2 Diameter Singling Router Security Overview
This section explains the security objectives and provides a generic overview of the DSR deployment model.
DSR Security Objectives
Oracle Communications Diameter Signaling Router (DSR) is developed with
security in mind and delivered with a standard configuration that
includes the best practices of Linux operating system security
hardening. These practices include the following security
objectives:
- Attack Surface Reduction
- Attack Surface Hardening
- Vulnerability Mitigation
Generic DSR Deployment Model
DSR is deployed in carrier’s and service provider’s core networks and
provides critical signaling routing functionality for 4G, LTE, and
IMS networks. The DSR solution is based on Linux servers and is
highly scalable to accommodate a wide range of capacities to address
networks of various sizes. The following image shows the generic
deployment strategy model for DSR.
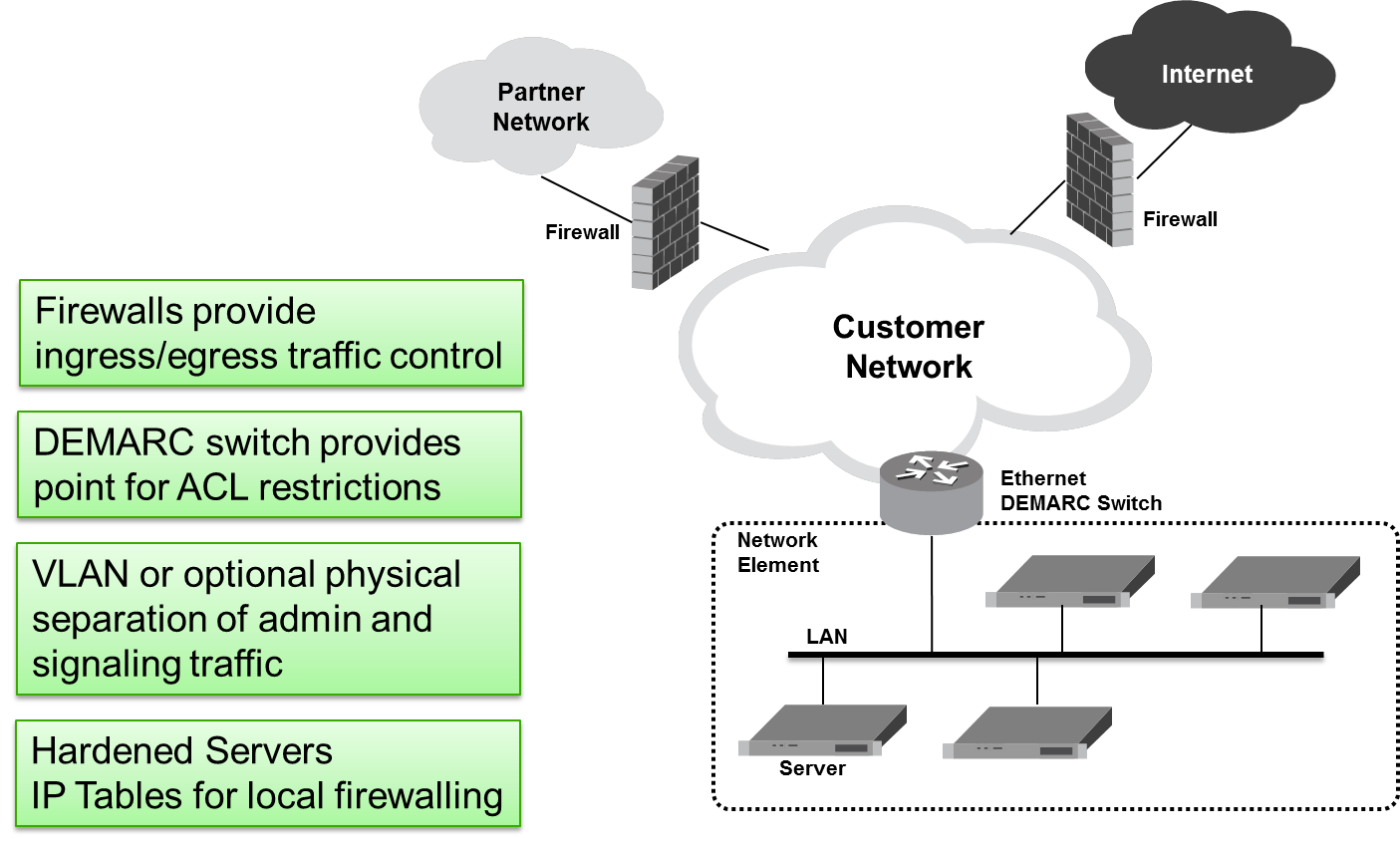
Figure 2-1 Generic DSR Deployment Strategy Model

A DSR node consists of a suite of servers and related
Ethernet switches that create a cluster of servers, operating as a
single Network Element. It is assumed that the service provider
establishes firewalls to isolate the core network elements from the
internet and partner networks, as shown in Figure 2-1. In addition to these firewalls, DSR provides additional security
capabilities such as:
- Access Control Lists (ACL) functionality at the demarcation switch.
