Setting Up Catalog Security
To set up catalog security, use the eProcurement Catalog Security Option (PV_CAT_FACTORY), the Catalog Types (PV_CAT_SOURCE), and the Catalog Security Type (PV_CAT_SEC_TYPE) components.
This section provides an overview of catalog security and discusses how to define catalog security options, define catalog types, define catalog security types, assign authorized item catalogs to security types, and define catalog security for business units.
|
Page Name |
Definition Name |
Usage |
|---|---|---|
|
PV_INSTALLATION_PV |
Define the catalog search type. To include business-unit level item catalog security, enter Y in the BU Catalog Control field. |
|
|
PV_CAT_FACTORY |
Define catalog security options. These are system wide access policies and GUI formats for the rule-based item catalog method. |
|
|
PV_CAT_SOURCE |
Define catalog types. |
|
|
PV_CAT_SEC_TYPE |
Define catalog security types. These are levels at which you apply catalog security, for example, at the user role level or the individual requester level. |
|
|
Security Type Attributes Page |
PV_CAT_ST_ATTR |
Define security type attributes which include query or prompt tables used. |
|
PV_CAT_SECURITY |
Assign authorized item catalogs to security types. |
|
|
PV_ACTIONS_BU |
Define catalog security for business units. The applicable eProcurement actions enable security for items from the business template, express forms, and direct connect suppliers. |
Catalog security makes it possible for you to control who uses a catalog. These techniques are available for controlling access to catalogs:
Apply item security at business unit and requester levels.
Apply item security using the rule-based catalog method.
Item Security at Business Unit and Requester Levels
You can limit the items available to the Purchasing business unit, the requester, or both. This method only applies if the items are loaded into the Item Master table. In other words, express forms, direct connect suppliers, and company templates (purchasing kits) are not limited or part of the search and browse functionality of the Search Catalog page.
The business unit level catalog security is maintained in the eProcurement Installation Options page and the Assign Catalog to Business Unit page. You enable the business-unit-level security by selecting the BU Catalog Control check box on the eProcurement Installation Options page. When this check box is selected, requesters can only access catalogs specifically assigned to the business unit used to enter the requisition.
Use the Assign Catalog to Business Unit page to define the available item catalogs for each Purchasing business unit. If this page is blank and BU catalog control is selected, then no items are available for requisition entry. The business unit level security applies only to eProcurement requisitions.
This requester level catalog security is maintained in the Requestor Setup page. Select the Use Only Assigned Catalogs check box and then enter the acceptable item catalog ID's in the Catalog Information section at the bottom of the page. When this check box is selected, the requester can only access catalogs specifically assigned to them. The available item catalogs would have to be defined individually for each requester to which security applied. The requester-level security applies to both PeopleSoft eProcurement and Purchasing requisitions.
In addition, if both the requester level and business unit level catalog security are used, only catalogs assigned to both levels can be accessed by the requesters.
Apply Item Security Using the Rule-Based Catalog Method
The rule-based item catalog method provides a framework to implement item catalog authorization. The architecture is flexible enough to allow for different implementations of item catalog security based on different requirements. This enables you to implement an organization-specific access policy, without the need to modify delivered code and objects.
The rule-based item catalog method uses different security levels (security types) to control item catalog access. The non rule-based method enables you to control security by the business unit level and the requester level; however, the rule-based method enables you to control security at any level that you choose. Just like the non rule-based method, the rule-based method restricts the user to the item catalogs that pass all the security restrictions.
In addition, the rule-based catalog method can extend item catalog security control to other item catalog sources such as company templates (purchasing kits), direct connect suppliers, and express forms.
There are two choices for applying the rule-based item catalog method:
Business Unit, User Role, and Requester Level: PeopleSoft delivers a predefined example that you can implement into the organization.
Much of this setup has already been defined for you; making implementation quicker and easier. This predefined method uses item catalog restrictions at the levels of business unit, user role, and individual requester. It also enables item searching and browsing on the Item Master table, express forms, direct connect suppliers, and company templates (purchasing kits). The addition of user role enables you to restrict requesters without defining each requester individually; this saves time and maintenance.
Rule-Based Item Catalog Method Defined for Unique Needs: Using the rule-based item catalog method, you can design an item catalog security using any item sources and any restriction level.
This method requires the most set up, but provides the tailored solution to an organization's specific needs.
To set up a rule-based item catalog method:
Use the eProcurement Catalog Security Option page to define system wide setting to create an eProcurement requisition.
Do not enable the access policy and GUI class types until you have finished the set up.
Use the Catalog Types page to define the item catalog sources, such as, the Item Master table, express forms, direct connect suppliers, and company templates (purchasing kits).
Create catalog security types to identify the levels to apply item restriction, such as, by business unit, user role, or requester.
The setup for the security types of business unit, requester, and user role are supplied by the Security Types Default page.
Use the Catalog Security page to define the authorized item catalogs for each of the security types.
For the security type of BUSINESS_UNIT, you can use either the Catalog Security page or the Assign Catalog to Business Unit page under Maintain Items. For the security type of REQUESTOR_ID, you can use either the Catalog Security page or the Requestor Setup page.
Use the eProcurement Business Unit Actions page to identify the eProcurement actions, such as express forms (EXPRESSFORM_SECURITY), direct connect (DCSUPPLIER_SECURITY), and company templates (TEMPLATE_SECURITY), that should be used for each business unit.
Return to the eProcurement Catalog Security Option page and enable the access policy and GUI class types.
Use the eProcurement Catalog Security Option page (PV_CAT_FACTORY) to Define catalog security options.
These are system wide access policies and GUI formats for the rule-based item catalog method.
Navigation:
This example illustrates the fields and controls on the eProcurement Catalog Security Options page. You can find definitions for the fields and controls later on this page.

