18 Deploying and Administering Communication Services
This chapter describes how to deploy and administer communication services in Oracle Communications Services Gatekeeper.
About Communication Services
All telecommunication traffic processed by Services Gatekeeper passes through a communication service. Each communication service includes an application-facing (north) interface connecting it to an application, a service plug-in that provides functionality, and a network-facing (south) interface connecting it to your network nodes.
For:
-
An overview of communication services, see Services Gatekeeper Concepts.
-
Details on the communication services that Services Gatekeeper includes, see Services Gatekeeper Communication Service Reference Guide.
-
Information on creating your own custom communication services see Services Gatekeeper Extension Developer's Guide.
Understanding How Communication Services are Packaged
Communication services are packaged and deployed in EAR files. Container services are packaged and deployed separately from the communication services and should not be modified.
All network protocol plug-ins that share the same group of application-facing interfaces are packaged into the same EAR file.
All communication services that share a common set of application-facing interfaces are grouped together. For example, Services Gatekeeper is delivered with two communication services for Parlay X 2. 1 Third Party Call:
-
Parlay X 2.1 Third Party Call/INAP, where INAP is exposed through Parlay X 2.1 Third Party Call interfaces.
-
Parlay X 2.1 Third Party Call/SIP, where SIP is exposed through Parlay X 2.1 Third Party Call interfaces.
Each group of communication services is packaged in two separate EAR files:
-
wlng_at_communication service.ear: This file serves as the service facade for the named communication service. It consists of modules shared among the communication service only. The wlng_at_communication service.ear file is deployed in the access tier.
-
wlng_nt_communication service.ear. This file serves as the service enabler for the named communication service. It contains the network protocol plug-ins for the communication service and common modules for the communication service. The wlng_nt_communication service.ear file is deployed in the network tier.
The communication services EAR files are located in the Middleware_home/ocsg_/applications directory.
A Communication Service Packaging Example
The files holding the communication services that share the Parlay X 2.1 Third Party Call communication service layer consist of the following artifacts:
-
wlng_at_third_party_call_px21.ear
-
wlng_nt_third_party_call_px21.ear
About the wlng_nt_third_party_call_px21.ear File
The wlng_nt_third_party_call_px21.ear file contains, among other modules:
-
Plugin_px21_third_party_call_inap.jar, which contains the Parlay X 2.1 Third Party Call/INAP plug-in.
-
Plugin_px21_third_party_call_sip.jar, which contains the Parlay X 2.1 Third Party Call/SIP plug-in.
The Plugin_px21_third_party_call_sip.jar file is one of the artifacts needed to achieve end-to-end service communication for communications services connecting to the SIP network. There is also a part that is deployed as a SIP servlet in the SIP Server container. The SIP servlet parts are packaged in a set of files, wlng-integration-management.jar, wlng-integration-console-ext.war, wlss-int.ear, and wlng-security.jar.
An HTTP servlet is available for plug-ins that use HTPP as the transport protocol and handle network-triggered messages from the network node. HTTP servlets are packaged as Web Archives (WARs) and are packaged in the network tier EAR for the communication service.
Other modules in wlng_nt_third_party_call_px21.ear are shared between the two network protocol plug-ins, including the common parts that are tied to the implementation of the communication layer, and any libraries and utilities shared among the plug-ins.
When adding or removing a plug-in to or from wlng_nt_communication service.ear, expand the EAR and the plug-in specific parts that are being added or removed.
Example 18-1 describes the elements in a wlng_nt_communication service.ear file.
Example 18-1 Contents of wlng_nt_<communication service>.ear
+---APP-INF/lib
...
communication service_callback_client.jar
/<utilities 1>.jar
...
/<utilities n>.jar
+---META-INF/MANIFEST.MF
/application.xml
/weblogic-application.xml
/weblogic-extension.xml
+---<plug-in 1>.jar
...
+---<plug-in n>.jar
+---<plug-in 1>.war
...
+---<plug-in n>.war
+---<communication service>_service.jar
In Example 18-1:
-
APP-INF/lib contains any JARs that are shared among the plug-ins in the EAR. This includes the client library for the service callback EJB communication service_callback_client.jar.
One or more utility jar files can be present, depending on the type of communication service.
-
META-INF/MANIFEST.MF is a standard manifest file.
-
META-INF/application.xml is the standard deployment descriptor for EARs.
-
META-INF/weblogic-application.xml is the WebLogic Server-specific deployment descriptor.
-
META-INF/weblogic-extension.xml is a WebLogic Server-specific deployment descriptor.
All plug-ins in the service enabler are packaged as individual jar files in the root of the EAR with the service EJB, communication service_service.jar.
If a plug-in connects to the telecom network using HTTP and supports network-triggered requests, there is also a corresponding WAR file that contains the servlet.