- VLAN or optional physical separation of administrative and signaling traffic.
- IP Tables functionality at the servers for local firewalling.
2.1 Basic Security Considerations
The following principles are fundamental to using any application securely:
- Keep software up to date. Consider upgrading to the latest maintenance release. Consult with Oracle support team to plan for Oracle Communications Diameter Signaling Router software upgrades.
- Limit privileges. Users must be assigned to the proper user group and reviewed periodically to determine relevance to current work requirements. For more information, see the User Administration section.
- Monitor system activity. Establish who must access which system components, how often, and monitor those components. For more information, see Host Intrusion Detection System (HIDS) and Security Logs and Alarms sections.
- Configure software securely. For example, use secure protocols such as TLS and strong passwords. For more information, see the GUI Passwords and Oracle Communications Diameter Signaling Router OS Standard Features sections.
- Change default passwords. The initial installation of the DSR system software uses default passwords. These passwords must be changed during installation. For more information, see Change Passwords for all DSR Administrative Accounts and Changing the Internal Web Service Passwords.
- Obtain and install X.509 web certificates for GUI and MMI access. The DSR system ships with a self-signed certificate that must be replaced before the system is put into operation. For more information, see the Certificate Management section.
- Learn and use the Oracle Communications Diameter Signaling Router security features. For more information, see Implement Oracle Communications Diameter Signaling Router Security and Optional IPsec Configuration sections.
- Keep up to date on security information. Oracle regularly issues security alerts for important vulnerability fixes. It is advisable to install the applicable security patches as soon as possible. For more details, see the security alerts page at http://www.oracle.com/technetwork/topics/security/alerts-086861.html#SecurityAlerts.
2.2 Accessing Diameter Signaling Router System
There are several ways to access the Oracle Communications Diameter Signaling Router
(DSR) system. They are as follows:
- Web browser GUI – The client access to the DSR GUI for remote
administration requires a web browser that supports a TLS 1.1 or TLS 1.2 enabled
session. This application is designed to work with most modern HTML5 compliant
browsers and uses JavaScript and cookies. When you access the DSR system through
the GUI interface, the Log In screen displays. Type the
Username and Password
credentials, and click Log In to access the GUI.
Figure 2-2 Diameter Signaling Router Login Page
 When successfully logged in, the Oracle Communications Diameter Signaling Router home page displays. To logout, click the upper-right corner link labelled Logout or select the bottom menu item.
When successfully logged in, the Oracle Communications Diameter Signaling Router home page displays. To logout, click the upper-right corner link labelled Logout or select the bottom menu item.Figure 2-3 Diameter Signaling Router Home Page

- CLI via SSH client – Normal login access is remote through network connections. The client access to the command-line interface (CLI) is with an SSH-capable client such as PUTTY, SecureCRT, or a similar client using the default administrative login account. SSH login is supported on the distinct management interface. To log out, enter the command, log out, and press Enter.
-
Local access can be supported by connecting a monitor and a keyboard.
Local access supports CLI only. When successfully logged in, a command-line
prompt containing
userid@hostname followed by a$prompt displays. There is no requirement to add additional users, but adding users is supported.Note:
Adding additional users is not supported on all hardware. - iLO/ILOM Web GUI access – Proliant Server iLO or Oracle ILOM provides web
GUI access from a web browser using the URL,
https://<iLO/ILOM IP Address>/. Using a supported web browser, log in to iLO/ILOM as an admin user by providing a username and password.