Use this page to define the access policy for the item catalogs and the GUI presentation for the Catalog Securities component. If you customize the access policy or GUI presentation, then insert a new row with a new implementation application class.
See PeopleTools: PeopleCode Developer's Guide
Field or Control |
Description |
|---|---|
Class Type |
Enter the interface classes to be used of access policy and GUI presentation. The system is delivered with the class types already defined. However, you can customize and add versions of these classes. The system delivered classes are:
|
Root Package ID |
Select the package of the PeopleCode class that you created. |
Application Class Path |
Enter an application class to further define the implementation (class types). You must enter implementation application classes for the class types of AccessPolicy and GUI. The system is delivered with two implementation application classes. You can override these with custom versions.
|
Description |
Enter a brief description of the purpose of the class type and implementation application class. |
Enabled |
Select to activate the class type and implementation application class combination for the row. Do not select this check box until you have completed the system setup for item catalog security. |
Use the Catalog Types page (PV_CAT_SOURCE) to define catalog types.
Navigation:
This example illustrates the fields and controls on the Catalog Types page. You can find definitions for the fields and controls later on this page.

Use this page to identify the types of item sources that should be available for requisition entry or retrieved by the search and browse feature. Enter all catalog types for use across the organization; this page applies system wide. The catalog types enabled on this page appear in the Catalog Type field on the Catalog Security page.
Field or Control |
Description |
|---|---|
Type |
Enter the catalog type. Use one or more of these options:
|
Record Name |
Enter the record definition that contains all the values for the item source. The system is delivered with the record names for the Item Master table, direct connect suppliers, express forms, and business templates. You can change this record name if you are customizing this area. |
Enabled |
Select to authorize access to this item source on the Catalog Security page. The system automatically changes to Y (yes) for type C and to N (no) for all other catalog types. |
Use the Catalog Security Types page (PV_CAT_SEC_TYPE) to define catalog security types.
These are levels at which you apply catalog security, for example, at the user role level or the individual requester level.
Navigation:
This example illustrates the fields and controls on the Catalog Security Types page. You can find definitions for the fields and controls later on this page.

Use this page to define the levels where security should be applied. For example, suppose that the items available should be restricted by the business unit used to enter the requisition, then activate the row for business unit on this page. You can have multiple security levels defined.
The system is delivered with three security types, business unit, requester ID, and role name. You can add additional security types, for example, ship to location, by inserting a new row on this page. When a user enters a requisition, the list of authorized item catalogs is the intersection of the catalogs granted to each of the security types.
Field or Control |
Description |
|---|---|
Security Type |
Enter a descriptive name for the security type. The system is delivered with BUSINESS_UNIT, REQUESTOR_ID, and ROLENAME. |
Root Package ID |
Enter the parent application package. |
Application Class Path |
Enter an interface class that contains the processing logic for the security type. The system is delivered with BusinesUnitSecurityType, RequestorSecurityType, and QuerySecurityType. The implementation application classes for business unit and requester are specific to those security types and link them into the existing item catalog security system using the Assign Catalog to Business Unit page and the Requestor Setup page. However, the QuerySecurityType is not specific to the user role name and can be used with any additional security types that you may add to this page. For example, suppose that you decide to add a ship to location as a security type, then you can use the QuerySecurityType class for both role name and ship to. |
Description |
Enter a description of the security type. |
Active |
Select to enable this security type for the SetID. If you select this for the security type of BUSINESS_UNIT, then the system:
If you activate the security type REQUESTOR_ID, then the system:
|
Catalog Security |
Click to access the Category Security page, where you can update security parameters. |
Security Type Attributes Page
Use the Security Type Attributes page (PV_CAT_ST_ATTR) to define security type attributes which include query or prompt tables used.
Navigation:
Click the Attributes tab.
This example illustrates the fields and controls on the Security Type Attributes page. You can find definitions for the fields and controls later on this page.

