Enabling Query Data Masking
PeopleSoft provides the ability to protect data in PS Query and ensure that only authorized users have access to PII/sensitive data used in the query.
Note: Query masking is applicable to all the PII/Sensitive fields configured in Data Masking.
This topic provides an understanding of query masking, the pages used to enable query masking, and Query Masking Examples.
Note: Query Masking requires PeopleTools 8.58.02.
|
Page Name |
Definition Name |
Usage |
|---|---|---|
|
EODP_RRF_MNT_FL |
Identify PeopleSoft Roles and define access to PII and/or sensitive fields. |
|
|
EODP_QRYMSK_RUN_FL |
Synchronize data privacy mappings defined in Data Privacy Framework with the Query system and authorized roles and their access to PII and/or sensitive fields. |
|
|
EODP_QMSK_EXCLU_FL |
Identify fields to be excluded from the Data Sync process. |
|
|
EODP_QRYSWITCH_FL |
Enable/disable the Query Masking feature. |
|
|
EODP_QRMSK_UTILITY |
Generate a list of users who can access PII/sensitive data. |
Query Masking is a configurable feature that can mask PII and /or Sensitive field used in PS Queries. Only authorized users have access to view or run a PS Query that uses PII/sensitive data.
When a query is run, the system checks:
If the Query Masking feature is enabled in the system.
If the fields used in the query are identified as Personally Identifiable Information (PII) or Sensitive in the Data Privacy Framework.
If the current user is authorized to view the PII and Sensitive fields.
Note: Data Privacy Framework maintains all the PII and/or sensitive fields in the product and the roles that have access to these fields. You can mark a field as PII/sensitive using Maintain Data Privacy Settings Page and define the roles that have access to specific fields using Authorized Roles Page. For more information, see Understanding Data Privacy.
You can enable the query masking feature using System Settings Page. If the Query Masking feature is not enabled, then there is no change in the PS Query behavior.
This does not impact or change the Query Security requirements for a user to access a PS Query.
In a query, a PII and/or sensitive field can be part of the query SELECT, WHERE or ORDER BY clause. For an unauthorized user:
If a PII and/or sensitive field is in the SELECT statement of the PS Query, then the PII/sensitive column output is masked.
If a PII and/or sensitive field is in the WHERE or ORDER BY clause, then PS Query stops the query process and does NOT return any output.
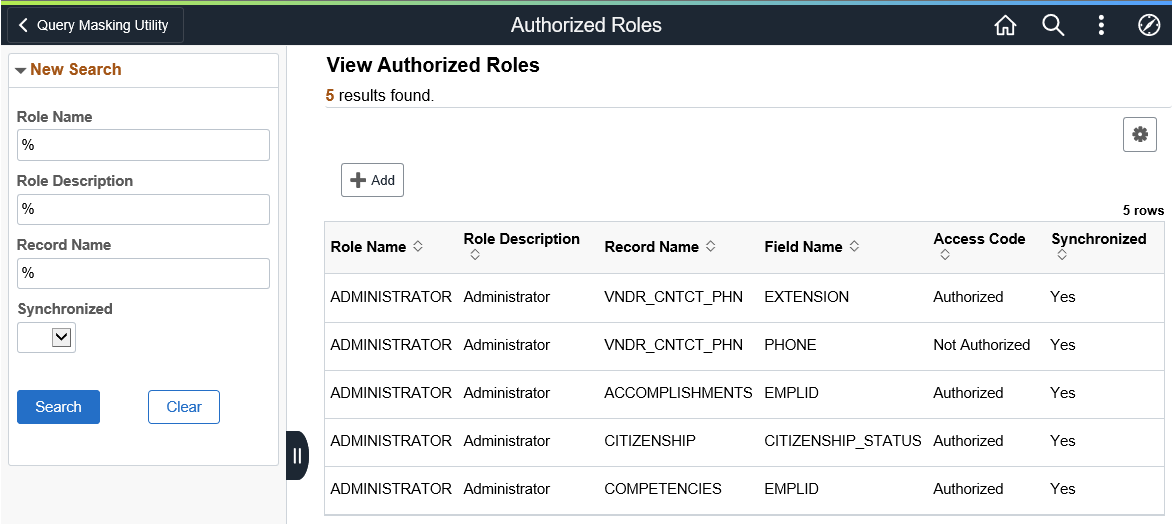
Use the Authorized Roles page (EODP_RRF_MNT_FL) to identify PeopleSoft Roles and define access to PII and/or sensitive fields.
Navigation:
This example illustrates the fields and controls on the Authorized Roles page.