For more information about enterprise application deployment descriptor elements, see ”Referencing JMS Resources in a WebLogic Application” in Oracle WebLogic Server Developing Applications for Oracle WebLogic Server.
Example 18-2 describes the elements in a plug-in jar file.
Example 18-2 Contents of <plug-in X>.jar
+---com/ +---org/ +---META-INF/MANIFEST.MF + instancemap + srv_depl.xml
The plug-in jar file contains the regular elements in a jar and an instancemap. The instancemap element uses the InstanceFactory class to instantiate the plug-in specific implementation of the required interface. See the discussion about "Retrieving Implementation Instances Using InstanceFactory" in Services Gatekeeper Extension Developer's Guide for more information.
Deploying SOAP and RESTful Facades on Multiple AT Clusters
For those communication services that have RESTful facades, both SOAP and RESTful facades are included in the standard EAR files.
If your installation needs to use multiple clusters of AT servers, you must make some adjustments. You cannot deploy the RESTful facade on multiple clusters within the same domain. You can deploy both the RESTful facade and the SOAP facade on a single cluster within the domain and deploy only the SOAP facade on multiple other clusters within that same domain.
To accomplish this, do the following:
-
Undeploy the standard EAR files for the communication services (including the session manager) you are using on any additional clusters your installation requires.
-
Replace the files with special equivalent EAR versions that contain only SOAP interfaces
The file names for .ear files for SOAP interfaces are identical to those of the standard files except that a _soap is appended to the end of the name. The following SOAP-only EAR files should be deployed (as needed) in this situation:
-
wlng_at_call_notification_px21_soap.ear
-
wlng_at_multimedia_messaging_px21_soap.ear
-
wlng_at_payment_px30_soap.ear
-
wlng_at_presence_px21_soap.ear
-
wlng_at_push_message_ews_soap.ear
-
wlng_at_session_soap.ear
-
wlng_at_sms_px21_soap.ear
-
wlng_at_subscriber_profile_ews_soap.ear
-
wlng_at_terminal_location_px21_soap.ear
-
wlng_at_third_party_call_px21_soap.ear
These files are found in the Middleware_home/ocsg/applications directory of your installation. Information on the content of these files is available in the ”Properties” section of each respective communication services reference in Services Gatekeeper Communication Service Reference Guide.
About the Deployment Procedure
Complete the deployment procedure before production.
Important:
From the Administration console:
-
Create Managed Servers for the non-REST AT clusters (for example, WLNG_AT1 and WLNG_AT2).
-
Create Managed Servers for the REST_AT cluster (for example, REST_AT1 and REST_AT2)
-
Create the clusters for these servers (for example WLNG_AT_Cluster and REST_AT_Cluster).
-
Assign the Managed Servers to their appropriate clusters:
-
WLNG_AT_Cluster WLNG_AT1 WLNG_AT2
-
REST_AT_Cluster REST_AT1 REST_AT2
-
-
Change all deployed applications with REST interfaces (that is, the standard EARs), including session manager, to target REST_AT_Cluster.
-
Change the targets of the AT JMS Servers from WLNG_AT* to the REST_AT*.
-
Change the target of WLNG_ATJMSResource from WLNG_AT_Cluster to REST_AT_Cluster.
-
Shut down all servers.
Edit the following snippet of the config.xml file manually. In default installations this file can be found at domain-home/config/config.xml.
<custom-resource> <name>accesstier</name> <target>WLNG_AT_Cluster</target> <descriptor-file-name>custom/at.xml</descriptor-file-name> <resource-class>com.bea.wlcp.wlng.management.descriptor.resource.WlngTierResource</resource-class> <resource-class>com.bea.wlcp.wlng.management.descriptor.resource.WlngTierResource</resource-class> </custom-resource>Change the target in the access tier custom resource from WLNG_AT_Cluster to WLNG_AT_Cluster, REST_AT_Cluster.
-
Locate and open the config.xml file.
In default installations, this file can be found at domain-home/config/config.xml.
-
Carefully edit the following snippet of the config.xml file manually.
<custom-resource> <name>accesstier</name> <target>WLNG_AT_Cluster</target> <descriptor-file-name>custom/at.xml</descriptor-file-name> <resource-class>com.bea.wlcp.wlng.management.descriptor.resource.WlngTierResource</resource-class> <resource-class>com.bea.wlcp.wlng.management.descriptor.resource.WlngTierResource</resource-class> </custom-resource>Change the target in the access tier custom resource from WLNG_AT_Cluster to WLNG_AT_Cluster, REST_AT_Cluster.
-
Start up the administration server and install and deploy the SOAP-only EAR files to the non-REST cluster (WLNG_AT_Cluster).
-
Start the newly installed EAR files using the Administration console. If you forget to do this, their status will be
prepared. -
Start the Managed Servers.
