Tomcat
dsrvnfm user mode:
- Go the
/path.The
./dsrvnfmStartup.pyscript is present. - Execute this
command:
./dsrvnfmStartup.py <option for tomcat to start,stop,restart> <ipAddress of vnfm, Don't use [] incase of IPv6>Examples:
./dsrvnfmStartup.py restart 2606:b400:605:b84a:6e41:6aff:fec7:8100./dsrvnfmStartup.py start 10.75.189.201
21.4 Resolve HA Alarms on VNF through VNFM Deployed Setup
Perform the following to resolve the HA alarms:
- Check the ping request and
response packets from Server-A and Server-B for which alarm has been raised, by
executing:
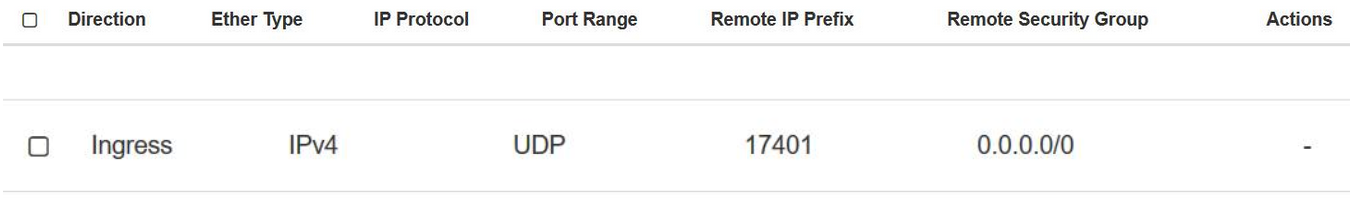
tcpdump -i eth1 -n "host <server-A>-imi or <server-B>-imi and port 17401 and udp"For example:
tcpdump -i eth1 -n "host noam00-17badf67-imi or noam01-17badf67-imi and port 17401 and udp" - If ping request or response packets are not coming
from any server, then add security group rule ingress (response) or egress (request)
to that instance.
The following image shows Ingress response:
Figure 21-1 Ingress Response
- Check the ping packets again
after adding the rule and ensure that
imirequest and response packets are received from each servers, by executing:tcpdump -i eth1 -n "<server-A>-imi or <server-B>-imi and port 17401 and udp" - Now restart the cmha process
on the node where the alarms are present, by executing:
pm.set off cmha && sleep 5 && pm.set on cmhaNote:
If the Node is HA Active, then restarting cmha will cause switch over.
21.5 Adding a Port in Openstack Security Groups
The Security Group Rules define the traffic that is allowed through instances assigned to the security group.
- Open
Security Groups tab on the Openstack Horizon.
A list of available Security Groups appear.
- From the list, click Manage Rules for the required Security Group.
-
Select Add Rule, provide all the required details in the dialog box.
Note:
In the CIDR field, the values for zero address are:- For IPv4 - 0.0.0.0/0
- For IPv6 - ::/0
- Click Add Rule.
21.6 Debug SNMP System Alerts
- Check the log files for any errors. For information about list of log files, see How to debug VNFM.
- If default configurations needs to be changed, perform SNMP System Traps Configurations.
21.7 Configure Flavor and Instantiation Levels in VNFM
Steps to configure Flavor and Instantiation Levels in VNFM:
The number of VMs to be allocated to each VNF Flavor and Instantiation Levels are present
in the file: /usr/share/vnfm/openstack/VnfSizing.yaml
A sample of the file is provided below:
dsrSignaling:
small:
diameter:
damp: 2
ipfe: 2
stp: 0
sbr: 0
udr: 0
large:
diameter:
damp: 32
ipfe: 4
stp: 0
sbr: 0
udr: 0- In
'dsrvnfm'user mode, edit this file:/usr/share/vnfm/openstack/VnfSizing.yaml - Change the number of VMs under the required VNF Type → Instantiation Level Id → Flavor Id and save the file.
For example: In DSR Signaling, under Diameter Flavor Id, small Instantiation Level Id, the user needs 16 DAMPs, 4 IPFEs, the sample of file would be as below:
Edited Sample File
dsrSignaling:
small:
diameter:
damp: 16
ipfe: 4
stp: 0
sbr: 0
udr: 0
large:
diameter:
damp: 32
ipfe: 4
stp: 0
sbr: 0
udr: 021.9 Disable SSH Weak Key Exchange Algorithms
sudo sshd -T |grep -i "^kexalgorithms"kexalgorithms curve25519-sha256,curve25519-sha256@ libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512,diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha256,diffie-hellman-group14-sha1,diffie-hellman-group1-sha1diffie-hellman-group-exchange-sha1- weak key algorithmdiffie-hellman-group1-sha1- weak key algorithm
/etc/ssh/sshd_config and
/etc/ssh/ssh_config files and on all the
servers:KexAlgorithms diffie-hellman-group-exchange-sha256,ecdh-sha2-nistp384Note:
Thediffie-hellman-group-exchange-sha256 and
ecdh-sha2-nistp384 are added as they are not reported as
Weak key algorithms. This result is overridden if ssh_config
and sshd_config contains KexAlgorithms
diffie-hellman-group-exchange-sha256,ecdh-sha2-nistp384 line.