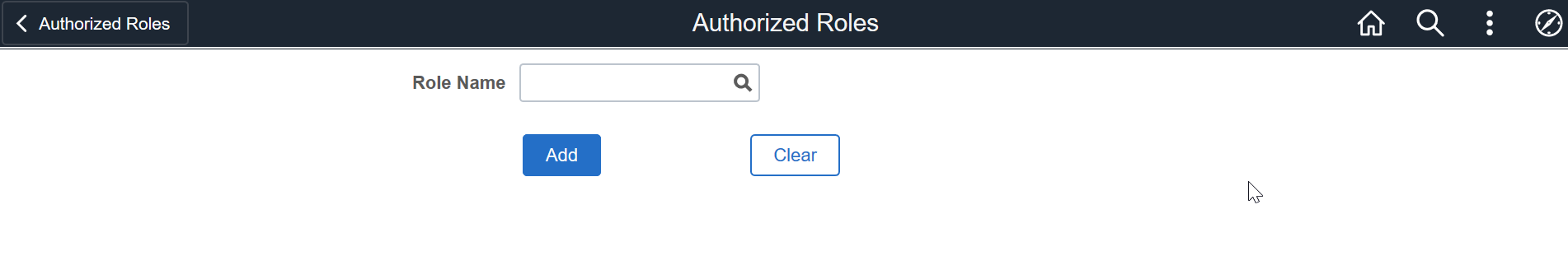
To add a role, click the Add button.
This example illustrates the Authorized Roles page when you click the Add button.
Field or Control |
Description |
|---|---|
Role Name |
Select the role to be authorized. |
To enter further details, select the role and click Add.
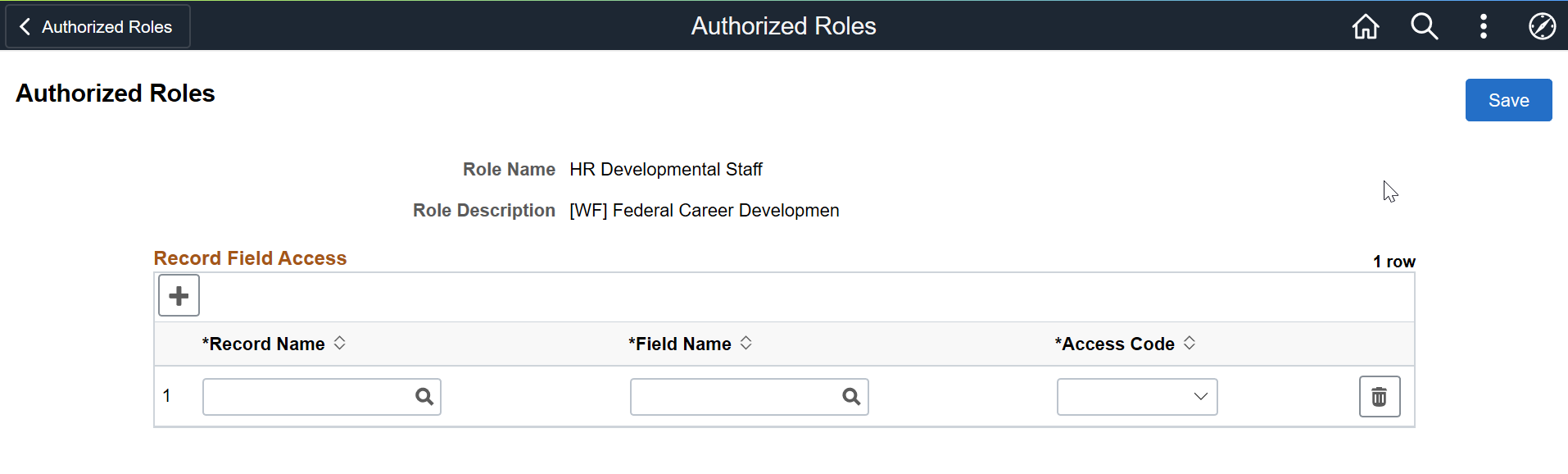
This example illustrates the Authorized Roles page (EODP_RRF_MNT_FL) to enter more details in a HCM database.
Field or Control |
Description |
|---|---|
Record Name |
Select the record name of the field that displays PII/sensitive information. |
Field Name |
Select the field name that displays PII/sensitive information. |
Access Code |
Select to indicate that the role has access to this field. Options include:
|
Note: If a PII and/or sensitive field is not defined for any PeopleSoft role, then no users has access to view the information in PS Query.
For more information, about PS Query behavior, see Query Masking Examples .
Use the Synchronize Data page (EODP_QRYMSK_RUN_FL) to synchronize data privacy mappings in Data Privacy Framework with the Query system and authorized roles and their access to PII and/or sensitive fields.
Navigation:
This example illustrates the Synchronize Data page.