For more information on using the Administration Console to accomplish these tasks, click Help on the console screen.
Understanding Communication Service Version Handling
Communication services are associated with release versions and can be upgraded using in-production deployment.
The version numbering is on the EAR level, which means that all network protocol plug-ins for a given collection of application-facing interface are redeployed.
The version number for a specific communication service is specified in the Weblogic-Application-Version attribute in META-INF/manifest.mf in wlng_at_communication service.ear and wlng_nt_communication service.ear, respectively.
For more information about how to develop applications for production redeployment, see ”Developing Applications for Production Redeployment" in Oracle Fusion Middelware Developing Applications for Oracle WebLogic Server.
Deploying and Undeploying Communication Services and Plug-ins
Communication services are deployed and undeployed as EAR files.
For a description of the different deployment options, see "Overview of the Deployment Process" in Oracle Fusion Middleware Understanding Oracle WebLogic Server.
The EAR file names for each communication service and the JAR names for the network protocol plug-ins are listed a table in the discussion on properties for each communication service chapter in Services Gatekeeper Communication Service Reference Guide.
The properties section also describes the JAR file for the plug-in and other artifacts, such as third-party libraries, used by the plug-in.
Following is an example on how to undeploy the Parlay X 2.1 Third Party Call communication service:
java weblogic.Deployer -adminurl http://<admin host>:<admin port> -user <admin user> -password <admin password -name wlng_nt_third_party_call_px21 -undeploy -graceful
If a plug-in has been removed from the EAR, use the mechanism described in "Performing a Hitless Upgrade".
Version Handling and Patching of Communication Services
See "Patch Management of Services Gatekeeper Systems" in Multi-tier Installation Guide for instructions on patching Services Gatekeeper, including communication services.
Accessing a Traditional Communication Service from DAF
You can access a traditional communication service in DAF by creating an API.
Installing and Configuring
Follow these steps to install and configure the API
-
Install OCSG single tier with cloud template.
-
Run addCommsPack.sh to install selected communication services, see reference for details.
-
Launch OCSG.
-
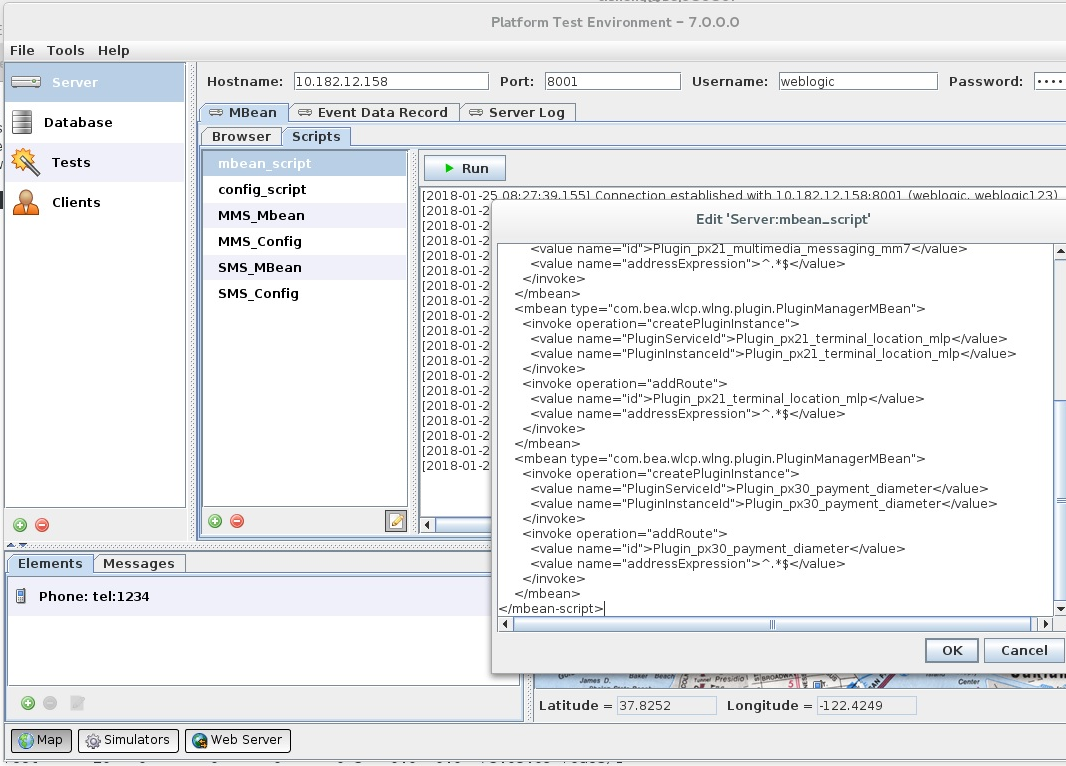
Create a plugin instance and add the route from the PluginManager MBean. Or run the script in the PTE MBean script tool as shown in Figure 18-1:
-
Configure plug-in settings
-
Connect to OCSG MBean using the WebLogic console or the PTE tool. Or run scripts using PTE as in the step above. Different plugins have different settings. This example provides settings for SMS, MMS, Payment and Location. Note that all these examples use PTE simulators as southbound services; you must change the settings if using your actual southbound communication service.