ssh_config and
sshd_config update, run the following
command:sudo sshd -T |grep -i "^kexalgorithms"diffie-hellman-group-exchange-sha256,ecdh-sha2-nistp384sudo sshd -T | grep -i "gssapiauthentication"
sudo sshd -T | grep -i "gssapikeyexchange"/etc/ssh/sshd_config and
/etc/ssh/ssh_config files, on all the
servers.sudo sed -i 's/.*GSSAPIAuthentication.*/#GSSAPIAuthentication no/i' /etc/ssh/sshd_config && sudo sed -i '/.*GSSAPIAuthentication.*/{x;/.*GSSAPIAuthentication.*/! {x;h;b;};x;d}' /etc/ssh/sshd_configsudo sed -i 's/.*GSSAPIAuthentication.*/# GSSAPIAuthentication no/i' /etc/ssh/ssh_config && sudo sed -i '/.*GSSAPIAuthentication.*/{x;/.*GSSAPIAuthentication.*/! {x;h;b;};x;d}' /etc/ssh/ssh_configNote:
If there is a line with the GSSAPIKexAlgorithms or gssapikexalgorithms parameter (case-insensitive), remove that line.sudo sshd -T | grep -i "gssapiauthentication"sudo sshd -T | grep -i "gssapikeyexchange"/etc/ssh/sshd_config and
/etc/ssh/ssh_config files, validate the
/etc/ssh/sshd_config file for
errors.sudo sshd -Tsshd
service.sudo service sshd restart21.10 Add or Update Certification
Note:
It is recommended to get a SSL certificate certified from a trusted authority, as Nessus scan results inSSL Certificate Cannot Be Trusted, SSL Self-Signed
Certificate issues.
- Run step 1 and 2 from VNFM Self Signed Certificate Generation procedure to produce
dsrVnfm.keyanddsrVnfm.csrfiles.Note:
For information on self signed certificate, refer to VNFM Self Signed Certificate Generation section. - Send these 2 files to a trusted CA authority for CA signature.
- Perform step 4 from VNFM Self Signed Certificate Generation procedure using the
dsrVnfm.crtfile shared back by the trusted CA authority.Note:
Run the remaining steps in the VNFM Self Signed Certificate Generation section to generate thevnfm_default.jksfile. - After creating
vnfm_default.jkscertificate, before copying it into/var/vnfm/certificate/, move the created certificate to backup, if it exists in/var/vnfm/certificate/path.
21.11 Changing VNF CLI and DSR GUI Log in Credentials
This section provides information to change VNF CLI and DSR GUI log in username and password.
Prerequisites
- The new credentials are supported by the DSR Image.
- The updated username must be a plain text.
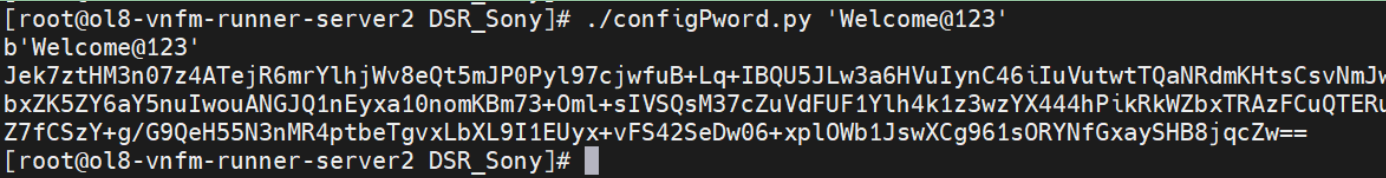
- The updated password must be encrypted using the utility function which
is
/configPword.py'passwordToBeEncrypted'.Following is an example showing the usage of the script:
Figure 21-2 Usage of Script
- The encrypted password must be updated in
VnfmPropeties.yamlfile.
Procedure
In the 'dsrvnfm' user mode:
- Open VnfmProperties file -
/opt/vnfm/config/VnfmProperties.yamlto edit the properties. - To change VNF CLI log in username and password, update
admUsrUsernameandadmUsrPwordfields. - To change the DSR GUI username and password, update
dsrNoamUsernameanddsrNoamPwordfields.