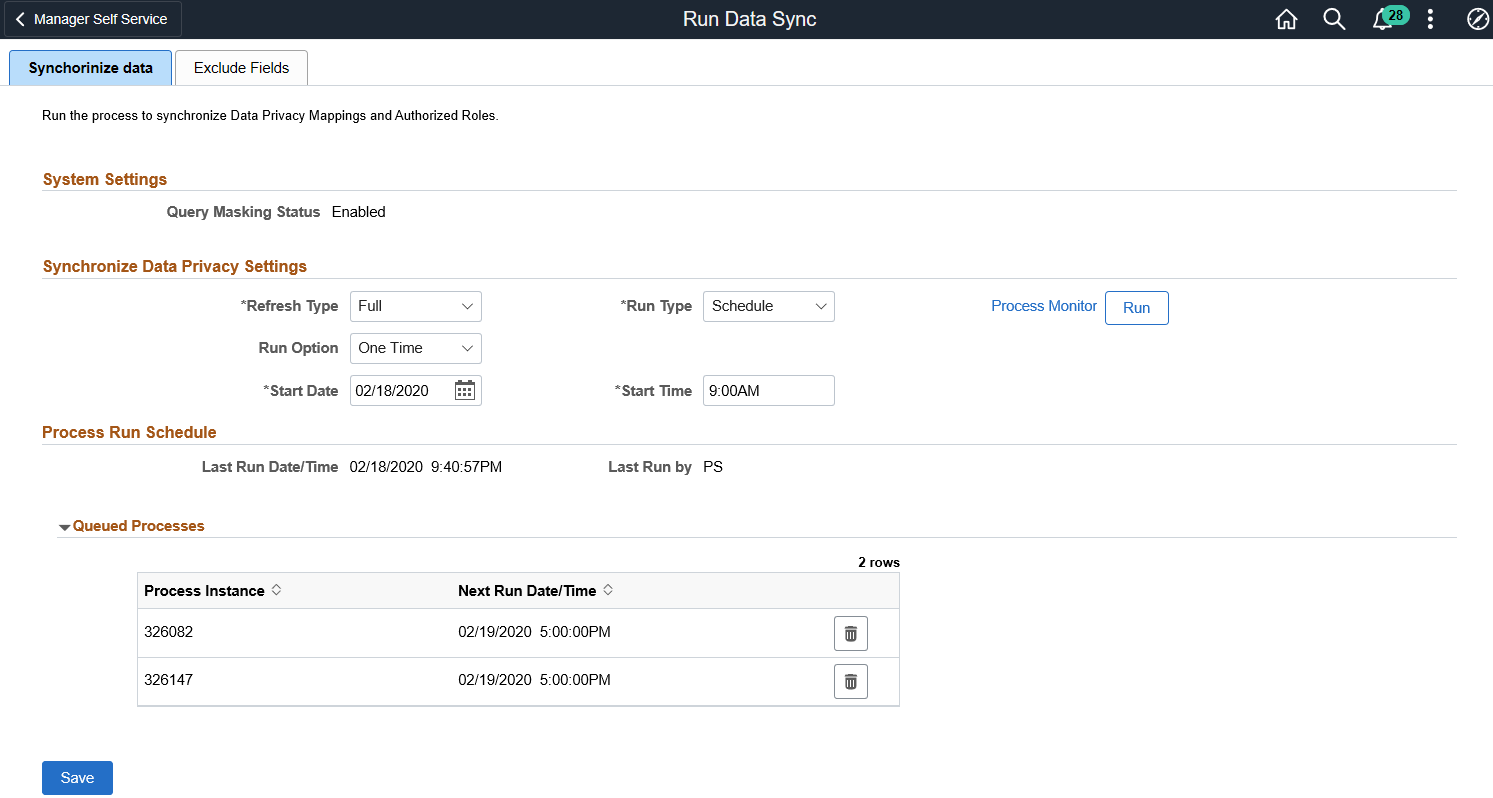
System Setting
Field or Control |
Description |
|---|---|
Query Masking Status |
Displays the query masking system status. For more information about enabling or disabling the query masking functionality, see System Settings Page. |
Synchronize Data Privacy Settings
Field or Control |
Description |
|---|---|
Refresh Type |
Select to determine the synchronization method. Options are:
|
Run Type |
Select to set the process run schedule. Options include:
|
Run Option |
Select an option:
Note: This field is available only if you select Schedule as the Run Type. |
Process Recurrence ID |
Select a Recurrence ID. Note: This field is only available if you select Recurrences as the Run Option. Recurrence ID’s are defined in the Process Scheduler. |
Start Date and Start Time |
Specify the start date and time for the sync process. Note: These fields are only available if you select One Time as the Run Option. |
Queued Processes
This section lists the process runs that are scheduled with the date and time. A request can be cancelled.
Note: PeopleSoft recommends that you schedule this sync process during low system usage hours. This is because the process updates internal tables and may sometimes result in data sync problems due to online transactions.