-
If Qos and Payment are not required, disable these plugins by running script in PTE so that no periodic error will be thrown.
-
-
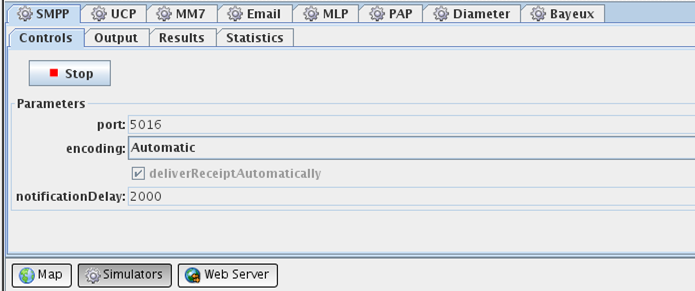
Now all the communication services settings are ready. If the southbound services are the PTE simulators, start the plugin simulators in PTE as shown in Figure 18-2.
Note:
If using actual communication services, this last step is not needed. -
Create the API for communication services.
-
If using REST to create API, reference examples for SMS, MMS, Payment and Location.
-
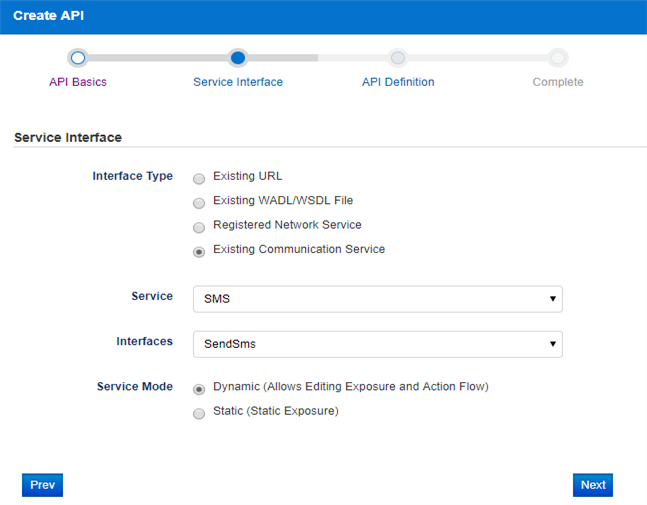
If using OCSG portal, select "Existing Communication Service" when creating API, and choose correct service and interface:
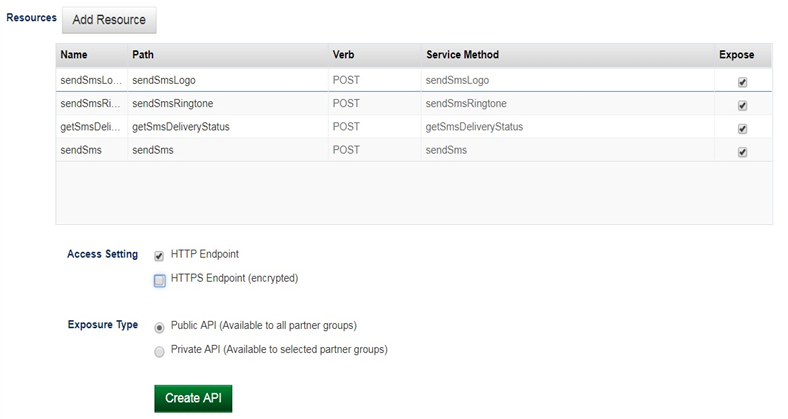
Then on next page, the corresponding methods will be auto added into resource table:
-
-
Create service provider group, service provider, application etc. as usual.
-
Note, to enable specified communication service, some SLA items need to be manually added into the service provider group SLA and application SLA using ServiceLevelAgreement MBean. See references for SMS, MMS and MMS.