Use this page to define the attributes for each of the security levels that you defined on the Security Types page.
Field or Control |
Description |
|---|---|
Default Access |
Determines access to catalogs when no data entry found for the security type in Catalog Security page. Enter Y to access all item catalogs and enter N for no access to item catalogs. For example, for the security type of business unit, if you do not enter the business unit AUS01 on the Catalog Security page, then a default access value of Y gives AUS01 access to all item catalogs; However, a default access value of N gives AUS01 no access to any item catalogs. Since the system uses an intersect policy, N would prevent any entries into the business unit AUS01. Note: The Default Access field is not applicable to the security type of REQUESTOR_ID, because the system always loads all requesters into the Catalog Security page. |
Query Name |
Enter a query record name to retrieve the acceptable values based on the security type record definitions. A query is required if the implementation application class on the Catalog Security Types page is the QuerySecurityType class. Design this query to retrieve the needed data to find rows. All necessary values can be retrieved based on the requisition's business unit, requester, or user ID. For example, if the ship to location is defined as a security type, then the query would be designed to retrieve the ship to based on the user ID on the User Preferences - Procurement page. |
Prompt Table |
Enter the prompt table to be used for this security type. A prompt table is required if the implementation application class is the system-delivered QuerySecurityType. |
SetID Control |
Select whether the security type query in the Query Name field is SetID controlled. |
Use the Catalog Security page (PV_CAT_SECURITY) to assign authorized item catalogs to security types.
Navigation:
Click the Catalog Security link.
This example illustrates the fields and controls on the Catalog Security page (1 of 2). You can find definitions for the fields and controls later on this page.
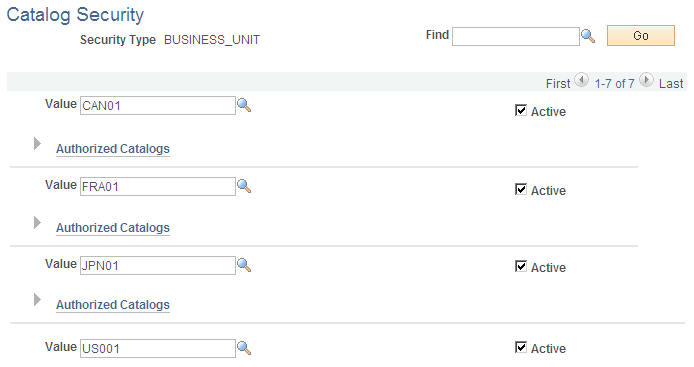
This example illustrates the fields and controls on the Catalog Security page (2 of 2). You can find definitions for the fields and controls later on this page.

For each security type (security level), define what item catalogs are available.
Field or Control |
Description |
|---|---|
Find |
Enter a value on which to search in the scroll area. Use this field when you have a large number of values in the scroll area. |
Value |
Select a field value that you have defined for this security type. |
Active |
Select to enable the item catalogs security for this value. If this value is not selected, then the Default Access field on the Security Type Attributes page is applied. |
Authorized Catalogs |
Click the Show Authorized Catalogs button to display or enter the set of item catalogs authorized for the value. This includes all item catalogs, no catalogs, or a specific set of catalogs. To add item catalogs, select the catalog type and click the Select Catalogs link to display all valid catalogs, then select the catalog and click the OK button. The new catalog appears in the Authorized Catalogs section. |
Add |
Select to add a new row to this page, so that you can enter a new value. |
Update All Business Units
Use this section to add or remove item catalogs to all of the listed values. For example, if a new item catalog is created after implementation, use this feature to add the catalog to all business units, requesters, and user roles. To add or remove item catalogs, select the catalog type, use the Select Catalogs link to display all valid catalogs, then select the catalogs and click the Add To All or Remove From All button.
Use the eProcurement Business Unit Actions page (PV_ACTIONS_BU) to identify the PeopleSoft eProcurement actions that should be used for each business unit.
The applicable PeopleSoft eProcurement actions enable security for items from the business template, express forms, and direct connect suppliers.
Navigation:
Click the eProcurement Business Unit Actions link on the Maintain Business Units page.
This example illustrates the fields and controls on the eProcurement Business Unit Actions page. You can find definitions for the fields and controls later on this page.

If you have set up the system to control access to direct connect, express forms, or company templates, then you must identify specific business units that utilize the catalog security. For each action, you need to identify business units you wish to apply catalog security to:
Field or Control |
Description |
|---|---|
Action Name |
Options are:
|
Note: Item security is always enabled for the items within the PeopleSoft Item Master table.