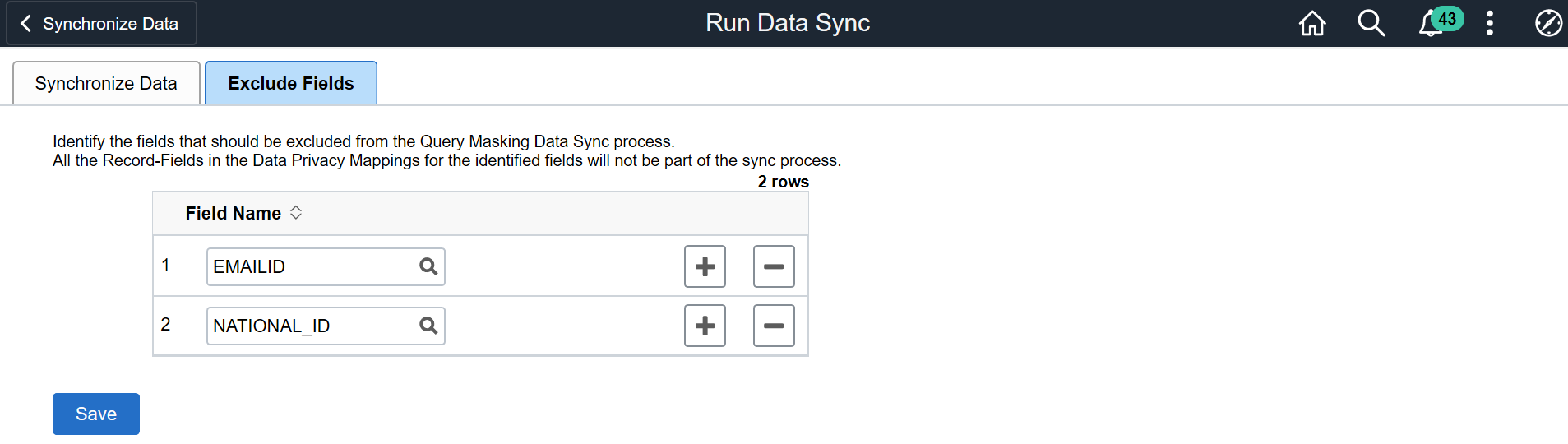
Use the Exclude Fields page (EODP_QMSK_EXCLU_FL) to identify the fields to be excluded from the Data Sync process.
Note: All record fields in the Data Privacy Mappings for the identified fields are not part of the sync process.
Navigation:
This example illustrates the Exclude Fields page.
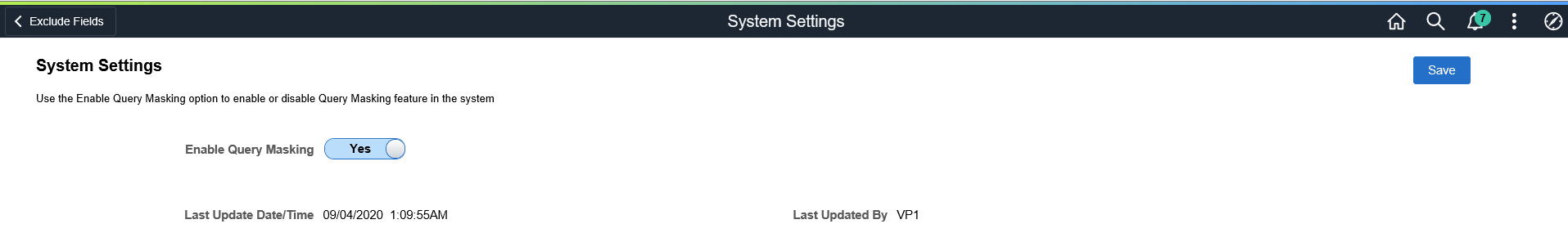
Use the System Settings page (EODP_QRYSWITCH_FL) to enable or disable the Query Masking feature.
Navigation:
This example illustrates the fields and controls on the System Settings page.
Field or Control |
Description |
|---|---|
Enable Query Masking |
Select Yes or No to enable or disable Query Masking feature for the system. |
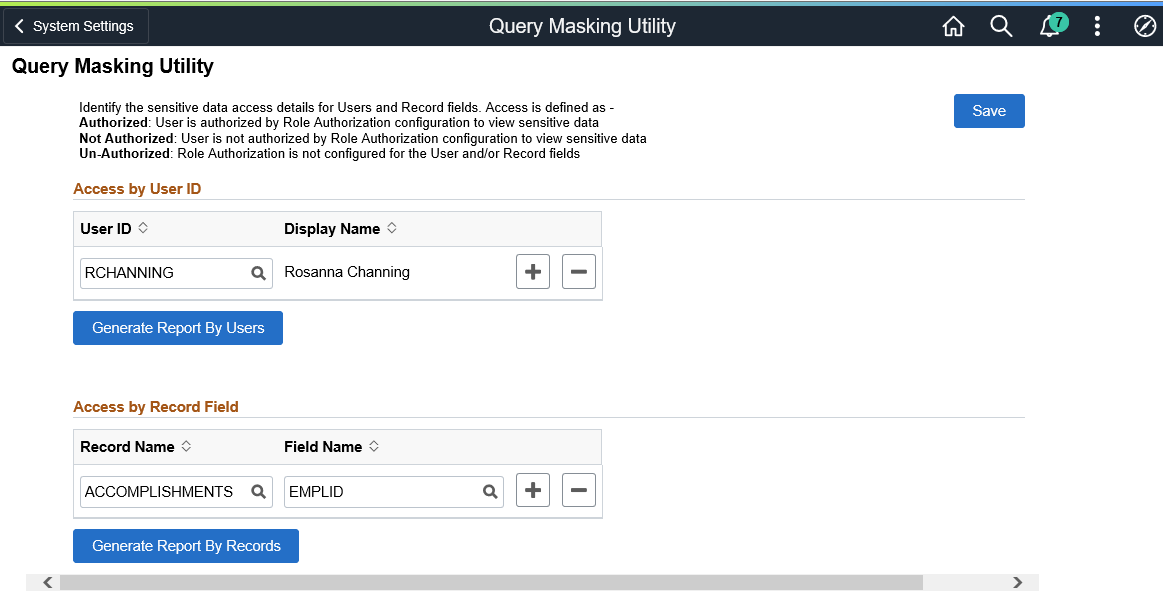
Use the Query Masking Utility page (EODP_QRMSK_UTILITY) generate a list of users who have access to PII/sensitive data.