Send Traffic
Sending traffic is different in DAF than in a traditional service in the following ways:
-
In DAF, the URL is
<your ip and port>/<api>/<api version>/<function name>. In a traditional service, the URL sometimes includes the user ID. For example,<your ip and port>/rest/<plugin>/<function name>/<user id>/... -
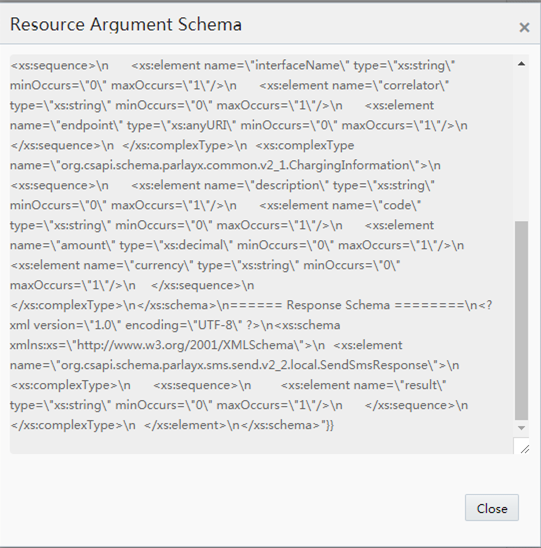
The format of the send payload can be found by right clicking the resource table item and selecting View Details when creating the API. The schema of the XML payload is shown in the detail view. Figure 18-5 shows an example:
The following lines show an example of an XML payload for an SMS send:
<?xml version="1.0" encoding="UTF-8" standalone="yes"?> <sendSms> <receiptRequest> <correlator>987654321</correlator> <endpoint>http://10.182.14.7:13444/jaxws/SmsNotification</endpoint> <interfaceName>interfaceName</interfaceName> </receiptRequest> <addresses>tel:1234</addresses> <message>Hello world</message> </sendSms>
Authentication
The traditional way of doing authentication is by logging into the sesssion manager and that authentication is then used to access the communication service. With DAF, north bound authentication (text, OAuth, or appkey) must be done on the DAF side.
In most cases, you cannot use traffic users in DAF to access traditional communication service traffic because SLA structures are completely different between the DAF user and the traditional communication-service user. In other words, most communication service interfaces should be exposed to DAF. The only exception is to start a notification listener. If you set SessionRequired to Disabled in ApplicationSessionMBean, you can use DAF users to receive notifications - in other words, to start a notification listener.
Service Types and Interfaces
When you create an API, only the service types and interfaces enabled in MBean can be listed in the Existing Commucication Service.
-
To see the enabled service types and interfaces, on the Admin console navigate to ${domain}->OCSG->${ManagedServerName}->Container Services->DafGeneralInformation->DafGeneralInformation and invoke the operation retrieveAvailableDafCSConfigurations.
-
To see theall the configured service types and interfaces, on Admin console navigate to ${domain}->OCSG->${ManagedServerName}->Container Services->DafGeneralInformation->DafGeneralInformation and invoke the operation retrieveDafCSConfigurations.
-
To enable or disable the service types and interfaces, on the Admin console navigate to ${domain}->OCSG->${ManagedServerName}->Container Services->DafGeneralInformation->DafGeneralInformation and invoke the operation updateDafCSConfigurations. You can invoke the operation retrieveDafCSConfigurations first and then do add/remove/update. Set the enable attribute to true if you want to enable service types or interfaces.
When enabled in the MBean, the service type or displayName attribute is shown in the portal.
OCSG has provided out-of-the-box confiugrations of service types and interfaces.
By default not all interfaces will be exposed to partner manager for DAF traffic. Table 18-1 describes the provided service types and interfaces.
Table 18-1 Service Types and Interfaces Exposed
| Service Type | Service Display Name | Exposed Interfaces (DisplayName) | Not Exposed Interfaces |
|---|---|---|---|
|
MultimediaMessaging-ParlayRestMms |
MMS |
com.bea.wlcp.wlng.px21.plugin.SendSmsPlugin(SendSms) com.bea.wlcp.wlng.px21.plugin.ReceiveSmsPlugin(ReceiveSmsP) oracle.ocsg.parlayrest.plugin.parlayRestSmsPlugin(parlayRestSms) com.bea.wlcp.wlng.ews.plugin.BinarySmsPlugin(BinarySms) |
com.bea.wlcp.wlng.px21.callback.SmsNotificationCallback com.bea.wlcp.wlng.ews.callback.BinarySmsNotificationCallback oracle.ocsg.parlayrest.callback.ClientSmsNotificationCallback com.bea.wlcp.wlng.px21.plugin.SmsNotificationManagerPlugin com.bea.wlcp.wlng.ews.plugin.BinarySmsNotificationManagerPlugin |
|
Sms |
SMS |
com.bea.wlcp.wlng.px21.plugin.TerminalLocationPlugin(TerminalLocation) oracle.ocsg.parlayrest.plugin.TerminalLocationPlugin(ParlayRESTTerminalLocation) |
com.bea.wlcp.wlng.px21.plugin.TerminalLocationNotificationManagerPlugin com.bea.wlcp.wlng.px21.callback.TerminalLocationNotificationCallback |
|
TerminalLocation-ParlayRestTerminalLocation |
Location |
com.bea.wlcp.wlng.px21.plugin.TerminalLocationPlugin(TerminalLocation) oracle.ocsg.parlayrest.plugin.TerminalLocationPlugin(ParlayRESTTerminalLocation) |