Navigation:
This example illustrates the fields and controls on the Query Masking Utility page.
Field or Control |
Description |
|---|---|
Access by User ID - User ID |
Select the User ID(s) to generate the access details report. |
Generate Report By Users |
Select to generate PII/sensitive data access details for the selected user(s). |
Access by Record Field - Record Name |
Select record name of the field that displays PII/sensitive information. |
Generate Report By Records |
Select to generate a list of user and roles that have access to the selected record fields. |
Report by Users
Report by User Access
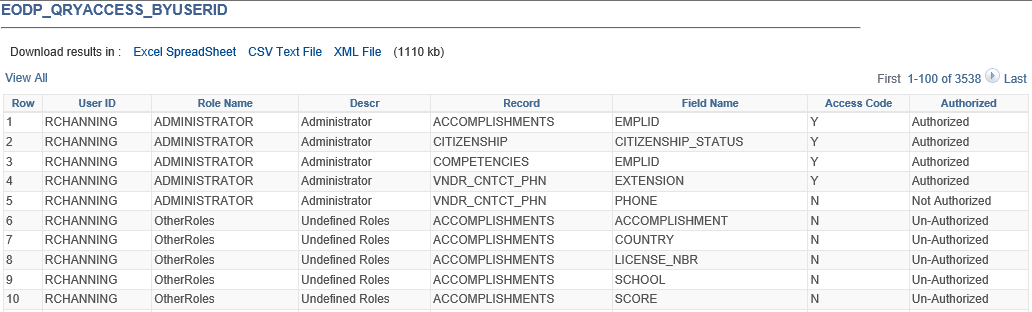
Report by Record
This example illustrates the Report by Record Field.
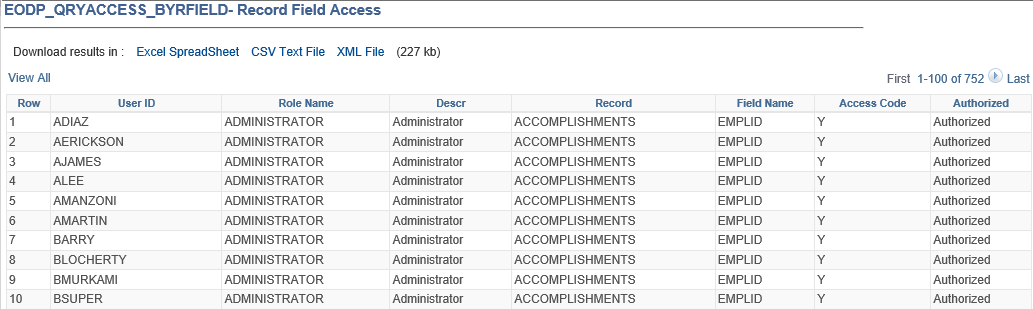
Field or Control |
Description |
|---|---|
Authorized |
This column indicates whether the user has access to the record and field combination. Options include:
|
This section discusses a few examples to describe Query Masking behavior.
Example 1 (FSCM)
Consider three FSCM users: User A, User B, and User C, and the roles assigned to each:
|
User A (VP1) |
User B (SVP1) |
User C (FVP1) |
|---|---|---|
|
Administrator |
Administrator |
Treasurer |
|
Bank Manager |
System Administrator |
Bank Manager |
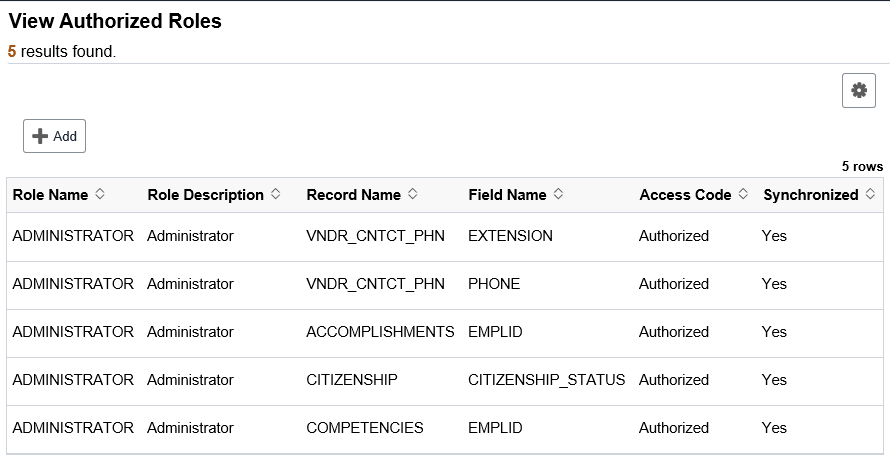
The Role Authorization configuration for Administer is:
This example illustrates the Authorized Roles setup for FSCM example 1.
User A, User B and User C run this query.
This example illustrates a Query SQL.

The PS Query output for User A and B is:
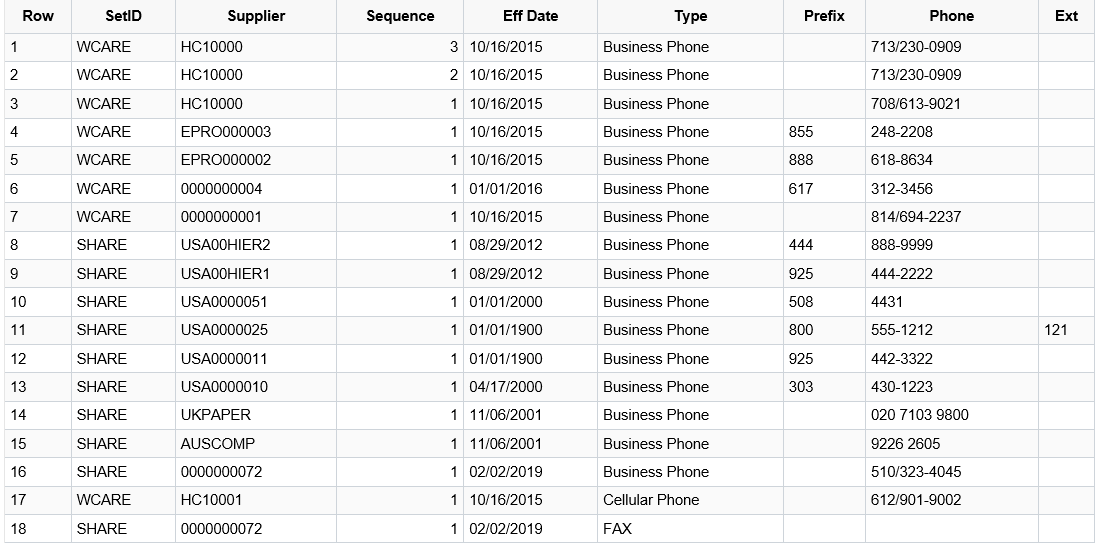
Phone and Ext (extension) are defined as “Authorized” for the Administrator role. Therefore, FSCM User A and B can view those values in the output.
The PS Query output for User C is:
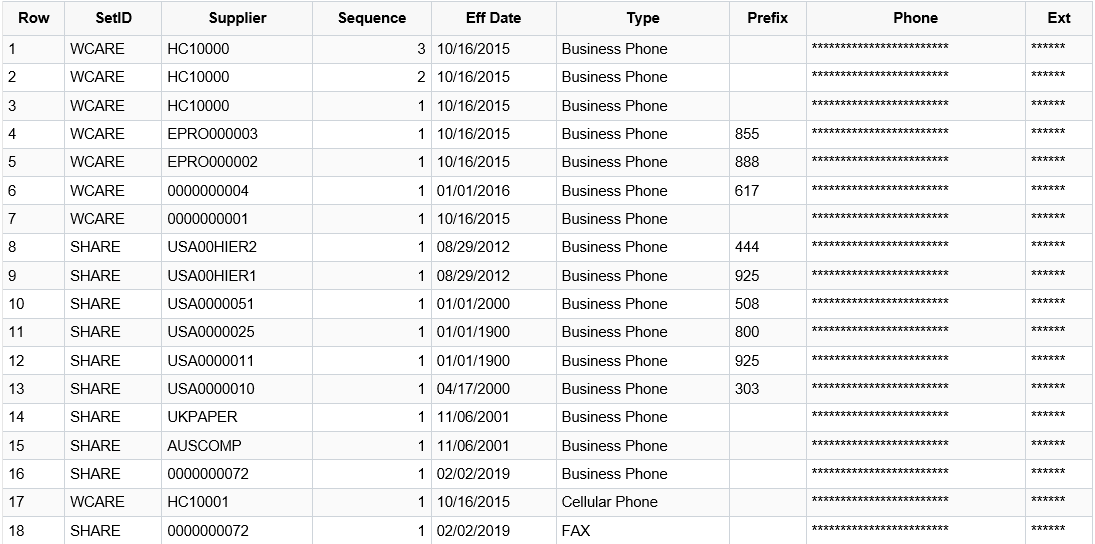
User C does not have the Administrator role, therefore the Phone and Ext (extension) column values are masked.