com.bea.wlcp.wlng.px21.plugin.TerminalLocationNotificationManagerPlugin com.bea.wlcp.wlng.px21.callback.TerminalLocationNotificationCallback |
|
Payment- ParlayRestPayment |
Payment |
com.bea.wlcp.wlng.px30.plugin.AmountChargingPlugin(AmountCharging) com.bea.wlcp.wlng.px30.plugin.ReserveAmountChargingPlugin(ReserveAmountCharging) com.bea.wlcp.wlng.px30.plugin.VolumeChargingPlugin(VolumeCharging) com.bea.wlcp.wlng.px30.plugin.ReserveVolumeChargingPlugin(ReserveVolumeCharging) oracle.ocsg.parlayrest.plugin.PaymentPlugin(ParlayRESTPayment) |
|
|
PxQoS-RestQoS |
QoS |
com.bea.wlcp.wlng.px40.plugin.ApplicationQoSPlugin(ApplicationQoS) com.bea.wlcp.wlng.px40.plugin.ApplicationQoSNotificationManagerPlugin(ApplicationQoSNotificationManager) oracle.ocsg.parlayrest.plugin.QoSPlugin(ParlayRESTApplicationQoS) |
com.bea.wlcp.wlng.px40.callback.ApplicationQoSNotificationCallback oracle.ocsg.parlayrest.callback.QoSNotificationCallback |
|
RestAppSubscription |
RestAppSubscription |
oracle.ocsg.parlayrest.plugin.ConfirmSubscriptionPlugin(ConfirmSubscription) oracle.ocsg.parlayrest.plugin.QuerySubscriptionPlugin(QuerySubscription) oracle.ocsg.parlayrest.plugin.SubscriptionPlugin(Subscription) |
Dynamic Versus Static Mode
You can configure the API to use communication services in two ways: Dynamic Mode or Static Mode. Table 18-2 shows the differences between dynamic and static mode.
Table 18-2 Comparison of Dynamic Mode and Static Mode
| Dynamic Mode | Static Mode | |
|---|---|---|
|
Multiple APIs to One Service Type |
Multiple APIs to specified ServiceType+Interface are supported. You can create multiple APIs to use same commucation service |
Multiple APIs to specified ServiceType+Interface are not allowed For a specified communication service, you can create only one API |
|
Northbound Context-Path |
You specify context path when you create the API |
The calling plugin manager internally generates the north-bound context-path |
|
Traffic Runtime |
The traffic is served by DAF runtime |
The traffic is served by Communication Service runtime |
|
DAF Action Support |
Supported |
Not supported |
Configuring DAF Two-Way SSL Support
OCSG supports two-way SSL communication with backend (southbound) service. When it creates an asynchronous or synchronous client for the backend service, OCSG invokes the loadKeyMaterial() method on the SSLContextBuilder to support client SSL and re-uses the managed server's key stores and SSL configuration.
Choosing an Alias When Multiple Aliases Are Matched
To allow you to specify the alias when multiple aliases are matched for the client SSL, you can specify the alias name by MBean, using the Private Key Alias on the SSL tab, or by using the oracle.sdp.daf.keystore.alias JVM parameters.
The following rules apply:
-
If you specify the oracle.sdp.daf.keystore.alias and its value is matched in multiple aliases, the alias of the oracle.sdp.daf.keystore.alias value is used.
-
If you do not specify oracle.sdp.daf.keystore.alias or the oracle.sdp.daf.keystore.alias value is not matched in multiple aliases, and if the MBean alias is matched in multiple aliases, the value of the Private Key Alias on the SSL tab is used.
-
If either of the above two cases are satisfied, you may choose to use any one of the multiple aliases.
Additional Considerations
You should also consider the following:
-
When the Key Store configuration changes, enable SSL on the managed server and restart the DAF module.
-
The following apply to the key store and trust store configuration:
-
For single-tier and single-tier standalone, the certification of the back-end service must be imported into OCSG trust store, which is specified by the WebLogic KeyStores MBean. Certification of the OCSG key store must be imported into the back-end service's trust store.
-
For a single-tier cluster environment, to echo the OCSG node, certification of the back-end service must be imported into the OCSG trust store, which is specified by the WebLogic KeyStores MBean. Certification of the OCSG key store must be imported into the back-end service trust store and it is recommended that all nodes use the same private key store string.
-
For a multi-tier cluster environment, to echo the OCSG node, certification of the back-end service must be imported into the NT trust store, which is specified by the WebLogic KeyStores MBean. Certification of the NT key store must be imported into the back-end service trust store and it is recommended that all NT nodes use the same private key store string.