Note: The Phone and Ext (extension) column values are masked as these fields are not defined as “Authorized” in the role authorization setup for the Treasurer and Bank Manager roles.
Example 2 (HCM)
Consider User A, User B, and User C run this query on a HCM database:
|
User A |
User B |
User C |
|---|---|---|
|
HR Administrator |
HR Administrator |
Payroll Administrator |
|
Payroll Administrator |
Benefits Administrator |
Benefits Administrator |
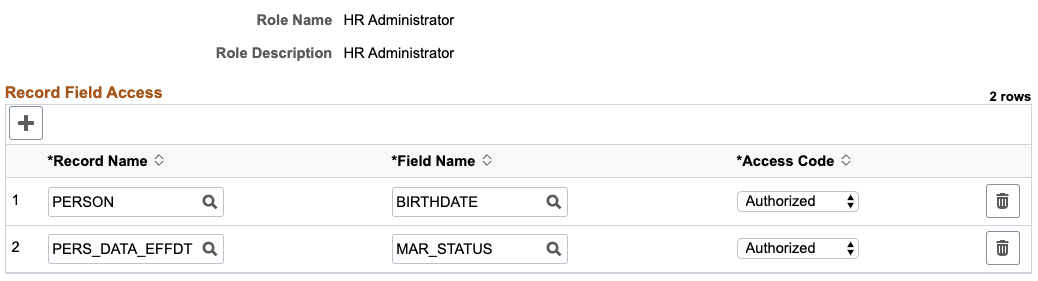
The Authorized Role page is configured:
This example illustrates the Authorized Roles page.
Query

This PS Query uses a PII and/or sensitive field ETHNIC_GRP_CD in the WHERE clause.
User A, User B and User C are not assigned to roles that authorizes access the ETHNIC_GRP_CD field. Unlike the first query, PS Query stops the query and returns an error stating ‘ You have insufficient access to retrieve this data’.
This PS Query behavior protects PII/sensitive information.
Example 3 (HCM)
Consider the same HCM users from the previous example.
In this example, for the HR Administrator role, the Role Authorization configuration is:
Authorized Role configuration for HR Administrator role.
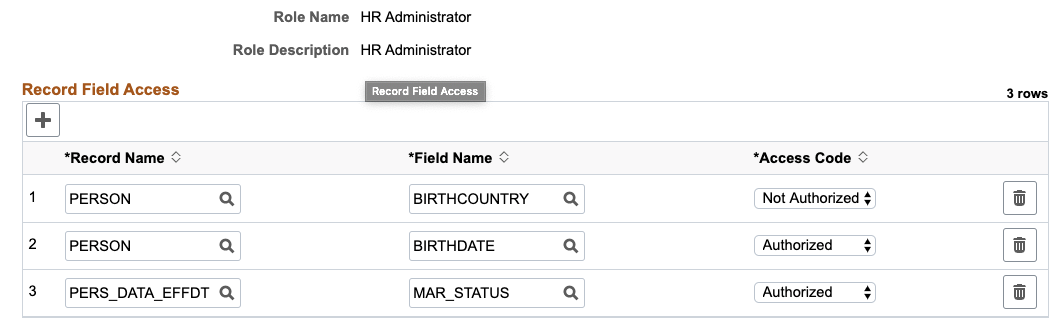
The PERSON.BIRTHCOUNTRY has an access code “Not Authorized”. This specification restricts all users with HR Administrator role from accessing the record field information.
Note: All other users who do not have the HR Administrator role can access the information.
When User A, User B and User C run the query, User A and User B do not have access to PERSON.BIRTHCOUNTRY field.
Query Output for User A and User B

However, User C does not have the HR Administrator role, and can view the Birth Country.
Query Output for User C
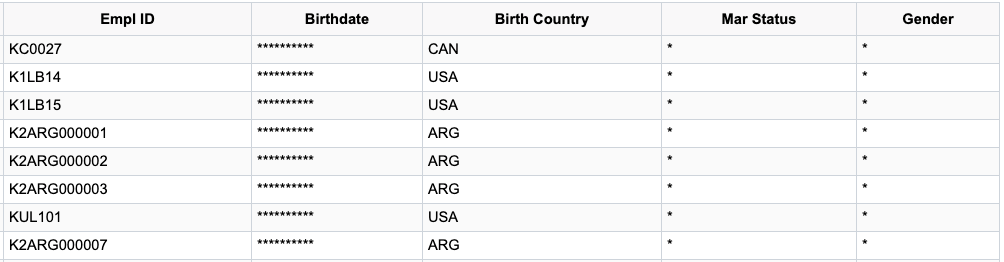
Note: PeopleSoft recommends that all users and their associated roles are reviewed in detail before setting a “Not Authorized” access.