-
Configuring Two-Way SSL for Southbound
Southbound service is required to support two-way SSL and must be configured correctly. You can use either spring boot or another weblogic server as the southbound SSL server. If you are using another WebLogic server as the SSL server, the configuration is same as "Configuring Two-Way SSL for Northbound".
For southbound two-way SSL, OCSG acts as the client. Follow these steps to configure southbound two-way SSL:
-
Generate a private key pair and a private key store using the following keytool command:
keytool -import -alias myCa1 -trustcacerts -file cert.cer -keystore ${ORACLE_HOME}/wlserver/server/lib/DemoTrust.jks -storepass DemoTrustKeyStorePassPhrase -
Configure the items server.ssl.key-store, server.ssl.key-store-password and server.ssl.key-password correctly based on the information from step 1.
-
Export the private key into a certificate file and import it into the OCSG's trust store.
-
Generate a trust key store and configure server.ssl.trust-store and server.ssl.trust-store-password correctly.
-
Import the OCSG's private key into the trust store.
-
Restart SSL for the first server on the Weblogic console for single-tier. For multi-tier, you configure each NT server one by one.
Configuring Two-Way SSL for Northbound
All northbound HTTPS traffic is handled by WebLogic. Follow these steps to configure WebLogic for northbound (incoming) two-way SSL requests:
-
Export the private key for northbound SSL (for self-signed private key) to a certificate file. If not a self-signed private key, export the root certificate of its private key, and import it into the trust store using the following key-tool command.
keytool -import -alias myCa1 -trustcacerts -file cert.cer -keystore ${ORACLE_HOME}/wlserver/server/lib/DemoTrust.jks -storepass DemoTrustKeyStorePassPhrase -
On the WebLogic console, change the SSL setting for the target sever : Domain -> Environment -> Servers -> select target server -> choose tab SSL -> click Advanced - > from the Two Way Client Cert Behavior drop-down menu, select "Client Certs Requested and Enforced".
-
Save and activate the changes.
-
Restart SSL for the first server on the Weblogic console for single-tier. For multi-tier, you configure each NT server one by one.
The northbound service then becomes accessible to OCSG
Adding Communication Service Applications
You can add communication service applications to an existing OCSG domain. The feature applies to a single-tier configuration only. All communication services are installed automatically in a multi-tier configuration.
The tool supports the Linux platform and performs the following operations:
-
Gets the necessary application package files from the installer
-
Configures the domain to deploy the applications
-
Updates the domain to add communication service related services
-
Updates the startup script to adjust related settings
-
Updates the installation inventory to allow the OPatch tool to update newly added packages.
The following packages are used by communication services:
Table 18-3 Packages Used By Communication Services
| Communication Service | Functionality | Packages Delivered | Optional Feature Set |
|---|---|---|---|
|
SMS |
Messaging |
wlng_at_sms_parlay_rest.ear (For one API interface) wlng_at_sms_px21_soap.ear (For SOAP interface) wlng_nt_sms_px21.ear (MUST be deployed) |
Application - SMS (ocsg_app_sms) |
|
MMS |
Messaging |
wlng_at_multimedia_messaging_parlay_rest.ear (For one API interface) wlng_at_multimedia_messaging_px21_soap.ear (For SOAP interface) wlng_nt_multimedia_messaging_px21.ear (MUST be deployed) wlng_at_multimedia_messaging_mm7.ear (For SOAP interface, MM7) wlng_nt_multimedia_messaging_mm7.ear (MUST be deployed for MM7) |
|
|
Payment |
Payment |
wlng_at_payment_parlay_rest.ear (For one API interface) wlng_at_payment_px30_soap.ear (For SOAP interface) wlng_nt_payment_px30.ear (MUST be deployed) |
Application - Payment (ocsg_app_payment) |
|
Terminal Location |
Location |
wlng_at_terminallocation_parlay_rest.ear (For REST interface) wlng_at_terminal_location_px21_soap.ear (For SOAP interface) wlng_nt_terminal_location_px21.ear (MUST be deployed) |
Application - Terminal Location (ocsg_app_termloc) |
|
QoS |
Quality of Service |
wlng_at_qos_px40.ear (For SOAP interface) wlng_nt_qos.ear (MUST be deployed) |
Application - QoS (ocsg_app_qos) |
|
Application Subscription |
Subscription |
wlng_at_app_subscription_rest.ear (For REST interface) wlng_nt_app_subscription.ear (MUST be deployed) |
Application - Subscription (ocsg_app_subscription) |
Using the Tool
Follow these steps to use the addCommsPack.sh tool:
-
Prepare a valid single-tier installer file.
-
Set the environment variable JAVA_HOME to the JDK location. Otherwise the tool will prompt the user to enter the location.
-
Shut down OCSG.
-
Run the following script and specify the domain location:
${ORACLE_HOME}/wlserver/common/templates/scripts/addCommsPack/addCommsPack.sh ${DOMAIN_HOME} ${SINGLETIER_INSTALLER_FILE} -
When the script finishes, restart OCSG.
The tool can add any application, server service as long as the required information is present in the list files.
You can customize the tool by editing the following files:
-
pkgList
Contains the required application package names, for example wlng_nt_sms_px21.ear. One line per package. Each line that starts with # is treated as a comment and ignored during processing.
-
serviceList
Contains the required service's full class name, for example oracle.ocsg.protocol.smpp.SMPPServerService. One line per server service. Each line that starts with # is treated as a comment and ignored during processing.
-
featuresetList
Contains the list of optional feature set names to be added to the installation inventory, for example ocsg_app_sms. One line per feature set. Each line that starts with # is treated as a comment and ignored during processing.
Overview of Container Services and Their Configuration Files
Table 18-4 gives an overview of the Services Gatekeeper configuration files.
Table 18-4 Services Gatekeeper Configuration Files
| File | Contains configuration for... |
|---|---|
|
Domain_home/config/config.xml |
WebLogic Server. See "Domain Configuration files" in Oracle WebLogic Server Understanding Domain Configuration for Oracle WebLogic Server. Note: Do not edit this file manually. The following additional elements are specific to Services Gatekeeper:
To manage the lifecycle of communication services, use the WebLogic Server tools, such as the Administration Console's Deployment page or the command-line tools. For more information see "Overview of Common Deployment Scenarios" in Oracle Fusion Middleware Deploying Applications to Oracle WebLogic Server. |
|
Domain_home/config/custom/at.xml |
Services Gatekeeper access tier container and container services. This is a custom resource. Note: Do not edit this file. |
|
Domain_home/config/custom/nt.xml |
Services Gatekeeper network tier container and container services. This is a custom resource. Note: Do not edit this file. |
|
Domain_home/config/custom/wlng-edr.xml |
EDRs, CDRs, and alarms. This is a custom resource Note: Do not edit this file manually. |
Finding Container services
Table 18-5 describes the Services Gatekeeper Java EE container services. The interfaces to these, with common classes, are packaged in
Middleware_home/ocsg/server/lib/wlng/wlng.jar
The container services are packaged in separate JARs, located in
Middleware_home/ocsg/server/lib/wlng/wlng.jar
Table 18-5 Services Gatekeeper Container Services
| Container service | Summary |
|---|---|
|
com.bea.wlcp.wlng.core.CoreServerService |
Performs initial setup during the start-up sequence. |
|
com.bea.wlcp.wlng.snmp.SNMPServerService |
SNMP service. |
|
com.bea.wlcp.wlng.event_channel.EventChannelServerService |
Broadcasts arbitrary events between modules and servers in a cluster. |
|
com.bea.wlcp.wlng.storage.StorageServerService |
Storage service. |
|
com.bea.wlcp.wlng.storage.db.DbServerService |
Storage provider for persistence using direct database access. |
|
com.bea.wlcp.wlng.storage.inval.InvalidatingServerService |
Storage provider for persistence using an invalidating cache. |
|
com.bea.wlcp.wlng.storage.configuration.ConfigurationStoreServerService |
Storage provider for configuration settings. |
|
com.bea.wlcp.wlng.edr.EdrServerService |
EDR service. |
|
com.bea.wlcp.wlng.core.budget.BudgetServerService |
Budget service. |
|
com.bea.wlcp.wlng.georedundant.GeoRedundantServerService |
Geographical redundancy service. |
|
Account service. |
|
|
com.bea.wlcp.wlng.statistics.StatisticsServerService |
Statistics service. |
|
com.bea.wlcp.wlng.plugin.PluginManagerServerService |
Plug-in manager. |
|
com.bea.wlcp.wlng.storage.georedundant.GeoRedundantStoreServerService |
Storage provider for intercepting store operations for geographically redundant stores, forwarding changes to the geo storage server service functions and reads to the local storage provider. |
|
com.bea.wlcp.wlng.geostorage.GeoStorageServerService |
Geo storage server service that has the geo storage singleton services, manages the geo-master lifecycle, performs calls remote calls to the other site, and consistency checks between sites. Also has the geo storage Mbean. |
|
com.bea.wlcp.wlng.tier_routing.TierRoutingManagerServerService |
Tier routing manager. |
Patching Container Services
You patch container services using the SmartUpgrade utility. See ”SmartUpgrade Support for JDBC” in Oracle Fusion Middleware Administering JDBC Data Sources for Oracle WebLogic Server.
You patch container services and WebLogic Server using the upgrade process. See "Understanding the 12c Upgrade Process" in Oracle Fusion Middleware Upgrade Planning Guide.