Example 4 (HCM Subrecord Fields Masking)
Consider the same users from the previous HCM examples.
In this example, the Maintain Data Privacy Settings page is configured for HR_I9_PERSON:
Maintain Data Privacy Settings for HR_I9_PERSON
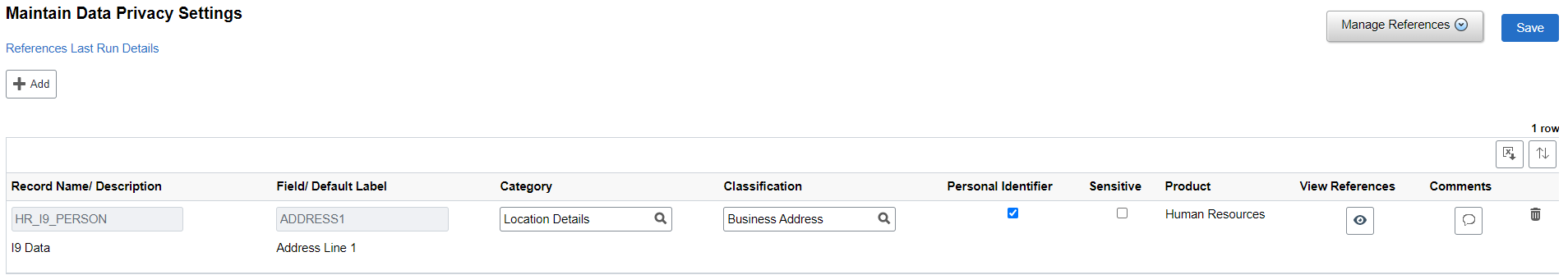
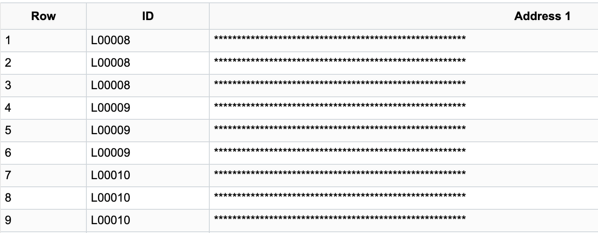
If Role Authorization is not configured, then because the ADDRESS1 field in both the ADDRESSES record and HR_I9_PERSON are from the ADDRESS_SBR sub-record, the ADDRESS1 field from both the records are masked.
This Role Authorization configuration for the HR Administrator role allows Users A and B to see the ADDRESS1 field from the ADDRESSES record:
Role Authorization configuration for the HR Administrator role:
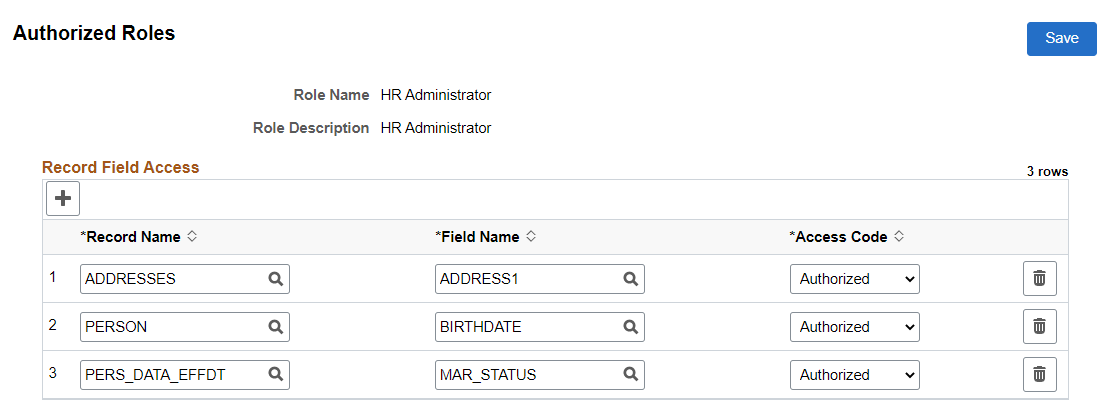
Query:

When User A, User B, and User C run the query, User A and User B have access to the Address1 field.
Example 4 Results User A and User B
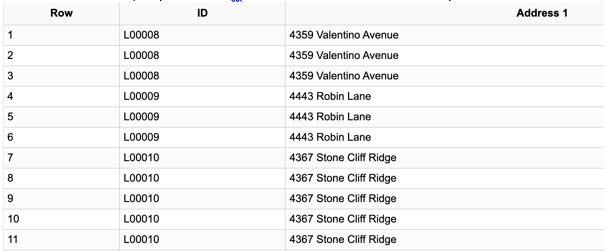
Example 4 Results User C